Light Cryptography
Texte intégral
Figure



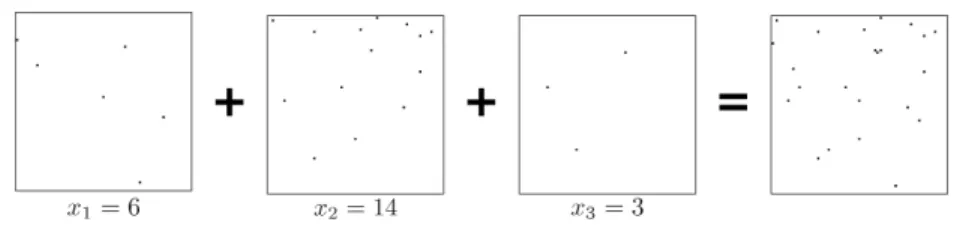
Documents relatifs
Enryption : The proess of obsuring information to make it unreadable without spe-.. ial knowledge, key les,
Specifically, we first define one-time signature schemes, next define a length-restricted version of this notion (analogous to Definition 6.2.1), then present a simple construction
INstruction N°240/DG/DGFP/du 27 mai 1995 relative au modalité d’applicatin des dispos tins du exécutif n° 95-12 du 29avril 1995modifiantet complétant le décret
In several previous papers, ending with the work of Rota and Taylor, a rigorous foundation for the umbral calculus was given.. Two umbrae a and a’ are said to be
The technique was used to solve the code equivalence problem for Reed-Muller codes [MS07], Polar codes [BCD + 16, Dra17], QC-LDPC codes [OTD08], a variant of the McEliece scheme
Three dispersive horizons are derived by cancelling the group velocity for white hole type flows (the incoming waves propagates on a counter current in the stimulated regime): the
[7] Franceschetti G, Iodice A, Migliaccio M and Riccio D 1999 Scattering from natural rough surfaces modeled by fractional Brownian motion IEEE Trans.
Purely visual objects created by colour spreading are expected to behave like any other physical object.. In particular, they are expected to block light and to