HAL Id: hal-00701137
https://hal.archives-ouvertes.fr/hal-00701137v2
Submitted on 7 Oct 2014HAL is a multi-disciplinary open access archive for the deposit and dissemination of sci-entific research documents, whether they are
pub-L’archive ouverte pluridisciplinaire HAL, est destinée au dépôt et à la diffusion de documents scientifiques de niveau recherche, publiés ou non,
Collaborative and Cybernetic Driving
Ana-Maria Roxin
To cite this version:
DELIVERABLE
DEL 5.3 Collaborative and Cybernetic
Driving
3 December 2008
ASSET–Road
DEL 5.3. Collaborative and Cybernetic Driving
Document information
Short title ASSET–Road
DEL 5.3. Collaborative and Cybernetic Driving
Client:
Contractor:
Order no.:
Edited by: Ana Roxin (UBM)
Version: 0.1
Authors: Ana Roxin (UBM)
Created on: 02/12/08
Revision Log
Version Date Action Partner
0.1 2 December 2008 Original draft UBM
0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9
Partner
Contents
1 Context Information ... 5 1.1 Definitions ... 5 1.2 Context Modelling ... 5 1.3 Context-aware Systems ... 7 2 Collaborative Driving ... 82.1 Definition and Principles ... 8
2.1.1 Wireless Communications supporting CDS 9 2.1.2 Digital Maps and Satellite Positioning supporting CDS 11 2.2 Cooperative Driving Applications ... 12
2.2.1 Longitudinal Collision Avoidance Systems (CAS) 12 2.2.2 Intelligent Speed Adaptation 14 2.2.3 Cooperative Intersection Collision Avoidance Systems (CICAS) 14 2.2.4 Cooperative Approaches for Vulnerable Road Users 15 2.2.5 Traffic Flow Improvement 15 3 Conclusions ... 16
1 Context Information
1.1
Definitions
The notion of context has been observed in numerous areas, including linguistics, philosophy, knowledge representation and problem solving in the field of artificial intelligence, and the theory of communication [8-11]. In most work of this nature, context is a key notion (e.g., treated as first-class objects in a logic), and logics have been developed to enable assertions to be made about contexts and allow context to be reasoned about explicitly in knowledge-based systems.
What is context? The Free Online Dictionary of Computing defines context as “that which surrounds, and gives meaning to, something else.”
This definition can be specialized to the application at hand. Whether that “something” is an assertion in logic, a person, an utterance, or a computer system, with a suitable definition for “meaning,” the intuition captured by the word context serves its purpose. [12] define context from the perspective of distributed and mobile computing, where a person is that “something,” and context refers to information about a person’s proximate environment, such as location and identities of nearby people and objects.
[14] gives an operational definition of context, which turns out to be very useful in practice and suitable for pervasive computing: “Context is any information that can be used to characterize the situation of an entity. An entity is a person, place, or object that is considered relevant to the interaction between a user and an application, including the user and applications themselves.”
1.2
Context Modelling
There has been much work in identifying what such information can be, the structure of the information, how to represent such information, and how to exploit context in specific applications. Contexts can include information such as location (e.g., of people or objects), time, execution state of applications, computational resources, network bandwidth, activity, user intentions, user emotions [15], and conditions of the environment [14].
Figure 1 illustrates the existing context information categories [1]:
• The primary context information consists in spatial information (identity, time and location). This kind of context information may be used in order to index entities.
• The secondary context information consists of additional aspects of a given entity, generally divided according the context they refer to (personal, technical, spatial, social or physical context).
UBM
Figure 1. Types of context
Models might be used for more complex kinds of contextual information, such as location models (e.g. [38]), world models [16], and activity models [17-19].
Indeed, there is tremendous diversity in what can be context, and the way context can be acquired and modelled is an avenue of much research. Recent workshops have focused on just this topic. To address the challenges in representing, structuring, managing, and using context, various knowledge-representation formalisms and techniques have been applied, including ontologies [20-23] that provide concepts for describing context and enable reasoning with and reuse of contextual information, first-order logic theories [24,25], and conceptual graphs [26]. One needs to consider what aspects of the physical world to sense for a given application to operate. The ontologies provide a vocabulary of concepts with which to express contexts, and formal mathematical representations enable automatic reasoning with the knowledge on the computer.
Pervasive computing utilizes contextual information about the physical world. This implies a number of important concerns related to the connection of sensor information to context-aware pervasive computing, including:
• What can be feasibly sensed;
• The best way to acquire sensor information;
• How to reason with sensor information to infer context.
In fact, any information which can be practically obtained via sensors can be used as context, including the emotional states of users and movements.
1.3
Context-aware Systems
Quoting from [13]: “…Context-aware software adapts according to the location of use, the collection of nearby people and objects, the accessible devices, as well as changes to those objects over time. A system with these capabilities surveys the computing environment and reacts to changes to that environment.” Context-aware pervasive computing is a study of pervasive computer systems (a combination of hardware and software) that are aware of context and can automatically adapt and respond to such context. Context awareness enables the system to take action automatically, reducing the burden of excessive user involvement and providing proactive intelligent assistance.
In [27], authors consider such use of perceptual information about the environment an essential ingredient of pervasive computing systems, distinguishing them from traditional computing. Such context-aware pervasive systems have wide-ranging applications, including context-aware information retrieval [28], reminder systems [29], context-aware mobile services and electronic tour guides [30], sentient objects [31,32], sentient cars [33], sentient buildings, context-aware response to emergencies, and intelligent context-aware environments [34], with potential benefits to society, ranging from proactive automated healthcare [35] and effective E-commerce [36] to more effective military systems [37] and safer cars. Indeed, one can also utilize context awareness in security warning systems in the home or public spaces. Many future computing systems will advantageously be context aware, and context-aware systems are becoming increasingly important, receiving worldwide attention from academia and industry.
To support the process of incident management, the need for mobile context-aware (spatial) information and supporting information systems is large. Adapting to changes in the environment is at the heart of context-aware computing where it is envisaged that, by adding context, computers could:
• Provide more relevant and useful location- and task-specific feedback by using, say, the user’s current location, the time of day, and the user’s electronic personal diary,
• Make user interaction more natural and personalised, thus increasing the richness of communication, and
• Be more dynamic by adapting to the continuously changing situation of the user.
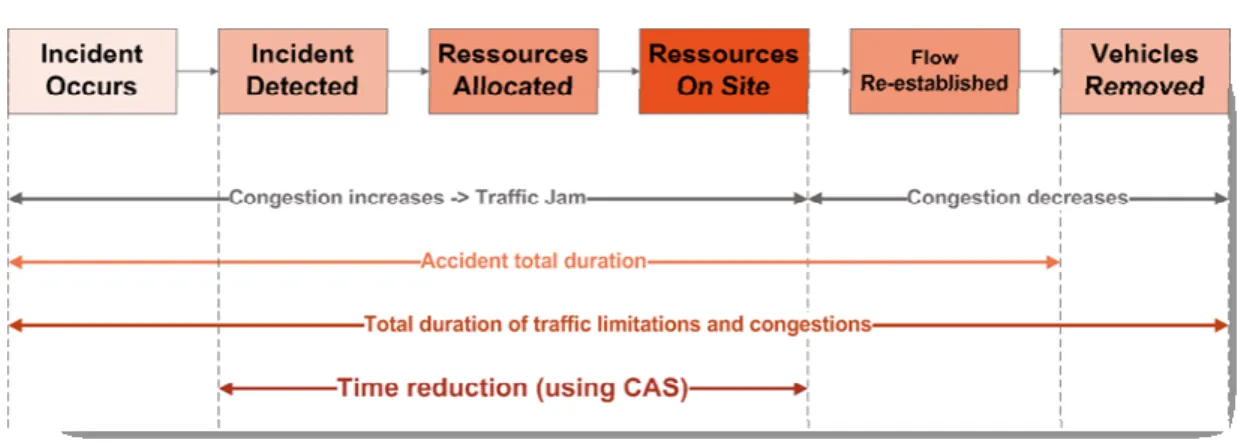
For example, real-time location and status information of an inspector makes logistics and coordination activities much more effective. Figure 2 gives an overview of the different phases of the incident management process. The introduction of mobile context-aware information systems can reduce the time interval between the detection of the interval and the flow of traffic is re-established in a significant way. This has in return a direct positive effect on the reduction of traffic jams.
UBM
Figure 2. Incident Management phases.
2 Collaborative Driving
2.1
Definition and Principles
What can be accomplished, however, if the vehicles cooperate with each other and the highway as an integrated system? What if information concerning traffic ahead, obstacles, and road and weather conditions were flowing as freely between electronic subsystems on the vehicle as do land-side computers accessing the Internet?
This is the fundamental premise for CDS, which open the way for a “federated computing” approach to road-vehicle systems. Some applications, such as intersection collision avoidance, work better with CDS, and others—such as traffic flow enhancement—are not possible at all without cooperation.
The prospect of employing vehicle-highway cooperation to gain vast improvements in the safety and efficiency of the road-vehicle system has been a part of the ITS program since the beginning. In fact, during the early years of ITS [then called Intelligent Vehicle highway system (IVHS)], the possibilities offered by a cooperative system approach were the central concept that gave momentum to the overall program. In those more visionary days, this cooperation was embodied in the idea of an AHS, whereby roadway elements and communications would interact with automated vehicles to increase road capacity. What is emerging now is a more gradual building-block approach.
Cooperative systems rely fundamentally on wireless communications to enable data exchange. Therefore, the first portion of this chapter is an overview of communications applied to this purpose. We then briefly cover maps and satellite positioning, which forms another pedestal on which CDS rests. Then we finally plunge into some CDS functional areas thus far neglected: intelligent-speed adaption (ISA), intersection crash avoidance (ICA), and IV-based traffic flow improvements.
2.1.1
Wireless Communications supporting CDS
In order to define vehicle communications, one must first differentiate the different types of communication that may occur. Mainly, there are two types of vehicle communication:
• Intra-vehicle communication reference communications that occur within a vehicle.
• Inter-vehicle communication represents communications between vehicles or vehicles and sensors placed in or on various locations, such as roadways, signs, parking areas, and even the home garage.
In the rest of this paper, we will only focus on inter-vehicle communications. The primary modes of communication in this category are the following:
• Vehicle to/from roadside communication mode requires using roadside transponders. Vehicle to/from roadside communication supports both vehicle-specific data as well as locally relevant data broadcast to vehicles. This category is referred to as Vehicle-to-Infrastructure (V2I) communication.
• Vehicle to/from vehicle communication mode includes in-line communications with neighbouring vehicles (including those travelling in the opposite direction and those travelling in the same lane). This category is referred to as Vehicle-to-Vehicle (V2V) communication.
For the concept of “intelligent vehicle” to be viable, a wide range of applications is needed, in order to lower the costs per application. Therefore, an extensive set of applications based on vehicle communications has been conceptualised. A sampling of these applications is given in the following table.
V2I Applications V2V Applications
Curve speed warning Emergency braking of forward vehicle
Optimal speed advisory Pre-crash warning
Highway work zone warning Driver advisories when making turns across traffic
Highway/rail crossing collision avoidance Lane change warning
Traffic signal violation warning Approaching emergency vehicle advisory
Low bridge warning Stop sign movement assistance
Road condition warning Road condition warning
Electronic toll collection Cooperative adaptive cruise control
Wireless diagnostics
Software “flashing”
Commercial driver log information
Vehicles acting as data probes for traffic and road information
UBM
Table 1. Vehicle wireless communications applications overview.
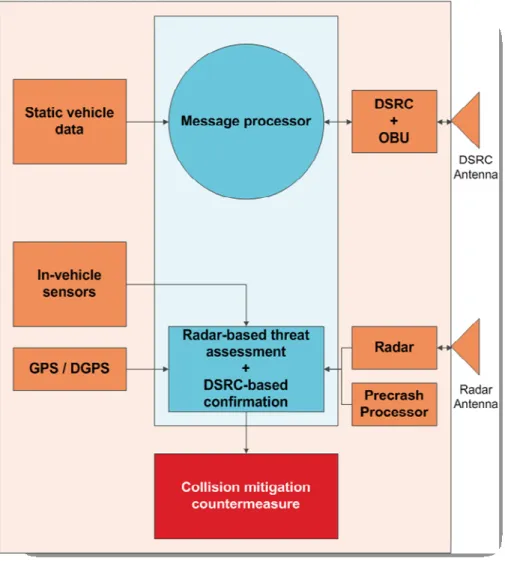
For illustrative purposes, communications for precrash sensing is examined in a bit more detail here. The required communication range is approximately 25m, with messaging in a broadcast mode for more basic systems. However, a cooperative precrash sensing system can also be conceptualized in which two-way communications occurs once the radar sensor predicts the eventuality of a collision, in order to exchange data such as vehicle type. A generic block diagram for such a system, developed within the VSCC project, is shown in Figure 3.
Figure 3. Cooperative Driving Application Illustration – Precrash Sensing
In Figure 3, in-vehicle sensors refers to information that is available on the vehicle data-bus, such as speed, yaw rate, longitudinal acceleration, lateral acceleration, steering wheel angle, air bag crash sensors, and brakes and throttle status data. Static vehicle data refers to parameters such as vehicle ID, class, size, mass, and DSRC antenna location. The differential GPS (DGPS) unit provides vehicle position, heading, and time stamp. The DSRC onboard unit (OBU) provides messaging at 10 Hz in broadcast mode and 50 Hz for two-way communications.
processor consists of a DSRC message processing unit and a radar processing unit to conduct the threat evaluation and confirmation based on the radar data, the host vehicle data and the DSRC message data. Commands for actuation of airbags or braking are generated by the collision countermeasures module.
2.1.2
Digital Maps and Satellite Positioning supporting
CDS
Onboard digital maps combined with satellite positioning can be seen as a type of cooperative system, as positioning data is received from outside the vehicle. Digital maps combined with satellite positioning can play a crucial role in supporting active safety systems as well as navigation. In previous chapters, we saw several references, including the applications of adaptive headlights and curve speed warning. Lane-level maps, which also include a rich data set regarding roadside hardware (guardrails, signs, bridge abutments), are under development for future systems, so that, for instance, a radar system has additional data in distinguishing on-road from off-road objects.
Automotive researchers have identified a wide range of applications that could be enhanced by digital map data. These include the following:
• Curve speed warning; • Curve speed control; • Adaptive light control; • Vision enhancement; • Speed limit assistant; • Path prediction;
• Fuel consumption optimization; • Power train management; • ACC (Adaptive Cruise Control); • ACC optimized for heavy trucks; • Stop & go ACC;
• Lane-Keeping Assist;
• Collision warning/avoidance; • Autonomous driving.
The map data assists in the overall scene interpretation in several ways. Image processing systems are complemented by map data on where the road is “supposed” to be, which can generally improve lane detection and reduce false alarms. Additionally, when the presence of exit ramps and splits in the road are known from the digital map, lane detection algorithms can take these features into account. Digital map data can also assist in maintaining lane tracking during temporary dropouts of vision sensing, due to camera “blinding” by direct sunlight at dawn or dusk, for instance. For radar systems, hills may cause a tracked target to suddenly “disappear” and three-dimensional map data can assist the system in maintaining tracking and reacquiring the target as the vehicle travels over the crest of a hill. A particular challenge for digital mapping is in keeping the map up-to-date. Current maps are created through a labour intensive and non-real-time process, with updates generated every few months. To support active safety systems, the maps must always be accurate; therefore, real-time updating is required. This requires, in turn, methods to collect the data as well as for vehicles to download new data and integrate it with the existing onboard map.
UBM
2.2
Cooperative Driving Applications
2.2.1
Longitudinal Collision Avoidance Systems (CAS)
Cooperative driving systems can provide warnings to drivers at high-risk areas for situations that cannot be detected by onboard vehicle sensors. These may be fixed hazards such as curves, dynamic hazards such as slippery road conditions or a disabled vehicle ahead, or even the presence of animals along the roadway detected by special sensing systems [7].
CAS provides the drivers with knowledge of the environment surrounding the vehicle with the intention of reducing the probability of accidents. Figure 4 depicts the “zone” of applicability of the various CAS.
Figure 4. Diagram of Collision Avoidance System [2].
Table 2 gives examples of vehicle-mounted sensors that support various collision and hazard avoidance strategies and prevent specific types of crashes [3]. Headway detection advises the driver of an imminent crash with an obstacle or to maintain a safe distance when following another vehicle. Proximity detection gives the driver information about adjacent lane vehicles or obstacles while backing up. The lane position monitor advises the driver if the vehicle is drifting out of its travel lane. In-vehicle signing conveys posted or dynamic information to the driver from the traffic management infrastructure. A gap acceptance aid advises the driver when it is safe to cross or turn at intersections. Vision enhancement gives the driver a clearer image of the roadway and environment ahead during reduced visibility conditions such as heavy rain, fog, and night-time.
Technique Vehicle-mounted sensor Preventable crash
Headway detection
Millimetre-wave radar, laser radar, video
Rear-end
Proximity detection Millimetre-wave radar, ultrasonic
Backing, lane change and merge
Lane position monitor
Laser radar, video, passive reflected light detector
Road departure, opposite direction
In-vehicle signing Video, infrared communications, microwave
Road departure, opposite direction, intersection, and crossing path
Gap acceptance aid
Video Intersection and crossing path
Vision enhancement Video, infrared communications, microwave transponder Reduced visibility
Table 2. Collision avoidance strategies and preventable crash types that are supported by vehicle-mounted sensors [4].
CAS can be divided into two basic categories: • Object detection systems
• Collision warning systems.
Each system is described in detail below.
2.2.1.1
Object Detection Systems
Object detection systems (ODS) are intended to monitor the area within close proximity of the vehicle (e.g., up to 3m) and provide a visual or audible warning when an object is detected near the vehicle. Given this small proximity, ODS are sometimes considered an “enhancement” to the driver’s mirror. These systems can detect the presence of an object but not its distance or relative speed. In Figure 4, ODS are represented by the circular shaped areas. They are defined as follows [2]:
• Forward Object Detection System (FODS) – As shown by the gray/light blue-shaded area, FODS monitors the area in front of a vertical plane intersecting the front bus wheels (the area within the forward view of the driver).
• Side Object Detection System (SODS) – As shown by the dark green area, SODS monitors the area behind the vertical plane intersecting the front bus wheels. It does not include the area behind the vehicle, only the area from the front wheels, down the side of the bus, to the rear bumper.
• Rear Collision Warning System (RODS) – As shown by the dark blue area, RODS monitors the area directly behind the vehicle.
2.2.1.2
Collision Warning Systems
Collision warning systems (CWS) monitor distances further away from the vehicle (up to 150m) and warn the driver of impending collisions. Algorithms use distance and relative speed information supplied by the detection sensors to calculate the time to contact a detected object, and then provide the driver with visual or audible warnings that increase in intensity as the time to contact approaches zero. The systems will provide warnings to the driver as vehicles/objects enter the field of view, or as the vehicle approaches a fixed object.
Figure 4 illustrates the different type of CWS with triangular shapes. They include the following [2]:
• Forward Collision Warning System (FCWS) – Shown in yellow, FCWS uses forward-looking sensors and warns the driver of the “Time to Contact” with a vehicle in the driver’s lane. Forward sensors are situated in the front of a vehicle with a widening view as they scan farther ahead.
• Rear Collision Warning System (RCWS) – Shown in red, RCWS warn the driver of an approaching vehicle of a rear-end collision. The warning is an
UBM
external indicator on the back of the equipped bus that alerts the driver in the approaching vehicle. (The driver of the equipped vehicle is not alerted of the impending collision.)
• Lane Departure Warning Systems (LDWS) – As shown by the green area, LDWS are camera-based systems that monitor lane markings. Together with object recognition software and algorithms that compute closing distance, LDWS provide warnings when a lane or road edge departure is imminent via visual, audible, or tactile warning signals.
2.2.1.3
Pedestrian Detection System
Pedestrian detection systems (PDS) notify the vehicle operator of an impending collision with a pedestrian. The systems can be designed to provide cocoon or direction of travel coverage. Due to constraints with radar and Lidar sensors, video-based recognition accounts for the majority of technologies used to implement pedestrian detection. The systems use pattern recognition and optical flow techniques to differentiate between a pedestrian and an inanimate object. PDS detect pedestrians through a search of objects containing specific characteristics. The systems then separate a potential pedestrian from the background images. The software compares body ratios, specific size constraints, etc. to differentiate a non-human object from a pedestrian. A PDS has a normal range of 10 to 40 meters.
2.2.2
Intelligent Speed Adaptation
The concept of ISA was first brought forth in Sweden. ISA calls for vehicles to be “aware” of the prevailing speed limit on roads and (at minimum) provide feedback to the driver when that speed is being exceeded or (at maximum) limit the vehicle’s speed to comply with the speed limit.
ISA is a combination of technological systems that support drivers in their choice of travel speeds. The following types of ISA systems have been defined by researchers:
• Advisory ISA – systems that remind drivers of the prevailing speed limit and exert no control over the vehicle;
• Supportive ISA – systems that provide some degree of vehicle-initiated limiting of speed, but allows the driver to override the system;
• Limiting ISA – systems that include vehicle-initiated speed limiting that cannot be overridden (usually accompanied by an emergency failure function). For ISA to function as an intelligent unit, the vehicle must know which road it is on and in which direction it is travelling, and be able to compare this with information on applicable speed limits and current vehicle speed. Most ISA trials around the world have adopted the use of Global Positioning System (GPS) technology for vehicle location and a digital database of speed limit information provided within the vehicle.
2.2.3
Cooperative
Intersection
Collision
Avoidance
Systems (CICAS)
• Help drivers maneuver through cross traffic; • Inform other drivers about impending violations; • Identify pedestrians and cyclists within an intersection. CICAS rely on the following components:
• Vehicle-based components like sensors, processors and driver interfaces. • Infrastructure-based components such as roadside sensors, processors and
messaging signs.
• Communication systems notably DSRC and the future IEEE 802.11p standard.
2.2.4
Cooperative Approaches for Vulnerable Road Users
The objective for these approaches is to improve the safety of vulnerable users based on:
• Enhanced autonomous on-vehicle sensors (based on laser, microwave and computer vision technologies);
• Co-operative means carried by the vulnerable road users (transponders, microwave/optical reflectors, etc.).
Several EU research projects have addressed this issue, notably: • PROTECTOR1 (Preventive safety for un-protected road user);
• WATCH-OVER2 (Vehicle-to Vulnerable road user cooperative communication
and sensing technologies to improve transport safety);
• SAFE-U3 (Sensors and system Architecture for VulnerablE road Users
protection) ;
• SAFESPOT4 (Cooperative Systems for Road Safety).
2.2.5
Traffic Flow Improvement
Traffic congestion has a pervasive effect on society. For example, with the public driving 1,900 million vehicle hours on a daily basis, losses to the German economy due to congestion have been estimated at 250 million Euros. A total of 18% of this travel is spent within stop-and-go conditions. In 1998, 2% of the routes were permanently congested and 17% were marginal. Future extrapolations show increases by as much as 351% by 2015. Figures from the United States are equally compelling—the annual financial cost of traffic congestion is $63 billion for the 85 largest cities, with annual delay per rush hour traveller at 46 hours. Each year, an estimated 5.6 billion gallons of fuel is wasted by engines idling in traffic jams [6]. Several approaches exist for improving the traffic flow, notably:
• Adaptive Cruise Control (ACC) can affect the stability of the traffic flow based on the dynamic response characteristics of the longitudinal control algorithms. Several implementations exist:
o Autonomous ACC controls time gaps based on sensing the vehicle ahead; 1http://cordis.europa.eu/data/PROJ_FP5/ACTIONeqDndSESSIONeq112422005919ndDOC eq1850ndTBLeqEN_PROJ.htm 2 http://www.watchover-eu.org/ 3 http://www.save-u.org/
UBM
o Responsive ACC must receive speed commands from a traffic operations centre;
o Cooperative ACC allows exchanging vehicle parameters (position, velocity, acceleration, heading) between the vehicle being tracked and the host vehicle. Figure 5 illustrates the benefits of Cooperative ACC compared to Autonomous ACC.
• A close headway operation via platooning is an approach that allows exchanging vehicle parameters along a string of vehicles, not just with the one ahead, using a “platooning” technique. This approach requires very fast update rates and low latencies. It offers a potential per-lane flow of about 6000 vehicles/lane/hour, which is about a three-fold increase of today’s traffic.
Figure 5. Relative effects on lane capacity [5].
3 Conclusions
Both the promise and the complexity of CDS can be deduced from this rather lengthy chapter. The main messages regarding CDS are the following:
• CDS can improve the performance of the entire road-vehicle system in terms of both safety and traffic performance.
As the Internet opened up new worlds, bringing vehicles into the connected society will open up a vast array of new services and features for vehicle owners, driven by entrepreneurial creativity and market forces. With our vehicles exchanging information and using highly accurate digital maps, our travel will be safer and more precise. The final “gap” in the wireless world will be bridged.
4 References
[1] Loke S., “Context-Aware Pervasive Systems - Architectures for a New Breed of Applications”, Auerbach Publications, 2007.
[2] Dunn T., R. Laver, D. Skorupski, D. Zyrowski, “Assessing the Business Case for Integrated Collision Avoidance Systems on Transit Buses”, August 2007, Federal Transit Administration, U.S. Department of Transportation.
[3] Najm, W.G. “Comparison of Alternative Crash Avoidance Sensor Technologies,” Proceedings, SPIE, vol. 2344. Bellingham, WA. 1994. pp. 62–72.
[4] Klein L. A., M. K. Mills, D. R.P. Gibson, “Traffic Detector Handbook”, Third Edition – Volume 1, Publication No. FHWA-HRT-06-108, October 2006, Federal Highway Administration.
[5] Bishop R., “Intelligent Vehicle – Technology and Trends”, Artech House, 2005. [6] “2004 Urban Mobility Report,” Texas Transportation Institute.
[7] Albert, S., “National Automated Highway System Consortium/Caltrans Greater Yellowstone Rural AHS Case Study,” synopsized inWestern Transportation Institute Newsletter, Volume 8, No. 2, September 2004.
[8] Akman, V., Context in Artificial Intelligence: A Fleeting Overview (English version of Contesti in intelligenza artificiale: una fugace rassegna), in Penco, C., Ed., La Svolta Contestuale, McGraw-Hill, Milano, 2002.
[9] Bouquet, P., Ghidini, C., Giunchiglia, F., and Blanzieri, E., Theories and uses of context in knowledge representation and reasoning, Journal of Pragmatics, 35(3), 455–484, 2003, Elsevier Science.
[10] McCarthy, J., Notes on formalizing contexts, in Ruzena Bajcsy, Ed. Proceedings of the 13th International Joint Conference on Artificial Intelligence, Morgan Kaufmann, San Mateo, CA, 1993, pp. 555–560.
[11] Brezillon, P., Representation of procedures and practices in contextual graphs, The Knowledge Engineering Review, 18(2), 147–174, 2003, Cambridge University Press.
[12] Schilit, B.N., Adams, N.I., and Want, R., Context-aware computing applications, in Proceedings of the Workshop on Mobile Computing Systems an Applications, December, 1994, IEEE Computer Society, pp. 85–90.
[13] Schilit, B.N., A System Architecture for Context-Aware Mobile Computing, Ph.D. thesis, Columbia University, 1995.
[14] Dey, A.K., Understanding and using context, Personal and Ubiquitous Computing Journal, 5(1), 5–7, 2001.
[15] Picard, R.W., Affective Computing, MIT Press, 1997.
[16] Lehmann, O., Bauer, M., Becker, C., and Nicklas, D., From home to world — supporting context-aware applications through world models, in Proceedings of the 2nd IEEE Annual Conference on Pervasive Computing and Communications
(PERCOM’04), IEEE Computer Society, 2004.
[17] Muhlenbrock, M., Brdiczka, O., Meunier, J.-L., and Snowdon, D., Learning to detect user activity and availability from a variety of sensor data, in Proceedings
UBM
of the 2nd IEEE Annual Conference on Pervasive Computing and Communications (PERCOM’04), IEEE Computer Society, 2004.
[18] Koile, K., Tollmar, K., Demirdjian, D., Shrobe, H., and Darrell, T., Activity zones for context-aware computing, in Proceedings of the 5th International Conference on Ubiquitous Computing (UBICOMP 2003), 2003.
[19] Tapia, E.M., Intille, S.S., and Larson, K., Activity recognition in the home using simple and ubiquitous sensors, Pervasive 2004, LNCS 3001, Springer-Verlag, Germany, 2004, pp. 158–175.
[20] Chen, H., Finin, T., and Joshi, A., An ontology for context-aware pervasive computing environments, The Knowledge Engineering Review (special issue on Ontologies for Distributed Systems) 18(3), 197–207, 2004.
[21] McGrath, R.E., Ranganathan, A., Campbell, R.H., and Mickunas, M.D., Use of Ontologies in Pervasive Computing Environments, Technical Report, UIUCDCS-R-2003-2332 ULU-ENG-2003-1719, April 2003
[22] Wang, X.H., Gu, T., Zhang, D.Q., and Pung, H.K., Ontology based context modeling and reasoning using OWL, in Proceedings of the Workshop on Context Modeling and Reasoning (CoMoRea’04) at the 2nd IEEE International Conference on Pervasive Computing and Communications, IEEE Computer Society Press, 2004.
[23] Matheus, C., Kokar, M., and Baclawski, K., A core ontology for situation awareness, in Proceedings of FUSION, July 2003, pp. 545–552, available at http://vistology.com/papers/FUSION03.pdf.
[24] Katsiri, E. and Mycroft, A., Knowledge representation and scalable abstract reasoning for sentient computing using first-order logic, in Proceedings of the Challenges and Novel Applications for Automated Reasoning (CADE-19 Workshop), July 2003, available at http://www.cl.cam.ac.uk/~am21/papers/nads03.pdf.
[25] Ranganathan, A. and Campbell, R.H., An infrastructure for context-awareness based on first order logic, Personal and Ubiquitous Computing Journal, 7, 353– 364, 2003.
[26] Peters, S. and Shrobe, H.E., Using semantic networks for knowledge representation in an intelligent environment, in Proceedings of the 1st IEEE Annual Conference on Pervasive Computing and Communications (PERCOM’03), 2003, IEEE Computer Society, Washington, D.C., pp. 323–329. [27] Saha, D. and Mukherjee, A., Pervasive computing: a paradigm for the 21st
century, IEEE Computer, 25–31, 2003.
[28] Brown, P.J. and Jones, G.J.F., Context-aware retrieval: exploring a new environment for information retrieval and information filtering, Personal and Ubiquitous Computing Journal 5(4), 253–263, 2001.
[29] Rhodes, B., The wearable remembrance agent: a system for augmented memory, Proceedings of the 1st International Symposium on Wearable Computers, Cambridge, MA, 1997, pp. 123–128.
[30] Abowd, G., Atkeson, C., Hong, J., Long, S., Kooper, R., and Pinkerton, M., Cyberguide: a mobile context-aware tour guide, ACM Wireless Networks 3, 421–433, 1997.
[31] Fitzpatrick, A., Biegel, G., Clarke, S., and Cahill, V., Towards a Sentient Object Model. Position Paper Workshop on Engineering Context-Aware Object Oriented Systems and Environments (ECOOSE), Seattle WA, November 2002, available at http://www.dsg.cs.tcd.ie/~biegelg/research/publications/biegel-som.pdf.
[32] Biegel, G. and Cahill, V., Sentient Objects: Towards Middleware for Mobile Context-Aware Applications. European Research Consortium for Informatics and Mathematics, ERCIM News No. 54, July 2003.
[33] Vidales, P. and Frank Stajano, F., The sentient car: context-aware automotive telematics, Proceedings of First IEEE European Workshop on Location Based Services (LBS-2002), London, also appeared as a poster at Ubicomp 2002. [34] Shafer, S., Brumitt, B., and Cadi, J.J., Interaction Issues in Context-Aware
Intelligent Environments. Human Computer Interaction 16(2–4), 2001.
[35] Bardram, J., Applications of context-aware computing in hospital work — examples and design principles. Proceedings of SAC ’04, March 14–17, Nicosia, Cyprus, 2004, pp. 1574–1579.
[36] Jin, L. and Miyazawa, T., MRM server: a context-aware and location-based mobile e-commerce server, Proceedings of the 2nd International Workshop on Mobile Commerce, USA, 2002, ACM Press, pp. 33–39.
[37] van der Poel, B., Context-Aware Rule-Based Data Distribution Algorithms and Methods for Pervasive Computing. M.Sc. thesis, Delft University of Technology, August 2002.
[38] Roxin, A., Wack, M., Location Models for Pervasive Road Networks, Journal of International Transactions on Systems Science and Applications, 2008, 4 (1), ISSN 1751-1461.

![Figure 4. Diagram of Collision Avoidance System [2].](https://thumb-eu.123doks.com/thumbv2/123doknet/12783173.361566/13.892.155.766.377.604/figure-diagram-collision-avoidance.webp)
![Table 2. Collision avoidance strategies and preventable crash types that are supported by vehicle-mounted sensors [4]](https://thumb-eu.123doks.com/thumbv2/123doknet/12783173.361566/14.892.150.777.125.233/collision-avoidance-strategies-preventable-supported-vehicle-mounted-sensors.webp)
![Figure 5. Relative effects on lane capacity [5].](https://thumb-eu.123doks.com/thumbv2/123doknet/12783173.361566/17.892.174.731.357.865/figure-relative-effects-lane-capacity.webp)