RESEARCH OUTPUTS / RÉSULTATS DE RECHERCHE
Author(s) - Auteur(s) :
Publication date - Date de publication :
Permanent link - Permalien :
Rights / License - Licence de droit d’auteur :
Institutional Repository - Research Portal
Dépôt Institutionnel - Portail de la Recherche
researchportal.unamur.be
University of Namur
A Context-Driven Approach for Guiding Agile Adoption
Ayed, Hajer; Vanderose, Benoît; Habra, Naji
Published in:
ICSEA 2015, The Tenth International Conference on Software Engineering Advances
Publication date: 2015
Document Version Peer reviewed version Link to publication
Citation for pulished version (HARVARD):
Ayed, H, Vanderose, B & Habra, N 2015, A Context-Driven Approach for Guiding Agile Adoption: The AMQuICk Framework. in R Oberhauser, L Lavazza, H Mannaert & S Clyde (eds), ICSEA 2015, The Tenth International Conference on Software Engineering Advances. Barcelona, Spain, pp. 228 - 233, ICSEA, Barcelona, Spain, 15/11/15.
General rights
Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain
The Tenth International Conference on Software Engineering Advances
ISBN: 978-1-61208-438-1
November 15 - 20, 2015
Barcelona, Spain
ICSEA 2015 Editors
Roy Oberhauser, Aalen University, Germany
Luigi Lavazza, Università dell'Insubria - Varese, Italy
Herwig Mannaert, University of Antwerp, Belgium
Stephen Clyde, Utah State University, USA
Forward
The Tenth International Conference on Software Engineering Advances (ICSEA 2015), held on
November 15 - 20, 2015 in Barcelona, Spain, continued a series of events covering a broad spectrum of
software-related topics.
The conference covered fundamentals on designing, implementing, testing, validating and
maintaining various kinds of software. The tracks treated the topics from theory to practice, in terms of
methodologies, design, implementation, testing, use cases, tools, and lessons learnt. The conference
topics covered classical and advanced methodologies, open source, agile software, as well as software
deployment and software economics and education.
The conference had the following tracks:
Advances in fundamentals for software development
Advanced mechanisms for software development
Advanced design tools for developing software
Software engineering for service computing (SOA and Cloud)
Advanced facilities for accessing software
Software performance
Software security, privacy, safeness
Advances in software testing
Specialized software advanced applications
Web Accessibility
Open source software
Agile and Lean approaches in software engineering
Software deployment and maintenance
Software engineering techniques, metrics, and formalisms
Software economics, adoption, and education
Business technology
Improving productivity in research on software engineering
Similar to the previous edition, this event continued to be very competitive in its selection process
and very well perceived by the international software engineering community. As such, it is attracting
excellent contributions and active participation from all over the world. We were very pleased to receive
a large amount of top quality contributions.
We take here the opportunity to warmly thank all the members of the ICSEA 2015 technical program
committee as well as the numerous reviewers. The creation of such a broad and high quality conference
program would not have been possible without their involvement. We also kindly thank all the authors
that dedicated much of their time and efforts to contribute to the ICSEA 2015. We truly believe that
thanks to all these efforts, the final conference program consists of top quality contributions.
help in handling the logistics and for their work that is making this professional meeting a success.
We hope the ICSEA 2015 was a successful international forum for the exchange of ideas and results
between academia and industry and to promote further progress in software engineering research. We
also hope Barcelona provided a pleasant environment during the conference and everyone saved some
time for exploring this beautiful city.
ICSEA 2015 Advisory Chairs
Herwig Mannaert, University of Antwerp, Belgium
Mira Kajko-Mattsson, Stockholm University & Royal Institute of Technology, Sweden
Luigi Lavazza, Università dell'Insubria - Varese, Italy
Roy Oberhauser, Aalen University, Germany
Elena Troubitsyna, Åbo Akademi University, Finland
Davide Tosi, Università dell'Insubria - Como, Italy
Luis Fernandez-Sanz, Universidad de Alcala, Spain
Michael Gebhart, iterate GmbH, Germany
ICSEA 2015 Research Institute Liaison Chairs
Oleksandr Panchenko, Hasso Plattner Institute for Software Systems Engineering - Potsdam, Germany
Teemu Kanstrén, VTT Technical Research Centre of Finland - Oulu, Finland
Osamu Takaki, Gunma University, Japan
Georg Buchgeher, Software Competence Center Hagenberg GmbH, Austria
ICSEA 2015 Industry/Research Chairs
Herman Hartmann, University of Groningen, The Netherlands
Hongyu Pei Breivold, ABB Corporate Research, Sweden
ICSEA 2015 Special Area Chairs
Formal Methods
Paul J. Gibson, Telecom & Management SudParis, France
Testing and Validation
Florian Barth, University of Mannheim, Germany
Web Accessibility
Adriana Martin, National University of Austral Patagonia (UNPA), Argentina
Software engineering for service computing
Committee
ICSEA Advisory Chairs
Herwig Mannaert, University of Antwerp, Belgium
Mira Kajko-Mattsson, Stockholm University & Royal Institute of Technology, Sweden
Luigi Lavazza, Università dell'Insubria - Varese, Italy
Roy Oberhauser, Aalen University, Germany
Elena Troubitsyna, Åbo Akademi University, Finland
Davide Tosi, Università dell'Insubria - Como, Italy
Luis Fernandez-Sanz, Universidad de Alcala, Spain
Michael Gebhart, iteratec GmbH, Germany
ICSEA 2015 Research Institute Liaison Chairs
Oleksandr Panchenko, Hasso Plattner Institute for Software Systems Engineering - Potsdam, Germany
Teemu Kanstrén, VTT Technical Research Centre of Finland - Oulu, Finland
Osamu Takaki, Gunma University, Japan
Georg Buchgeher, Software Competence Center Hagenberg GmbH, Austria
ICSEA 2015 Industry/Research Chairs
Herman Hartmann, University of Groningen, The Netherlands
Hongyu Pei Breivold, ABB Corporate Research, Sweden
ICSEA 2015 Special Area Chairs
Formal Methods
Paul J. Gibson, Telecom & Management SudParis, France
Testing and Validation
Florian Barth, University of Mannheim, Germany
Web Accessibility
Adriana Martin, National University of Austral Patagonia (UNPA), Argentina
Software engineering for service computing
Muthu Ramachandran, Leeds Beckett University, UK
ICSEA 2015 Publicity Chairs
Shahliza Abd Halim, Universiti of Technologi Malaysia (UTM) - Skudai, Malaysia
Mohammad Abdallah, Al-Zaytoonah University of Jordan, Jordan
Adla Abdelkader, University of Oran, Algeria
Muhammad Ovais Ahmad, University of Oulu, Finland
Moataz A. Ahmed, King Fahd University of Petroleum & Minerals – Dhahran, Saudi Arabia
Syed Nadeem Ahsan, TU-Graz, Austria
Mehmet Aksit, University of Twente, Netherlands
Ahmed Al-Moayed, Hochschule Furtwangen University, Germany
Azadeh Alebrahim, University of Duisburg-Essen, Germany
Mamdouh Alenezi, Prince Sultan University - Riyadh, Saudi Arabia
Basem Y. Alkazemi, Umm Al-Qura University, Saudi Arabia
Mohammad Alshayeb, King Fahd University of Petroleum and Minerals, Saudi Arabia
Zakarya A. Alzamil, King Saud University, Saudi Arabia
Vincenzo Ambriola, Università di Pisa, Italy
Jose Andre Dorigan, State University of Maringa, Brazil
Buzzi Andreas, Credit Suisse AG – Zürich, Switzerland
Andreas S. Andreou, Cyprus University of Technology - Limassol, Cyprus
Maria Anjum, Durham University, UK
Paulo Asterio de Castro Guerra, Tapijara Programação de Sistemas Ltda. - Lambari, Brazil
Colin Atkinson, University of Mannheim, Germany
Marco Autili, University of L’Aquila, Italy
Robert Azarbod, Oracle Corporation, USA
Thomas Baar, Hochschule für Technik und Wirtschaft (HTW) Berlin, Germany
Gilbert Babin, HEC Montréal, Canada
Muneera Bano, International Islamic University - Islamabad, Pakistan
Fernando Sérgio Barbosa, Escola Superior de Tecnologia do Instituto Politécnico de Castelo Branco,
Portugal
Jorge Barreiros, CITI/UNL: Center of Informatics and Information Technology UNL || ISEC/IPC: ISEC
-Polytechnic Institute of Coimbra, Portugal
Florian Barth, University of Mannheim, Germany
Gabriele Bavota, University of Salerno, Italy
Noureddine Belkhatir, University of Grenoble, France
Simona Bernardi, Centro Universitario de la Defensa / Academia General Militar - Zaragoza, Spain
Jorge Bernardino, Polytechnic Institute of Coimbra - ISEC-CISUC, Portugal
Ateet Bhalla, Independent Consultant, India
Celestina Bianco, Systelab Technologies - Barcelona, Spain
Christian Bird, University of California, USA
Kenneth Boness, Reading University, UK
Mina Boström Nakicenovic, Sungard Front Arena, Stockholm, Sweden
M. Boukala-Ioualalen, University of Science and Technology Houari Boumediene, Algeria
Fernando Brito e Abreu, Instituto Universitário de Lisboa (ISCTE-IUL), Portugal
Hongyu Pei Breivold, ABB Corporate Research, Sweden
Manfred Broy, Technische Universität München, Germany
Stefan Burger, Allianz Deutschland AG, Germany
David W. Bustard, University of Ulster - Coleraine, UK
Haipeng Cai, University of Notre Dame, USA
Fabio Calefato, University of Bari, Italy
Vinicius Cardoso Garcia, Centro de Informática (CIn) - Universidade Federal de Pernambuco (UFPE),
Brazil
José Carlos Metrôlho, Polytechnic Institute of Castelo Branco, Portugal
Bengt Carlsson, Blekinge Institute of Technology – Karlskrona, Sweden
Rocío Castaño Mayo, Universidad de Oviedo, Spain
Everton Cavalcante, Federal University of Rio Grande do Norte, Brazil / IRISA-UMR CNRS-Université de
Bretagne-Sud, France
Alexandros Chatzigeorgiou, University of Macedonia, Greece
Antonin Chazalet, IT&Labs, France
Yoonsik Cheon, The University of Texas at El Paso, USA
Federico Ciccozzi, Mälardalen University, Sweden
Vanea Chiprianov, University of Pau, France
Morakot Choetkiertikul, Mahidol University, Thailand
Antonio Cicchetti, Mälardalen University, Sweden
Federico Ciccozzi, Mälardalen University, Sweden
Marta Cimitile, Unitelma Sapienza University, Italy
Tony Clark, Middlesex University, UK
Stephen Clyde, Utah State University, USA
Methanias Colaço Júnior, Federal University of Sergipe, Brazil
Rebeca Cortázar, University of Deusto - Bilbao, Spain
Oliver Creighton, Siemens AG, Germany
Carlos E. Cuesta, Rey Juan Carlos University - Madrid, Spain
Beata Czarnacka-Chrobot, Warsaw School of Economics, Poland
Zhen Ru Dai, Hamburg University of Applied Science, Germany
Darren Dalcher, Hertfordshire Business School, UK
Peter De Bruyn, University of Antwerp, Belgium
Claudio de la Riva, Universidad de Oviedo - Gijon, Spain
Peter De Bruyn, University of Antwerp, Belgium
Diego Dermeval Medeiros da Cunha Matos, Federal University of Campina Grande (UFCG), Brazil
Onur Demirors, Middle East Technical University, Turkey
Steven A. Demurjian, The University of Connecticut - Storrs, USA
Vincenzo Deufemia, University of Salerno, Italy
Antinisca Di Marco, University of L'Aquila - Coppito (AQ), Italy
Themistoklis Diamantopoulos, Aristotle University of Thessaloniki, Greece
Tadashi Dohi, Hiroshima University, Japan
José André Dorigan, State University of Londrina, Brazil
Lydie du Bousquet, J. Fourier-Grenoble I University, LIG labs, France
Roland Ducournau, LIRMM - CNRS & Université Montpellier 2, France
Juan Carlos Dueñas López, Universidad Politécnica de Madrid, Spain
Slawomir Duszynski, Fraunhofer Institute for Experimental Software Engineering, Germany
Christof Ebert, Vector Consulting Services, Germany
Arabia
Vladimir Estivill-Castro, Griffith University - Nathan, Australia
Kleinner Farias, University of Vale do Rio dos Sinos (Unisinos), Brazil
Fausto Fasano, University of Molise - Pesche, Italy
Feipre Ferraz, CESAR / CIN-UFPE, Brazil
Martin Filipsky, Czech Technical University in Prague, Czech Republic
Derek Flood, Dundalk Institute of Technology (DkIT), Ireland
Diego Fontdevila, Universidad Nacional de Tres de Febrero, Argentina
Rita Francese, University of Salerno, Italy
Terrill L. Frantz, Peking University HSBC Business School, China
Jicheng Fu, University of Central Oklahoma, USA
Felipe Furtado, Recife Center of Advanced Studies and Systems / Federal University of Pernambuco,
Brazil
Cristina Gacek, City University London, UK
Matthias Galster, University of Canterbury, New Zealand
G.R. Gangadharan, IDRBT, India
Stoyan Garbatov, OutSystems, Portugal
José Garcia-Alonso, University of Extremadura, Spain
Kiev Gama, UFPE, Brazil
Antonio Javier García Sánchez, Technical University of Cartagena, Spain
José García-Fanjul, University of Oviedo, Spain
Michael Gebhart, iteratec GmbH, Germany
Sébastien Gérard, CEA LIST, France
Paul Gibson, Telecom SudParis, France
Yossi Gil, Technion - Israel Institute of Technology, Israel
Ignacio González Alonso, Infobótica RG University of Oviedo, Spain
Oleg Gorbik, Accenture - Riga Delivery Centre, Latvia
Mohamed Graiet, ISIMS, MIRACL, Monastir, Tunisia
Gregor Grambow, University of Ulm, Germany
Carmine Gravino, Università degli Studi di Salerno, Italy
George A. Gravvanis, Democritus University of Thrace, Greece
Jeff Gray, University of Alabama, USA
Sam Guinea, Politecnico di Milano, Italy
Bidyut Gupta, Southern Illinois University, USA
Ensar Gul, Marmara University - Istanbul, Turkey
Zhensheng Guo, Siemens AG - Erlangen, Germany
Nahla Haddar, University of Sfax, Tunisia
Waqas Haider Khan Bangyal, IUI Islamabad, Pakistan
Imed Hammouda, University of Gothenburg, Sweden
Jameleddine Hassine, King Fahd University of Petroleum & Minerals (KFUPM), Saudi Arabia
Shinpei Hayashi, Tokyo Institute of Technology, Japan
José R. Hilera, University of Alcala, Spain
Jun Iio, Faculty of Letters - Chuo University, Japan
Naveed Ikram, Riphah International University – Islamabad, Pakistan
Gustavo Illescas, Universidad Nacional del Centro-Tandil-Bs.As., Argentina
Claire Ingram, Newcastle University, UK
Emilio Insfran, Universitat Politècnica de València, Spain
Shareeful Islam, University of East London, U.K.
Slinger Jansen (Roijackers), Utrecht University, The Netherlands
Marko Jäntti, University of Eastern Finland, Finland
Kashif Javed, Abo Akademi University, Finland
Hermann Kaindl, TU-Wien, Austria
Mira Kajko-Mattsson, Stockholm University and Royal Institute of Technology, Sweden
Ahmed Kamel, Concordia College - Moorhead, USA
Dariusz W. Kaminski, The Open University, UK
Teemu Kanstrén, VTT Technical Research Centre of Finland - Oulu, Finland
Lucia Kapova, Karlsruhe Institute of Technology, Germany
Tatjana Kapus, University of Maribor, Slovenia
Krishna M. Kavi, University of North Texas, USA
Carlos Kavka, ESTECO SpA, Italy
Markus Kelanti, University of Oulu, Finland
Abeer Khalid, International Islamic University Islamabad, Pakistan
Foutse Khomh, École Polytechnique de Montréal, Canada
Holger Kienle, Freier Informatiker, Germany
Reinhard Klemm, Avaya Labs Research, USA
Mourad Kmimech, l’Institut Supérieur d’informatique de Mahdia (ISIMA), Tunisia
Jens Knodel, Fraunhofer IESE, Germany
William Knottenbelt, Imperial College London, UK
Takashi Kobayashi, Tokyo Institute of Technology, Japan
Radek Kocí, Brno University of Technology, Czech Republic
Christian Kop, Alpen-Adria-Universität Klagenfur, Austria
Georges Edouard Kouamou, National Advanced School of Engineering - Yaoundé, Cameroon
Segla Kpodjedo, Ecole de Technologie Supérieure - Montreal, Canada
Natalia Kryvinska, University of Vienna, Austria
Tan Hee Beng Kuan, Nanyang Technological University, Singapore
Vinay Kulkarni, Tata Consultancy Services, India
Sukhamay Kundu, Louisiana State University - Baton Rouge, USA
Eugenijus Kurilovas, Vilnius University and Vilnius Gediminas Technical University, Lithuania
Rob Kusters, Open University/Eindhoven University of Technology, Netherlands
Alla Lake, LInfo Systems, LLC - Greenbelt, USA
Einar Landre, Statiol ASA, Norway
Kevin Lano, King's College London, UK
Casper Lassenius, MIT, USA
Jannik Laval, University Bordeaux 1, France
Luigi Lavazza, Università dell'Insubria - Varese, Italy
Luka Lednicki, ABB Corporate Research, Sweden
Maria Teresa Llano Rodriguez, Goldsmiths/University of London, UK
Klaus Lochmann, Technische Universität München, Germany
Sérgio F. Lopes, University of Minho, Portugal
Juan Pablo López-Grao, University of Zaragoza, Spain
Ivan Machado, Universidade Federal da Bahia, Brazil
Ricardo J. Machado, University of Minho, Portugal
Sajjad Mahmood, King Fahd University of Petroleum and Minerals, Saudi Arabia
Charif Mahmoudi, LACL - Paris 12 University, France
Nicos Malevris, Athens University of Economics and Business, Greece
Herwig Mannaert, University of Antwerp, Belgium
Cristiano Marçal Toniolo, Faculdade Anhanguera, Brazil
Eda Marchetti, ISTI-CNR - Pisa Italy
Alexandre Marcos Lins de Vasconcelos, Federal University of Pernambuco, Brazil
Daniela Marghitu, Auburn University, USA
Adriana Martin, National University of Austral Patagonia (UNPA), Argentina
Luiz Eduardo Galvão Martins, Federal University of São Paulo, Brazil
Miriam Martínez Muñoz, Universidad de Alcalá de Henares, Spain
Jose Antonio Mateo, Aalborg University, Denmark
Fuensanta Medina-Dominguez, Universidad Carlos III Madrid, Spain
Karl Meinke, KTH Royal Institute of Technology, Sweden
Igor Melatti, Sapienza Università di Roma, Italy
Andreas Menychtas, National Technical University of Athens, Greece
Jose Merseguer, Universidad de Zaragoza, Spain
Apinporn Methawachananont, National Electronics and Computer Technology Center (NECTEC),
Thailand
Markus Meyer, University of Applied Sciences Ingolstadt, Germany
João Miguel Fernandes, Universidade do Minho - Braga, Portugal
Amir H. Moin, fortiss, An-Institut Technische Universität München, Germany
Hassan Mountassir, University of Besançon, France
Henry Muccini, University of L'Aquila, Italy
Aitor Murguzur, IK4-Ikerlan Research Center, Spain
Elena Navarro, University of Castilla-La Mancha, Spain
Mahmood Niazi, King Fahd University of Petroleum and Minerals, Saudi Arabia
Oksana Nikiforova, Riga Technical University, Latvia
Natalja Nikitina, KTH Royal Institute of Technology - Stockholm, Sweden
Mara Nikolaidou, Harokopio University of Athens, Greece
Marcellin Julius Nkenlifack, Univeristé de Dschang - Bandjoun, Cameroun
Tetsuo Noda, Shimane University, Japan
Marc Novakouski, Software Engineering Institute/Carnegie Mellon University, USA
Nicole Novielli, University of Bari, Italy
Bo Nørregaard Jørgensen, Centre for Energy Informatics - University of Southern Denmark, Denmark
Roy Oberhauser, Aalen University, Germany
Fabio Palomba, University of Salerno, Italy
Päivi Parviainen, VTT, Software Technologies Center, Finland
Aljosa Pasic, ATOS Research, Spain
Fabrizio Pastore, University of Milano - Bicocca, Italy
Asier Perallos, University of Deusto, Spain
Óscar Pereira, University of Aveiro, Portugal
Beatriz Pérez Valle, University of La Rioja, Spain
David Pheanis, Arizona State University, USA
Pasqualina Potena, University of Alcalá, Spain
Christian Prehofer, Kompetenzfeldleiter Adaptive Kommunikationssysteme / Fraunhofer-Einrichtung für
Systeme der Kommunikationstechnik ESK – München, Germnay
Abdallah Qusef, University of Salerno, Italy
Salman Rafiq, Fraunhofer Institute for Embedded Systems and Communication Technologies, Germany
Claudia Raibulet, Università degli Studi di Milano-Bicocca, Italy
Muthu Ramachandran, Leeds Beckett University, UK
Amar Ramdane-Cherif, University of Versailles, France
Raman Ramsin, Sharif University of Technology, Iran
Gianna Reggio, DIBRIS - Università di Genova, Italy
Zhilei Ren, Dalian University of Technology, China
Hassan Reza, University of North Dakota - School of Aerospace, USA
Samir Ribic, University of Sarajevo, Bosnia and Herzegovina
Elvinia Riccobene, University of Milan, Italy
Daniel Riesco, National University of San Luis, Argentina
Michele Risi, University of Salerno, Italy
Gabriela Robiolo, Universidad Austral, Argentina
Oliveto Rocco, University of Molise, Italy
Rodrigo G. C. Rocha, Federal Rural University of Pernambuco, Brazil
Daniel Rodríguez, University of Alcalá, Madrid, Spain
María Luisa Rodríguez Almendros, Universidad de Granada, Spain
Siegfried Rouvrais, Institut Mines Telecom Bretagne, France
Suman Roychoudhury, Tata Consultancy Services, India
Mercedes Ruiz Carreira, Universidad de Cádiz, Spain
Alessandra Russo, Imperial College London, UK
Mehrdad Saadatmand, Mälardalen University / Alten AB, Sweden
Krzysztof Sacha, Warsaw University of Technology, Poland
Francesca Saglietti, University of Erlangen-Nuremberg, Germany
Sébastien Salva, LIMOS-CNRS / Auvergne University / IUT d'Aubière, France
Maria-Isabel Sanchez-Segura, Carlos III University of Madrid, Spain
Luca Santillo, Agile Metrics, Italy
Gaetana Sapienza, ABB Corporate Research, Sweden
Federica Sarro, University College London, UK
Patrizia Scandurra, University of Bergamo - Dalmine, Italy
Giuseppe Scanniello, Università degli Studi della Basilicata - Potenza, Italy
Christelle Scharff, Pace University, USA
Fernando Selleri Silva, Mato Grosso State University (UNEMAT), Brazil
István Siket, University of Szeged, Hungary
Abu Bakar Md Sultan, Universiti Putra Malaysia, Malaysia
Sidra Sultana, National University of Sciences and Technology, Pakistan
Lijian Sun, Chinese Academy of Surveying & Mapping, China
Mahbubur R. Syed, Minnesota State University – Mankato, USA
Davide Taibi, Free University of Bozen, Italy
Osamu Takaki, Gunma University, Japan
Giordano Tamburrelli, Università della Svizzera Italiana (USI), Swizterland
Wasif Tanveer, University of Engineering and Technology - Lahore, Pakistan
Nebojša Taušan, University of Oulu, Finland
Pierre Tiako, Langston University, USA
Maarit Tihinen, VTT Technical Research Centre of Finland - Oulu, Finland
Massimo Tivoli, University of L'Aquila, Italy
Maria Tortorella, University of Sannnio - Benevento Italy
Davide Tosi, Università degli studi dell'Insubria - Varese, Italy
Peter Trapp, Ingolstadt, Germany
Elena Troubitsyna, Åbo Akademi University, Finland
Mariusz Trzaska, Polish-Japanese Academy of Information Technology, Poland
George A. Tsihrintzis, University of Piraeus, Greece
Masateru Tsunoda, Kinki University, Japan
Henry Tufo, University of Colorado at Boulder, USA
Javier Tuya, Universidad de Oviedo - Gijón, Spain
Andreas Ulrich, Siemens AG, Germany
Christelle Urtado, LGI2P / Ecole des Mines d'Alès - Nîmes, France
Dieter Van Nuffel, University of Antwerp, Belgium
Timo Vepsäläinen, Tampere University of Technology, Finland
Laszlo Vidacs, Hungarian Academy of Sciences, Hungary
Tanja Vos, Universidad Politécnica de Valencia, Spain
Stefan Wagner, University of Stuttgart, Germany
Hironori Washizaki, Waseda University, Japan
Stefan Wendler, Ilmenau University of Technology, Germany
Agnes Werner-Stark, University of Pannonia, Hungary
Norman Wilde, University of West Florida, USA
Andreas Winter, Carl von Ossietzky University, Germany
Victor Winter, University of Nebraska-Omaha, USA
Martin Wojtczyk, Technische Universität München, Germany & Cubotix, USA
Haibo Yu, Shanghai Jiao Tong University, China
Elisa Yumi Nakagawa, University of São Paulo (USP), Brazil
Saad Zafar, Riphah International University - Islamabad, Pakistan
Amir Zeid, American University of Kuwait, Kuwait
Michal Zemlicka, University of Finance and Administration, Czech Republic
Gefei Zhang, Celonis GmbH, Germany
For your reference, this is the text governing the copyright release for material published by IARIA.
The copyright release is a transfer of publication rights, which allows IARIA and its partners to drive the
dissemination of the published material. This allows IARIA to give articles increased visibility via
distribution, inclusion in libraries, and arrangements for submission to indexes.
I, the undersigned, declare that the article is original, and that I represent the authors of this article in
the copyright release matters. If this work has been done as work-for-hire, I have obtained all necessary
clearances to execute a copyright release. I hereby irrevocably transfer exclusive copyright for this
material to IARIA. I give IARIA permission or reproduce the work in any media format such as, but not
limited to, print, digital, or electronic. I give IARIA permission to distribute the materials without
restriction to any institutions or individuals. I give IARIA permission to submit the work for inclusion in
article repositories as IARIA sees fit.
I, the undersigned, declare that to the best of my knowledge, the article is does not contain libelous or
otherwise unlawful contents or invading the right of privacy or infringing on a proprietary right.
Following the copyright release, any circulated version of the article must bear the copyright notice and
any header and footer information that IARIA applies to the published article.
IARIA grants royalty-free permission to the authors to disseminate the work, under the above
provisions, for any academic, commercial, or industrial use. IARIA grants royalty-free permission to any
individuals or institutions to make the article available electronically, online, or in print.
IARIA acknowledges that rights to any algorithm, process, procedure, apparatus, or articles of
manufacture remain with the authors and their employers.
I, the undersigned, understand that IARIA will not be liable, in contract, tort (including, without
limitation, negligence), pre-contract or other representations (other than fraudulent
misrepresentations) or otherwise in connection with the publication of my work.
Exception to the above is made for work-for-hire performed while employed by the government. In that
case, copyright to the material remains with the said government. The rightful owners (authors and
government entity) grant unlimited and unrestricted permission to IARIA, IARIA's contractors, and
IARIA's partners to further distribute the work.
Patterns for Specifying Bidirectional Transformations in UML-RSDS
Sobhan Yassipour-Tehrani, Shekoufeh Kolahdouz-Rahimi, and Kevin Lano
1
Towards a Framework for Software Product Maturity Measurement
Mohammad Alshayeb, Ahmad Abdellatif, Sami Zahran, and Mahmood Niazi
7
An Exploratory Study on the Influence of Developers in Code Smell Introduction
Leandro Alves, Ricardo Choren, and Eduardo Alves
12
The Object Oriented Petri Net Component Model
Radek Koci and Vladimir Janousek
18
“Free” Innovation Environments: Lessons learned from the Software Factory Initiatives
Davide Taibi, Valentina Lenarduzzi, Muhammad Ovais Ahmad, Kari Liukkunen, Ilaria Lunesu, Martina Matta, Fabian Fagerholm, Ju?rgen Mu?nch, Sami Pietinen, Markku Tukiainen, Carlos Ferna?ndez-Sa?nchez, Juan Garbajosa, and Kari Systa?
25
Performance Exploring Using Model Checking A Case Study of Hard Disk Drive Cache Function
Takehiko Nagano, Kazuyoshi Serizawa, Nobukazu Yoshioka, Yasuyuki Tahara, and Akihiko Ohsuga
31
Towards a Better Understanding of Static Code Attributes for Defect Prediction
Muhammed Maruf Ozturk and Ahmet Zengin
40
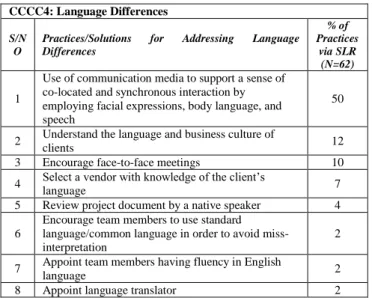
Communication and Coordination Challenges Mitigation in Offshore Software Development Outsourcing Relationships: Findings from Systematic Literature Review
Rafiq Ahmad Khan, Siffat Ullah Khan, and Mahmood Niazi
45
Adapting Heterogeneous ADLs for Software Architecture Reconstruction Tools
Dung Le, Ana Nicolaescu, and Horst Lichter
52
Verifying and Constructing Abstract TLA Specifications: Application to the Verification of C programs
Amira Methni, Matthieu Lemerre, Belgacem Ben Hedia, Serge Haddad, and Kamel Barkaoui
56
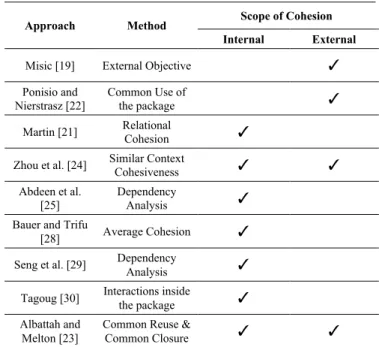
Revisiting The Package-level Cohesion Approaches
Waleed Albattah and Suliman Alsuhibany
62
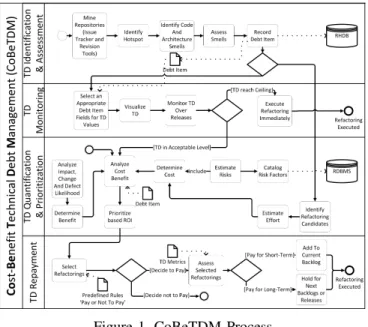
Towards a Technical Debt Management Framework based on Cost-Benefit Analysis
Muhammad Firdaus Bin Harun and Horst Lichter
Aiming Towards Modernization: Visualization to Assist Structural Understanding of Oracle Forms Applications
Kelly Garces, Edgar Sandoval, Rubby Casallas, Camilo Alvarez, Alejandro Salamanca, Sandra Pinto, and Fabian Melo
86
Effects of Recency and Commits Aggregation on Change Guide Method Based on Change History Analysis
Tatsuya Mori, Anders Hagward, and Takashi Kobayashi
96
Towards Flexible Business Software
Ahmed Elfatatry
102
EBGSD: Emergence-Based Generative Software Development
Mahdi Mostafazadeh, Mohammad Reza Besharati, and Raman Ramsin
108
A GPU-aware Component Model Extension for Heterogeneous Embedded Systems
Gabriel Campeanu, Jan Carlson, and Severine Sentilles
115
Soft System Stakeholder Analysis Methodology
Markus Kelanti, Jarkko Hyysalo, Jari Lehto, Samuli Saukkonen, Markku Oivo, and Pasi Kuvaja
122
Publish/Subscribe Cloud Middleware for Real-Time Disease Surveillance
Silvino Neto, Marcia Valeria, Plinio Manoel, and Felipe Ferraz
131
Requirement’s Variability in Model Generation from a Standard Document in Natural Language
Juliana Greghi, Eliane Martins, and Ariadne Carvalho
139
An Approach to Compare UML Class Diagrams Based on Semantical Features of Their Elements
Oksana Nikiforova, Konstantins Gusarovs, Ludmila Kozacenko, Dace Ahilcenoka, and Dainis Ungurs
147
Model-Based Evaluation and Simulation of Software Architecture Evolution
Peter Alexander, Ana Nicolaescu, and Horst Lichter
153
Towards Time-triggered Component-based System Models
Hela Guesmi, Belgacem Ben Hedia, Simon Bliudze, Saddek Bensalem, and Jacques Combaz
157
A User-App Interaction Reference Model for Mobility Requirements Analysis
Xiaozhou Li and Zheying Zhang
170
Model-Driven Engineering of Software Solutions for QoS Management in Real-Time DBMS
Salwa M'barek, Leila Baccouche, and Henda Ben Ghezala
192
An Approach for Reusing Software Process Elements based on Reusable Asset Specification: a Software Product Line Case Study
Karen D. R. Pacini and Rosana T. V. Braga
200
An Extensible Platform for the Treatment of Heterogeneous Data in Smart Cities
Cicero A. Silva and Gibeon S. A. Junior
207
Improving the Application of Agile Model-based Development: Experiences from Case Studies
Kevin Lano, Hessa Alfraihi, Sobhan Yassipour-Tehrani, and Howard Haughton
213
Metrics Framework for Cycle-Time Reduction in Software Value Creation - Adapting Lean Startup for Established SaaS Feature Developers
Pasi Tyrvainen, Matti Saarikallio, Timo Aho, Timo Lehtonen, and Rauno Paukeri
220
A Context-Driven Approach for Guiding Agile Adoption: The AMQuICk Framework
Hajer Ayed, Benoit Vanderose, and Naji Habra
228
Kanban in Industrial Engineering and Software Engineering: A Systematic Literature Review
Muhammad Ovais Ahmad, Jouni Markkula, Markku Oivo, and Bolaji Adeyemi
234
Efficient ETL+Q for Automatic Scalability in Big or Small Data Scenarios
Pedro Martins, Maryam Abbasi, and Pedro Furtado
242
The Role of People and Sensors in the Development of Smart Cities: A Systematic Literature Review
Italberto Figueira Dantas and Felipe Silva Ferraz
248
A Knowledge Base for Electric Vehicles in Inner-City Logistics
Volkmar Schau, Johannes Kretzschmar, Thomas Prinz, and Paul Hempel
257
Building a Service Manager For a Smart City Archicture
Gutemberg Cavalcante, Felipe Ferraz, and Guilherme Medeiros
261
Intersection of MPS.BR-E and SPICE Models Focused on Projects for the Automotive Industry
Vanessa Matias Leite, Jandira Guenka Palma, and Emmanuel da C. Gallo
An Approach for Sensor Placement to Achieve Complete Coverage and Connectivity in Sensor Networks
Monia Techini, Ridha Ejbali, and Mourad Zaied
277
Dynamic Symbolic Execution using Eclipse CDT
Andreas Ibing
280
Evaluating the Usability of Mobile Instant Messaging Apps on iOS Devices
Sergio Caro-Alvaro, Antonio Garcia-Cabot, Eva Garcia-Lopez, Luis de-Marcos, and Jose-Javier Martinez-Herraiz
286
Multi-Criteria Test Case Prioritization Using Fuzzy Analytic Hierarchy Process
Sahar Tahvili, Mehrdad Saadatmand, and Markus Bohlin
290
Analysis of Optimization Requirement of Mobile Application Testing Procedure
Manish Kumar, Kapil Kant Kamal, Bharat Varyani, and Meghana Kale
297
Property Based Verification of Evolving Petri Nets
Yasir Imtiaz Khan and Ehab Al-Shaer
301
Dynamic Evolution of Source Code Topics
Khaled Almustafa and Mamdouh Alenezi
307
Model Transformation Applications from Requirements Engineering Perspective
Sobhan Yassipour Tehrani and Kevin Lano
313
Analyzing the Evolvability of Modular Structures: a Longitudinal Normalized Systems Case Study
Philip Huysmans, Peter De Bruyn, Gilles Oorts, Jan Verelst, Dirk van der Linden, and Herwig Mannaert
319
Applying ISO 9126 Metrics to MDD Projects
Ricardo Alonso Munoz Riesle, Beatriz Marin, and Lidia Lopez
326
Evaluation of a Security Service Level Agreement
Chen-Yu Lee and Krishna M. Kavi
333
Towards Systematic Safety System Development with a Tool Supported Pattern Language
Jari Rauhamaki, Timo Vepsalainen, and Seppo Kuikka
341
An Analysis of sSven Concepts and Design Flaws in Identity Management Systems
Joao Jose Calixto das Chagas and Felipe Ferraz
Applications of Security Reference Architectures in Distributed Systems: Initial Findings of Systematic Mapping Study
Sajjad Mahmood, Muhammad Jalal Khan, and Sajid Anwer
363
Cif: A Static Decentralized Label Model (DLM) Analyzer to Assure Correct Information Flow in C
Kevin Muller, Sascha Uhrig, Michael Paulitsch, and Georg Sigl
369
Minimizing Attack Graph Data Structures
Peter Mell and Richard Harang
376
Reliability-Aware Design Specification for Allowing Reuse-Based Reliability Level Increment
Patricia Lopez, Leire Etxeberria, and Xabier Elkorobarrutia
386
Best Practices for the Design of RESTful Web Services
Pascal Giessler, Michael Gebhart, Dmitrij Sarancin, Roland Steinegger, and Sebastian Abeck
392
Criteria of Evaluation for Systems Using Sensor as a Service
Anderson Brito and Felipe Ferraz
398
Middleware Applied to Digital Preservation: A Literature Review
Eriko Brito, Paulo Cesar Abrantes, and Bruno de Freitas Barros
404
Middleware For Heterogeneous Healthcare Data Exchange: A Survey
Carlos Bezerra, Andre Araujo, Bruno Rocha, Vagner Pereira, and Felipe Ferraz
409
Teaching Robotics and Mechanisms
Daniela Marghitu and Dan . Marghitu
415
Case of Enterprise Architecture in Manufacturing Firm
Alicia Valdez, Griselda Cortes, Sergio Castaneda, Gerardo Haces, and Jose Medina
419
An Empirical Investigation on the Motivations for the Adoption of Open Source Software
Davide Taibi
426
Gamifying and Conveying Software Engineering Concepts for Secondary Education: An Edutainment Approach
Roy Oberhauser
432
Several Issues on the Model Interchange Between Model-Driven Software Development Tools
Una Ieva Zusane, Oksana Nikiforova, and Konstantins Gusarovs
451
Testing Smart Cities Through an Extensible Testbed
Guilherme Medeiros, Felipe Ferraz, and Gutemberg Cavalcante
457
Implementing the Observer Design Pattern as an Expressive Language Construct
Taher Ghaleb, Khalid Aljasser, and Musab Al-Turki
463
Supporting Tools for Managing Software Product Lines: a Systematic Mapping
Karen D. R. Pacini and Rosana T. V. Braga
470
Recovering Lost Software Design with the Help of Aspect-based Abstractions
Kiev Gama and Didier Donsez
477
Networking-based Personalized Research Environment : NePRE
Heeseok Choi, Jiyoung Park, Hyoungseop Shim, and Beomjong You
484
Decision Making and Service Oriented Architecture for Recruitment Process Using the New Standard Decision Model and Notation (DMN)
Fatima Boumahdi, Houssem Eddine Boulefrakh, and Rachid Chalal
Patterns for Specifying Bidirectional Transformations in UML-RSDS
K. Lano,
S. Yassipour-Tehrani
Dept. of Informatics King’s College London
London, UK
Email: kevin.lano@kcl.ac.uk, s.yassipour-tehrani@kcl.ac.uk
S. Kolahdouz-Rahimi
Dept of Software Engineering University of Isfahan
Isfahan, Iran
Email: sh.rahimi@eng.ui.ac.ir
Abstract—In this paper, we identify model transformation spec-ification and design patterns, which support the property of transformation bidirectionality: the ability of a single specification to be applied either as a source-to-target transformation or as a target-to-source transformation. In contrast to previous work on bidirectional transformations (bx), we identify the important role of transformation invariants in the derivation of reverse transformations, and show how patterns and invariants can be used to give a practical means of defining bx in the UML-RSDS transformation language.
Keywords — Bidirectional transformations; transformation design patterns; UML-RSDS
I. INTRODUCTION
Bidirectional transformations (bx) are considered important in a number of transformation scenarios:
• Maintaining consistency between two models which may both change, for example, if a UML class dia-gram and corresponding synthesised Java code both need to be maintained consistently with each other, in order to implement round-trip engineering for model-driven development.
• Where a mapping between two languages may need to be operated in either direction for different purposes, for example, to represent behavioural models as either Petri Nets or as state machines [12].
• Where inter-conversion between two different repre-sentations is needed, such as two alternative formats of electronic health record [3].
Design patterns have become an important tool in software engineering, providing a catalogue of ‘best practice’ solutions to design problems in software [7]. Patterns for model transfor-mations have also been identified [14], but patterns specifically for bx have not been defined.
In this paper, we show how bx patterns can be used to obtain a practical approach for bx using the UML-RSDS language [11].
Section II defines the concept of a bx. Section V de-scribes related work. Section III dede-scribes UML-RSDS and transformation specification in UML-RSDS. Section IV gives
SL and a target language TL. R(m, n) holds for a pair of
models m of SL and n of TL when the models consist of data which corresponds under R. It should be possible to automatically derive from the definition of R both forward and reverse transformations
R→: SL× TL → TL R←: SL× TL → SL
which aim to establish R between their first (respectively second) and their result target (respectively source) models, given both existing source and target models.
Stevens [16] has identified two key conditions which bidi-rectional model transformations should satisfy:
1) Correctness: the forward and reverse transforma-tions derived from a relation R do establish R:
R(m, R→(m, n)) and R(R←(m, n), n) for each
m : SL, n : TL.
2) Hippocraticness: if source and target models already satisfy R then the forward and reverse transformations do not modify the models:
R(m, n) ⇒ R→(m, n) = n
R(m, n) ⇒ R←(m, n) = m
for each m : SL, n : TL.
The concept of a lens is a special case of a bx satisfying these properties [16].
III. BX SPECIFICATION INUML-RSDS
UML-RSDS is a hybrid model transformation language, with a formal semantics [10] and an established toolset [11]. Model transformations are specified in UML-RSDS as UML use cases, defined declaratively by three main predicates, expressed in a subset of OCL:
1) Assumptions Asm, which define when the transfor-mation is applicable.
2) Postconditions Post, which define the intended effect of the transformation at its termination. These are an ordered conjunction of OCL constraints (also termed
rules in the following) and also serve to define a
procedural implementation of the transformation. 3) Invariants Inv, which define expected invariant
prop-implementation perspective, the constraints of Post also define intended computation steps of the transformation: each com-putation step is an application of a postcondition constraint to a specific source model element or to a tuple of elements.
For example, an elementary transformation specification
τa2b on the languages S consisting of entity type A and T
consisting of entity type B (Figure 1) could be: (Asm) :
B→forAll(b | b.y ≥ 0)
(Post) :
A→forAll(a | B→exists(b | b.y = a.x→sqr()))
(Inv) :
B→forAll(b | A→exists(a | a.x = b.y→sqrt()))
The computation steps α of τa2b are applications of
B→exists(b | b.y = a.x→sqr()) to individual a : A. These
consist of creation of a new b : B instance and setting its y value to a.x∗ a.x. These steps preserve Inv: Inv ⇒ [α]Inv.
Figure 1. A to B Transformation τa2b
This example shows a typical situation, where the invariant is a dual to the postcondition, and expresses a form of min-imality condition on the target model: that the only elements of this model should be those derived from source elements by the transformation. In terms of the framework of [16], the source-target relation Rτ associated with a UML-RSDS
transformation τ is Post and Inv. As in the above example,
Rτ is not necessarily bijective. The forward direction of τ is
normally computed as stat(Post): the UML activity derived from Post when interpreted procedurally [10]. However, in order to achieve the correctness and hippocraticness properties,
Inv must also be considered: before stat(Post) is applied to the
source model m, the target model n must be cleared of elements which fail to satisfy Inv.
In the a2b example, the transformation τa2b× with postcon-dition constraints:
(CleanTarget1) :
B→forAll(b | not(b.y ≥ 0) implies
b→isDeleted())
(CleanTarget2) :
B→forAll(b | not(A→exists(a | a.x = b.y→sqrt()))
implies b→isDeleted())
is applied before τa2b, to remove all B elements which fail to
be in Ra2b with some a : A, or which fail to satisfy Asm.
e : E satisfying P”. That is, the Unique Instantiation pattern
[14] should be used to implement ‘check before enforce’ se-mantics. The forward transformation τ→is then the sequential composition τ×; τ of the cleanup transformation and the standard transformation (enhanced by Unique Instantiation).
In the reverse direction, the roles of Post and Inv are interchanged: elements of the source model which fail to satisfy Asm, or to satisfy Post with respect to some element of the target model should be deleted:
(CleanSource2) :
A→forAll(a | not(B→exists(b | b.y = a.x→sqr()))
implies a→isDeleted())
This cleanup transformation is denoted τa2b∼×. It is followed by an application of the normal inverse transformation τa2b∼ which has postcondition constraints Inv ordered in the corresponding order to Post. Again, Unique Instantiation is used for source model element creation. The overall reverse transformation is denoted by τ← and is defined as τ∼×; τ∼.
In the case of separate-models transformations with type 1 postconditions (Constraints whose write frame is disjoint from their read frame), Inv can be derived automatically from Post by syntactic transformation, the CleanTarget and CleanSource constraints can also be derived from Post, and from Asm. This is an example of a higher-order transformation (HOT) and is implemented in the UML-RSDS tools.
In general, in the following UML-RSDS examples, τ is a separate-models transformation with source language S and target language T, and postcondition Post as an ordered conjunction of constraints of the form:
(Cn) :
Si→forAll(s | SCond(s) implies
Tj→exists(t | TCond(t) and Pi,j(s, t)))
and Inv is a conjunction of dual constraints of the form (Cn∼) :
Tj→forAll(t | TCond(t) implies
Si→exists(s | SCond(s) and P∼i,j(s, t)))
where the predicates Pi,j(s, t) define the features of t from those
of s, and are invertible: an equivalent form P∼i,j(s, t) should exist, which expresses the features of s in terms of those of t, and such that
Si→forAll(s | Ti→forAll(t | Pi,j(s, t) = P∼i,j(s, t)))
under the assumptions Asm. Table I shows some examples of inverses P∼ of predicates P. The computation of these inverses are all implemented in the UML-RSDS tools (the
reverse option for use cases). More cases are given in [11].
The transformation developer can also specify inverses for particular Cn by defining a suitable Cn∼ constraint in Inv, for example, to express that a predicate t.z = s.x + s.y should be inverted as s.x = t.z− s.y.
Each CleanTarget constraint based on Post then has the form:
(Cn×) :
TABLE I. EXAMPLES OF PREDICATE INVERSES P(s,t) P∼(s, t) Condition t.g = s.f s.f = t.g Assignable features f , g t.g = s.f→sqrt() s.f = t.g→sqr() f , g non-negative attributes t.g = K∗ s.f + L s.f = (t.g− L)/K f , g numeric attributes Numeric constants K, L, K̸= 0
t.rr = s.r→including(s.p) s.r = t.rr→front() and rr, r ordered association ends t.rr = s.r→append(s.p) s.p = t.rr→last() p 1-multiplicity end
t.rr = s.r→sort() s.r = t.rr→asSet() r set-valued, rr ordered t.rr = s.r→asSequence()
R(s, t) and Q(s, t) R∼(s, t) and Q∼(s, t)
t.rr = TRef [s.r.idS] s.r = SRef [t.rr.idT] rr association end with idS primary key of SRef , element type TRef , idT primary key of TRef r association end with
element type SRef t.g = s.r.idS s.r = SRef [t.g] idS primary key of SRef ,
Attribute g r association end with
element type SRef Tj[s.idS].rr = TRef [s.r.idSRef ] Si[t.idT].r = SRef [t.rr.idTRef ] idS, idSRef primary
r has element type SRef , keys of Si, SRef
rr has element type TRef idT, idTRef primary keys of Tj, TRef
IV. PATTERNS FORBX
In this section, we give a patterns catalogue for bx, and give pattern examples in UML-RSDS.
A. Auxiliary Correspondence Model
This pattern defines auxiliary entity types and associations which link corresponding source and target elements. These are used to record the mappings performed by a bx, and to propagate modifications from source to related target elements or vice-versa, when one model changes.
Figure 2 shows a typical schematic structure of the pattern.
Figure 2. Auxiliary Correspondence Model pattern
Benefits: The pattern is a significant aid in change-propagation between models, and helps to ensure the correct-ness of a bx. Feature value changes to a source element s can
source and target languages, and the necessary actions in creat-ing and accesscreat-ing correspondence elements adds complexity to the transformation and adds to its execution time and memory requirements.
Related Patterns: This pattern is a specialisation of the
Auxiliary Metamodel pattern of [14].
Examples: This mechanism is a key facility of Triple Graph Grammars (TGG) [1][2], and correspondence traces are maintained explicitly or implicitly by other MT languages such as QVT-R [15].
In UML-RSDS, the pattern is applied by introducing aux-iliary attributes into source and target language entity types. These attributes are primary key/identity attributes for the entity types, and are used to record source-target element corre-spondences. Target element t : Tj is considered to correspond
to source element(s) s1 : S1, ..., sn : Sn if they all have the
same primary key values: t.idTj = s1.idS1, etc. The identity attributes are String-valued in this paper. The correspondence between a source entity Si and a target entity Tj induced by
equality of identity attribute values defines a language mapping or interpretation χ of Siby Tj in the sense of [13]:
Si 7−→ Tj
with Si→collect(idSi) = Tj→collect(idTj).
The existence of identity attributes facilitates element lookup by using the Object Indexing pattern [14], which defines maps from String to each entity type, permitting elements to be retrieved by the value of their identity attribute:
Tj[v] denotes the Tj instance t with t.idTj = v if v is a
postconditions Cn of the form
Si→forAll(s | SCond(s) implies
Tj→exists(t | TCond(t) and Pi,j(s, t)))
derived constraints Cn∆ can be defined for the incremental application of Cn to model increments (finite collections of creations, deletions and modifications of model elements).
The incremental version τ∆of a transformation τ is defined to have postconditions formed from the constraints Cn∆ for each postcondition Cn of τ , and ordered according to the order of the Cn in the Post of τ . In a similar way, target-source change propagation can be defined. Change propagation is implemented in UML-RSDS by the incremental mode of use case execution.
B. Cleanup before Construct
This pattern defines a two-phase approach in both forward and reverse transformations associated with a bx with relation
R: the forward transformation R→ first removes all elements
from the target model n which fail to satisfy R for any element of the source m, and then constructs elements of n to satisfy
R with respect to m. The reverse transformation R← operates
on m in the same manner.
Benefits: The pattern is an effective way to ensure the correctness of separate-models bx.
Disadvantages: There may be efficiency problems because for each target model element, a search through the source model for possibly corresponding source element may be needed. Elements may be deleted in the Cleanup phase only to be reconstructed in the Construct phase. Auxiliary Corre-spondence Model may be an alternative strategy to avoid this problem, by enforcing that feature values should change in response to a feature value change in a corresponding element, rather than deletion of elements.
Related Patterns: This pattern is a variant of the
Construc-tion and Cleanup pattern of [14].
Examples: An example is the Composers bx [4]. Im-plicit deletion in QVT operates in a similar manner to this pattern, but can only modify models (domains) marked as
enforced [15]. In UML-RSDS, explicit cleanup rules Cn×
can be deduced from the construction rules Cn, for mapping transformations, as described in Section III above. If identity attributes are used to define the source-target correspondence, then Cn× can be simplified to:
Tj→forAll(t | TCond(t) and
Si→collect(sId)→excludes(t.tId) implies
t→isDeleted())
and
Tj→forAll(t | TCond(t) and
Si→collect(sId)→includes(t.tId) and s = Si[t.tId]
and not(SCond(s)) implies t→isDeleted())
In the case that TCond(t) and SCond(s) hold for corresponding
s, t, but Pi,j(s, t) does not hold, t should not be deleted, but
Pi,j(s, t) should be established by updating t:
For a transformation τ , the cleanup transformation τ× has the above Cn×constraints as its postconditions, in the same order as the Cn occur in the Post of τ . Note that τ→ is τ×; τ , and
τ∆ is τ×; τ incrementally applied.
C. Unique Instantiation
This pattern avoids the creation of unnecessary elements of models and helps to resolve possible choices in reverse mappings. It uses various techniques such as traces and unique keys to identify when elements should be modified and reused instead of being created. In particular, unique keys can be used to simplify checking for existing elements.
Benefits: The pattern helps to ensure the Hippocraticness property of a bx by avoiding changes to a target model if it is already in the transformation relation with the source model. It implements the principle of ‘least change’ [17].
Disadvantages: The need to test for existence of elements adds to the execution cost. This can be ameliorated by the use of the Object Indexing pattern [14] to provide fast lookup of elements by their primary key value.
Examples: The key attributes and check-before-enforce semantics of QVT-R follow this pattern, whereby new elements of source or target models are not created if there are already elements, which satisfy the specified relations of the transfor-mation [16]. The E→exists1(e | P) quantifier in UML-RSDS is used in a similar way. It is procedurally interpreted as “create a new e : E and establish P for e, unless there already exists an e : E satisfying P” [11]. For bx, the quantifier exists should also be treated in this way. If a transformation uses identity attributes (to implement Auxiliary Correspondence Model), the quantifier E→exists(e | e.eId = v and P) can be interpreted as: “if E[v] exists, apply stat(P) to this element, otherwise create a new E instance with eId = v and apply stat(P) to it”. This ensures Hippocraticness.
D. Phased Construction for bx
This pattern defines a bx τ by organising Rτ as a union of
relations RSi,Tjwhich relate elements of entities Si and Tj which
are in corresponding levels of the composition hierarchies of the source and target languages. Figure 3 shows the typical schematic structure of the pattern. At each composition level there is a 0..1 to 0..1 relation (or more specialised relation) between the corresponding source and target entity types.
Benefits: The pattern provides a modular and extensible means to structure a bx.
Examples: The UML to relational database example of [15] is a typical case, where Package and Schema correspond at the top of the source/target language hierarchies, as do Class and Table (in the absence of inheritance), and Column and
Attribute at the lowest level.
In UML-RSDS a transformation defined according to this pattern has its Post consisting of constraints Cn of the form
Si→forAll(s | SCond(s) implies
Tj→exists(t | TCond(t) and Pi,j(s, t)))
where Si and Tj are at corresponding hierarchy levels, and Inv
consists of constraints Cn∼ of the form
Tj→forAll(t | TCond(t) implies
Si→exists(s | SCond(s) and P∼i,j(s, t)))
No nested quantifiers or deletion expressions x→isDeleted() are permitted in SCond, TCond or Pi,j, and Pi,j is restricted to
be formed of invertible expressions.
Each rule creates elements t of some target entity type
Tj, and may lookup target elements produced by preceding
rules to define the values of association end features of
t: t.tr = TSub[s.sr.idSSub] for example, where TSub is lower
than Tj in the target language composition hierarchy (as in
Figure 3) and there are identity attributes in the entities to implement a source-target correspondence at each level. Both forward and reverse transformations will conform to the pattern if one direction does. The assignment to t.tr has inverse:
s.sr = SSub[t.tr.idTSub].
Two UML-RSDS bx τ : S → T, σ : T → U using this pattern can be sequentially composed to form another bx between S and U: the language T becomes auxiliary in this new transformation. The forward direction of the composed transformation is τ→; σ→, the reverse direction is σ←; τ←.
E. Entity Merging/Splitting for bx
In this variation of Phased Construction, data from multiple source model elements may be combined into single target model elements, or vice-versa, so that there is a many-one relation from one model to the other. The pattern supports the definition of such bx by including correspondence links between the multiple elements in one model which are related to one element in the other.
Benefits: The additional links enable the transformation to be correctly reversed.
Disadvantages: Additional auxiliary data needs to be added to record the links. The validity of the links between elements needs to be maintained. There may be potential conflict between different rules which update the same element. Related Patterns: This uses a variant of Auxiliary Cor-respondence Model, in which the corCor-respondence is between elements in one model, in addition to cross-model dences. The attributes used to record intra-model
correspon-that represents this class. The Pivot/Unpivot transformation of [3] is an example of Entity Splitting.
In the general case of merging/splitting, the inverse of Cn:
Si1→forAll(s1 | ...
Sin→forAll(sn | SCond(s1, ..., sn) implies
Tj1→exists(t1 | ...
Tjm→exists(tm | TCond(t1, ..., tm) and
P(s1, ..., sn, t1, ..., tm))...)) ...)
is Cn∼:
Tj1→forAll(t1 | ...
Tjm→forAll(tm | TCond(t1, ..., tm) implies
Si1→exists(s1 | ...
Sin→exists(sn | SCond(s1, ..., sn) and
P∼(s1, ..., sn, t1, ..., tm))...))...) In UML-RSDS, correspondence links between elements in the same model are maintained using additional attributes. All elements corresponding to a single element will have the same value for the auxiliary attribute (or a value derived by a 1-1 function from that value).
F. Map Objects Before Links for bx
If there are self-associations on source entity types, or other circular dependency structures in the source model, then this variation on Phased Construction for bx can be used. This pattern separates the relation between elements in target and source models from the relation between links in the models. Benefits: The specification is made more modular and extensible. For example, if a new association is added to one language, and a corresponding association to the other language, then a new relation relating the values of these features can be added to the transformation without affecting the existing relations.
Disadvantages: Some features of one entity type are treated in separate relations.
Examples: In UML-RSDS a first phase of such a transfor-mation relates source elements to target elements, then in a second phase source links are related to corresponding target links. The second phase typically has postcondition constraints of the form Si→forAll(s | Tj[s.idS].rr = TRef [s.r.idSRef ]) to
define target model association ends rr from source model association ends r, looking-up target model elements Tj[s.idS]
and TRef [s.r.idSRef ] which have already been created in a first phase. Such constraints can be inverted to define source data from target data as: Tj→forAll(t | Si[t.idT].r =
SRef [t.rr.idTRef ]). The reverse transformation also conforms
to the Map Objects Before Links pattern.
An example of this pattern is the tree to graph transforma-tion [9], Figure 4.
A first rule creates a node for each tree:
Tree→forAll(t | Node→exists(n | n.label = t.label))
Figure 4. Tree to graph metamodels
The corresponding invariant predicates, defining the reverse transformation, are:
Node→forAll(n | Tree→exists(t | t.label = n.label))
and
Edge→forAll(e |
Tree→exists(t | Tree→exists(p |
t.parent→includes(p) and
t.label = e.source.label and p.label = e.target.label)))
Inv is derived mechanically from Post using Table I, and
pro-vides an implementable reverse transformation, since stat(Inv) is defined.
V. RELATEDWORK
There are a wide range of approaches to bx [8]. Cur-rently the most advanced approaches [2][5] use constraint-based programming techniques to interpret relations P(s, t) between source and target elements as specifications in both forward and reverse directions. These techniques would be a potentially useful extension to the syntactic inverses defined in Table I, however the efficiency of constraint programming will generally be lower than the statically-computed inverses. The approach also requires the use of additional operators extend-ing standard OCL. Further techniques include the inversion of recursively-defined functions [18], which would also be useful to incorporate into the UML-RSDS approach.
In [13] we identify the role of language interpretations
χ : S → T in specifying transformations. Interpretations are
closely related to transformation inversion: at the model level a mapping Mod(χ) : Mod(T)→ Mod(S) from the set of models of T to those of S can be defined based on χ: the interpretation of an S language element E in Mod(χ)(n) for n : Mod(T) is that of χ(E) in n. Syntactically, the inverse of a transformation
τ specified by a language morphism χ can be derived from χ:
the value of a feature f of source element s of source entity
E is set by s.f = t.χ(E :: f ) in the case of an attribute, and
by s.r = SRef [t.χ(E :: r).idTRef ] in the case of a role with element type SRef .
relation R with a changed other model, should make a minimal possible such change to the model. In our approach, Post in the forward direction, and Inv in the reverse direction, express the necessary minimal conditions for the models to be related by R. The synthesised implementation of these constraints as executable code carries out the minimal changes necessary to establish Post and Inv, and hence satisfies the principle of least change.
VI. CONCLUSION
We have defined a declarative approach for bidirectional transformations based on the derivation of forward and reverse transformations from a specification of dual postcondition and invariant relations between source and target models. The approach enables a wide range of bx to be defined, including cases of many-to-one and one-to-many relations between models, in addition to bijections. We have described transformation patterns which may be used to structure bx. The derivation of reverse transformations has been implemented in the UML-RSDS tools [11].
REFERENCES
[1] A. Anjorin and A. Rensink, “SDF to Sense transformation”, TU Darmstadt, Germany, 2014.
[2] A. Anjorin, G. Varro, and A. Schurr, “Complex attribute manipulation in TGGs with constraint-based programming techniques”, BX 2012, Electronic Communications of the EASST vol. 49, 2012.
[3] M. Beine, N. Hames, J. Weber, and A. Cleve, “Bidirectional transfor-mations in database evolution: a case study ‘at scale’”, EDBT/ICDT 2014, CEUR-WS.org, 2014.
[4] J. Cheney, J. McKinna, P. Stevens, and J. Gibbons, “Towards a reposi-tory of bx examples”, EDBT/ICDT 2014, 2014, pp. 87–91.
[5] A. Cicchetti, D. Di Ruscio, R. Eramo, and A. Pierantonio, “JTL: a bidirectional and change propagating transformation language”, SLE 2010, LNCS vol. 6563, 2011, pp. 183–202.
[6] K. Czarnecki, J. Nathan Foster, Z. Hu, R. Lammel, A. Schurr, and J. Terwilliger, “Bidirectional transformations: a cross-discipline perspec-tive”, GRACE workshop, ICMT, 2009.
[7] E. Gamma, R. Helm, R. Johnson, and J. Vlissides, “Design Patterns: Elements of Reusable Object-Oriented Software”, Addison-Wesley, 1994.
[8] Z. Hu, A. Schurr, P. Stevens, and J. Terwilliger (eds.), “Report from Dagstuhl Seminar 11031”, January 2011, www.dagstuhl.de/11031. [9] D. S. Kolovos, R. F. Paige, and F. Polack, “The Epsilon Transformation
Language”, ICMT, 2008, pp. 46–60.
[10] K. Lano and S. Kolahdouz-Rahimi, “Constraint-based specification of model transformations”, Journal of Systems and Software, vol. 88, no. 2, February 2013, pp. 412–436.
[11] K. Lano, The UML-RSDS Manual,
www.dcs.kcl.ac.uk/staff/kcl/uml2web/umlrsds.pdf, 2015.
[12] K. Lano, S. Kolahdouz-Rahimi, and K. Maroukian, “Solving the Petri-Nets to Statecharts Transformation Case with UML-RSDS”, TTC 2013, EPTCS, 2013, pp. 101–105.
[13] K. Lano and S. Kolahdouz-Rahimi, “Towards more abstract specifica-tion of model transformaspecifica-tions”, ICTT 2014.
[14] K. Lano and S. Kolahdouz-Rahimi, “Model-transformation Design Patterns”, IEEE Transactions in Software Engineering, vol 40, 2014, pp. 1224–1259.
[15] OMG, MOF 2.0 Query/View/Transformation Specification v1.1, 2011. [16] P. Stevens, “Bidirectional model transformations in QVT: semantic issues and open questions”, SoSyM, vol. 9, no. 1, January 2010, pp. 7–20.