Investigation of tool geometry effect and penetration strategies on cutting forces during thread milling
Texte intégral
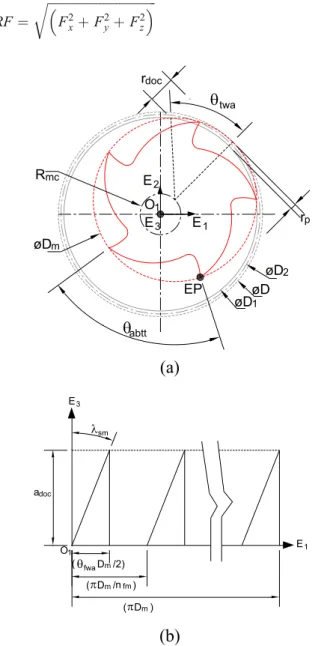
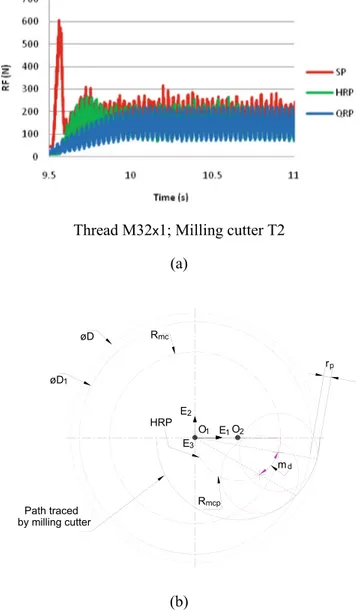
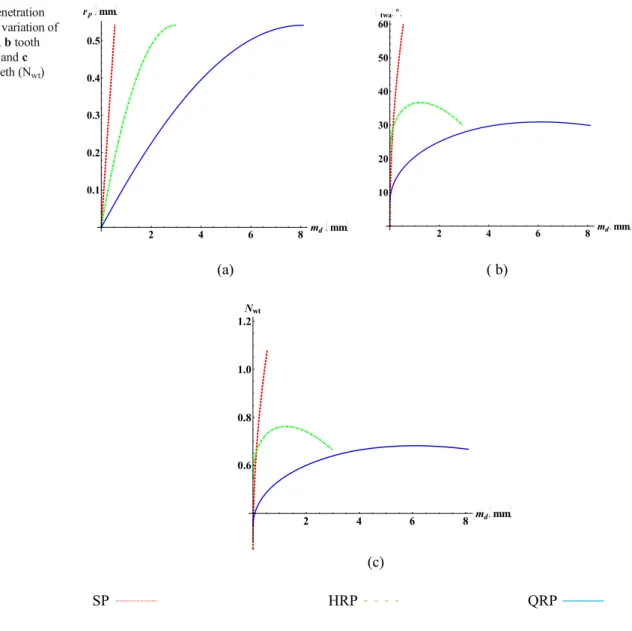
Figure

Documents relatifs
This is done by observing the plas- moids using data from the Cluster spacecraft; tracing their motion deeper into the magnetosphere from one spacecraft to the next; using
In this chapter we’ve managed to cover a lot of ground very quickly just by using publicly available sources and port scanners. We used tools such as theHarvester and Maltego to
Nevertheless, compared to prominent attacks such as SQL-Injection or Cross-site scripting (XSS), there is currently no penetration test tool that is capable of analyzing the security
• Evaluation with more than 5000 apps, thus demonstrating its accuracy. • Able to daily validate ail apps deployed on Google Play or Apple App Store... ABSTRACT
مﻟ ءﺎﯾﺑﻧﻷا نإ و ، ءﺎﯾﺑﻧﻷا ﺔﺛرو ءﺎﻣﻠﻌﻟا نإ ﱢروﯾ ًارﺎﻧﯾد اوﺛ ًﺎﻣﻫرد ﻻ و ﱠﻧإ ﱠرو ﺎﻣ ﱢظﺣﺑ ذﺧأ ﻪﺑ ذﺧأ نﻣﻓ مﻠﻌﻟا اوﺛ رﻓاو { 1 ﱠنإ دوﻣﻋ وﻫ مﻠﻌﻟا مﻣﻷا
Narratives and Traces: “ Trans-” Quantitative and Qualitative Meth- ods for Bridging the Gap between Objective and Subjective Data.. Bulletin de Méthodologie Soci- ologique /
He provides an excellent classification of assessment procedures by delineating assessment into empirical, psychometric, and intui- tive components (p.. He then examines
Information security assessment is the process of determining the effectiveness of security measures to reach specific security objectives?. The assessment is usually performed
