Visualization of Mouse Neuronal Ganglia Infected by Herpes Simplex Virus 1 (HSV-1) Using Multimodal Non-Linear Optical Microscopy
Texte intégral
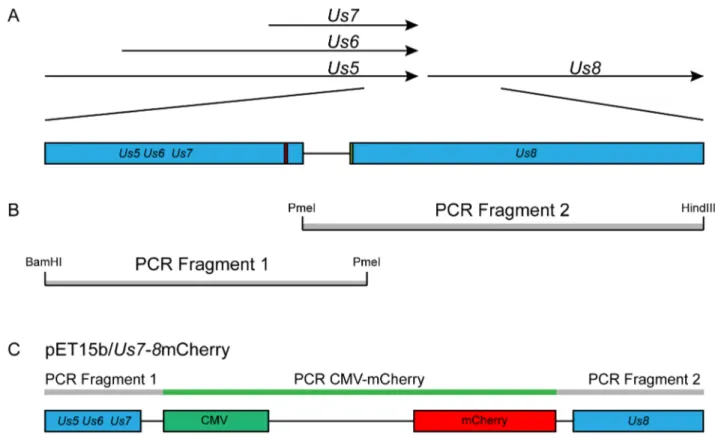
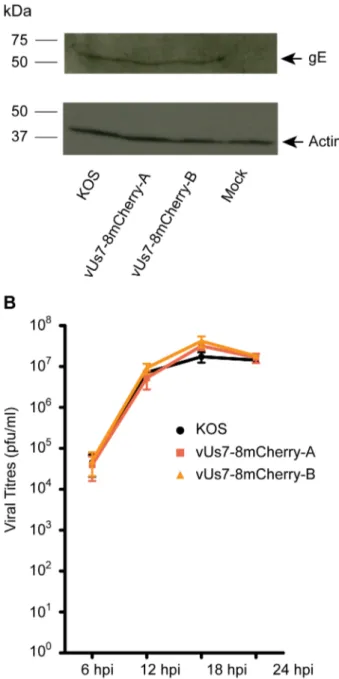
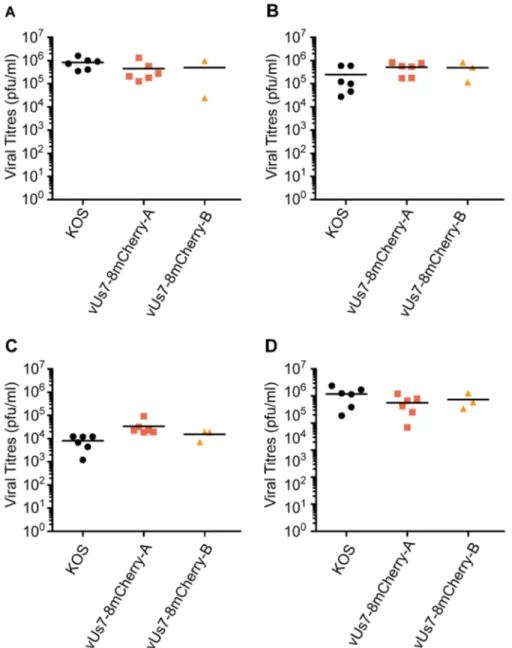
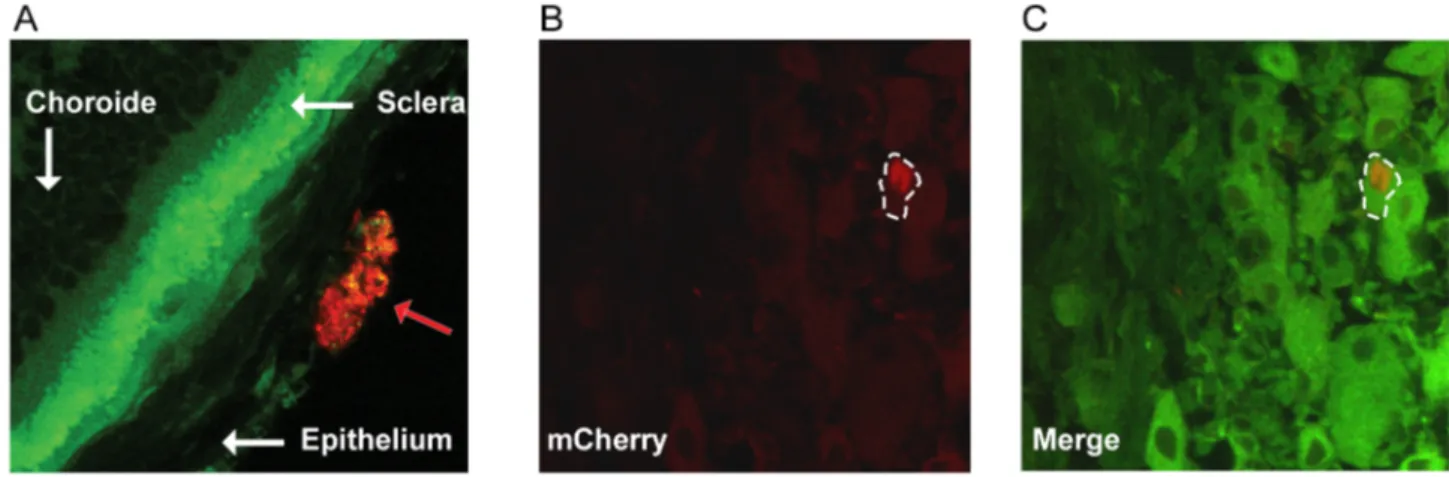
Figure
Documents relatifs
The ability to employ both label and label ‐ free imaging on peritoneum tissue, carcinoses nodules, vascular stent in aorts or fibrosis, that are complex medical samples, will
(j, k) Axial reconstruction of MPM images combining SHG (green), revealing plaster particles and wood cellulose, and 2PEF (red) in two spectral bands: (j) around 485 nm,
Laboratoire interdisciplinaire de Physique B.P. This simple and efficient technique using frequency-shifted optical feedback needs the sample to be scanned in order to obtain
‘deep-OCM’) of a high-numerical aperture infrared full-field optical coherence microscope, which includes aberration correction for the compensation of refractive index mismatch and
Vero cells and viruses were in- cubated with extracts at different stages of the viral infection to determine the mode of antiviral activity such as protection, absorption,
Column 1 shows the fixed TRUS images, column 2 shows the moving MR images, columns 3 − 4 show the registration results in terms of transformed MR images and checker-board using TPS
ا مﺳﻘﻧ يرطﯾﺗﻟا كﻠﯾﺎﺑو يزﻛرﻣﻟا مﻛﺣﻟا رﻘﻣ نﯾﺑ طﺑارﻟا قﯾرطﻟا اذﻫ إ ﻰﻟ 12 ﺔﻠﺣرﻣ ﺔﻌﺑرأ نﯾﺑ ﺎﻣ قرﻐﺗﺳﺗ ﻰﻟإ ا ﺔﻠﺣﻣ تﻧﺎﻛ ﺔﻠﺣرﻣ لﻛ ﻲﻓو ،رﯾﺳﻟا نﻣ مﺎﯾأ ﺔﺳﻣﺧ ﻹ
The fourth and last class contains trust-region methods (see e.g. Powell [25] and Conn, Scheinberg and Toint [8]), in which all available function values are used to build a