Applying Systems Thinking Towards Countering Hybrid Warfare
by
Peihao Raymond Tan
B. Eng. (Hons) Electrical Electronics Engineering
National University of Singapore, 2009
Submitted to the MIT System and Design Management Program in Partial Fulfillment of the Requirements for the Degree of
Master of Science in Engineering and Management at the
Massachusetts Institute of Technology
February 2019
2019 Peihao Raymond Tan. All rights reserved.
The author hereby grants to MIT permission to reproduce and to distribute publicly paper and electronic copies of this thesis document in whole or in part in any medium now known or
hereafter created.
Signature redacted
Signature of Author Certified by Accepted by_ MASSACHUSETTS INSTITUTE OF TECHNOLOGY
MAR 142019
LIBRARIES
Peihao Raymond Tan MIT System and Design Management Program 'January 10, 2019
Signature redacted
Donna H. Rhodes Principal Research Scientist, Sociotechnical Systems Research Center Director, Systems Engineering Advancement Research Initiative (SEAri) Thesis Supervisor
Signature redacted
I
Joan RubinExecutive Director, System Design and Management Program
This page is intentionally left blank
Applying Systems Thinking Towards Countering Hybrid Warfare
by
Peihao Raymond Tan
Submitted to the MIT System and Design Management (SDM) program on January 10, 2019 in Partial Fulfillment of the Requirements for the Degree of Master of Science in Engineering and
Management.
Abstract
Carl von Clausewitz, a famous Prussian general and military theorist asserted that war's nature of being violent, interactive, and fundamentally political, does not change - only its character does. According to Clausewitz, the character of war is a dynamic phenomenon that manifests differently with the "spirit" of each age. In our current digital age, technology has heavily influenced interactions, including warfare. In addition to boosting traditional military means, technology has enabled rapid and widespread weaponization of social, information and infrastructural instruments for political coercion. A rising trend of combining national instruments of power to wage war simultaneously across the political, military, economic, social, information and infrastructural domains is a rapidly emerging threat, characteristic of modem "hybrid wars" being fought today. Traditional military-centric defense policies and strategies are ill-prepared to address such threats that deliberately operate in the "grey zone", playing on ambiguity and tailoring coercion to remain just below detection and response thresholds. In this research, a combination of literature review, descriptive study, inductive approach, normative research, case study and systems thinking are applied to analyze the hybrid warfare threat and then construct a suitable response framework, treating it as system with interrelated constituent parts, synergistically working together over time, within the wider international context, to deliver an emergent counter hybrid warfare capability.
Thesis Supervisor: Donna H. Rhodes
Title: Principal Research Scientist, Sociotechnical Systems Research Center Director, Systems Engineering Advancement Research Initiative (SEAri)
This page is intentionally left blank
Acknowledgements
There are many people I would like to thank for supporting me as I pursued my degree and worked on this research. First and foremost is my wife, Jinyi, who knowing my passion in intellectual pursuits, encouraged me to undertake a master's program, put her career on hiatus, and selflessly dedicated her time and effort to supporting me and my two sons during our stay away from home.
I am also extremely grateful to my two young sons, Jayern and Jaysen, for even their mere presence
in this journey. Even the simplest of things, like their smiles and welcome hugs I received each day as I returned from school, energized me to work through my research.
Next, I would like to thank my thesis advisor, Dr. Donna Rhodes, without whom this thesis would not have materialized. Her rich experience and ever-willingness to help students despite her busy schedule saw to me benefiting and learning much from her. I am really fortunate to have her as my advisor, providing valuable, timely and sincere feedback as I developed my research.
I would like to thank Joan Rubin, the executive director of the SDM program, and other members
of the SDM staff for their support and effort in making this journey such an enriching experience for me.
I would like to thank my organization, the Defense Science and Technology Agency, for
sponsoring my degree, as part of the constant career-building and grooming they invest in me.
I would like to thank my family in Singapore, in the US, and especially those who flew in to spend
quality time and warm our hearts during our stay away from home. Such times with family were precious, knowing they would be fleeting.
Last but certainly not least, I would like to thank my friends who were with me in Cambridge for this journey. I have benefitted much from them, both academically from our collaboration in team assignments, and spiritually from the friendship forged over family outings, meals and "boys' nights" at the Muddy Charles Pub.
This page is intentionally left blank
Table of Contents
A BSTRA CT ... 3
AC K N O W LED G EM ENTS ... 5
TA BLE O F CO NTEN TS ... 7
LIST O F FIG U R ES... 9
LIST O F TA BLES...11
LIST OF ACRONYMS AND ABBREVIATIONS... 13
CH A PTER 1: IN TR O DU CTIO N ... 15
1.1 BACKGROUND ... 15
1.2 M OTIVATION ... 15
1.3 AIM ... 15
1.4 RESEARCH Q UESTIONS AND RESEARCH A PPROACH ... 16
1.5 SCOPE ... 18
1.6 RESEARCH CONTRIBUTION... 18
1.7 THESIS STRUCTURE... 19
CHAPTER 2: OVERVIEW OF HYBRID WARFARE... 21
2.1 D EFINITIONS OF H YBRID W ARFARE ... 21
2.2 CRITICISM S ON D EFINITIONS ... 29
2.3 A W AY A HEAD ... 30
CHAPTER 3: PROPOSED HOLISTIC DEFINITION OF HYBRID WARFARE... 31
3.1 ESTABLISHING AN ALTERNATIVE APPROACH TO EXPLAINING HYBRID WARFARE ... 31
3.2 REFRAMING THE COLLECTIVE VOICES ON HYBRID WARFARE ... 32
3.2. 1 N ature ... 38 3.2.2 A ctors ... 38 3.2.3 M eans... 39 3.2.4 M anner of efforts... 39 3.2.5 M anner of effects... 40 3.2.6 Interim objectives... 41 3.2.7 E nd goal ... 41
3.3 CHARACTERISTIC D ESCRIPTION OF H YBRID W ARFARE... 41
3.4 OBJECTIVE AND APPROACH OF MEASURING "HYBRIDITY" OF WARFARE ... 42
3.4.1 System Entities that can be hybridized ... 43
3.4.2 System Attributes suggesting hybridity ... 44
3.4.3 O bjectives-D riven M easurem ent Approach... 44
3.5 O BSERVING H YBRIDIZABLE ENTITIES... 46
3.6 M EASURING "H YBRIDITY"... 51
3 .6 .1 V a rie ty ... ... 5 1 3 .6 2 U n ity ... ... 5 1 3.6.3 Adaptivity ... 52
3.6.4 S yn chron icity ... 5 3 3 .6.5 Sy n erg y ... 5 3 3 .6.6 Sp ecificity ... 5 4
3.7 REPRESENTING "HYBRIDITY" ... 55
CHAPTER 4: OVERVIEW OF COUNTER HYBRID WARFARE... 57
4.1 COUNTER HYBRID WARFARE RECOMMENDATIONS BY OTHER AUTHORS ... 57
4.2 ASSESSMENT OF CURRENT STATE OF COUNTER HYBRID WARFARE ... 62
CHAPTER 5: PROPOSED STRATEGY FOR RESPONSE TO HYBRID WARFARE... 63
5.1 PREMISES USED IN CONSTRUCTING HYBRID WARFARE RESPONSE FRAMEWORK... 63
5.2 ASPECTS OF HYBRID WARFARE RESPONSE ... 64
5.3 HYBRID WARFARE RESPONSE AS A SYSTEM ... 68
5.3.1 System Boundary and Emergent Value Delivered... 68
5.3.2 System Building Blocks... 69
5.3.3 Supp orting P rocesses... 70
5.3.4 Supp orting Structure ... 92
5.3.5 Proposed Hybrid Warfare Response System Architecture ... 99
CHAPTER 6: CASE STUDY ... 103
6.1 PURPOSE OF CASE STUDY ... 103
6.2 A PPROACH OF CASE STUDY ... 103
6.3 CASE ACCOUNT: RUSSIAN-UKRAINE CONFLICT (2000-2014)... 105
6.3.1 C hoice of case ... 105
6.3.2 M otivationfor choice of case...106
6.3.3 Chronology of activities in Russian-Ukraine conflict (2000 - 2014)... 106
6.4 APPLYING PROPOSED RESPONSE FRAMEWORK TO RUSSIAN-UKRAINE CONFLICT ... 110
6.4.1 Understanding, Vulnerability Assessment, and Strengthening... 110
6.4.2 Monitoring, Detecting, and Tracking ... 111
6.4.3 Probing, Sensing, Orchestrating, and Responding... 113
6.4.4 Coordinating and Collaborating ... 114
6.4.5 Similarities between current trajectory and proposed
framework
... 114CHAPTER 7: CONCLUSION AND FUTURE WORK ... 117
7.1 RESEARCH QUESTIONS AND CONTRIBUTIONS ... 117
7.2 L IM ITA TION S ... 11 7 7.3 F UTURE R ESEARCH ... 1 18 REFERENCES... 121
APPENDIX A ... 125
List of Figures
Figure 1-1: Research Approach Flowchart... 17
Figure 2-1: Horizontal and Vertical Escalation [9]... 22
Figure 2-2: Hybrid Threats as a confluence of other threats [15]... 22
Figure 2-3: Aspects of Hybrid Attack and Defense [11]... 24
Figure 2-4: Regularity of warfare depending on regularity of opponents and activities [15] .... 25
Figure 2-5: Callard-Faber Model onforms of war [24]... 28
Figure 2-6: Hybrid Warfare on the modality scale of war... 29
Figure 3-1: "Broad-Narrow" dilemma of hybrid warfare definitions... 32
Figure 3-2: System Architecture of Hybrid Warfare ... 42
Figure 3-3: "Hybridity " as a hierarchy of ilities ... 44
Figure 3-4: Constituents offormal entities in Hybrid Warfare... 47
Figure 3-5: Hybrid Warfare Activity Dashboard ... 48
Figure 3-6: Time Series of a Hypothetical Hybrid Warfare Scenario... 50
Figure 3-7: Hybridity Characterization of a Hypothetical Hybrid War ... 55
Figure 4-1: Nature of activities in the phases of a hybrid conflict []... 59
Figure 4-2: Possible mappings of DIMEFIL activities mapped against PMESII elements [35]. 61 Figure 5-1: OPD showing Hybrid Warfare Response as a System within its Context... 69
Figure 5-2: OPD showing Building blocks of Hybrid Warfare Response System ... 70
Figure 5-3: Nested Supporting Processes of Hybrid Warfare Response ... 71
Figure 5-4: Dashboard for visualizing monitored health of societal functions ... 72
Figure 5-5: ASCOPE enablers of PMESIJfunctions [49]... 73
Figure 5-6: Entities along Value Delivery Pathway in System Architecture of Hybrid Warfare. 77 Figure 5-7: 3 possible scenarios of societal degradation in relation to hybrid warfare attacks. 78 Figure 5-8: Detection threshold concepts for triggering restoration cycle ... 79
Figure 5-9: Tracking of societal health using time-series of health-monitoring dashboard ... 80
Figure 5-10: Terrorist Threat Cycle by Stratfor... 81
Figure 5-11: Hybrid Warfare Threat Cycle... 82
Figure 5-12: Illustration of tracking multiple potential aggressors' threat activities ... 83
Figure 5-13: Temporal correlations between threat activities and victim's degradation... 84
Figure 5-14: Desired cumulative outcome of iterative planning... 85
Figure 5-15: Cynefin Framework System Types and Decision-Making Processes... 87
Figure 5-16: Examples of DIMEFIL actions as response against Hybrid Warfare [53] ... 88
Figure 5-17: Forming Response System's Intelligent Actors
from
Societal Stakeholders ... 96Figure 5-18: Detailed Hybrid Warfare Response System Architecture in OPM ... 100
Figure 5-19: Extracting single processes
from
Response System Architecture ... 100Figure 6-1: Mismatch between historical case accounts and thesis' case-study motivation ... 103
Figure 6-2: Russia's series of Hybrid Warfare actions on Ukraine ... 112 Figure 6-3: Ukraine's societal health dashboard attributing degradations to Russia's actions 113
This page is intentionally left blank
List of Tables
Table 1-1: Research Questions and Approach ... 16
Table 1-2: Research contribution to categories of stakeholders ... 19
Table 3-1: Hybrid Warfare Concept "2-down-1-up" Decomposition ... 34
Table 3-2: Decomposition of "Hybrid Warfare" into System Entities and Attributes... 43
Table 3-3: Aspects of Hybridity ... 44
Table 3-4: Intersecting the Entities and Attributes perspectives of Hybridity... 45
Table 3-5: Phenomena to be measured by Hybridity ... 45
Table 3-6: Four Categories of Hybrid Warfare Actors... 47
Table 3-7: Sample Hybrid Warfare Damage Trajectories ... 53
Table 3-8: Traceability of Hybridity measurement treatment to objectives ... 54
Table 5-1: Hybrid Warfare Response "2-down-i-up" Analysis ... 64
Table 5-2: Mapping Hybrid Warfare response aspects to elements in Systems Language... 69
Table 5-3: Generic recovery protocols against prevalent hybrid aggression tools... 75
Table 5-4: 3 Tracking Tasks Using 2 Perspectives ... 80
Table 5-5: How Hybrid Warfare qualifies as a Complex System in the Cynefin Framework... 86
Table 5-6: Summary of response processes' objectives, tasks, and capability requirements... 91
Table 5-7: Assigning supporting structure to supporting processes based on capability needs.. 92
Table 5-8: Example of societal stakeholders... 95
Table 5-9: Hybrid Warfare Response HQ's scope ofresponsibilities in supporting processes ... 97
Table 5-10: Hybrid Warfare Response task forces' responsibilities in supporting processes ... 98
Table 5-11: Hybrid Warfare Response Specialists' responsibilities in supporting processes... 98
Table 6-1: Validation treatment for supporting processes in proposedframework... 105
Table 6-2: Chronology of Russian-Ukraine conflict activities between 2000 and 2014... 106
Table 7-1: Research contributions addressing research questions... 117
Table 7-2: Limitations in the measurement of "hybridity" ... 118
This page is intentionally left blank
List of Acronyms and Abbreviations
Al ASCOPE C4ISR COMPASS DARPA DIMEFIL IT HQ MPECI NATO NGO OODA OPD PMESII SAP US DOD Artificial IntelligenceAreas, Structures, Capabilities, Organization, People, and Events
Command, Control, Communications, Computer, Intelligence, Surveillance, and Reconnaissance
Collection and Monitoring via Planning for Active Situational Scenarios Defense Advanced Research Projects Agency
Diplomatic, Information, Military, Economic, Financial, Intelligence, and Legal Information Technology
Headquarters
Military, Political, Economic, Civilian, and Informational North Atlantic Treaty Organization
Non-Governmental Organization Observe Orient Decide Act Object Process Diagram
Political, Military, Economic, Social, Informational, and Infrastructure Synchronized Attack Package
United States Department of Defense
Chapter 1: Introduction
The topic of this thesis is the understanding of and response towards the growing threat of hybrid warfare. This chapter lays out the background, motivation, aim, research questions, research approach, scope, contributions of the work, and specifies the structure of the rest of the thesis.
1.1 Background
The mutually assured destruction doctrine effected by the advent of nuclear weapons has resulted in the "stability-instability paradox", which states that to the extent military escalations stabilize at the strategic level (i.e. nuclear threshold), they would destabilize at the lower levels of violence to pursue political objectives while avoiding overly costly consequences [1]. This paradox conceivably accounts for belligerent entities' increased propensity and proficiency in synchronizing employment of non-military, lower intensity subversion tactics to undermine societal stability of targeted nations - a threat phenomenon whose prominence, effectiveness, and consequences though widely acknowledged, is left contentiously termed as "hybrid warfare".
1.2 Motivation
Perhaps because most nations' defense strategies are grounded in doctrines aimed at addressing traditional military warfare, response to the largely non-military nature of hybrid warfare remains lagging behind the threat [2] [3] [4]. The urgency to prepare many nations who currently remain vulnerable to hybrid warfare is the motivation for this thesis' primary objective of proposing a suitable response framework. In addition, having been a practicing systems architect for 3 years and currently pursuing a master's degree on systems design and management, the author recognizes the value of systems thinking and sees potential in applying such an approach towards achieving this objective.
1.3 Aim
In articulating this thesis' aim based on the above motivations, the author found the "To-By-Using" framing [5] to be particularly useful. Using that, the aim of this thesis can be stated as:
To prepare nations' defenses against hybrid warfare
By proposing a practical and effective response framework Using a Systems Thinking approach
1.4 Research Questions and Research Approach
While the thesis' aim implied that the primary research question be on how to respond to the
threat of hybrid warfare, preliminary review of such existing effort suggested that a significant
source of the difficulty stemmed from the lack of consensus and robust understanding of the threat [2] [3] [6]. If the problem definition is not clear, it is of little value, and we certainly cannot hope to adequately solve what we do not understand. Tienhoven echoes this in saying "it seems
problematic... developing countermeasures, whilst there is little agreement on what the concept means" [6]. A logical pre-requisite to proposing countermeasures is thus to first properly define
what the threat is. In addition, from a practicality perspective, since potential adopters would
naturally question how applicable the eventual proposed response framework is, some preliminary form of validation of the framework is required. These three overarching research questions, their purpose and requisite deliverables are summarized in the first four columns of Table 1-1.
Table 1-1: Research Questions and Approach
Knowledge Gathering, Qualitative Analysis
~ . ~ . DecriptiveInductive Nomtv ase
Study1~~~~~~ aprah4esac Suy4 What is hybrid
warfare?
Problem definition
(Pre-req)
Holistic, robust definition
How to .hei,
respond to th Th sis Practical response framework 4 4 '
threat?
Is the response Assessment of framework
framework Validation effectiveness, when applied on 4
applicable? a historical case
Observe and gather facts.
2 From observations, derive insights on how things work.
3 Gather facts to identify aspects that can be improved.
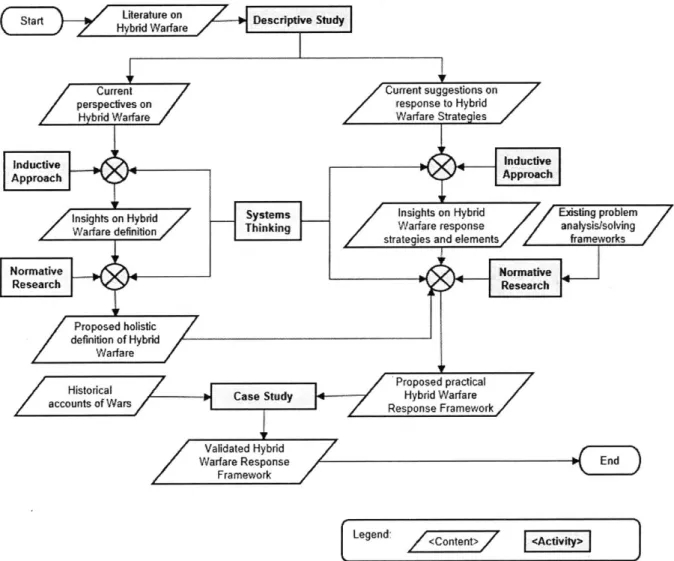
Research approaches the author found suitable for this thesis were primarily of knowledge gathering and qualitative analysis types. The nature of each research question informs their respective choice of specific approach methods (i.e. descriptive study, inductive approach, normative research, or case study). The remaining columns on the right of Table 1-1 show the assignment of research approaches to each research question. In addition to these, the author leverages experience in systems thinking and draws inspiration from existing frameworks to complement the inductive approach and normative research methods. Figure 1-1 shows how this described research approach flows towards this thesis' end goal.
nsigtsonHybr TkeDesceriptnve Study
acoutsofWrid CaWaSudfHbrdraear
Current Current su estions on
pectives on response to Hybrid
Hy Pbrid Warfare7 Warfare StrategiesZ
Inductive Inductive
Approach Approach
Insights on Hybrid/ systems Insights on Hybrid Existing problem Warfare definition Thinking Warfare response analysisdsolving
strategies and elements frameworks
Normative Normative
Research +Research
Prp sd holistic
Pdefinition of Hybrid Warfare
Histoical Proposed practical
HccunsofWars Case Study Hybrid Warfare
accontsof arsResponse Framework/
Validated Hybrid
W arfare Response Ed
F rramework
Legend: <ontent> <Activity>
Figure 1-1: Research Approach Flowchart
1.5 Scope
This thesis deals primarily with establishing a common problem definition and associated language for hybrid warfare, and proposes a new framework for responding to this threat. In deriving a proposed threat definition, the author employs research methods in Table 1-1, but does not take additional steps to verify ensuing consensus from other hybrid warfare authors. The author also made a conscious decision to limit hybrid warfare response framework discussions to a defensive stance (i.e. restoring the victim nation's societal normalcy) and not venture into counter-offensive strategies aimed at eliminating threat sources. The latter requires substantial dedicated effort beyond the resources and timeframe accorded to this thesis. Due to resource availability, the case study approach used for validating the proposed framework is limited to the use of one case.
1.6 Research Contribution
This research provides several contributions to stakeholders and their existing bodies of knowledge on hybrid warfare threat and response strategies. A construct the author found useful for identifying areas of research contribution is Parnell and Driscoll's taxonomy of stakeholders [7]. Based on this taxonomy's description of the 6 types of system stakeholders (Decision Authority',
ClientA Owner7, User, Consumer9, and Interconnected' ) and this thesis' proposed counter hybrid
warfare framework being the relevant system, Table 1-2 summarizes the author's envisaged research contribution to specific stakeholders.
5 The stakeholder(s) with ultimate decision gate authority to approve and implement a system solution
6 The person or organization that solicited systems decision support for a project; and/or the stakeholder that
principally defines system requirements
7 The person or organization responsible for proper and purposeful system operation
8 The person or organization accountable for proper and purposeful system operation.
9 The person(s) or organization(s) that realize direct or indirect benefits from the products or services of the system.
'0 The persons or organizations that will be virtually or physically connected to the system and have potential benefits, costs, and/or risks caused by the connection.
Table 1-2: Research contribution to categories of stakeholders Stakeholder
TypeSpeifi staehoderEnvisioned Research Contribution of Thesis
Type Specific stakeholder
Decision A system architecture acting as an implementation
Authority Various nations' leadership. plan for building up a nation's counter hybrid warfare
capability.
MIT Systems Engineering Advancement Research Initiative
Client (SEAri). Contributions to the larger systems research program.
MIT System and Design Management (SDM).
Various nations' counter hybrid Findings, perspectives, tools, and recommendations
Owvner warfare academics and planners. pertaining to hybrid warfare threats and defense
against it.
Various nations' counter hybrid warfare Findings, perspectives, tools, and recommendations
User Vai nones informing the buildup of counter hybrid warfare
capability owners. capabilities.
Findings, perspectives, tools, and recommendations
Consumer Various nations' whole-of-society. contributing to counter hybrid warfare capabilities that
safeguard societies' peace and normalcy.
Findings, perspectives, tools, and recommendations
Interconnected Various nations' whole-of-society. informing the roles, responsibilities and benefits for
counter hybrid warfare actors.
In addition, the concluding chapter also provides recommendations on future research efforts that can contribute towards augmenting nations' response capabilities against hybrid warfare.
1.7 Thesis Structure
Chapter 1 lays out the motivation, goals, approach and structure of this work. Chapter 2 reviews existing literature to provide an overview of various perspectives on hybrid warfare. Chapter 3 analyzes current views on the hybrid warfare threat and employs Systems Thinking methods to re-frame the problem definition in a more practical perspective. Chapter 4 reviews existing literature suggesting principles, policies, structures or processes aimed at countering hybrid warfare threats. Chapter 5 complements existing recommendations with other problem-solving frameworks and Systems Thinking to propose a holistic response framework against hybrid warfare. Chapter 6 applies the proposed response framework to a historical case of hybrid warfare to assess its validity. Chapter 7 recaps the research findings, revisits the research questions, identifies research limitations and discusses future work in this vein.
Chapter 2: Overview of Hybrid Warfare
Chapter 1 established that a pre-requisite to effective response strategies is to sharpen the problem definition, making it tractable for analysis and response planning. Although in a broad sense, hybrid warfare entails simultaneously employing multiple forms of pressure to coerce a victim to submit to the aggressor's demands, it is widely recognized that there is currently no established consensus on the definition of this concept [8] [9] [6] [10] [11] [12] [13] [2]. To convey a flavor of hybrid warfare and the debate about it, this chapter summarizes the different views by various authors and examines why the current disparate interpretations makes analyses problematic.
2.1 Definitions of Hybrid Warfare
Cullen adopted the definition of hybrid warfare being "the synchronized use of multiple
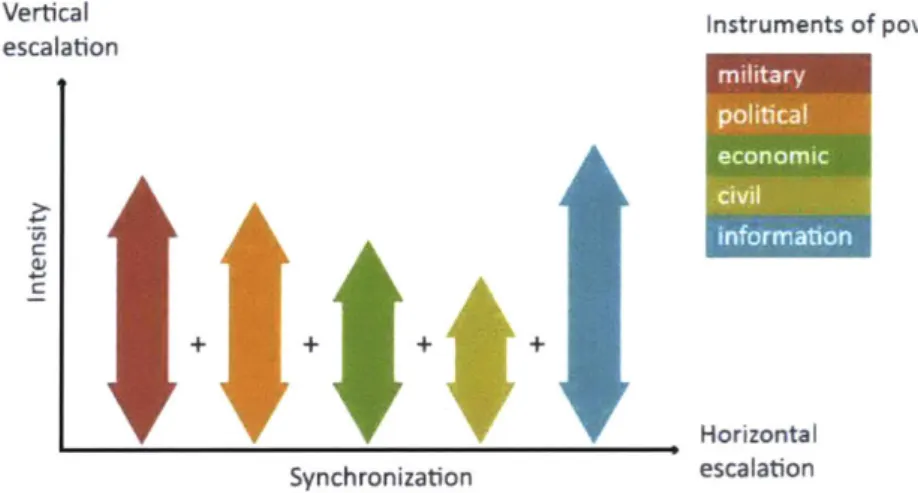
instruments of power tailored to specific vulnerabilities across the full spectrum of societal functions to achieve synergistic effects" [9]. Notable key concepts he mentioned included synergy
in aggressors' use of MPECI11 instruments of power against victims' vulnerabilities in PMESII12 societal functions, attention to tailoring of "synchronized attack packages" that dynamically strategize horizontal and vertical escalation (i.e. coercive actions) and de-escalation (i.e. compensatory actions) (see Figure 2-1), careful management of attack signature and exploiting of ambiguity to avoid retribution, and the complexity of hybrid warfare in terms of unpredictability and sensitivity to its wider context.
NATO [14] [4] [15] prefers the use of "hybrid threats" to "hybrid warfare ", defining the former
as "those posed by adversaries, with the ability to simultaneously employ conventional and conventional means adaptively in pursuit of their objectives" and "combine military and non-military as well as covert and overt means, including disinformation, cyber-attacks, economic pressure, deployment of irregular armed groups and the use of regular forces". Notable key
concepts mentioned by NATO include the simultaneous and adaptive combination of military and non-military, traditional and irregular, covert and overt means in time and space, hybrid threats
Military, Political, Economic, Civilian and Informational
1 Political, Military, Economic, Social, Informational, and Infrastructure
being a confluence of conventional, irregular, terrorism and criminal threats (see Figure 2-2), and the argument that it is conducting old tactics, only at higher speed, scale, and intensity, facilitated by rapid technological change and global interconnectivity [14].
Vertical Instruments of power
escalation
C
~~"i""a
Horizontal
Synchronization escalation
Figure 2-1: Horizontal and Vertical Escalation 191
Figure 2-2: Hybrid Threats as a confluence of other threats 1151
Miklaucic [4] aligns with NATO's opinion that hybrid warfare encompasses a wide variety of existing adverse actions and what is new is its "adaptive and systematic use of such means
singularly and in combination by adversaries in pursuit of long-term political objectives, as opposed to their more random occurrence, driven by coincidental factors " [4]. Miklaucic likewise
highlighted the complex nature of hybrid warfare, characterized by the interrelatedness of its constituent elements, complicated and interdependent nature of activities, multiplicity of stakeholders with different interests, and the dynamic international security environment. He observed that employment of hybrid warfare was attractive to state actors seeking
attributability and where overt action is ruled out for various reasons. He also opined that the harm done by hybrid threat elements is felt most intimately in the private sector, where adversaries attack bottom lines and leech on the operations of individual companies and industrial sectors.
Puyvelde suggested that "any threat can be considered hybrid as long as it is not limited to a single
form
and dimension of warfare " [10]. However, he proceeded to acknowledge that because thisdefinition was broad, when a threat is defined as "hybrid", the term loses its value instead of clarifying the reality of modem warfare. Puyvelde shares NATO and Miklaucic's assessment that hybrid warfare is "more of the same", and that its novelty lies in the use of modem technology, notably in the information and cyber domains.
Pindjak defined hybrid conflicts as involving "multilayered efforts designed to destabilize a
functioning
state andpolarize its society " [16]. He observed that other key trends in hybrid warfareincluded manipulating influential policy and decision makers, polarizing the targeted nation's population, and maintaining covertness to avoid retribution. Kols [17] echoed Pindjak's observation on hybrid warfare's polarization of society, adding that information operations, all modes of communication, cyberattacks, disinformation, propaganda, and psychological operations were common tools used. On maintaining covertness, Kols assessed that this was critical for achieving decisive strategic results, before the victim recognizes and reacts to the war.
Richterova defined hybrid warfare as a "conflict applying combination and simultaneous use of
conventional and irregular warfare, involving both state and non-state actors, used adaptively in pursuit of their objectives and not limited to physical battlefield or territory" [11]. She echoed
other authors' observations such as Miklaucic's assertion that it is an old phenomenon employed on a larger scale and exploiting old tools in new ways, as well as Pindjak's observation that it focuses on dividing society, making political decisions difficult to employ. Other notable key concepts she highlighted include the importance of exploring and exploiting vulnerabilities of victim nations, and hybrid warfare's phases comprising preparation, attack and follow-up stages. Lastly, she emphasized hybrid warfare's multi-modal attack nature targeting physical, psychological, cultural, political and human dimensions, and identified key aspects of hybrid attacks and defenses shown in Figure 2-3.
Aspects of hybrid attack and defence"
Attack Defence
prvtzpower 7
Figure 2-3: Aspects of Hybrid Attack and Defense [111
Marcus defined "Hybrid war" as "an amalgam of overt and covert military power; a combination
of bullying and subversion along with just a dash of deniability -all intended to make a full-scale response that much harder" [8]. His observations were largely consistent with those of other
authors, including aggressors' careful calibration of subversive efforts to maintain plausible deniability and avoid big responses, as well as the use of disinformation as a key instrument abusing social media and cyber elements.
Lanoszka defined hybrid warfare as a strategy that "deliberately integrates the use of various
instruments of national power so as to achieve foreign policy objectives in the light ofthe believed goals and capabilities ofthe adversary " [18]. He asserts that the intention of hybrid warfare is not
oriented at defending the international status quo. Similar to Bond, who defined hybrid warfare as
"the projecting of all elements of national power along a continuum of activities from stability, security, and reconstruction operations, to armed combat" [19], he discussed the integrated use
of economic, social, political, military, diplomatic and informational elements of national power. Lanoszka observed that the employment of these elements involved all public institutions, and encompassed multiple tactics such as propaganda, espionage, agitation, criminal disorder, fifth
columns'3 and unmarked soldiers. He also highlighted hybrid warfare's distinctive preference of
subversion over conventional military engagement, and likewise the importance in maintaining plausible deniability to deter strong retaliation. Lastly, Lanoszka also assessed that hybrid warfare is complex in that activities are difficult to manage, and miscalculations are likely.
While Purton [15] did not construct his own definition of hybrid warfare, he viewed it as combinatorial employments of regular and irregular warfare, each of which could be further resolved into regularity and irregularity of opponents and activities. Figure 2-4 shows his differentiation between regular and types of irregular warfare on this basis.
0
Regular Activities
irregular Activities
Regular Warfare a. Irregular b. Irregular c. Presence of d. Intersection
opponents activities 'Irregularness' of Irregular
opponents and
actvities
Figure 2-4: Regularity of warfare depending on regularity of opponents and activities 1151
Similar to NATO, Hoffman [12] [20] preferred the use of "hybrid threats" to "hybrid warfare", defining the former as "any adversary that simultaneously and adaptively employs afused mix of
conventional weapons, irregular tactics, terrorism and criminal behavior in the battle space to obtain their political objectives ". He explained that the term "hybrid" captures both the organization and the means, and asserted that the most important characteristic of hybrid threats
was convergence - the ability to apply and combine different means, uniquely and with deliberate
" Groups of individuals, covertly embedded within a much larger population that they seek to undermine and agitate, waiting for hostilities to break out before becoming active. [18]
synergies specifically designed against a target. He also observed that successful hybrid threats tend to have a higher degree of centralized control coordinating and directing across multiple attack domains to achieve synergy.
The US DOD uses "irregular warfare" rather than "hybrid warfare", assessing that "in practice,
most wars and campaigns are hybrids of conventional and irregular warfare operations" and that
"the balance or primary focus of operations gives a war, campaign, or major operation its predominant character" [21]. Their analysis studied how aggressors sought to undermine
adversarial leaderships' legitimacy and credibility via political and economic means, while isolating and thereafter gaining control and influence over the relevant population via psychological and social means such as tribal politics, social networks, religious influences and cultural mores.
Tienhoven adopted a very broad definition that hybrid warfare "indicates a combination of two or
multiple forms of warfare" [6]. He characterized hybrid warfare along the four dimensions of simultaneity (i.e. degree of simultaneously applying different modes of warfare),fusion (i.e. degree
of fusing different modes of warfare towards one's own advantage), multi-modality (i.e. degree of mixing and applying different modes of warfare), and catastrophic (i.e. degree of damage). Drawing largely from the works of Hoffman, Glenn and McCuen, Tienhoven also categorized and explained the combinable modes of warfare in four physical forms (i.e. conventional capabilities, irregular tactics, terrorism, and criminal activities) and four conceptual forms (i.e. political, economic, information and social means).
Glenn defined a hybrid threat as "an adversary that simultaneously and adaptively employs some
combination of (1) political, military, economic, social, and information means, and (2)
conventional, irregular, catastrophic, terrorism, and disruptive/criminal warfare methods. It may
include a combination of state and non-state actors" [13]. He spoke about the involvement of
whole-of-government, non-governmental and inter-governmental agencies, relevant commercial enterprises, and other pertinent parties in employing PMESI means in conventional and irregular manners.
McCuen stated that hybrid warfare indicates battles fought on "both physical and conceptual
dimensions: the former a struggle against an armed enemy and the latter, a wide struggle for 26
control and support of the combat zone's indigenous population, the support of the home
fronts
of the intervening nations, and the support of the international community" [22]. Notable key pointshe elaborated include hybrid warfare's effectiveness hinging on achieving strategic objectives in both the physical and conceptual dimensions, the use of social elements in populations being the battlegrounds, and the ability to wage war without relying on conventional military might.
Dayspring defined hybrid warfare generally as "a way of synchronizing the range of possible
means toward achieving a desired end, while minimizing the risks associated with direct military confrontation. ", and more specifically as "the synchronized application ofpolitical and military
forms of war, through direct and indirect means, in order to satisfy strategic objectives while minimizing the political risks associated with traditional war" [2]. He described hybrid warfare's synchronized weaponization of all instruments of national power, and the limitations of the DIME-FIL 4 model in capturing the full range of military options. Specifically, he opined that hybrid
warfare changes strategic dynamics by dividing military forms of war into elements allowing states to consider new ways to achieve desired goals. Like Richterova [11], Dayspring also discussed notable phases in hybrid warfare, starting with the establishing of strategic objectives, followed by employing means to violate the victim state's sovereignty during a time of peace, breaking their will and ability to resist, before the eventual overt introduction of force. Also similar to other authors, Dayspring noted hybrid warfare's preferential timing and limiting of coercive violence below detection and reaction thresholds to minimize chances of escalation to direct military confrontation or triggering of international intervention.
Qiao
and Wang were widely recognized as the most revolutionary of modern warfare thinkers,coining the term "unrestricted warfare" as opposed to "hybrid warfare". The pair described the former as a long-term approach "using all means, including armedforce or non-armedforce,
military and non-military, and lethal and non-lethal means to compel an enemy to accept one's interest " [23]. Their book, titled "Unrestricted Warfare", explored possible weaponization of even commonplace things close to ordinary citizens (e.g. immigration and culture), to engage in war.
1 Diplomatic, Information, Military, Economic, Financial, Intelligence, and Legal
Callard and Faber adopted the term "combination warfare" in preference over "hybrid warfare", describing the former as a "combination of manyforms ofwar ", drawing on "virtually all spheres
of human activity" [23] [24]. The pair asserted that modem conflict will become increasingly "civilianized" as traditional and non-traditional combatant exploit the identified forms of warfare in their Callard-Faber model (Figure 2-5). They explained that while many of these forms may look familiar, what is unfamiliar is aggressors' increasing ability to bundle these in unprecedented manners and at different times, to create shifting but sustained pressure on a victim nation.
Combination Warfare: "10,000 Methods Combined as One"
Above-Military Forms of War Military Forms of War Non-Military Forms of War
Cultural warfare Nuclear warfare Diplomatic warfare
Ideological warfare Conventional warfare Economic/economic aid or
Psychological warfare Bio/chemical warfare Policy warfare
Resources warfare Ecological warfare Financial warfare
Social Networks warfare Space warfare Trade warfare
Technological warfare Electronic/information/ Legal/moral warfare
Fictitious/fabrication warfare ISR warfare Sanctions warfare
Agricultural warfare Guerrilla warfare Religious/holy warfare
Black market warfare Terrorist warfare Media/propaganda/Internet
Global-level drug warfare Air exclusion zones warfare
Intelligence warfare Forced population shifts/
migrations
Figure 2-5: Callard-Faber Model on forms of war 1241
Oskarsson discussed the use of DIMEFIL instruments of national power as viable means for the conduct of hybrid warfare, and the disproportionate growth in importance of non-military instruments, with the Information domain asserting the most influence [25]. Her opinions on the key characteristics of hybrid warfare (e.g. deliberation in design, simultaneity and adaptive combination of means, importance of covertness in remaining below response thresholds) were largely shared by other authors.
2.2 Criticisms on Definitions
The diverse perspectives on hybrid warfare have prompted various criticisms arguing why definitions have not been helpful in facilitating analysis and countermeasures. Specifically, it has been argued that the terminology's utility is limited by its inconsistency, vagueness, and non-novelty.
1. Inconsistency. The lack of an authoritative definition and overall consensus limits the common
understanding much needed to unite the community in cohesive problem-solving. In particular, the extent and prominence of the non-military means in hybrid warfare remains debated [6].
2. Vagueness. Understandably due to its multi-faceted nature, some attempts at a concise definition of hybrid warfare end up being too broad for practical analysis [6]. For example, noting the difficulty in identifying historical wars where only a single form of warfare was employed, applying descriptions such as "a combination oftwo or multipleforms of warfare "
[6] or "as long as it is not limited to a single form and dimension of warfare." [10] would
suggest that almost all wars were "hybrid", rendering the term redundant. Specifically, Figure
2-6 illustrates how other than a hypothetical "mono-modal war", the full spectrum ranging
from "bimodal" (i.e. minimally hybrid) to "all-modal" (i.e. maximally hybrid) war, though varying greatly, would. over-simplistically be classified as "hybrid warfare", losing the distinction needed for describing and analyzing specific instances of warfare. The US DOD reinforces this point, stating that "in practice, most wars and campaigns are hybrids " [21].
"Hybrid Warfare" .. .Modality of warfare 1 2co "monomodal "bimodal-- warfare" warfare"
Figure 2-6: Hybrid Warfare on the modality scale of war
3. Non-novelty. Citing numerous historical employments of elements often considered under
hybrid warfare [8] [18], sources questioned the terminology's novelty, especially in light of existing concepts [6] like "irregular warfare" or "unconventional warfare". It was argued that giving a new name to a pre-existing phenomenon does not aid problem-solving, and that
"hybrid warfare" is potentially redundant, if it is indeed nothing new. Others argued instead that the novelty lies in the proficiency of orchestrating and execution to the hybridization concept's full synergistic potential [14] [4].
2.3 A Way Ahead
In struggling to reconcile how a well-acknowledged threat [9] can be so ill-defined, the need for an appropriate treatment towards understanding hybrid warfare, as a pre-requisite for practical analysis and response planning, became clear. This is echoed by Cullen's and Dayspring's opinions that "in
order to solve a problem, one muchfirst understand it" [9] and specifically that "what hybrid warfare lacks is a general theory that will serve to
frame
its use in a meaningful manner" [2]. Moreover,despite criticisms on the terminology, Dayspring rightfully suggested that "dismissing hybrid
warfare as meaningless jargon is pointless, however, because it has already gained a level of common usage " [2]. A logical ensuing treatment pursued in the next chapter is thus drawing on
distilled insights from literature to inform exploration of alternative manners towards understanding the threat concept, and thereafter converge onto a holistic yet practical description
of hybrid warfare.
Chapter 3: Proposed Holistic Definition of Hybrid Warfare
Having reviewed modern warfare scholars' opinions about hybrid warfare and examined the challenges in framing the concept in the preceding chapter, this chapter takes these into consideration, in a systems thinking approach to proposing a holistic and practical definition of hybrid warfare.3.1 Establishing an Alternative Approach to Explaining Hybrid Warfare
If an interim goal for facilitating cohesive response/countermeasure planning is to have a unifying
and tractable problem definition on hybrid warfare, literature reviewed suggests that current definitions probably fall short of this due to a trade-off between agreeability and usability. Definitions range from narrow ones which are tractable yet divisive due to their specificity, to broad ones which are highly agreeable yet impractical because of their overly-inclusive nature in attempts to extract commonalities across multiple opinions. The latter, especially, is an assessment shared by many authors. Notably, Tienhoven opined that current literature on hybrid warfare is too general to add value because it is not specific enough to identify hybrid warfare in specific cases [6], while presumably because "hybrid" has such a broad connotation, Puyvelde cautioned that "when any threat or use offorce is defined as hybrid, the term loses its value and causes confusion" [10].
Figure 3-1 illustrates what the author came to think of as a "broad-narrow dilemma", where hybrid warfare definitions fall along a broad-narrow spectrum, with none quite achieving the utopia point (tractable and unifying) ideal for cohesive response and countermeasure planning.
Usability Tractable
Narrow, Utopia for
assertive cohesive definitions problem-solving Divisive Agreeability Unifying Broad, tentative definitions Impractical
Figure 3-1: "Broad-Narrow" dilemma of hybrid warfare definitions
The myriad definitions that can fall within the broad-narrow span of what can constitute hybrid warfare may be a good indication that though sufficient to convey a general flavor, thinking of hybrid warfare as a single class is over-simplistic and unhelpful because it does not provision for the necessary distinctions to differentiate specific instances of hybrid warfare and inform ensuing analysis. Rather, the conflicting tensions stretching this terminology suggests that the concept is one based on degree, where a measure of "hybridity" may be more helpful for characterization and practical analysis than a single category of "hybrid warfare". The US DOD similarly alluded to some form of "measure of degree" when it mentioned about a "predominant character " of war
depending on its "balance or primary focus of operations" [21]. Consequently, instead of proposing yet another variant of hybrid warfare definition, the author opined that it be more beneficial for this thesis to adopt an alternative approach of explaining the threat phenomenon with two supporting artefacts: 1) a characteristic description of what constitute hybrid warfare, and 2) an appropriate means to measure "hybridity" of wars. The following subsections proceed to examine these.
3.2 Reframing the Collective Voices on Hybrid Warfare
Since the shortfall is in consensus rather than definitions of hybrid warfare, instead of attempting to introduce new interpretations, this thesis aims to more appropriately add value by employing
descriptive study and inductive approaches (see Figure 1-1-I) to draw insights from and best reframe existing literature into a collective voice describing hybrid warfare.
The objectives set forth upfront before constructing this characteristic description are:
1. To use a structured and traceable approach, leveraging systems thinking.
2. To balance between succinctness and capturing the collective wisdom of authors in literature reviewed.
3. Where conflict arises between aiding practical analysis and fulfilling academic rigor, to
prioritize the former.
A structured systems thinking method the author found applicable for the reviewing and reframing
of existing literature into a collective hybrid warfare description is the "2-down-i-up" approach
[5] which helps define a system by aggregating and abstracting its list of fundamental elements.
As performed in Table 3-1, from the overarching concept of hybrid warfare, numerous characteristics cited in literature were first populated two levels down as level 2 conceptfragments before abstracting them one level back up, within a more manageable number of level ] concept
clusters to eventually be used for describing the overarching concept succinctly. This approach
also makes the description derivation process traceable to its sources.
15 The normative research element is featured more prominently in the subsequent discussion on the "Hybridity"
metric, which is a specifically identified improvement dimension of Hybrid Warfare description.
Table 3-1: Hybrid Warfare Concept "2-down-1-up" Decomposition Level 1
Concept Level 2 Concept Fragments
Clusters
* Pursuit of objectives [14] [11]
* Pursuit of (long-term [4]) political objectives [20] [19] [2] [25] U Foreign policy objectives [18]
* Control or influence over, and support of, a relevant population [21] * o *Undermine adversary's legitimacy [21]
* Accept aggressor's interest [2] * Territorial goals [25]
* Degrade full spectrum of societal functions [9]/ undermine societal functions [4]/ subversion g [8] [18]:
- o Political [9] [11] (e.g. subvert internal political cohesion [18] [2], government functions [13], manipulate political processes [2], voter manipulation [2])
"F3 o Military [9]
.- o Economic [9] [13]/ disrupt economy [18]/ manipulate economic conditions (e.g. financial dependency)[2]
o Social [9]/ Society [22] (incl. humans [11]/ population [13] [22], cultural [11], morale [13])/ social dynamics (e.g. tribal politics, religious influences, cultural mores) [21] o Informational [9] [13]/ Psychological [11] [12]
co o Infrastructure [9] (incl. Physical [11] [12])
_ o Create new vulnerabilities (e.g. strategic entrapment, reliance) [9] > * Horizontal and vertical escalation/de-escalation"6 [9]
Z a Destabilize a functioning state [16] [17]
* Polarize [16]/ divide [17] its (i.e. state's) society * Not limited to physical battlefield or territory [11]
- Undermine target [11]
a Involve all public institutions [18] e Environment [13]
* Avoid retribution [16]/ big response [8]
CJ
- Make a full-scale response that much harder [8]/ without provoking escalations to direct confrontation [2]
C3
* Deter strong retaliation [18]
* Minimizing the risks associated with direct military confrontation [2]/ inducing international military intervention [2]
* Minimizing political risks associated with traditional war [2]
0* Magnify perceived cost of resistance [2]
16 Although de-escalation may connote alleviating certain vulnerabilities, this is done with the intention of seeding
future vulnerabilities or avoiding triggering responses. 34
Level 1
Concept Level 2 Concept Fragments
Clusters
* Synergistic [9] [12]/ Synergy [12] * Simultaneous Effects [9]
* Multiple, coordinated in purposes [9] - Non-linear effects [9]
* Force multiplying, "whole greater than sum of parts" [9] & Indirect [9] [2]
. "much more than amalgamation" [4]
* Exploit [10]
* Use of asymmetries'7 [10], asymmetric [17] * Different but complementary ends [18]
- "Convergence" [20]
* Ambiguity (in attributability, intention, causality) [9] [26] o Sow doubts [14]/ Create uncertainty [181
0
* Non-attributability [4]/ avoid attribution [16]
* "Before an adversary even recognizes that war has begun" [17] * Deniability [8] [26]/ plausible deniability [18] [2]
e Hard to anticipate [23]
* Complicating decision making [26]
* Tailored to/ target/directed at victim's known, specific, inherent vulnerabilities [9] [26]/ exploit opponents' weakness [10]/ identify and exploit vulnerabilities of target [17]/
c using interdependencies and vulnerabilities of societies [11]! in light of believed goals and capabilities of the adversary [18]
* * Unique combinations [12]/ unprecedented [23] * Designed [16]/ Specifically designed to target [12]
* "Attack packages" [9]
Deliberately designed [25] e Low intensity [11]
* Emphasis on instruments of low levels of violence [2]/ fall short of armed conflict
. [26]
t' 2 Bullying [8]
H . Maintained below obvious response thresholds [9] [2] [25] * Deliberately restrained [2]
e Carefully calibrated [8] 9 Varying intensity [18]
* Exploit gaps and lapses in policies (triggering international response) [18]
9 Strategic balance within the covert-overt spectrum [9]/ covert [25] and overt means 4 [14] [10] [8] [26]/ overt and covert military power [8]
* Clandestine [16]
r7
> Under the radar [16]
* Maintained below obvious detection thresholds [9]
0
- * Disguised use of force [18] * Obscure true intentions [2]
7 The author interprets this as employing means in a manner that achieve disproportionate outcomes with respect to
the inputs.
Levell 1
Concept Level 2Concept Fragments
____Clusters
-o 0 0 0
Coordinate across multiple battlespaces [9] Combination in space [14]
Not limited to physical battlefield [11]
. Synchronized [9]/ synchronizing [2]
. Simultaneous [9] [14] [11] [20] [12] [6] [2]/ Simultaneously [13] [25]/ Simultaneity [6] * Coordinate multiple in time [9]
* Combination in time [14] c Timed [2]/ different times [23]
* Intentional [9]/ Deliberately [8] [2] * Systematic [4] * Coordinated [11] [9] [26]/ Calculation [2]/ * Strategic plan [26] Cd) 0 0 0 0 S 0 0
Combined [14]/ combination [4] [11] [6] [13] [2] [23] [25] [26]/ combining [16] Umbrella [4]/ bundle [23]
Blend [10]/ amalgam [8]/ Fused mix [20]/ fusion [6]/ Heterogeneous composition [6]/ Mix and match [23]/ Encompass different (tactics) [18]
Full spectrum [10]/ full range of different modes [12]/means [2]/ Comprehensive [13] Many forms [23] and dimensions [10] [6]/ Across all domains [12]
Multi-layered Efforts [16]/ Multimodal [11] [14] [20]/ multiple modes [6] Intearates [181/ intearated [181 [261
* Dynamic strategizing [9]
* Adaptively [14] [4] [11] [20] [13] [25] * Flexible [11]
Ca 9 Mutation [11]
< Horizontal and vertical escalation/de-escalation [9] e Different levels of violence [2]
9 Shifting pressure [23] * As circumstances change [23]
" Unified direction [12]
* Centralized control [12]
" "Conventional" [14] [10] [11] [20] [21] [6] [13] [26] and "non-conventional" [14] [1 0]/Unconventional [26] means
* "Traditional" [14]/ "Regular" [10] [18] [15] and "non-traditional" [17]/ "Irregular" [14] [10] [11] [18] [15] [20] [6] [13] [2]
" Kinetic operations and subversive efforts [16] * Physical vs conceptual dimensions [22] [6] " Accept no rules [121
* Instruments of power [9] [18]/ National instruments of power [18] [19]/ all instruments of state/national power [2] [26]/ coercive pressures [25]/ all means [271 e.g.
o Military [18] [19] [13] [2] [27] [25] (Physical [11]/ Kinetic) -(i.e. regular forces) and Non-military (e.g. irregular armed groups) [14]
o Political [21] [6] [19] [13] [2] [25] [26] (incl. Diplomatic [11] [19] [2])/ political support of separatists [11]
o Economic pressure [14] [21] [19] [13] [2] [25] [26] (incl. resource warfare [23]) 36 ca) 0. E C NT 1.. 0 CA E M. U' 0 U CA U C-' =41
Level 1
Concept Level 2 Concept Fragments
Clusters
o Civil [11]/ privatized [11]/ Social [6] [13] [19] [13]
o Information [10] [6] [19] [13] [2] [25]/ Cognitive elements of warfare [9]/Psychological Operations [17] [21] [25]/ influence influential policy makers and key decision makers [16], Disinformation [14] [17] [11] [8] [18] [26], Sow doubts, [14], Information Operations [17]/ warfare [18], propaganda [17] [11] [18] [26], subversive intelligence [11], media power [11], social media [8]
o Intelligence [2] o Financial [2] o Legal [2]
" Instead of large scale military invasion [11]/ (subversion,) over conventional military engagement [18]/ may not need conventional military strength to wage war directly [22]/ military used as a threat rather than primary instrument of aggression [2]
" Criminal activity [14] [11] [20] [6] [13]/ criminal disorder [18]
" Terrorism [14] [4] [20] [6] [13]/ terrorist attacks [11]/ Terrorist power [11]
" (Asymmetric) Technology [20], Digital technology [9], (mis)use of advance technology systems [11]
" Cyber Attacks [14] [17] [11] [26]/ warfare [10]/ power [11]/ elements [8] " Ethnic conflict [4]
" Sabotage [11]
* Guerilla Warfare [18]/ unmarked soldiers [18]/ armed proxy groups [2] " Espionage [18]
" Agitation'8 and "fifth columns"'9 [18] " Ecological warfare [23]
" Combination Warfare [24]
Combination Warfare: "10,000 Methods Combined as On' Above-Militay Forms of War Uitary Forms ol War Non-Mfitaey Forms of War
cutftrw wirfara Nudews wnar 00plotc walfat
kdr-o~gorea wartme Crhornaw wadamr Economrwaonorc k
P,'ychobgcad warare Bkhemca wadtre Pohey warae
Rowrces warfare Ecoogical warfare Fmancial warfare
S Ntwarki waNO are Space warfare Trade warfare TeohnOgical warfare ecfroncanfwreatont Legamoral warfare
Fseawesfabuicaion warfare ISf warfare Sactione warfare
ACuthural warfare Guerrira warfare Reqous/hoy wardare
Black rnarket warfare Terronst warfare MedapropaqadaWnter
Gkrba4evet dmug wadare Air exclusion zones worfare
... ... .. .... 1Iellrgnce warfare Forced popriabon shOft
[24] * Indiscriminate coercion [12]
e State and non-state actors [11] [12] [13] [26] * Regular and Irregular opponents [15]
e Variety of actors beyond authority of states [11]
'
I5
* Whole of government [13]* Non-government [13]/ Commercial [13]/ civilian actors [26] * Include international agencies [13]
e "other pertinent parties" [13]
* Military and paramilitary [26]
18 create dissension and discord within a target society" [18]
19 "groups of individuals... covertly, embedded within a much larger population that they seek to undermine... agitate... wait for hostilities to break out... before becoming active" [18]
20 because "state and non-state actors" covers the entire space of actors 37