Publisher’s version / Version de l'éditeur:
Vous avez des questions? Nous pouvons vous aider. Pour communiquer directement avec un auteur, consultez la première page de la revue dans laquelle son article a été publié afin de trouver ses coordonnées. Si vous n’arrivez pas à les repérer, communiquez avec nous à PublicationsArchive-ArchivesPublications@nrc-cnrc.gc.ca.
Questions? Contact the NRC Publications Archive team at
PublicationsArchive-ArchivesPublications@nrc-cnrc.gc.ca. If you wish to email the authors directly, please see the first page of the publication for their contact information.
https://publications-cnrc.canada.ca/fra/droits
L’accès à ce site Web et l’utilisation de son contenu sont assujettis aux conditions présentées dans le site LISEZ CES CONDITIONS ATTENTIVEMENT AVANT D’UTILISER CE SITE WEB.
Student Report; no. SR-2009-13, 2009-01-01
READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THIS WEBSITE.
https://nrc-publications.canada.ca/eng/copyright
NRC Publications Archive Record / Notice des Archives des publications du CNRC : https://nrc-publications.canada.ca/eng/view/object/?id=7c5db1fa-1ed9-4190-9d2f-529836410e86 https://publications-cnrc.canada.ca/fra/voir/objet/?id=7c5db1fa-1ed9-4190-9d2f-529836410e86
NRC Publications Archive
Archives des publications du CNRC
For the publisher’s version, please access the DOI link below./ Pour consulter la version de l’éditeur, utilisez le lien DOI ci-dessous.
https://doi.org/10.4224/18238675
Access and use of this website and the material on it are subject to the Terms and Conditions set forth at Deployment of Anti-Virus Definitions through McAfee ePolicy Orchestrator
National Research Council Canada Institute for Ocean Technology Conseil national de recherches Canada Institut des technologies oc ´eaniques
SR-2009-13
Student Report
Deployment of Anti-Virus Definitions through McAfee
ePolicy Orchestrator.
Gash, R.
Gash, R., 2009. Deployment of Anti-Virus Definitions through McAfee ePolicy Orchestrator. St. John's, NL : NRC Institute for Ocean Technology. Student Report, SR-2009-13.
DOCUMENTATION PAGE
REPORT NUMBER
SR-2009-13
NRC REPORT NUMBER DATE
August 21, 2009 REPORT SECURITY CLASSIFICATION
Unclassified
DISTRIBUTION Unlimited TITLE
DEPLOYMENT OF ANTI-VIRUS DEFINITIONS THROUGH MCAFEE EPOLICY ORCHESTRATOR
AUTHOR(S) Robert Gash
CORPORATE AUTHOR(S)/PERFORMING AGENCY(S)
Institute for Ocean Technology (IOT), National Research Council (NRC) PUBLICATION
SPONSORING AGENCY(S) IOT PROJECT NUMBER 421020
NRC FILE NUMBER
KEY WORDS
Anti-Virus, Batch Script, DAT, ENGINE, Firewall, Group Policy, McAfee ePolicy Orchestrator, SQL
PAGES 28 FIGS. 13 TABLES 0 SUMMARY
McAfee ePolicy Orchestrator is a Windows server-end McAfee VirusScan management application. It is used in order to manage the automatic updating of anti-virus definitions, engines, and patches for VirusScan on Windows systems. It allows easy monitoring for anti-virus distribution, as well as custom alerting in the event of anti-virus outbreaks or other related security threats. This report contains the methods in which to install, configure, and manage this software effectively in the IOT environment, and offers suggestions as to how it can be further improved.
ADDRESS National Research Council Institute for Ocean Technology Arctic Avenue, P. O. Box 12093 St. John’s, NL A1B 3T5
National Research Council Conseil national de recherches Canada Canada
Institute for Ocean Institut des technologies Technology océaniques
DEPLOYMENT OF ANTI-VIRUS DEFINITIONS THROUGH
MCAFEE EPOLICY ORCHESTRATOR
SR-2009-13 Robert Gash August 2009
ii CONTENTS
LIST OF FIGURES... iii
1 INTRODUCTION ... 1
1.1 Previous IOT Anti-Virus Update Methods ... 1
1.2 Issues Regarding Previous Update Methods ... 1
1.3 Current Usage of McAfee ePolicy Orchestrator ... 3
2 INSTALLATION ISSUES AND REQUIREMENTS ... 3
2.1 Installing on Windows Server with McAfee Anti-Virus ... 3
2.2 Port Configurations ... 4
2.3 Authentication ... 5
3 REGULAR ePO MANGEMENT ... 6
3.1 Adding Network PCs ... 6
3.2 Adding New McAfee Products ... 11
3.3 DAT File Distribution ... 13
3.3.1 Automatic updating ... 14
3.3.2 Manual updating ... 17
3.4 Compliance Testing and Notifications ... 17
3.5 Custom Policies ... 19
4 Conclusion ... 21
5 Recommendations ... 21
REFERENCES ... 23 APPENDIX A... A-1
iii
LIST OF FIGURES
Figure 1 – Disabling McAfee Service Protection – pg. 4 Figure 2 – McAfee ePO Server Port Configuration – pg. 5 Figure 3 – McAfee Authentication Settings – pg. 6
Figure 4 – Windows Firewall Group Policy Settings – pg. 7 Figure 5 – Importing Active Directory Containers – pg. 8 Figure 6 – Sending Agent Install – pg. 9
Figure 7 – Batch Script Function – pg. 10
Figure 8 – Checking In McAfee Products – pg. 12 Figure 9 – McAfee DAT File Distribution – pg. 13 Figure 10 – Repository Pull Task Settings – pg. 15 Figure 11 – Editing Scheduled Update Tasks – pg. 16 Figure 12 – ePO Generated Reporting – pg. 18
1 1 INTRODUCTION
1.1 Previous IOT Anti-Virus Update Methods
The anti-virus software currently used at the Institute for Ocean Technology is McAfee VirusScan Enterprise. Prior to August 2009, IOT used batch login scripts to distribute anti-virus definitions and scanning engines to over 200 PCs in the building. Every day, new definitions are released from McAfee in the form of DAT files. Once the DAT files have been released, an e-mail notification is sent to the Computer Systems Help Desk. A system administrator previously had to download these files manually to a common shared network folder. A batch script with declared variables for DAT version numbers would then be changed to correspond to the new DAT version. This batch script would be called during the NT Login process on all Windows systems connected to the IOTPC domain.
1.2 Issues Regarding Previous Update Methods
While login scripts are very effective at keeping systems updated, several issues with this method cause inefficiencies in day-to-day operations. Each daily DAT file is typically over 100 MB in size and McAfee does not currently offer incremental upgrades.
The DAT files, which were distributed through the batch scripts, were standalone Windows executable files. These files must download, decompress, unpack, and install (requiring the automatic restarting of McAfee processes and services).
2
This alone is very CPU and memory intensive (especially as executing the DAT file does so at a regular system priority), and doing so on login slows the Windows loading process significantly. With DAT files growing larger, users getting updates through this method are noticing significantly long boot times. This is not only an annoyance, but also hinders productivity.
A large number of computers in the building running the Windows operating system are used for data collection and modeling. These systems often run for many days at a time in order to do calculations or to provide resources. A number of users are also choosing to leave their computers on for extended periods of time in order to avoid the hassle of a lengthy startup times. As these systems do not restart, they would often go weeks (or longer) without critical updates and patches and therefore be left wide open to new threats.
During peak login hours, particularly in the morning, it’s common for over 100 computers to connect to the server around the same time and begin downloading the 100 MB update file. While not a major concern, this would have put a higher strain on the network and could have potentially slowed down certain network resources.
From a system administration standpoint, batch updates require daily manual effort in order to download DATs and edit scripts. Since the scripts can be terminated on login, it’s possible for some users to circumvent updates. It is also hard to determine how many systems are receiving updates regularly and if there are any problem areas.
3
1.3 Current Usage of McAfee ePolicy Orchestrator
Upon discussion, research, and testing of possible alternatives to the update process (as well as the feasibility of switching anti-virus software), the decision was made to use McAfee ePolicy Orchestrator 3.6.1 (ePO) as a solution to the issues mentioned above. McAfee ePO is server-end software designed to manage McAfee products. Using McAfee Agent software on networked PCs (already included with installations of McAfee VirusScan Enterprise), ePO is able to make regular communication with client systems in order to distribute DATs, patches, and custom policies. It has the ability to schedule tasks for distributing updates, randomize update-pushing events to reduce network strain, run updates at low system priority to reduce interference, and distribute updates regularly without requiring systems to restart. Once configured, this software also provides a great deal of automation to the updating process and offers system administrators more control over anti-virus software in the building through the use of custom policies and agent monitoring reports.
2 INSTALLATION ISSUES AND REQUIREMENTS
2.1 Installing on Windows Server with McAfee Anti-Virus
McAfee requires that the ePO software be installed on a Windows Server machine. If installing ePO on a server that already has McAfee VirusScan
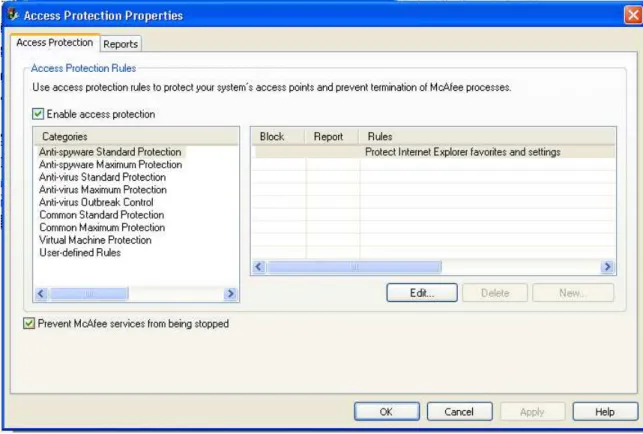
4
Enterprise installed, the “Prevent McAfee services from being stopped” option must be deselected from the Access Protection properties within the VirusScan console (shown below in Figure 1). Otherwise, the installation (which requires the restarting of McAfee Services) will fail.
Figure 1 – Disabling McAfee Service Protection
2.2 Port Configurations
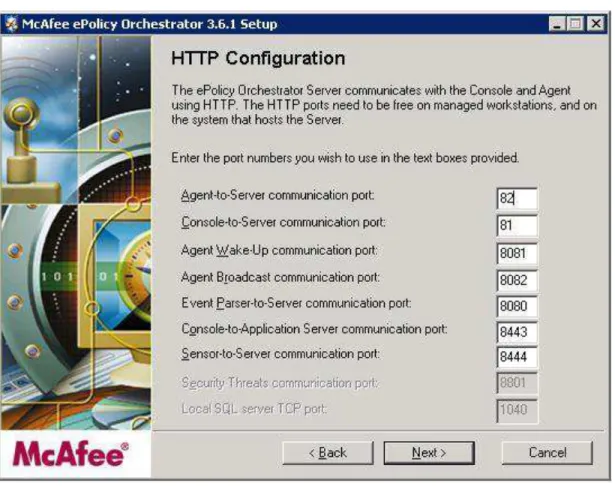
During the install and initial configuration of McAfee ePO, a multitude of ports must be specified for the server to use in regular operation. Most of these can be set to the recommended install default unless the server used already requires that TCP port 80 be open for another service (i.e., Web or WSUS). ePO is currently hosted from Tesla (IOT’s WSUS server), and therefore another port
5
(82) must be chosen for Agent-to-Server communication. Port 82 is recommended as the communication is http-based using a lightweight Apache server. Full port configuration is shown in Figure 2 below:
Figure 2 – McAfee ePO Server Port Configuration
2.3 Authentication
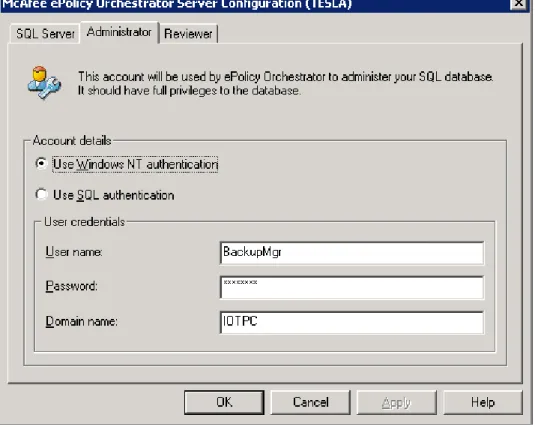
Once the server software is installed, regular management is done through the ePO Console software installed on Tesla. The data and configuration settings accessible from the console are located in an SQL database served from Tesla and require either the NT Domain Administrator credentials of the database creator or SQL database owner credentials. The recommended setup for the IOT
6
environment would be to use SQL authentication, but due to configuration issues, ePO currently uses NT Domain Administrator authentication. If the NT account assigned to owner of the SQL database changes, the server must be configured to accept this change. Authentication can be changed via the CfgNaiMs.exe program (shown in Figure 3) located in C:\Program Files\McAfee\ePO\3.6.1.
Figure 3 – McAfee Authentication Settings
3 REGULAR ePO MANGEMENT 3.1 Adding Network PCs
Before any PCs can be managed under ePO, Windows Firewall settings must be configured to allow communication between the PCs and the ePO server. As
7
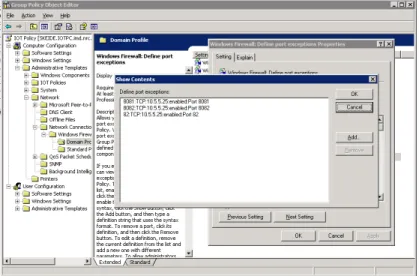
shown in the port settings listed in Figure 2, McAfee Agents require TCP ports 82, 8081, and 8082 to be open within the scope of Tesla. The agent also requires File and Printer sharing with Tesla for distribution of software. Windows XP SP2 and newer versions of Windows require that these settings be configured on Windows Firewall through NT Domain Group Policy settings.
Figure 4 – Windows Firewall Group Policy Settings
To do this, the IOTPC group policy must be edited under Administrative Templates > Network > Network Connections > Windows Firewall as seen in Figure 4 above (Deploying Windows Firewall). These changes must be made to both the Domain and Standard profiles.
Once Windows Firewall Group Policy settings have been applied, PCs can be added to ePO management. There are many ways to do this but the following practices are recommended:
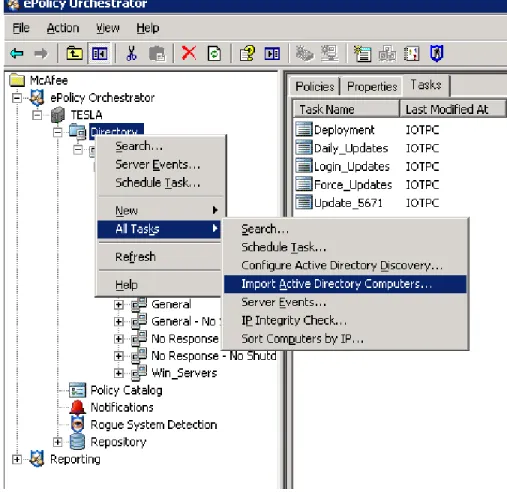
1) Active Directory Import: The most efficient way of initially adding PCs to ePO management is through importing containers of computers from the
8
Active Directory. This can be done within the ePO console by expanding the TESLA tree and right-clicking Directory, selecting All Tasks, and then selecting “Import Active Directory Computers” (Figure 5).
Figure 5 – Importing Active Directory Containers
Once a list of computers is generated, create groups of PCs and distribute Agent activations (below) in small sections until the majority of computers are under ePO management.
2) Individual PC Agent Deployment: Once the majority of computers are imported, begin installs to individual groups or computers. If the computer is not already listed, add it to a group by right-clicking, selecting New, and
9
then selecting Computer. To push the agent install, right-click on the individual system or group and then select Send Agent Install (Figure 6) giving it administrator privileges.
Figure 6 – Sending Agent Install
Other options, such as hiding the Graphical User Interface of the install from the user, can also be specified. Once the agent is installed, the computer will make contact with the ePO server when it reaches its communication interval time. This usually takes 10 minutes but can take up to an hour. Server communication can be forced sooner by selecting “Agent Wakeup Call” (Figure 6).
10
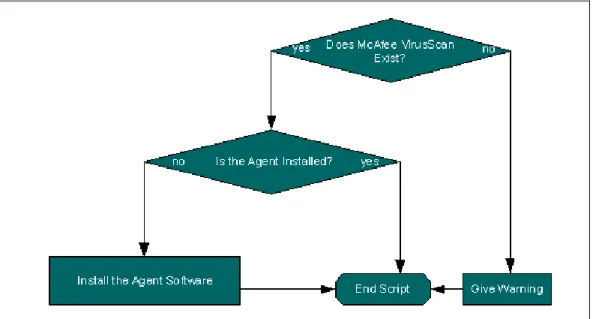
3) Batch script installers and login redundancy tests: Once the PC network is mostly managed by ePO, a batch script can be written to test the existence of an agent install on the required system. The script can also be used to start manual McAfee agent install executables created by logging into the McAfee ePO console and selecting the link to the “Package Creation Wizard” (creating an executable with the name FRAMEPKG.EXE). Using this script ensures that all systems logging into the domain IOTPC will have the agent software installed and can silently install the software if required. Such a script would function as follows in Figure 7:
Figure 7 – Batch Script Function
When an agent is installed on a machine, a registry entry is made which references the ePO server. The script could test the existence of the agent by testing if the registry entry existed. Running FRAMEPKG.EXE will ensure the agent installed along with VirusScan is complete and up-to-date. Once the agent installer has executed, a series of commands is required in order to
11
configure the agent and call into the server. An XML site list file must be exported in order to point the agent to the server. This file can be generated by expanding the “Repository” tree in the ePO console and selecting “Software Repositories”. At the top of the right-pane, select “Export Repository list”. An example of a basic script structure doing all of this is shown as follows:
@ECHO OFF
REM Check for McAfee installation
IF EXIST %McAfeeDirectory% GOTO TEST GOTO NOAV
REM Check for Agent installation :TEST
REG QUERY “hklm\Software\Network Associates\ePolicy Orchestrator \Agent” /v “ePOServerList” | find /I “TESLA”
IF ERRORLEVEL 1 GOTO FAIL IF ERRORLEVEL 0 GOTO END
REM Stop existing agent processes, install new agent files, REM activate agent, communicate with server
:FAIL
START /w %McAfeeDirectory%\FRMINST /remove=agent /s START /w %ServerDirectory%\FRAMEPKG /install=AGENT
START /w %McAfeeDirectory%\FRMINST /install=agent /siteinfo= %ServerDirectory%\sitelist.xml /s
START /w %McAfeeDirectory%\CMDAGENT /p GOTO END
:NOAV
ECHO No Anti-Virus found! Please contact HelpDesk! PAUSE
:END
The full script used by IOT can be found as Appendix A in this report.
3.2 Adding New McAfee Products
In order to manage settings and information about software and DAT coverage, each piece of software used must be registered with the ePO database. This
12
requires newer versions of McAfee software be registered with ePO before deploying it. As of this report, IOT uses McAfee VirusScan and AntiSpyware versions 8.0, 8.5, and 8.7 and is configured to manage only these products.
Although optional, an administrator can push the software installation package from the server to a client PC if they “Check-In” a McAfee catalog.z file. To do this, select “Repository” from the tree on the left-hand side. In the right-hand panel, select “Check in package” as shown below in Figure 8. Browse to the directory where the product install files are located.
13
To manage this software from the server, select the “Check in NAP” option also shown above. As before, browse to the directory where the product install files are located. Once these NAP files are checked into the ePO server, custom Policies can be created to further manage the settings of the software (see section 3.5).
3.3 DAT File Distribution
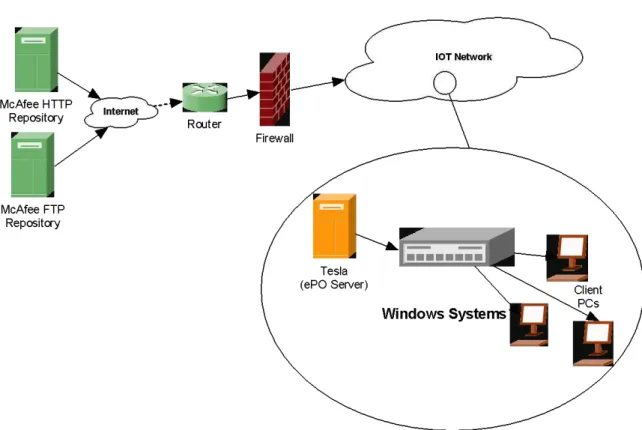
Figure 9 – McAfee DAT File Distribution
The McAfee DAT file distribution scheme shown above in Figure 9 is a graphical representation of the path in which McAfee Anti-Virus Updates are pushed. The Tesla ePO Server will make contact with the McAfee Repository servers
14
requesting availability of updates. If available, Tesla will automatically download them. Tesla will then push the updates out to all connected systems. Scheduled tasks will ensure all other systems are updated.
3.3.1 Automatic updating
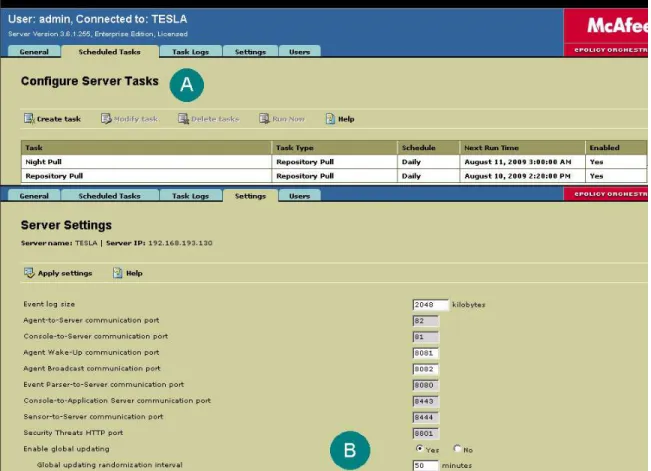
McAfee ePO automation is achieved through the use of scheduled tasks. The first task must be to pull DAT, Engine, and software updates if available. To create or manage a pull task, select “TESLA” from the left-hand tree and then select the “Scheduled Tasks” tab from within the ePO console. From this window (shown in Figure 10 A), you can create new tasks or modify existing ones. There are currently two tasks for redundancy.
15
Figure 10 – Repository Pull Task Settings
Once the pull task has completed, updates are automatically pushed to client systems one of two ways. McAfee can use a process known as “Global Updating” to immediately update all currently running systems. This is set through the “Settings” tab (Figure 10 B). To manage network strain, a “randomization interval” can be set to distribute a set number of updates per minute. The number of systems divided by the randomization interval will equal the number of systems updated per minute. The current setting is 50 minutes (ensuring that around 4 to 5 systems will get their updates per minute). The other method in which systems can receive updates is through the use of Agent Update tasks. These tasks can be set to run at login, when systems are idle, or
16
at set times. To set an Agent Update task, right click on a specific group or computer from the left-hand tree and select “All Tasks” > “Schedule Task” > “ePolicy Orchestrator Agent: Update”.
Figure 11 – Editing Scheduled Update Tasks
To edit the new task, select the “Tasks” tab at the top of the right-hand pane and right click. Select “Edit Task” and use the “Settings” button to choose what will be updated using the task (Figure 11). Use the “Schedule” tab to select a time and enable the task to run it.
To ensure thorough updates, certain tasks should be set to run at least once a month (such as update on login or when idle). This will ensure that computers that are not connected to the network regularly (such as notebooks) or
17
computers that are only powered on when required (such as DAS PCs) receive updates.
3.3.2 Manual updating
In the event that the scheduled automatic pull tasks fail (or an emergency set of definitions is released from McAfee), it is possible to manually pull the updates and push them.
To download the most recent updates, Select “Repository” from the right-hand side. Select the link that says “Pull Now” (Figure 8) and use the wizard to start the download. Once new DAT, engine, or patch files have been downloaded, Global Updating will automatically distribute them to active systems. To target specific systems, expand the “Directory” tree on the left-hand side and select the PC required. Create an Agent Update task to “Run Immediately” (See section 3.1.1).
3.4 Compliance Testing and Notifications
Administrators will want to test update coverage throughout the network to ensure that the ePO server is functioning correctly and that automated tasks are optimized for best distribution. This can be checked through the ePO server’s SQL database.
18
Within the ePO console installed on Tesla, administrators can test compliance by using ePO-generated reports. This can be done by selecting and expanding the “Reporting” tree, and expanding “ePO Databases”” > “ePO_TESLA” > “Reports” > “Anti-Virus” > “Coverage” (Figure 12).
Figure 12 – ePO Generated Reporting
There are many different reports that can be generated from this. One of the most useful reports is the “DAT/Definition Deployment Summary”. This report (when not filtered) can show the versions of DATs deployed throughout the building and list computers with Anti-Virus uninstalled. Tracking compliance is important for network administrators (Cole, Fossen, et. al.). This information can
19
be used to schedule redundancy tasks such as updating while idle or on login (see section 3.3).
E-mail notifications can be sent to administrators in the event of a software error or virus outbreak. This can aid in the ability to contain problematic systems. E-mail notifications can be configured using by selecting “Notifications” from the left-hand tree. Current settings will send an e-mail to IOT Help Desk in the event that a virus is detected and not removed over six machines, if over one hundred instances of the same virus are found and not removed, or if a user attempts to uninstall McAfee products.
3.5 Custom Policies
All McAfee products can be managed through custom policies once a product’s NAP file is “checked-in” to ePO (see section 3.2). Custom policies can be set for both McAfee Agents as well as McAfee VirusScan Enterprise. Of particular importance for agents is that policies should be defined to minimize the impact of the ePO Agent on user-systems (configure for least-obtrusive resource consumption).
Policies are designed to delegate control over all managed McAfee software. This results in users being unable to remove or disable default McAfee settings, particularly that of VirusScan Enterprise. In the event that a user attempts to disable a default setting (or add a program exception), the user will be successful
20
until the next period of Agent-to-Server communication (currently set to 60 minute intervals).
To define custom policies for an individual system or group of systems, highlight the object from the left-hand side and select the “Policy” tab from the right-hand pane. Custom policies must be designed for each in-use version of McAfee VirusScan. Click “Edit” to create a new policy mimicking that of the McAfee Default policy and then change settings as desired (see example in Figure 13 below).
21 4 Conclusion
McAfee ePolicy Orchestrator as been installed on almost all PCs in the IOT Computer Systems managed environment. Batch login scripts test to ensure that systems are managed by ePO and install ePO to systems that are not. Updates are regularly distributed to all systems as seen through reporting, and virus detection reports can already be viewed.
As well as effective update distribution, computer login times are now faster. The software is very effective in distributing server bandwidth, and many of the issues presented in Section 1 have been solved.
5 Recommendations
McAfee ePolicy Orchestrator was implemented over a limited period of time. As such, there are several issues which the author wishes were further investigated.
i) SQL Authorization: The McAfee ePO console currently uses NT Domain authorization for access to and administration rights to the ePO MSSQL database (see section 2.3). The preferred method would be to set up a SQL account as the database administrator. This would avoid the issue of changing database privilege settings upon password changes of the NT account.
ii) Improved Update Policy: While the current policies and update tasks in place are effective, some custom tasks should be designed for the purpose of updating IOT notebooks and PCs that are rarely active.
22
These systems should be placed in a custom group to receive updates on login and/or when idle.
23
REFERENCES
Cole, Fossen, et. al. SANS Security Esssentials and the CISSP 10 Domains: 1.2 Defense In-Depth. SANS Press, 2004. 95-96.
“Deploying Windows Firewall Settings With Group Policy.” 17 Dec. 2004. Microsoft Tech Net. 30 June 2009 <http://technet.microsoft.com/en-us/ Library/bb490626.aspx>.
Elms, Wayne. Computer Systems Group. Institute for Ocean Technology. St. John’s, NL, Canada. Personal Correspondence. 2009.
Walsh, Doug. Computer Systems Group. Institute for Ocean Technology. St. John’s, NL, Canada. Personal Correspondence. 2009.
Wong, Gilbert. Computer Systems Group. Institute for Ocean Technology. St. John’s, NL, Canada. Personal Correspondence. 2009.
A-1
APPENDIX A
A-2
NOTE: The word processor used removed some of the spacing in the original script. Any line starting with non-batch syntax is a continuation of the previous line.
@ECHO OFF
REM This script will test if the McAfee ePO Agent is installed on the REM local machine. If the Agent is not installed, It will activate the REM Agent already REM installed with McAfee Anti-Virus Enterprise and REM report back to the server. If no REM Anti-Virus is detected, It REM will display an error.
REM Last updated 06-Aug-2009 RG, rmgash@gmail.com REM (AV8.5/8.7, Agent 3.5/3.6/4.0)
REM Check for the McAfee installation (both locations of McAfee)
if exist %SystemDrive%"\Program Files\McAfee\VirusScan Enterprise\" GOTO MCTEST1
if exist %SystemDrive%"\Program Files\Network Associates\VirusScan\ "
GOTO MCTEST2 GOTO NOAV
REM Check for instance of TESLA in Agent reg entry :MCTEST1
reg query "hklm\Software\Network Associates\ePolicy Orchestrator\Agent" /v "ePOServerList" | find /i "TESLA" IF ERRORLEVEL 1 GOTO FAIL1
IF ERRORLEVEL 0 GOTO END
:MCTEST2
reg query "hklm\Software\Network Associates\ePolicy Orchestrator \Agent" /v "ePOServerList" | find /i "TESLA"
IF ERRORLEVEL 1 GOTO FAIL2 IF ERRORLEVEL 0 GOTO END
REM Stop existing agent processes, install new agent files, activate REM agent, communicate with server
:FAIL1 ECHO.
ECHO Installing McAfee Agent...Please Wait... ECHO.
START /w %SystemDrive%"\Program Files\McAfee\Common Framework\" FRMINST.EXE /remove=agent /s
START /w \\Karfe\PCcommon\SOFTWARE\MCAFEE\FRAMEPKG.EXE /install= AGENT
START /w %SystemDrive%"\Program Files\McAfee\Common Framework\" FRMINST.exe /install=agent /siteinfo=N:\Software\McAfee\
sitelist.xml /s
START /w %SystemDrive%"\Program Files\McAfee\Common Framework\" CMDAGENT.exe /p
GOTO END
:FAIL2 ECHO.
A-3
ECHO Installing McAfee Agent...Please Wait... ECHO.
START /w %SystemDrive%"\Program Files\Network Associates\Common Framework\"FRMINST.EXE /remove=agent /s
START /w \\Karfe\PCcommon\SOFTWARE\MCAFEE\FRAMEPKG.EXE /install=AGENT
START /w %SystemDrive%"\Program Files\Network Associates\Common Framework\"FRMINST.exe /install=agent
/siteinfo=N:\Software\McAfee\sitelist.xml /s
START /w %SystemDrive%"\Program Files\Network Associates\Common Framework\"CMDAGENT.exe /p
GOTO END
:NOAV echo.
echo !!!! WARNING !!!! McAfee Anti-Virus/SpyWare software NOT found.
echo.
echo Please contact Computer Systems Help Desk at 685-2587. echo.
PAUSE :END