Cloud Security and Platform Thinking: An analysis of Cisco
Umbrella, a cloud-delivered enterprise security
by
Apoorva Parikh
B.E. Electronics Engineering, National Institute of Technology, University of Allahabad, India 2002 MBA, Said Business School, University of Oxford, UK, 2009
Submitted to the System Design and Management Program in Partial Fulfillment of the Requirements for the Degree of
Master of Science in Engineering and Management at the
Massachusetts Institute of Technology
February 2019
@ 2019 Apoorva Parikh. All rights reserved.
The author hereby grants to MIT permission to reproduce and to distribute publicly paper and electronic copies of
this thesis document in whole or in part in any medium now known or hereafter created.
Signature redacted
Signature of A uthor...
MIT System Design and Management January 31, 2019
C ertified by ...
...
Signature redacted
...
(I Michael A. Cusumano
Sloan Management Review Distinguished Professor of Management Thesis Supervisor
Signature redacted
A c c e p te d b y ... . . . . -- - - - - -- - - -- - - - - ...--
MASSACHUSETTS INSTITUTE I Joan S. Rubin
OF TECHNOLOGY Executive Director, System and Management Program
MAR
14 2019
LIBRARIES
This page is intentionally left blank
Cloud Security and Platform Thinking: An analysis of Cisco
Umbrella, cloud-delivered enterprise security
by
Apoorva Parikh
Submitted to the MIT System Design and Management Program on January 31, 2019 in Partial Fulfillment of the Requirements for the Degree of Master of Science in Engineering and
Management
Abstract
Cisco's security business segment with over $2 billion in revenue in fiscal 2018, makes Cisco one of the largest enterprise security players in the market. It is also one of the fastest growing business segments for Cisco, with last five years' CAGR at 12%. While this growth rate is in line with the estimated CAGR for cybersecurity market growth between 2018 - 2022, another leading incumbent's growth rate shows there is an opportunity to grow even faster. What can Cisco do to accelerate its security business group's growth and, more broadly, how can Cisco maintain its leadership position in a rapidly evolving and highly fragmented cybersecurity market?
The goal of this thesis is two folds: first, is to discover the emerging cybersecurity needs for enterprises under the dynamic threat landscape in mobile, cloud-era, and the resultant growth opportunities and challenges these present to Cisco's security business group. Second, is to discover the main elements of Cisco security business group's current growth strategies and to evaluate platform thinking as a potential growth strategy for Cisco's Cloud Security business. We find Cisco Umbrella, a recently launched cloud security offering exhibits potential to become a foundation for Cisco Cloud Security as an open platform ecosystem. We conclude by discussing a potential future platform direction for Cisco Umbrella and raise follow-on questions for further consideration.
Thesis Supervisor: Michael A. Cusumano
Title: Sloan Management Review Distinguished Professor of Management
This page is intentionally left blank
Acknowledgements
To my best friend (and spouse) Ujjayini -for your love, support and partnership in this adventure!
As I conclude this journey at MIT, I feel an overwhelming sense of gratitude. First, to be a part of MIT System Design and Management (SDM) program, where I was introduced to 'What is a platform?' at the core lectures by Prof. Michael A. Cusumano and Dr. Bruce G. Cameron. And then to have an opportunity to spend a summer with Cisco's strategy team, both of which have inspired this thesis.
I would like to thank Cisco Strategy and Security business group teams for their encouragement
and support throughout the research and writing of the thesis. Specifically, to Brian Roddy for brainstorming potential directions of research, and Todd Graham to champion my cause and be a sounding board to the initial ideas. A special thank you to John Amaral, who has been a great mentor and my 'go-to' subject matter expert on cloud security.
Most of all, I would like to thank my thesis advisor, Prof. Michael A. Cusumano, for inspiration, guidance and mentorship on platform thinking and how technology firms create sustainable competitive advantage through platform strategy.
A big thank you also to - Anthony Bettini at Tenable, Chris Wysopal at Veracode, Nishant Doshi, Palo Alto Networks, Harold Moss at Akamai, Sam Curry at CyberReason, Frank Wang at Dell Technologies Capital, and Raphael Yahalom at MIT - for insightful discussions to validate my understanding of evolution of cybersecurity to its current state and for your expert views on future direction shaping -internet, threat landscape and cybersecurity.
This page is intentionally left blank
Contents
Abstract...3
Acknowledgem ents ... 5
List of figures...8
1 Introduction... 9
1.1 M otivation and relevance: Why now?... 9
1.2 Research Questions ... 12
1.3 Research approach ... 13
1.4 Platforms and the method to Platform thinking ... 13
1.5 Structure of the thesis... 19
2 Evolution of cybersecurity (1970s - 2000s)... 21
2 .1 O v erv iew ... 2 1 2.2 1970s - 1980s: Emergence of Internet, unsecure by design ... 24
2.3 1990s: The dawn of cybersecurity ... 28
2.4 2000s: Securing network perimeter against institutionalized cyber attacks... 32
3 Cybersecurity: current state and emerging needs ... 38
3.1 2010s - Present: Disappearing network perimeter and emergence of Cloud Security...38
3.2 Equifax Hack: An example of current state of challenges ... 45
3.3 Future direction and emerging needs: A summary of industry expert interviews ... 50
4 Enterprise platform strategy case studies and platform approach to cybersecurity...54
4 .1 O v erv iew ... 54
4.2 Enterprise software platform success case study: Salesforce.com ... 55
4.3 Emergent directions in cybersecurity vendors: platform and cloud... 64
4.4 W hat would a cybersecurity platform look like?... . . . . .. . . .. . . .. . . .. . . . .. . . . 74
5 Applying platform thinking to Cisco Cloud Security ... 78
5.1 Cisco - company background and strategy... 78
5.2 Security is one of the key growth drivers for Cisco... 82
5.3 Vision for Security business ... 86
5.4 Cisco Umbrella - foundation for Cisco cloud security platform ... 88
5.5 Cisco Umbrella - current platform strategy... 91
6 Conclusion ... 97
List of figures
# Figure
Pg.
1 Figure 1.1 - Cybersecurity vendors ratings, Survey by ESG, 2017 12
2 Figure 1.2 - Airbnb co-founder Brian Chesky's tweet 14
3 Figure 1.3 - Dilbert on Platform 15
4 Figure 1.4 - Ycombinator co-founder Paul Graham's tweet on overuse of the word 'Platform' 15
5 Figure 1.5 - Four strategic platform challenges 17
6 Figure 1.6 - Key questions to assess each of the four strategic platform challenges 18
7 Figure 1.7- 'Coring' and 'Tipping' platform strategies 19
8 Figure 2.1 - WannaCry infections across the world and example business impacts 21
9 Figure 2.2 - The Morris Worm source code on display (Intel Free Press) 22
10 Figure 2.3 - Evolution of Cybersecurity 23
11 Figure 2.4 - A plaque at Rossoti's (Image credit: Alpine Beer Garden) 25 12 Figure 2.5 - Image capture of original BGP design (three napkin protocol) found on Network 27
Collective Podcast with Toni Li
13 Figure 2.6 - Enterprise Computing era 1990s 29
14 Figure 2.7 - Unprotected network vs. network protected by firewall (zone of risk limited to 31
firewall)
15 Figure 3.1 - 2000s vs. 2010s IT evolution: Dissolving of Network Perimeter 39
16 Figure 3.2 - Zero Trust concept- identity centric security 44
17 Figure 3.3 Timeline of Equifax breach 46
18 Figure 4.1 - Salesforce platform vs. product revenue 56
19 Figure 4.2: Salesforce Platform Architecture 58
20 Figure 4.3 illustrates a few network effects from Coring and Tipping 59
21 Figure 4.4 - Platform war: Microsoft, Adobe and SAP for coalition to compete against Salesforce 63
22 Figure 4.5 Palo Alto Networks' Security Operating Platform 66
23 Figure 4.6 Threat Intelligence Cloud 67
24 Figure 4.7 Logging Service 67
25 Figure 4.8 - Key uses cases supported by the Application Framework 68
26 Figure 4.9 -Zscaler direct to cloud security and access 72
27 Figure 4.10: Zscaler technology integrations 73
28 Figure 4.11 -Potential industry-wide platform architecture for Cybersecurity 75
29 Fig 5.1: Cisco quarterly revenue vs. growth - Q4 2015 to Q1 2019 and recurring software 82
subscription indicator
30 Figure 5.2 - Cisco security revenue - last 5 years 83
31 Figure 5.3 - Need for integration and architectural approach to cybersecurity 84
32 Figure 5.4 - Vendor consolidation sentiment for cybersecurity 84
33 Figure 5.5 - Revenue multiples vs. growth for select cybersecurity vendors (Bubble indicates 85 market cap)
34 Figure 5.6 - Cisco cybersecurity vision evolution 86
35 Figure 5.7 - snapshot from opening keynote of Cisco Live in Barcelona, Jan 29, 2019 88
36 Figure 5.8: High level conceptual overview of Umbrella platform 92
37 Figure 5.9 - OpenDNS - enforcing security at DNS layer 95
38 Figure 5.10 - Mapping Cisco Umbrella as a potential industry-wide platform (to fig 4.11) 95 39 Figure 6.1 - Illustrative example of extending Cisco Umbrella as an open ecosystem cloud 99
1
Introduction
The topic of this thesis is - Cloud Security and Platform Thinking: An analysis of Cisco Umbrella, cloud-delivered enterprise security. This chapter includes the motivation and relevance of the topic, the key research questions and the approach to find answers to the research questions, as well as the structure of the rest of the thesis.
1.1 Motivation and relevance: Why now?
CYBER THREATS ARE INCREASINGLY MORE DAMAGING, POINT-BASED SECURITY SOLUTIONS
ARE NOT SUFFICIENT
"To date, it was simply the fastest-propagating piece of malware we've ever seen. By the second
you saw it, your data center was already gone. "i' Craig Williams, Director at Cisco Talos Outreach
According to an article covered in Wired.com, on the afternoon of June 27, 2017, confused Maersk (the world's largest shipping conglomerate) staffers began to gather at that help desk in twos and threes, almost all of them carrying laptops. On the machines' screens were messages in red and black lettering. Some read "repairing file system on C:" with a stark warning not to turn off the computer. This was the attack of NotPetya, a malware whose goal was purely destructive. It irreversibly encrypted computers' master boot records, the deep-seated part of a machine that tells it where to find its own operating system. Any ransom payment that victims tried to make was futile. No key even existed to reorder the scrambled noise of their computer's contents. The result was more than $10 billion in total damages, according to a White House assessment. WannaCry, the more notorious worm that spread a month before NotPetya in May 2017, is estimated to have cost between $4 billion and $8 billion.2
In an increasingly connected and digital world, cyber threats such as NotPetya, WananCry, Petya, et al, are causing substantial financial and infrastructure damage globally. As noted in The WSJ article by Alan Brill, the Senior Managing Director at Duff & Phelps, "NotPetya was really there
' Article - The Untold Story of NotPetya, The Most Devastating CyberAttack in History, Wired (Aug, 2018) Available at: https://www.wired.com/story/notpetya-cyberattack-ukraine-russia-code-crashed-the-world/
2 Article - The Untold Story of NotPetya, The Most Devastating CyberAttack in History, Wired (Aug, 2018)
to cause irreparable damage and make your data permanently unavailable. Anybody who thinks this kind of thing couldn't happen again is naive".3
Little wonder, according to a recent McKinsey survey, 75 percent of experts consider cybersecurity to be a top priority.4 And a recent study from Accenture says, two-thirds of CEOs and boards now have direct oversight of cybersecurity. 5 Gartner forecasts that by 2020, more than 60 percent of organizations will invest in multiple data security tools such as data loss prevention, encryption and data-centric audit and protections tools, up from approximately 35 percent today.6 While demand for best of breed continues, integrating various cybersecurity products and technologies is now a central factor in purchasing decisions. A recent research report from the Enterprise Strategy Group (ESG) reveals that organizations are actively building architecture to support such
integrations.7
LEADING TECHNOLOGY PLAYERS HAVE STARTED THINKING IN THE DIRECTION OF
PLATFORMS
Rick Howard, the chief security officer for Palo Alto Networks, a leading network security company believes the future of cybersecurity is all about the platform, and that the cyber- security consumption model will be disrupted by orchestration and automation in the cloud. 8
Rick is not alone to envision the 'platformization' direction for cybersecurity. Eric Troup, CTO for WorldWide Communications and Media Industries at Microsoft holds a similar viewpoint, that security and privacy must be embedded throughout and platforms are increasingly key to
3 Article - One year after NotPetya CyberAttack, Firms Wrestle with Recovery Costs, The Wall Street Journal (Jun, 2018) Available at:
https://www.wsj.com/articles/one-year-after-notpetya-companies-still-wrestle-with-financial-impacts-1530095906
' Article -A new posture for cybersecurity in a networked world, McKinsey (Mar, 2018) Available at:
https://www.mckinsey.com/business-functions/risk/our-insights/a-new-posture-for-cybersecurity-in-a-networked-world
I Report - 2018 State of Cyber Resilience, Accenture Security (Apr, 2018) Available at https://www.accenture.com/us-en/insights/security/2018-state-of-cyber-resilience-index
6 Press Release - Gartner (Dec, 2017). Available at https://www.gartner.com/newsroom/id/3836563
7 Research Report, ESG, Jon Oltsik, 'The Shifting Cybersecurity Landscape', (Apr 2017), Available at: https://www.esg-global.com/research/esg-research-report-the-shifting-cybersecurity-landscape
8 Article - Insight by Palo Alto Networks, Federal News Network (July, 2017) Available at
https://federalnewsnetwork.com/innovation-in-government/2017/07/the-future-of-cybersecurity-is-all-about-the-platform/
cybersecurity.' Stephen Gillet, CEO and co-founder of Chronicle, a new Alphabet (Google's parent) business dedicated to cybersecurity, argues that the proliferation of data from the dozens of security products that a typical large organization deploys is paradoxically making it harder, not easier, for teams to detect and investigate threats. As a result, it is pretty common for hackers to go undetected for months, or for it to take a team months to fully understand what's going on once they've detected an issue. All this adds up to more data breaches, more damage, and higher security costs. His team at Chronicle (founded in 2016), believes there is a better way to cybersecurity, by building intelligence and analytics platform to solve the problem.1 0
OPPORTUNITY FOR CISCO
Cybersecurity market is huge. Research firm IDC estimates security solutions spending will hit
$92 billion in 2018 and continue to grow at CAGR of 10% to reach over $130 billion by 2022.11
Cisco is well positioned to capture this massive market. Today, Cisco is one of the largest cybersecurity companies by revenue, with FY 2019 run-rate cybersecurity revenue of $2.6 billion
(Qi 2019 at $651 million'2) (-11% growth over $2.3 billion revenue in FY 201813). According to the research firm ESG, Cisco tops the mindshare of the organizations for enterprise-class cybersecurity (offering that includes leading integrated products, central management, professional/managed services, etc.), beating some of the largest pure play cybersecurity vendors
such as Symantec and Check Point Software. See figure Figure 1.1 below.
9 Blog - Growing role of Platforms in Cybersecurity, Microsoft (Mar, 2017) Available at https://blogs.msdn.microsoft.com/etblog/2017/03/27/growing-role-of-platforms-in-cybersecurity/
'0 Blog - Give Good the Advantage, Introducing Chronicle, a new Alphabet business dedicated to cybersecurity, Medium (Jan, 2018) Available at https://medium.com/chronicle-blog/give-good-the-advantage-75ab2c242e45
" IDC Spending Guide Forecasts WorldWide Spending on Security..., IDC (Oct, 2018) Available at
https://www.idc.com/getdoc.jsp?containerld=prUS44370418
12 Cisco - QI FY 2019 Revenue Highlights (Nov, 2018) Available at https://investor.cisco.com/investor-relations/overview/default.aspx
3 Annual report FY 2018, Cisco (Oct, 2018) Available at
https://www.cisco.com/c/dam/en-us/about/annual-report/2018-annual-report-full.pdf *h*
Please rate the following vendors-regardless of whether or not your organization currently uses their products or services-with respect to the breadth of their cybersecurity products and/or services designed for scale, integration, and to support business process requirements
of a large organization. (Percent of respondents, N=176)
* Enterprise-class cybersecurity vendor
Tactical provider of cybersecurity point tools and/or services * Don't know enough about this vendor to have an opinion
Cisco 3S%
IBM Security 36%
Microsoft 49%
Symantec (including Blue Coat) 48%
McAfee (formerly Intel Security)
Amazon Web Services (AWS) 59*1
Dell SecureWorks
Palo Alto Networks 52%
RSA Security 59%
Check Point Software 56%
Kaspersky FireEye 54% Fortinet 49% Trend Micro Forcepoint 45% Sophos - 56% Imperva Proofpoint 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100 Source: Enterprise Sr - '
Figure 1.1 - Cybersecurity vendors ratings, Survey by ESG, 2017 [71
The ESG research also emphasizes the need for clear definition and roadmap for a cybersecurity platform. More than half of research participants indicated that platform definitions provided by cybersecurity vendors have not been clearly conveyed or need more specifics.
Combined with the leading cybersecurity mindshare across enterprises large and small, and the depth and breadth of its cybersecurity capabilities (including cloud-delivered enterprise security Cisco Umbrella and recently acquired Duo Security, a leader in unified access security and multi-factor authentication), Cisco could as well become a thought leader in platformization of cybersecurity.
1.2 Research Questions
To assess the platform opportunity for Cisco Umbrella, this thesis focuses on three main questions: 1.
2.
What are the emerging cybersecurity challenges that the enterprises face today? What would an 'ideal' cybersecurity platform look like?
3. How should Cisco think about cloud security as a platform and platform as a growth
strategy?
1.3 Research approach
The broader understanding of the problem and the scope of this research is based on the interactions the author had with the strategy, product and engineering leads at Cisco during the summer. For further research and analysis, the author relies on the following methods:
i. literature review around Platform Thinking (books and management review papers and articles by Professors Michael Cusumano, David B. Yoffie, Annabelle Gawer, Andrei Hagiu, Simon Rothman, Sangeet Paul Chaudary, Geoffrey Parker and Marshall Van Alstyne),
ii. reviewing annual reports and presentations, product announcements, developer conferences' key takeaways, and technical papers from leading cybersecurity players
iii. Interviews and workshops with Cisco cloud security team
iv. Interviews with external key stakeholders, which include - subject experts at academia, research, engineering and strategy leaders at leading cybersecurity technology companies and expert investor in the field.
The main method employed for the thesis is described in the next section 1.4.
1.4 Platforms and the method to Platform thinking
PLATFORMS"Bill Gates got it immediately. It took Andy Grove 10 years to figure it out, and 20 years for Steve
Jobs."14
The famous quote in NYTimes book chat by David B. Yoffie, strategy professor at Harvard Business School, refers to what made Microsoft, Intel and Apple (after many years) such dominant
winners both in terms of market share and profits - "Building Platforms and Ecosystems ". In their
14 Article -Bill Gates, Andy Grove and Steve Jobs: The Strategies They Shared, NYTimes (May 2015) https://bits.blogs.nytimes.com/2015/05/12/bill-gates-andy-grove-and-steve-jobs-the-strategies-they-shared/?ref=technology
book, 'Strategy Rules', professors David B. Yoffie and Michael Cusumano, drive home the point -Bill Gates ability to quickly grasp the value of an "industry-spanning platform rather than merely products" was what made Microsoft a dominant PC player within a few years.1 5 Airbnb co-founder, Brian Chesky's famous tweet from 2014 [Figure 1.2] is another example showing how platforms grow and capture market share much faster than traditional industry businesses. 16 17
Brian Chesky* Follow
@bchesky
Marriott wants to add 30,000 rooms this year.
We will add that in the next 2 weeks.
8:11 PM - 10 Jan 2014285 Retweets 244 Likes
*
33 1 285 rn 244
,iure 1.2 - Airhnb co-Iounder Brian Chesky s t\cc1
And Peter Schwartz, SVP for Strategic Planning, summarizes the value of platforms as a key growth strategy for Salesforce:
"Platforms today power learning and innovation at the speed of business by providing collaborative and sometimes exponentially productive spaces for value creation. At Salesforce, we take this model seriously, not just by building our own platform and apps but by opening our platform to millions of partners, developers, and customers, allowing them to customize and layer on top of our core. [...] For Salesforce, a vibrant platform ecosystem of customer developers, apps, and support services, one that has loyalty and mutual commitment as its life blood, is our engine of growth." 18
' Book -Strategy Rules, Cusumano M. and Yoffie D., (Harper Collins, Apr 2015)
16 White Paper -From Business Modeling to Platform Design, Simon Cicero, available at: https://platformdesigntoolkit.com/wp-content/docs/Platform-Design-Toolkit-Whitepaper-ENG.pdf
" Brian Chesky's tweet available at:
https://twitter.com/bchesky/status/421856850384932864?lang=en
18 Article - The Power of Platforms, John Hagel, Deloitte Insights (Apr 2015). Available at:
https://www2.deloitte.com/insights/us/en/focus/business-trends/2015/platform-strategy-new-level-business-trends.html
Therefore, there is a little surprise that the platforms are grabbing an increasing attention in the digital era.19 Platform Hunt, an open initiative aimed to help entrepreneurs build successful platform businesses has identified 170+ platform examples, including large companies as well as startups. 20 However, a spillover effect of the success of companies such as Microsoft, Intel, Apple,
or more recent ones as Google, Amazon, Facebook, Salesforce, et al, is such that the word 'platform' has become an ubiquitous business lexicon (captured well by Scott Adams in [Figure
1.3]21 and by Viaweb and YCombinator co-founder Paul Graham in his recent tweet [ Figure
1.4]22).
I HIRED A CONSULTANT BLAH BLAH CLOUD. TO HELP US EVOLVE OUR E BLAH BLAH CLOUD.
PRODUCTS TO CLOUD BLAH BLAH CLOUD. COMPUTING. BLAH BLAH CLOUD.
Figure 1.3 - Dilbert on Platform
I IT'S AS IF YOU'RE A 1 TECHNOLOGIST AND g A PHILOSOPHER ALL j 1 IN ONE! BLAH BLAH PLATFORM.
Figure 1.4 - Ycombinator co-founder Paul Graham's tweet on overuse of the word 'Platform'
19
Article - What Twitter knows that Blackberry ddn't, Chaudary S., Parker G., Van Alstyne M. (Oct 2013). Available at: https://www.marketwatch.com/story/what-twitter-knows-that-blackberry-didnt-2013-10-10
20 Article - The 9 Types of Software Platforms, Platform Hunt, (Jun 2016). Available at: https://medium.com/platform-hunt/the-8-types-of-software-platforms-473c74f4536a 21 Article - Advice to Startups: Stop using the word 'Platform' Available at:
https://www.philsimon.com/blog/platforms/advice-to-startups-stop-using-the-word-platform/ 22 Paul Graham tweet available at: https://twitter.com/paulg/status/1 030880974429515776?lang=en
,
Paul Graham*paulgIf the description of your startup has the
word "platform" in it, there's a better
description that doesn't.
11:15 AM -18 Aug 2018
645 Retweets 3.146 Likes 0
* * ...
*
While there is some anecdotal element of truth in Paul Graham's tweet from August 2018, it is important to understand what a Platform is and what are the key drivers to enable a platform market.
WHAT IS A PLATFORM? WHAT ARE KEY DRIVERS FOR PLATFORM MARKET?
In their forthcoming book, "The Business of Platforms - Strategy in the Age of Digital Competition, Innovation and Power", Michael Cusumano, Annabelle Gawer and David Yoffie define platform as: mechanisms (virtual or physical) that bring together individuals and
organizations so they can innovate or interact in ways not otherwise possible. They also have the potential for non-linear increases in value for everyone associated with the platform ecosystem."2
The 'non-linear increases in value' as a key differentiating factor of platforms, is well-resonated
by Bill Gates famous quote in conversation with Chamath Palihapitya (founder of venture capital
fund Social + Capital and an early senior executive at Facebook) - "A platform is when the economic value of everybody that uses it, exceeds the value of the company that creates it. Then it's a platform. "24
Both definitions above hint at strong network effects in the play for power of a platform. Cusumano, et al, argue while network effects are necessary for a platform, they do not sufficiently explain why a particular company ends up with all of most of a market.25 The likelihood of winner-take-all-or-most outcome in a platform business will depend on four key drivers: the strength of network effects, the difficulty of multi-homing, lack of opportunities for competitor differentiation and niche competition, and the strength of entry barriers. A platform business must ultimately offer a compelling product or service that is superior to what the competition offers, generate a profit, as well as protect its competitive advantage. Let us look into a method that enables platform business to do so.
23 The Business of Platforms - Michael A. Cusumano, Annabelle Gawer, David B. Yoffie (Forthcoming, Harper
Business, Summer 2019). See also, Annabelle Gawer and Michael A. Cusumano, Platform Leadership: How Intel, Microsoft, and Cisco Drive Industry Innovation (Boston: Harvard Business School Press, 2002) and Michael A. Cusumano, "The Evolution of Platform Thinking," Communications of the A CM, January 2010, vol. 53, no. 1, pp.. 32-34
24 Transcript: @Chamath At Strictly VC's Insider Series (September, 2015) Available at http://haystack.vc/2015/09/17/transcript-chamath-at-strictlyvcs-insider-series/
25 See also, Michael Cusumano's colleagues' Andrei Hagiu and Simon Rothman, "Network Effects Aren't Enough," Harvard Business Review, April 2016.
THE METHOD TO PLATFORM THINKING
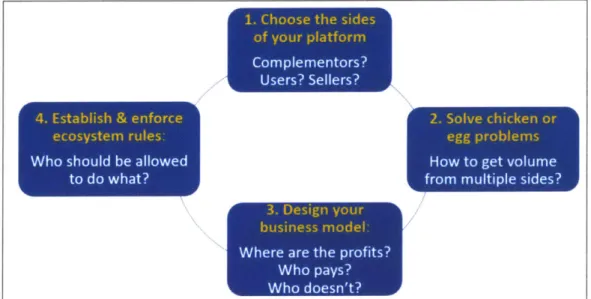
To find the answers to the main research questions, the thesis deploys the platform thinking method from Michael Cusumano, Annabelle Gawer and David Yoffie's forthcoming book The Business of Platforms. According to Cusumano, et al, the platform builders need to think around four strategic challenges. (See figure 1.5).
Figure 1.5 - Four strategic platform challenges
Four strategic platform challenges2 7 (footnote the book):
Choose the sides ofyour platform:
First step is to identify the various market sides. These could be buyers, sellers, consumers (in case of transaction platforms) or complementors - third parties who innovate new product or services based on your platform (in case of innovation platforms).
Solve chicken or egg problems:
Second step is to solve the chicken or egg problem of how to attract enough users or complementors to generate strong network effects.
26 The Business of Platforms - Michael A. Cusumano, Annabelle Gawer, David B. Yoffie (Forthcoming, Harper Business, Summer 2019)
27 The Business of Platforms - Michael A. Cusumano, Annabelle Gawer, David B. Yoffie (Forthcoming, Harper Business, Summer 2019)
Design the business model:
Third step is to design a business model. Business model needs to enable rapid platform adoption and growth, with a path to becoming profitable. The model needs to identify how to monetize the platform, while subsidizing the platform users and to do so ensuring sustainable network effects.
Establish and enforce ecosystem rules:
Fourth step is to establish an ecosystem governance: who gets to do what on the platform. Innovation platforms need to ensure the quality of complements and clarify who can connect to and innovate on top of the platform. The ecosystem governance should encourage continuous innovation and allow complementors as well as users to benefit in a sustainable manner
(sustainable: able to compete effectively with rivals and make a profit).
Thinking deeper around these four steps, the companies can start assessing the platform opportunity and developing a roadmap to their platform. Figure 1.6 below lists the key questions that the companies must resolve to build a successful platform.
Key questions Examples from leading platform companies
1. What is the 'core" (value driver) around which the platform ecosystem will be built?
2. What is the use case or 'killer application' that demonstrates your core and attracts the complementors to start building on your platform?
3. Who will be the first complementors that will stimulate demand for the platform by making new products and services that add value?
4. How can a platform owner make it attractive for potential customers to buy the platform even if there are few complementary applications?
5. How can platform owner persuade complementors to invest in platform-specific innovations if there is uncertainty about the number of end-users who are willing to pay?
6. How to make it financially exciting and rewarding for third parties to innovate?
7. How to continually deliver new "building block" technologies and enabling tools that raduce complementors' costs of development and increase their ability to innovate in new directions?
8. What would be the degree of 'openness"?
9- What would be the extent to which platform owner competes with its complementors? What would be the ecosystem rules for competition and cooperation between the platform owner and external complementors?
ServiceMax, a field service software acquired by GE for $915 million. by building on Force.com architecture (from Salesforce), CEO David Arnold explained how each service customers contextual intelligence can be seen in real-time by everyone involved in serving customers.
Apple launched iPhone and IPad with a few bundled application that were developed in-house, such as web-browser, Mail, Photos, Video, iPod, iTunes, Notes, Contacts and Calendar. It also obtained key external apps such as Google Maps and New York Times, ensuring the provision of early complements.
In PC world, Microsoft made it free and easy for developers to write new applications, and the price of Windows rose accordingly.
Today, developer conferences have become ubiquitous: Microsoft, Intel, Apple, Facebook, Salesforce, Amazon and Google, all sponsor such conferences. Venture funds, incubators and accelerators are also aimed at encouraging developers and startups to create complementary innovations.
Apptus, a Configure-Price-Quote (CPO) automation software, built on native Force.com (Salesforce platform), decided to launch on Microsoft Dynamics and Azure as well in 2016 after Salesforce's acquisition of a competitor CPQ company, SteelBrick. On its partnership with Microsoft, Apptus highlighted how it also leverages machine learning from Azure ML and its own technology hosted on Azure to bring extra muscle to Salesforce platform.
Figure 1.6 - Key questions to assess each of the four strategic platform challenges18-29-30-31
" The Business of Platforms - Michael A. Cusumano, Annabelle Gawer, David B. Yoffer (Forthcoming, Harper Business, Summer 2019)
29 Article - Why Salesforce is winning Cloud Platform War, Forbes (Oct 2013) Available at
https://www.forbes.com/sites/louiscolumbus/2013/10/07/why-salesforce-is-winning-the-cloud-platform-war/#77ff9c142c13
30 Article - GE Digital snags ServiceMax for $915 million, TechCrunch (Nov 2016) Available at
https://techcrunch.com/2016/11/14/ge-digital-snags-servicemax-for-915-million/
31 Article -Apptus CEO on poly partnering with Salesforce and Microsoft, Diginomica (Jul 2017) Available at
18 Choosing the sides of your platform Solve chicken or egg problem Design the business model Establish and enforce ecosystem uleq
Specifically, for Cisco, the platform challenge is to figure out how it can provide enough compelling value to potential partners/complementors to convince them to adopt Cisco's solution. We deploy Cusumano and Gawer's 'Coring"' and 'Tipping' principles to evaluate Cisco's cloud strategy. For Cisco, this is a 'Coring' challenge - how develop a solution to an industry-wide problem that other firms will see as "core" or essential, and adopt it. This is also a tipping problem, since there are other solutions and the market has not yet tipped. (See figure 1.7 on next page).
Technology Actions to Consider " Solve an essential system" problem
" Facilitate external companies* provision of add-ons;
" Keep Intellectual property dosed
on the innards of your technology " Maintain strong interdependencies
between platform and complements
" Try to develop unique, compelling
features that are hard to Imitate and that attract users
" Tip across markets: absorb and bundle
technical features from an adjacent market
Business Actions to Consider
" Solve an essential business problem for many industry players
" Create and preserve complementors'
incentives to contribute and innovate " Protect your main source of revenue
and profit
" Maintain high switching costs to
competing platforms
" Provide more incentives for
complemen-tors than your competitors do " Rally competitors to form a coalition
* Consider pricing or subsidy mechanisms
that attract users to the platform
igiure 1.7 - toring and Tipping' platform strategies
1.5 Structure of the thesis
Chapter 1 introduces the motivation and relevance behind the thesis topic. It lays out the main research questions and the approach to answer these questions. The chapter also introduces the method used to assess the platform opportunity in the field of cybersecurity and in particular, for the analysis of Cisco's cloud security solution.
Chapter 2 provides an overview of the evolution of cybersecurity field, and the development of key cybersecurity architectures and technologies., and the emerging security needs for today's enterprises and businesses.
https://diginomica.com/2017/07/03/apttus-ceo-on-poly-partnering-with-salesforce-microsoft/
32 Michael Cusumano, Annabelle Gawer, 'How companies become platform leaders', MIT Sloan Management
Review, (Winter, 2008), Available at: https://sloanreview.mit.edu/article/how-companies-become-platform-leaders/ Strategic Option
Coring
How to create a new platform where none existed before
Tipping
How to win platform wars by building market momentum
-I
Chapter 3 provides an overview of the current state of cybersecurity and, also the emerging security needs for today's enterprises and businesses.
Chapter 4 employs Cusumano's platform thinking method to assess the current direction taken by leading players such as [Salesforce as a platform success], and [Palo Alto Networks, and Zscaler, as platform wannabes for cybersecurity]. The chapter concludes with 'what would an ideal cybersecurity platform look like?' The key findings from this analysis inform the opportunities and threats for Cisco' cloud security positioning.
Chapter 5 provides an overview of Cisco's security business, with a particular focus on cloud-delivered enterprise security solution - Umbrella. The chapter concludes with the analysis of Cisco Umbrella through the lens of Cusumano's platform thinking framework and concludes with potential future direction for Cisco Umbrella.
2
Evolution of cybersecurity (1 970s
-
2000s)
2.1 Overview
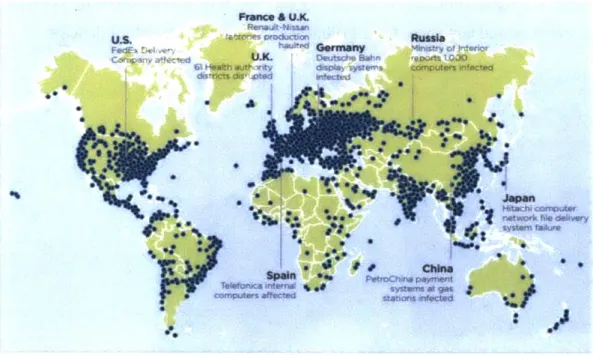
NotPetya's damages were estimated at $10 billion33. Maersk alone reported a loss of $300 million. While no customer or business data is believed to have been exposed, Maersk Chairman Jim Hagemann Snabe said at World Economic Forum, "the attack resulted in reinstall of our entire infrastructure". In total, Maersk reinstalled 4,000 servers, 45,000 PCs, and 2,500 applications over ten days. 3 Maersk is just one such example of one of the many different cyber-attacks that are materially affecting business outcomes. Figure 2.1 below shows another such example, the global damage caused by WannaCry infections.
Race & U.K
RermAt-tNsm
Figure 2.1- Wanna~r in eons acrossd ewou ndeapl uins mpcs
haArtd d yTt Maingstry o inHiot y
= =-eled U.K. DeutltOsaio h eQe7.4 1030 61 Heathra~wy dpa s~venms c0Ronvxr, ifadd
districtsctld
Sk. Sr* ev.
cimpukatm affectea
attack/f da
sp an *4 Peto~hmpayment
SIagesorce- ite~mawa etech ic (Mayrw 207) A Waiab at 9
a
Figure 2.1 -WannaCry infections across the world and example business impacts1
11 Article - The Untold Story of NotPetya, The Most Devastating CyberAttack in History, Wired (Aug, 2018)
Available at: https ://www.wired.com/story/notpetya-cyberattack-ukraine-russia-code-crashed-the-world/
11 Article - NotPetya ransomware forced Maersk to reinstall 4000 servers, 45000 PCs, ZDNet (Jan 2018)
Available at: https://www.zdnet.com/article/maersk-forced-to-reinstall-4000-servers-45000-pcs-due-to-notpetya-attack!
15 Image source - intel.malwaretech.com (May, 2017), Available at
According to Cybersecurity Ventures, at macro-level, cybercrime will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015. 36 [Cybersecurity Ventures defines cybercrime as damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, embezzlement, fraud, and post-attack disruption to the normal course of business, forensic investigation, restoration and deletion of hacked data and systems, and reputational harm.]
Flashback just 30 years, November 1988, The Morris Worm (written to gauge the size of the internet), was one of the first computer worms that brought down the internet. According to an
article from La Trobe University3 7, just 99-line program (figure 2.2) affected 6,000 computers
(roughly, 10% of the computers connected to the internet at that time). The U.S. Court of Appeals found the cost of removal ranged from $200 to $53,000, with Cliff Stoll of Harvard using this data to estimate that the worm caused anywhere from $100,000 to $10,000,000 worth of damage.
Figure 2.2 - The Morris Worm source code on display (Intel Free Press)3
36 Report - Annual CyberCrime Report, CyberSecurity Ventures (Oct 2017), Summary available at https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-20 16/
37 Article - The fascinating evolution of cybersecurity, La Trobe University. Available at https://www.latrobe.edu.au/nest/fascinating-evolution-cybersecurity/
38 Picture - Intel Free Press. Available at https://www.flickr.com/photos/intelfreepress/10483246033/in/photolist-gYnnPg-gXQSbD-9PLiaH-9PLio4-9PPasW-9PLise-9PPacm-gXQSaM-dyAgC3
Two immediate questions come to mind,
1. How did we reach from such solitaire hacking as The Morris Worm to industry numbing organized attacks such as NotPetya?
2. What is required to safeguard against the burgeoning cyberattacks?
To address the first question, the author summarizes the evolution of cybersecurity looking through a three-dimensional lens of: shape of internet, attack vectors and cybersecurity technology (see table 2.1). Looking at internet evolution over last 40 years as shown in table 2.1 helps build perspective on how the internet was not designed to be secure and on how the proliferation of internet and dynamism of IT architectures feed into both increasing frequency and intensity of cyberattacks. Without understanding the history of internet and cybersecurity, it is difficult to understand the future direction and the emerging needs to secure physical and digital assets interconnected over the ever-changing internet. The author also uses figure 2.3 to set the context for industry expert interviews to begin addressing the second question.
1990s Client-Server in general parlance Solitaire hacking 2000s 2010s Cloud computing/ Dominance of data mobile - the
center/ network disappearance of perimeter network perimeter
Nation state, organized supply chain
Attack vectors The Morris Worm (1988), No intention of harm Mailing-lists & Cyber CERT. security mjordomo@lists.gn ac.net, LISTSERV@netspa ce.org Sniffer, IP Spoofing, Denial of service [Telnet, FTP, SMTP, USENET] Network firewall, Security Firewall, Antivirus SSL/TSL Data theft, Phishing, Aggressive malware [www, audio, video, teleconference, music, live
news, database systems] Advanced proxies and filtering (application gateways), VPN, Intrusion Detection Ransomware, zero-day, fileless, organized syndicate [elastic and massive scale and
distributed computing] Cloud security, Zero Trust, AI/ML for detection and response
Figure 2.3 - Evolution of Cybersecurity (thick arrows show prominence)
(Note: The purpose of figure 2.3 is to provide a broad understanding of the evolution of cybersecurity. It is not meant to be an exhaustive coverage of all prevalent cyber threats and cybersecurity technologies.) Shape of internet 1970s - 1980s ARPANET BGP, TCP/EP 4 M P
kh-From The Morris Worm to NotPetya, how did we reach here?
2.2 1970s - 1980s: Emergence of Internet, unsecure by design
"We did not focus on how you could wreck this system intentionally", Vinton G. Cerf, Chief
Internet Evangelist and VP at Google, Co-founder TCP-IP
A network that combined unprecedented reach, speed and efficiency with the ability to act
anonymously "that's aperfectformulafor the dark side ", Leonard Kleinrock, PhD MIT, Professor at UCLA, a pioneer in networking
[Quotes source: Net of Insecurity, a series by Craig Timberg, Washington Post (May 2015)'9] Key points
" ARPANET and TCP/IP -why internet is the way it is today
" Encryption algorithms themselves were considered a potential threat to national security
* The three napkin protocol, a key to internet proliferation, making it even more unsecure * Birth of CERT (Computer Emergency Response Team)
Historian Ian Peter lists five competing theories for origins of internet on his website www.nethistory.info 40. While there are many claims to the invention of internet, ARPANET and TCP/IP (a famous communication protocol, which became the backbone of internet), are perhaps two critical motions that manifested the Internet that we know today.
ARPANET and the need for internetworking
Prior to 1970s, there was no internet. At the height of the Cold War, in 1958, US launched Advanced Research Projects Agency (ARPA)41, to ensure that communication network in the US remains active, in the event of a nuclear attack that might destroy telephone lines and wires (the then existing national defense network). The idea was to have connected computers to keep a communication network active for the US military (known at ARPANET). From an article in The
9 https://www.washingtonpost.com/sf/business/2015/05/30/net-of-insecurity-part- 1/?utm term=.5595388da0 1 c 40 Article - So who really did invent the Internet?, Ian Peter. Available at
http://www.nethistory.info/History%20of%2Othe%2OIntemet/origins.htmi
4 Article -A brief history of internet, ScienceNode (February 2017), Available at: https://sciencenode.org/feature/a-brief-history-of-the-internet-.php
Gaurdian42 , according to the scientist Don Nielsen, (Stanford Research Institute (SRI), where Don worked on radio-based packet switched network), the important distinction of origins of internet is that it came out of US military. That is why it was designed to work anywhere. However, the
1969 ARPANET was a computer network, which linked mainframes at universities, government
agencies and defense contractors around the country and included nearly 60 nodes by the mid-1970s. ARPANET was not mobile and it communicated over the fixed links. The need was two-folds: one to build a wireless network where the data packets could be relayed across the US military (spread across the world) through radio or satellite. Second, connect the wireless networks to the wired network of ARPAENT, so "internetworking".
Internetworking becomes real - Transmission Control Protocol/Internet Protocol (TCP/IP)3
The need for internetworking resulted TCP/IP, the work done by Vinton G. Cerf and fellow computer scientist Robert E. Kahn in 1970s, allowed virtually any computer network in the world to communicate directly with any other, no matter what hardware, software or underlying computer language the systems used. And in August 1976, the first such electronic message was sent successfully, from a radio signal from a van parked in the parking lot of the Alpine Beer Garden (then known as Rossotti's) to an office building on a wired ARPANET in Menlo Park.44
G OF THE INTERNE,,
27, 1976, scientists fw
Icelebrated the
su-tests by sending an c lG
"I computer set up of n pi, - %rit Inn. The
messo(y-rk to SRI and on throu); ARPANET, to Boston,
gmjrning of the Internet A(
Figure 2.4 - A plaque at Rossoti's (Image credit: Alpine Beer Garden)15
42 Article -How the internet was invented, The Gaurdian (July, 2016) Available at:
https://www.theguardian.com/technology/2016/jul/I 5/how-the-internet-was-invented-1976-arpa-kahn-cerf
4 This section is from the Essay The Net of Insecurity, Craig Timberg, Washington Post (May 2015). Available at: https://www.washingtonpost.com/sf/business/2015/05/30/net-of-insecurity-part-1/?utmterm=.5595388da01c 11 Article -How the internet was invented, The Gaurdian (July, 2016) Available at:
https://www.theguardian.com/technology/2016/jul/I 5/how-the-internet-was-invented-1976-arpa-kahn-cerf 4 Image source: http://www.alpineinnbeergarden.com/gal.html (Image 4)
TCP/IP- not designed to be secure 46
With Cerf and Kahn's work on TCP/IP, internet was set to become a global utility such as electricity. TCP/IP protocol enabled any network in the world to communicate directly with any other, irrespective of the hardware, software or operating systems or languages that the systems used. Both Cerf and Kahn were aware of importance of security, but in the context of military setting and not in terms of public or commercial use. TCP/IP could have been secured by built-in encryption, however, that would not happen due to two main reasons. First, end-to-end encryption required large amount of computing power and expensive hardware to work properly. Second and more importantly, while the National Security Agency while supported secure internet for military use, it had serious concerns about encryption for public or commercial use. While TCP/IP was not designed to be secure due to technology and political challenges, the open and accessible nature of TCP/IP made it a dominant protocol with worldwide acceptance.
The 'three napkin protocol' (Border Gateway Protocol (BGP) - takes internet global, also makes
it ripe for attack47
As public and commercial use of internet increased during 1980s, the big issue of the time was a possibility that Internet could break down. Outside ARPANET, in 1989 in an engineering conference Austin, Yakhov Rekhter from IBM and Kirk Lougheed, a founding employee of Cisco, 'scribbled' a solution that could avoid such Internet breakdown on paper napkins. What they jokingly called, 'a three napkin protocol', formally known as Border Gateway Protocol (BGP),
was a quick fix to routing data across the internet.
46 Refer to footnote 42
4' This section is from the Essay - The Long Life of a Quick Fix, Craig Timberg, Washington Post (May 2015). Available at :
https://www.washingtonpost.com/sf/business/2015/05/31/net-of-insecurity-part-2/?utm term=. 13ee103900f5
A.--# 00. el~I d r'' ~ M ~~i '000 IfA-"A 4V
Figure 2.5 - Image capture of original BGP design (three napkin protocol) found on Network Collective Podcast with Toni Li"
Simply put, BGP helps a system on the network to take a packet and transmit is farther on the internet to the desired destination. This is a critical function because internet, a complex web of network of networks, has no map. BGP enables routing decisions based on information provided
by neighboring systems, which in turn gather information rom their neighbors in cyberspace. As
Cisco describes, Border Gateway Protocol (BGP) is an Internet Engineering Task Force (IETF) standard, and the most scalable of all routing protocols. BGP is the routing protocol of the global Internet, as well as for Service Provider private networks.49
While BGP really makes global internet possible, it is also inherently insecure because BGP's architecture is based on trust. BGP assumes that when a router says it's the best path, it's telling the truth. That gullibility makes it easy for eavesdroppers to fool routers into sending them traffic.5 0 It wasn't that BGP or TCP/IP inventors did not know about security issues. Further, their contemporaries such as Radia Perlman (now EMC Fellow, back in the time, engineer at Digital Equipment Corporation (DEC)) and Robert Metcalfe (Founder of 3Com), actually experimented and built products that had extra security features such as built-in encryption, but none came close to contend the dominance of BGP. BGP still governs the global internet. As Lougheed said in the
4 Podcast, History of Networking, BGP by Toni Li from Network Collective (Sep 2017). Available at: https://thenetworkcollective.com/2017/09/hon-li-bgp/
49 Cisco company website, product information. Available at:
https://www.cisco.com/c/en/us/products/ios-nx-os-software/border-gateway-protocol-bgp/index.html
50 Revealed: The Internet's Biggest Security Hole, Article of Wired, August 2008. Available at:
https://www.wired.com/2008/08/revealed-the-in/
Washington Post essay, 'Long Life of a Quick Fix', "If lack of security becomes a significant cost to doing business, a lot of people will be interested in fixing the problem. At this point, people are just patching their way through it, keeping one step ahead of the bad guys."5 1 Lougheed's comment neatly captures the approach to cybersecurity in 1990s and 2000s.
First attacks
Prior to 1990s, there weren't real malicious cyberattacks. 1980s saw the birth of a few hacker groups such as the LOpht (based in Cambridge, MA). LOpht members detailed systemic risks and vulnerabilities in critical infrastructure such as Windows NT server and the Internet itself52. The
hacking activity at LOpht and nuisance attacks such as The Morris Worm gave rise to the Computer Fraud and Abuse Act (1986) and eventually led to the establishment of CERTs (Computer Emergency Response Teams, first established at Carnegie Mellon University5 3) as a central team
to respond to such cyberattacks.
2.3 1990s: The dawn of cybersecurity
1990s was really when the Internet started becoming mainstream, with the creation of world wide web (www - Tim Berners-Lee's idea of publishing, locating and retrieving documents stored on
Internet servers across the world ) and with launch of Mosaic, a browser written for the web5 4
(product from the first internet startup, Marc Andreesen's Mosaic Communications, later known as Netscape).
Kev poin s
" The beginning of enterprise computing era in a client-server architecture
" Notable cyberthreats emerged attacking clients (end-user PCs) by macro-viruses such as
(Michaelangelo, Melissa, Iloveyou and Concept), and targeting service disruption by Denial of Service (DoS) attacks
5 Refer to note 46, sub-section 'No one was buying'
52 Article, The LOpht Legacy, The Ethical Hacker Network (Jun 2018), Available at:
https://www.ethicalhacker.net/columns/sanabria/the-Opht-legacy/
" History, The CERT division at CMU. Available at:
https://www.sei.cmu.edu/about/divisions/cert/index.cfm#history
5 John Naughton (2016) The evolution of the Internet: from military experiment to General Purpose Technology, Journal of Cyber Policy, 1:1, 5-28, DOI: 10.1080/23738871.2016.1157619
* Advent of security firewalls (Checkpoint) to safeguard corporate networks and anti-virus software (McAfee and Symantec) and web browser security (Netscape) to safeguard PC users
Client-server architecture, and first applications on internet
While Microsoft in 1980s brought computing to homes through Windows OS on personal computers (PCs), the enterprise computing era began in 1990s with powerful server computers
linked to desktop PCs. Such client-server groups formed disparate systems of local area networks (LANs) and applications, which were integrated together in a single infrastructure, as shown in figure 2.6 below.
Figure 2.6 - Enterprise Computing era 1990s"5
The business requirements during this time were mostly around accessing remote terminal services (Telnet), file transfer (File Transfer Protocol - FTP), email (Simple Mail Transfer Protocol -SMTP) and USENET (the Network News Transfer Protocol - NNTP). 56
First real cyberattacks affecting business world, still primarily carried out by solitaire hackers
5 Image source: https://paginas.fe.up.pt/~als/mislOe/ch5/chpt5-lbullettext.htm
The emergent cyberattacks of the time exploited vulnerabilities in the server operating systems such as Windows NT and Windows 95 to disrupt the services for legitimate users and targeted commonly prevalent applications such as email and word processor on the end-user PCs.
DOS ATTACKS - SYN FLOOD, SMURF, AND BUFFER OVERFLOW
As explained by a leading cybersecurity company Palo Alto Networks, Denial of Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash. In both instances, the DoS attack deprives legitimate users (i.e. employees, members, or account holders) of the service or resource they expected.
The most common type of DoS attacks deployed included, Syn Flood (sending requests to all the open ports on the network until they are saturated with requests and none are available for legitimate users to connect to), Smurfing (leveraging misconfigured network devices by sending spoofed packets that ping every computer on the targeted network, instead of just one specific machine) and Buffer overflow (send more traffic to a network address than the programmers have built the system to handle and exploit the system on its crash )57.
In September 1996, Syn Flood DoS attack against Panix, New York City's oldest internet service provider, took it offline for one full week. In 1997, there was a similar Syn Flood attack by a Romanian teenager on the IRC network, affecting internet service providers in Norway, Romania,
UK and the US. During the same period, the Pentagon, NASA and hundreds of universities were
targeted in a series of DoS attacks by a teenager from Israel, using "Teardrop" and "Bonk" techniques, which exploited known vulnerabilities in Microsoft windows operating systems.58
MACRO-VIRUS ATTACKS -CONCEPT AND MELLISA
Concept was one of the first viruses to spread across different countries during 1995-1997. Unlike, executable program files viruses, this was a macro-virus (present in macro programs in the documents such as Microsoft Word), which gets executed every time the infected document is
1 What is Denial of Service Attack (DoS), Cyberpedia by Palo Alto Networks, Available at:
https://www.paloaltonetworks.com/cyberpedia/what-is-a-denial-of-service-attack-dos
58 Article, 'Protection against Denial of Service Attacks', Georgios Loukas, Gulay Oke, The Computer Journal Vol.
00 No. 0, 2009. doi:10.1093/comjnl/bxh00, available at:
https://pdfs.semanticscholar.org/cdd9/1609bb48cb0a43d56c51c87e293564d747c9.pdf
opened.59
Such macro-viruses became materially damaging, when distributed over mass email. Mellisa, created by New Jersey based programmer David Smith, released in 1999 was the first example of rapidly spreading email virus, which affected over 1 million computers, costing businesses an estimated $80 million.60
DoS and virus attacks of 1990s, while still led by solitaire hackers, seeded the need for cyber security solutions.
EARLY FORM OF CYBERSECURITY: SECURITY FIREWALLS, ANTIVIRUSES AND SSL 1551, 1601
The first network firewalls appeared in the late 1980s and were routers used to separate a network into smaller LANs. Firewalls like this were put in place to limit problems from one LAN spilling over and affecting the whole network. With the rise of DoS attacks in 1990s, the idea of network firewalls was extended beyond such inter-LAN safeguarding, to secure the corporate networks against threats from outside (Internet). These were IP routers with filtering rules, known as security firewalls. As Frederic Avolio explains, the key principle of firewall is to act as a controlled gateway between two or more networks through which all traffic must pass. A firewall enforces a security policy and it keeps an audit trail. By including a security firewall between internet and private corporate network, businesses could essentially protect their private networks, by limiting the to and fro access to internet through firewall only, as shown in figure 2.7 below.
Figure 2.7 - Unprotected network vs. network protected by firewall (zone of risk limited to firewall)
[55]
The first commercial security firewall to hit the market was from Digital Equipment Company, called DEC - SEAL (Secure External Access Link) in 1991. In 1994, Check Point Systems, 59
Malware Defense History, Ch 5. Macro Viruses, Dr. Nikolai Bezroukov 1994-2013. Unpublished notes. Version 0.80.October, 2013 Available at:
http://www.softpanorama.org/Malware/Malwaredefense history/ChO5_ macroviruses/Zoo/concept.shtml 60
Article, 'Creator of Melissa virus gets 20 months in jail', The New York Times (May 2002), Available at: https://www.nytimes.com/2002/05/02/nyregion/creator-of-melissa-virus-gets-20-months-in-jail.html
introduced Firewall - 1, the first 'user-friendly' security firewall, with graphical management interface, greatly simplifying installation and administration.
Security firewalls were good at providing secure connections to internet based on filtering rules for address information (in case of packet firewalls at IP layer, circuit firewalls at transport layer), and some high-level application data such as URL information, commands passed to FTP (in case of application gateways at Application layer). However, these firewalls were not good at protecting from internal bad intent (ie insider using Internet gateway for malice), protecting connections that did not go through firewall (eg. Connecting to internet from modem and telephone) and protecting
against computer viruses.
Beyond security firewalls protecting corporate private networks, there was an increasing need to protect the endpoints (PCs) also from computer viruses (such as Concept, Mellisa, et al), and to secure the internet activity (through browsers such as Mosaic/Netscape Navigator and Microsoft Internet Explorer). McAfee's VirusScan and Symantec's Norton Antivirus came to dominance for their antivirus technology that could identify virus signatures and prevent them from executing on the end user computers. Further, in 1994, the Secure Sockets Layer Protocol (SSL) was invented
by Netscape Communications to secure communications between clients and server applications
over an unprotected network, such as the Internet and it has been de facto standard for cryptographic protocol since then. SSL provides privacy and integrity of the data that client and server applications exchange and authentication of one or both endpoints of the communication session.61 Today, beyond web browsing (HTTPS protocol), SSL also secures email (SMPT protocol), phone call (VOIP protocol), file sharing (FTP protocol) and many others.
2.4 2000s: Securing network perimeter against institutionalized cyber attacks Netscape's SSL invention (securing the internet browser) fueled the 'dot-com' businesses (ecommerce, search, social networking etc.) as well as the demand for corporate services to be consumed over internet by employees. In 2000s, data started becoming the new oil, and data centers started becoming the nerve centers as businesses rapidly moved 'online'.
61 The Secure Sockets Layer and Transport Layer Security, Jinwoo Hwang, IBM (Jun 2012), Available at:
https://www.ibm.com/developerworks/library/ws-ssl-security/index.htm