By
Anthony M. Koonce
B.S., Nuclear Engineering and Engineering Physics (2003) Rensselaer Polytechnic Institute, Troy, NY
Submitted to the Department of Nuclear Science and Engineering in Partial Fulfillment of the Requirements for the Degree of
Master of Science in
Nuclear Science and Engineering
at the
Massachusetts Institute of Technology September 2006
@ 2006 Massachusetts Institute of Technology
All rights reserved
The author hereby grants to MIT permission to reproduce and to distribute publicly paper and electronic copies of this thesis document in whole or in part.
Signature of Author. A .. r.. ... . ... ... .. ... ...
9 Anthony M. Koonce
Department of Nuclear Science and Engineering August 18, 2006 Certified by... .... ... ... ...
Professor George E. Apostolakis Department of Nuclear Science and Engineering Engineering Systems Division Thesis advisor Certified by... . ...,. ... ... ... . ...
-T-7]P1rofessor Michael W. Golay Department of Nuclear Science and Engineering
j A Tlbisjeader A ccepted by... """ "."..... ... - - --- -.. - ""_"
MASSACHUSrrTS INA rrUTE,
r efou r Jefrey A,. Coderres Chairman, Departmental Committee on Graduate Students
ARCHIVES OF TECHNOLOGY
OCT 1 2 2007
Bulk Power Risk Analysis: Ranking Infrastructure Elements
According to their Risk Significance
By
Anthony M. Koonce
Submitted to the Department of Nuclear Science and Engineering on August 18, 2006 in partial fulfillment of the requirements for the degree of Master of Science in Nuclear
Science and Engineering
Abstract
Disruptions in the bulk power grid can result in very diverse consequences that include economic, social, physical, and psychological impacts. In addition, power
outages do not affect all end-users of the system in the same manner. For these reasons, a risk analysis of bulk power systems requires more than determining the likelihood and magnitude of power outages; it must also include the diverse impacts power outages have on the users of the system.
We propose a methodology for performing a risk analysis on the bulk power system. A power flow simulation model is used to determine the likelihood and extent of power outages when components within the system fail to perform their designed
function. The consequences associated with these failures are determined by looking at the type and number of customers affected. Stakeholder input is used to evaluate the relative importance of these consequences. The methodology culminates with a ranking of each system component by its risk significance to the stakeholders. The analysis is performed for failures of infrastructure elements due to both random causes and malevolent acts.
Thesis Supervisor: George E. Apostolakis
Title: Professor of Nuclear Science and Engineering and Engineering Systems
Acknowledgments
I would first like to thank my advisor, Professor Apostolakis, for his help and
guidance throughout this work. He was instrumental in my understanding of the context and implementation of risk assessment through discussions in classroom settings, formal settings, as well as informal settings. I really appreciated the non-topic discussions and stories as well. I could not have hoped for a better advisor. Remember, "Life is hard ... "
I would also like to thank the people at Sandia National Laboratories for their help
with this project, both in intellectual guidance and financial funding. I am specifically thankful to Dr. Ben Cook for his many discussions and ideas throughout this work. I also want to thank Bryan Richardson, the author of the load flow simulation model used in this work, for his help explaining the capabilities and limitations of the simulation model to me.
Most importantly, I would like to thank my wife, Sarah, for being my biggest supporter. I would like to thank her specifically for her encouragement, support, and patience while I completed my studies at MIT. I must also include my daughters, Averey
and Faith, for reminding me what the really important things in life are.
Anthony Koonce NSE September 2006
Table of Contents
Abstract ... 3
Acknowledgm ents ... 5
1. Introduction ... ...
9
2. Risk Assessm ent... 13
2.1 Overview ... ... 13
2.2 The MIT M ethodology ... ... 14
3. M ethodology ...
...
17
3.1 Overview... ... 17
3.2 Infrastructure Elements ... 18
3.3 Infrastructure Analysis... ... 21
3.4 Value Tree and Constructed Scales ... ... 26
3.5 Ranking ... 38
4.
Discussion ...
42
4.1 Stakeholder S-1 ... 42 4.2 Sensitivity Evaluation ... ... 445.
Concluding Remarks ...
... .... 48
References ... 50
Appendices ... 53
A. Analytical Hierarchy Process Results ... .... ... 53
A.1 Stakeholder S-1 Results ... ... ... 53
A.2 Stakeholder S-2 Results ... ... 54
A.3 Stakeholder S-3 Results ... ... 55
A.4 Stakeholder S-4 Results ... ... 56
A.5 Stakeholder S-5 Results ... 57
B. Load Shed Vectors (% of load lost at each load bus) ... 58
B.1 Transmission Lines ... ... 58
B .2 G enerators ... ... 59
B .3 B uses ... ... 59
C. Physical Consequence Results ... 60
C.1 Transmission Lines ... 60
C .2 G enerators ... 6 1 C .3 B uses ... ... 6 1 D. Consequence Matrices ... 62
E. Component Impact on Each PM by Stakeholder... ... 63
E .1 Stakeholder S-1 ... ... 63
E .2 Stakeholder S-2 ... ... 65
E.3 Stakeholder S-3 ... 67
E.4 Stakeholder S-4 ... 69
E .5 Stakeholder S-5 ... ... 71
F. Component Risk-Significance by Stakeholder ... .... 73
F. 1 Stakeholder S-1 ... ... 73 F.2 Stakeholder S-2 ... ... 74 F.3 Stakeholder S-3 ... ... 75 F.4 Stakeholder S-4 ... 76 F.5 Stakeholder S-5 ... 77
List of Figures
Figure 1: Methodology overview ... 17Figure 2: Single area IEEE RTS-96 grid (Ref. 27) ... ... 19
Figure 3: Infrastructure analysis overview. ... ... ... 22
Figure 4: Survey of stakeholder input... 29
List of Tables
Table 1: Custom er data per bus. ... ... 20
Table 2: Customer portion of physical consequences for transmission line 4 ... 26
Table 3: Participating members' affiliation with the electric utility company ... 27
Table 4: Constructed scales for Economics performance measures. ... 30
Table 5: Constructed scales for Image Performance Measures ... 31
Table 6: Constructed scales for Health & Safety performance measures ... 32
Table 7: Constructed scales for Environment performance measures ... 33
Table 8: PM mapping techniques. ... ... ... 34
Table 9: Consequence matrix for Customer PM... ... 36
Table 10: Matrix for Fauna PM...37
Table 11: Impacts to each PM for transmission line 4... 38
Table 12: Susceptibility levels of infrastructure assets ... 39
Table 13: Susceptibility and value combinations for each vulnerability category... 39
Table 14: Infrastructure asset vulnerability categories for ranking element failures due to m alevolent acts... 40
Table 15: Top 10 components ranked by vulnerability level for S-1 (minor malevolent acts) . ... 43
Table 16: Top 10 components ranked according to their expected disutility for S-1 (random failures)... 43
Table 17: Value tree weights (rankings) for each IC and PM by stakeholder ... 45
Table 18: Top 10 components ranked by vulnerability level for all stakeholders ... 46
Table 19: Top 10 components ranked by expected disutility for all stakeholders ... 47
Anthony Koonce NSE NSE September 2006September 2006
1. Introduction
The electrical supply system in North America including the United States, Canada, and a small portion of Northern Baja, Mexico, can be viewed as consisting of three parts. These are the generation of electrical power, the transmission of electricity,
and the distribution of electricity to the end-users. The bulk power system is the generation and transmission portion of the system. The term 'bulk' refers to the large amounts of electrical power before it is distributed to the end-users [1].
The bulk power grid is an international system that is divided into three major regions. These regions are known as the NERC (North American Electric Reliability Council) Interconnections: the Eastern Interconnection; the Western Interconnection; and the ERCOT (Electric Reliability Council of Texas) Interconnection. The Eastern
Interconnection services the U.S. states and Canadian provinces east of, and including, the great plane region. The Western Interconnection provides power to states and provinces west of, and including, the Rocky Mountain area. The smallest
interconnection, ERCOT Interconnection, covers the majority of Texas. These interconnections exhibit strong connectivity within themselves but are only weakly connected to each other.
NERC was established in 1968 in response to the 1965 Northeast Blackout. NERC is a non-government agency in the United States and Canada that sets guidelines for the reliable and safe operation of the bulk power grid. NERC has no authority to impose its recommendations but, rather, relies on the common good and self-interest of its members for adherence to its guidelines [2,3].
Besides NERC, there are other stakeholders involved with the bulk power system. The Federal Energy Regulatory Commission (FERC) is one of these stakeholders.
FERC, besides regulating other energy infrastructures, regulates the transmission and hydro production of electricity in the United States [4]. FERC, as an independent federal agency, has the authority to enforce its regulations through civil penalties. FERC is currently promoting the voluntary formation of Regional Transmission Organizations (RTOs, also known as Independent System Operators, ISOs) that oversee the entire
Anthony Koonce NSE September 2006
transmission capabilities in the United States [5]. Currently, there are 11 RTOs that operate the transmission lines in most states. RTOs operate transmission grids to maintain continuity of service between generation companies and the customers. They are also responsible to ensure nondiscriminatory access to the bulk power grid and are involved with the coordination of planned outages between multiple sites. Beside these bulk power grid stakeholders, there are also the electric utility companies themselves. Electric utility companies include publicly traded companies, federal and state agencies, rural cooperatives, and independent energy providers.
Many end-user groups constitute the customers of the bulk power system making it an equally diverse group. These users include individual citizens, manufacturers, financial networks, communication companies, transportation networks, medical
facilities, government agencies, and gas and water supply infrastructures. Electric power supports almost every aspect of our lives everyday, either directly or indirectly, and has become an integral part of our national security and economy.
In light of recent events, such as the 2003 Northeast Blackout, and the prevalent dependencies on electric power, it is recognized that a large disruption in the bulk power system, either due to random events or intentional attacks, may result in widespread consequences. These consequences could include economic, social, physical, and psychological impacts. The blackout of the Northeast on August 14, 2003, that affected over 50 million people, has been estimated to have had an economic impact between $4 billion and $10 billion in the United States alone [6].
There is a large amount of literature that analyzes failures in the bulk power system as they impact the economy. Zimmerman et al. [7] have developed a
methodology that employs the economic accounting concept. The methodology uses cost factors to assign a monetary value to the consequences (loss of life, business losses, and loss of services) that may result from terrorist attacks on the bulk power system. The
authors then combine these dollar values into a single measure, the economic impact, which is used to evaluate the risk terrorist attacks pose to the power grid. Greenburg [8]
illustrates the use of this methodology by developing a terrorist attack scenario on the
September 2006
New Jersey electric power supply network and then evaluates the impacts on the New Jersey economy. The economic impacts of the August 14, 2003 Northeast Blackout as stated in Reference 6 were also based on economist evaluations of metrics that included spoilage of perishable goods, cost of power not provided, lost productivity, disposal of goods in production during power outage, extra wages for employees, and equipment restart expenses. As stated earlier, there are various types of impacts (social, physical, and psychological) that accompany economic impacts with failures in the bulk power grid, some of which may be socially unacceptable to be assigned a dollar 'cost.'
Analysis of past blackout data [9] show that outages and disturbances follow a power law distribution with a tail that shows that larger blackout frequencies decrease as a power function of its size. This is contrary to the previous belief that the frequencies of major blackouts decreased exponentially. Chen et al [10] confirm this distribution, and its tail, by analyzing NERC data of power outages that date back to 1984. Carreras et al [11] further investigate this distribution of blackout sizes by looking for critical loading points in electric power systems. They present an electric power transmission model that represents loads and generators as nodes of a network and use linear programming to analyze the network. Load shedding is observed as the load demand of the system is increased and the capacity of supply is held constant. This study shows that there are two transitions that define a critical loading that greatly increases the risk of major blackouts. One transition occurs when the load demand overcomes the total capacity of generation. A second transition occurs when load demand causes the transmission lines to become overloaded. Criticality of electric transmission systems was verified by Nedic et al. [12] using AC power modeling.
There are also works that look at 'hardening' effects of the bulk power grid against terrorist attacks. Salmeron et al. [13] use non-linear programming to construct a power flow model that establishes the load flow of an electric power grid system. Lines are then attacked, or removed from service, and the power flow model is used to
reestablish a stable configuration with portions of the system's load not served. The effects on the system are tracked as multiple lines are removed from service. These
results are used to find the optimal applications of available resources to harden the system and minimize the effects of terrorist action. Bier et al [14] introduce a linear programming algorithm that also solves this optimization problem of applying available resources to the power grid with similar results as the previous work.
Engineers at the Duke Power Company have proposed a value-based approach to investment planning regarding upgrades to the power system [15]. Their methodology looks at the expected cost of proposed improvements and the expected cost to customers of future outages without this improvement. They combine the customer cost and investment cost to determine the minimal value over a time period using discounting of future costs. The lowest value of the combined cost determines the appropriate time to make the improvement to the transmission system. To do this, the engineers look at the likelihood of future outages, the possible effects of these outages, and the cost imposed onto the customers if these outages occur. This work looks at the direct economic impact to customers that result from power outages but not the social, physical, and
psychological impacts.
This thesis focuses on analyzing the risks associated with the bulk power system using the viewpoint of an electric utility company. Section 2 summarizes past work on risk assessment which is the basis for the methodology developed and applied to the bulk power grid in Section 3. Section 4 offers a discussion of the results and, finally, Section
5 offers a number of concluding remarks. A series of appendices show the results of the calculations.
Anthony Koonce NSE NSE September 2006September 2006
2. Risk Assessment
2.1 OverviewThere are three components that make up risk in a technological system. These are the sequences of failures that can lead to undesirable consequences, their likelihood of occurrence, and the consequences that accompany these failures. This triplet definition of risk was proposed by Kaplan and Garrick [16] when they defined risk as the answers to the following three questions:
* What can happen? * How likely is it to occur? * What are the consequences?
There are methods, such as Probabilistic Risk Assessment (PRA; also called Quantitative Risk Assessment -QRA), for answering these three questions in complex but well defined systems such as nuclear power stations, chemical processing plants, and space systems [17]. For large, national infrastructures, these methods need to be adapted to the infrastructure's technological and sociopolitical complexities [18]. Garrick et al [19] outline a possible application of PRA techniques in the analysis of infrastructures. They point out that the full application of these techniques requires the development of processes by which private and government bodies will be able to share data freely. The difficulty in applying these methods to the risk assessment of infrastructures is further exacerbated when terrorism or malevolent acts are to be considered due to problems with determining the likelihood of a successful attack. The assessment of the likelihood that a terrorist attack will occur requires information on the intent, capability, and resources to carry out the attack. Given that a group possesses these traits, determining the point, or points, of attack requires knowledge of the goals, beliefs, and desires of the group. The probability of the attack being successful depends upon the quality of countermeasures in place to deter or combat the attack [20]. For these reasons, the MIT methodology (to be described shortly) assumes threats of appropriate levels for the analysis and leaves the likelihood of attack to the agencies responsible for collecting intelligence (Ref. 18). The
risk assessment of infrastructures presents additional difficulties due to their diffuse nature.
To answer the fist two risk questions when dealing with infrastructures, the ideas of vulnerabilities and threats are used. Haimes [21] defines these two terms as follows:
"Vulnerability is the manifestation of the inherent states of the system (e.g.
physical, technical, organizational, cultural) that can be exploited to adversely affect (cause harm or damage to) that system."
"Threat is the intent and capability to adversely affect (cause harm or damage to)
the system by adversely changing its states." We adopt these definitions in this thesis.
2.2 The MIT Methodology
Apostolakis and Lemon (Ref. 18) develop a screening methodology for diffuse infrastructures and rank vulnerabilities to terrorism. The authors apply their methodology to the water, electric power, and gas distribution systems on the Massachusetts Institute of Technology (MIT) campus. The methodology requires the stakeholders to determine the importance of possible consequences that may result from successful attacks on these infrastructures. These consequences include impacts on public image, Institute
operations, economics, health, safety, and the environment. The stakeholder group in this work is a multidisciplinary team that includes decision makers of the MIT Department of Facilities with expertise in finance, utility operations, and space planning [22].
The stakeholder input is used to create a value tree that reflects the stakeholders' views. A minimal cut set (mcs) approach is used to identify and analyze vulnerabilities in the infrastructures. The consequences resulting from successful attack on the
vulnerabilities are then applied to the value tree to determine the stakeholder impact (value) each vulnerability represents. Apostolakis and Lemon point out that determining the likelihood of a terrorist attack is very difficult to determine and is best left to the
security and intelligence agencies. Their work assumes a "minor" level of threat to be present. The work then determines the susceptibility of each mcs to this level of threat by
September 2006
looking at its accessibility and security measures. The susceptibility of each mcs is then combined with its value for ranking. The result is a ranking that requires a mcs to have both a high susceptibility and a high value to be placed higher in the ranking.
Michaud and Apostolakis [23] expand the methodology developed by Apostolakis and Lemon by analyzing a water supply network for an entire city. The authors use network theory and component capacity to analyze the water supply infrastructure rather than the mcs approached proposed in Reference 18. Michaud and Apostolakis also expand the methodology by including the duration of system failures in their analysis to capture the time dependence of the consequences resulting from failures in the
infrastructure. These authors do not look only at terrorist acts on the infrastructure but split the threats to the system into mechanical (random) failures and malevolent acts. This allows the analysis to determine the risk within the infrastructure due to random failures and the risk due to terrorist attack that is conditional on the assumed threat level.
Patterson and Apostolakis [24] further develop the MIT ranking methodology by identifying critical locations within multiple overlapping infrastructures. They apply the methodology to the chilled water supply, domestic water supply, steam supply, natural gas, and electric power infrastructures on the MIT campus. The authors employ the Geographic Information System (GIS) to determine the geographical layout of each infrastructure. GIS also provides extensive data on the infrastructure user groups identified within the work. Due to the larger number of infrastructures and users
included in the analysis, the authors use Monte Carlo simulation and importance measure concepts for the analysis of each infrastructure. The authors borrow the concept of importance measures from PRA [25] and they generalize it to include the stakeholder values. Each infrastructure is analyzed independently to assign to each location a value of the new importance measure the authors call Geographic Valued Worth (GVW). Once each infrastructure is analyzed, the GVWs from each infrastructure for a given location are summed to determine the location's overall GVW. These GVWs are used to rank the various locations.
Anthony Koonce NSE September 2006
The next section describes the MIT methodology, as it applies to the bulk power grid, in detail. Detail of the grid and customer groups used in the work are also provided.
Anthony Koonce NSE NSE September September 20U6'2UUb
3. Methodology
3.1 OverviewThe MIT risk ranking methodology is a systematic process to analyze failures in an infrastructure and rank them according to their impacts on the stakeholders. The work presented in this paper is an application to the bulk power grid of the methodology
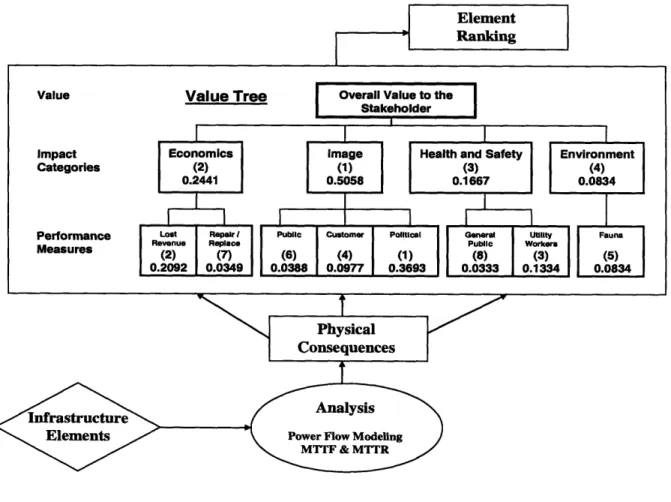
developed in References 18, 23, and 24. The stakeholders used in this presentation are five members of an electric utility company. Figure 1 illustrates the methodology. Although details will be provided later, a brief overview is given here.
Figure 1: Methodology overview.
The methodology begins by identifying assets and components of the bulk power infrastructure that will be included in the analysis. Analysis of the infrastructure is then preformed, using the Sandia AC load flow simulation model [26], to determine the physical consequences resulting from the failure of the components. These consequences include the number and type of customers affected, and the duration of the power
outages. These consequences are input to a value tree that incorporates the stakeholders' views of possible impacts. The value tree is then used to determine the impact the consequences have on these stakeholders. The amount of impact a component represents to the stakeholder is its value. Each component value is then combined with its
susceptibility to failure or attack. The combination of value and susceptibility is then used to rank the components according to their risk significance. The following subsections describe the process of this methodology in detail.
3.2 Infrastructure Elements
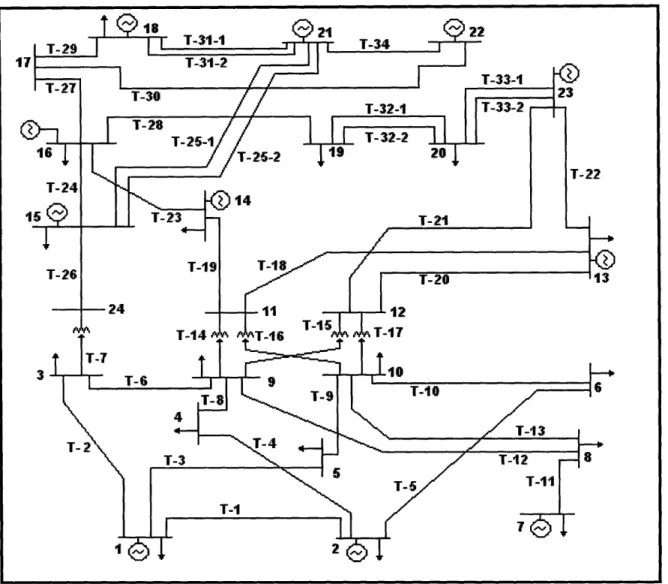
The IEEE 1996 Reliability Test System (RTS-96) [27] is a test grid that has been established to evaluate bulk power reliability analysis techniques. The system does not resemble any portion of the North American power grid but has been developed to provide a universal standard that could be used for diverse applications (Ref. 27). The
single area RTS-96 is used as the study grid for our application.
The single area RTS-96 grid (Figure 2) contains 24 buses and 38 transmission lines. The buses consist of 9 load only buses, 8 load/generation buses, 3 generation only buses, and 4 transmission buses (no load or generation on the bus). Reference 27
provides data for generators, buses, and transmission lines that include capacities, failure rates and probabilities, mean times to repair/failure (MTTR/MTTF), and line lengths. However, there are no established customers associated with the RTS-96 grid. This requires that an artificial customer load be created and placed on the grid for our work.
Anthony Koonce NSE NSE September 2006September 2006
Figure 2: Single area IEEE RTS-96 grid (Ref. 27).
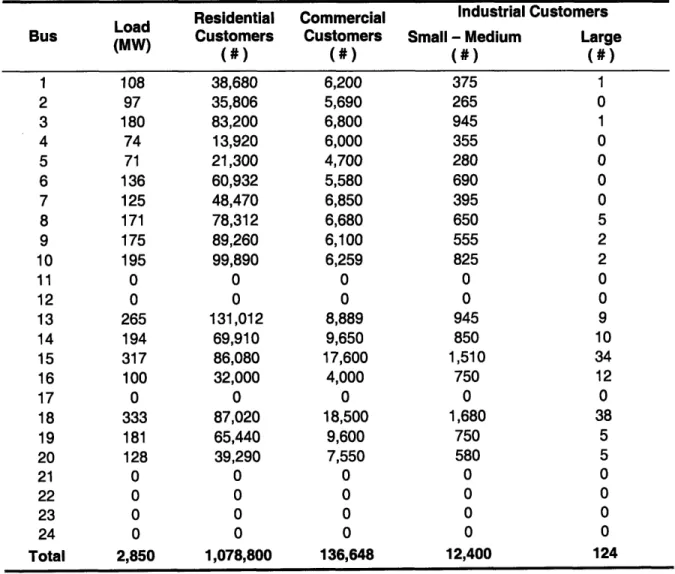
We introduce four customer groups: Residential customers, Commercial
customers, Small - Medium Industrial customers, and Large Industrial customers. These customer groups were selected based on Edison Electric Institute [28], which identifies the customer groups as Residential, Commercial, and Industrial. The Industrial customer
group was split into two groups, small - medium and large, so that the differences between these customer types could be included in the analysis, e.g., the impact due to down time, equipment re-start time, and the loss of product that results from power interruptions as discussed in the IEEE Gold Book [29].
Customers for each customer group were placed on each load bus using national average usage data (Ref. 28) and the load history for the system (Ref. 27). These customers were added to each group until the load capacity of the RTS-96 was reached. Table 1 shows the customer loading. To simulate diversity within the grid, the customers
are not placed in the same ratio among the groups on each bus. These customer groups were developed and applied to the grid prior to the infrastructure analysis. For
application to an actual portion of the North American power grid, an assessment of the customers on the grid would be required. This assessment could be done using the utility company's customer data or by surveying the area which the analysis would cover.
Commercial Customers (#) 6,200 5,690 6,800 6,000 4,700 5,580 6,850 6,680 6,100 6,259 0 0 8,889 9,650 17,600 4,000 0 18,500 9,600 7,550 0 0 0 0 136,648 Industrial Customers Small - Medium Large
(#) (#) 375 1 265 0 945 1 355 0 280 0 690 0 395 0 650 5 555 2 825 2 0 0 0 0 945 9 850 10 1,510 34 750 12 0 0 1,680 38 750 5 580 5 0 0 0 0 0 0 0 0 12,400 124
Table 1: Customer data per bus.
Anthony Koonce NSE September 2006
Bus 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 Total Load
(MW)
108 97 180 74 71 136 125 171 175 195 0 0 265 194 317 100 0 333 181 128 0 0 0 0 2,850 Residential Customers (#) 38,680 35,806 83,200 13,920 21,300 60,932 48,470 78,312 89,260 99,890 0 0 131,012 69,910 86,080 32,000 0 87,020 65,440 39,290 0 0 0 0 1,078,800 September 2006 NSE Anthony KoonceThe infrastructure elements whose failures will be investigated are the generators, buses, and transmission lines that make up the bulk power grid. The threats to these elements include both random failures and malevolent acts. Malevolent acts are the intentional disruption of the infrastructure by purposely preventing a component from carrying out its designed operation.
Single-failure scenarios are used as the failure scenarios in the presentation of this methodology. As for attacks, only minor threats are considered. Minor threats are threats, such as vandalism or employee sabotage, that have the ability to attack a single infrastructure asset, but do not possess the ability to attack multiple assets with a coordinated attack. Even though the failure of multiple components would likely have larger consequences, the likelihood of multiple failures may decrease drastically, a fact that would partly offset their importance or value in the ranking process. This single-component limitation was made in part due to the limitations of the model used to analyze the power grid at this time and due to the rapidly increasing number of
combinations of simultaneous events. If the present work included an actual portion of the North American power grid, the investigation of higher-order vulnerabilities would need to be covered to include coordinated attacks on multiple targets, as well as
concurrent failures of two or more assets.
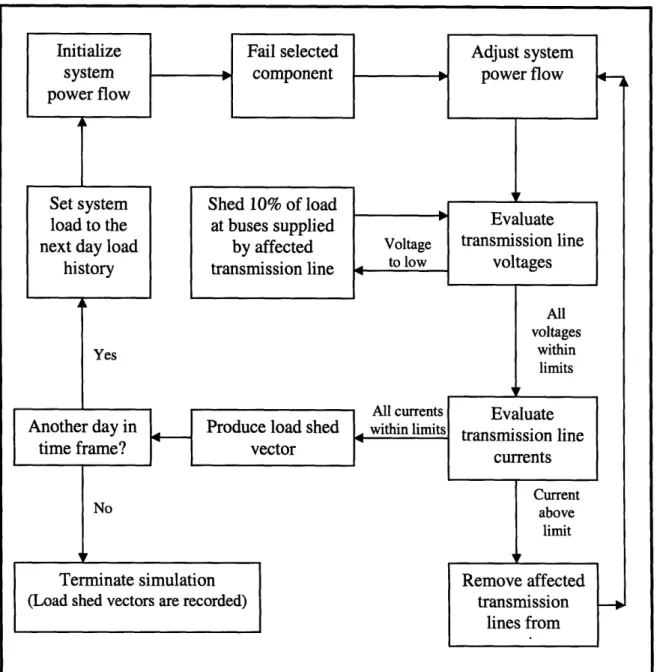
3.3 Infrastructure Analysis
The infrastructure analysis of the bulk power grid employs an AC load flow simulation model developed at Sandia National Laboratories (Ref. 26). For input into the load flow model, the single area RTS-96 is modeled as a network that includes the buses as nodes and the transmission lines as arcs. Node data include the real and reactive power generating capacity, the real and reactive power load demand, the customer loading, and the peak load history for each day in a 52 week year (364 days). Arc data include the voltage and current capacities (Ref. 27). The load flow model is currently limited to modeling only one generator per bus. Work is underway to update the program's generator modeling characteristics and allow for the modeling of multiple
generators on each bus. The analysis presented in this work combines the total generating capacity on each bus and treats it as a single generator.
Figure 3: Infrastructure analysis overview.
Figure 3 provides an overview of the infrastructure simulation model.
Infrastructure analysis begins by selecting a system component (generator, transmission line, or bus) to be failed and the time frame for the analysis. The analysis time frame can
Initialize
Fail
selected
Adjust
system
system P component P power flow
power flow
Set system Shed 10% of load E
load to the at buses supplied Evaluate
next day load by affected Voltage transmission line
hisoryto
low
voltages
history transmission line to low voltages
All voltages
Yes within
limits All currents Evaluate Another day in Produce load shed within limits
time frame? vector transmission linecurrents
Current
No above
limit
Terminate simulation Remove affected
(Load shed vectors are recorded) transmission
lines from
be any time length between one day and 364 days (the entire load history period). This allows the analysis of the bulk power grid to be performed using varying seasonal data, such as the effects of the weather on component failure rates/frequencies and the consequences resulting from component failures during extreme cold/hot seasons. The number of days selected in the time frame will be the number of simulations run for the
selected component. Transmission line 4 is selected as the failed component along with a time frame of 21 days and will serve as the example throughout this section.
The load flow simulation model uses a quasi-steady state step in time to
determine the effects an initial, single-component failure has on the entire infrastructure. This step in time simulation has the ability to identify components in the grid that
experience conditions outside of their limits, e.g., transmission lines that experience over current conditions. These components are then tripped off line causing a cascading effect to be captured. This cascading effect can result in the initial, single-component failure causing more load shed than a normal stability analysis would conclude.
The power flow model begins by initializing the system with a stable flow for the first day of the time frame. To do this, the system loading for the day is determined by the load history data provided in the RTS-96 (Ref. 27). The day's peak load is assumed to last the entire day. A stable flow is established when the existing load is being supplied with power from available generators and each transmission line is within its voltage and current capacities.
Once the system is in a fault-free, stable condition, the selected component is failed (transmission line 4 for our example). The introduced fault of the selected component causes a disturbance in the power flow. The simulation model adjusts the generated power at each generator to attempt to regain a stable flow in response to this disturbance. Power is adjusted until the generating capacity is reached or the load is met
on each bus, which ever occurs first. The current and voltage on each transmission line is tracked during this power adjustment.
Any transmission line that has a voltage below its limit requires load to be shed in order to bring the line voltage within specifications. Load shedding is done in 10%
increments of the total bus load. This incremental load shed is done to simulate the segregation of load by the various branches leaving the bus in the distribution system. This simplifying assumption is made due to the RTS-96 not possessing an established distribution system that further carries the electric power from the bulk power grid to the end users. If an actual portion of the North American bulk power system were analyzed, where the distribution system is identifiable, the increments of load that may be shed at each bus would be determined by the configuration and priority of each branch in the distribution system. After each transmission line voltage is verified within its limits, the current on each line is investigated.
The simulation model identifies the transmission lines that are carrying a current above its limit. Transmission lines with excessive current will be tripped out of service
and will require additional adjustment to the load flow. Any adjustment to the load flow will require the transmission line voltages to be reevaluated as in the previous step.
Once a stable load flow has been reestablished, the amount of load shed at each bus is recorded within a load shed vector and the simulation is repeated for the next day
in the time frame or terminates if the time frame is complete. To complete the analysis of the components in the system, the entire simulation process is repeated for each
remaining component using the same time frame.
The load shed vector is an N-dimensional vector that represents the effect the failed component has on the system with N being the number of buses in the grid. N is 24 for the single area RTS-96 grid. Each element of the load shed vector is the
percentage of load at its respective bus that has been shed to regain stability in the
system. The elements that correspond to a transmission bus (no customers present on the bus) will always be zero. Since the simulation can encompass several days, a separate
load shed vector is produced for each day of the simulation time frame. Our example time frame is 21 days; therefore, 21 load shed vectors are produced for the failure of
transmission line 4.
The affected component, the number and type of customers affected, and the duration of the power outages make up the physical consequences of system failures. The
September 2006 NSE
type and number of customers affected by load shedding is determined by the load shed vectors. It is assumed for the RTS-96 customer base that the customers on a bus are evenly dispersed over the distribution system branches (10% increments) of the bus. That is, if a bus experiences a 20% load shedding during a failure scenario, 20% of each customer group on that bus will be shed to meet the load shedding requirement. The duration of the power outage is determined by the failed component. The duration of a failure scenario is assumed to be the component's mean time to repair (MTTR) or permanent outage duration time as specified in the RTS-96. For our example,
transmission line 4 is the failed component so the duration of the scenario is 10 hours. This time equates to the required time to repair the line and is listed as its permanent outage duration time listed in Reference 27.
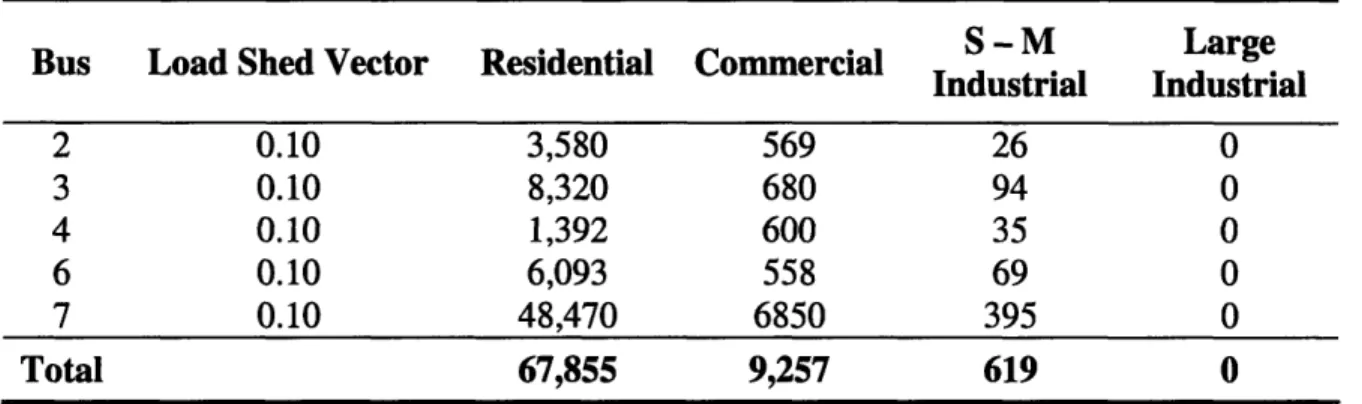
As mentioned previously, the time frame selected for the analysis determines the number of load shed vectors calculated for each component in the system. Due to the system load history (a different peak load for each day), these load shed vectors for a single component may vary throughout the time frame. We assume that the load shed vector that results in the largest amount of load shed is the representative vector for the component. The customer portion of the physical consequences of losing transmission line 4 is given in Table 2. The zero elements of the load shed vector are omitted since there would be no load loss on their associated buses. It is not allowed to shed a portion of a single customer, for this reason, there are no large industrial customers lost upon failure of transmission line 4.
Anthony Koonce NSE September 2006
S - M Large
Bus Load Shed Vector Residential CommercialM Large
Industrial Industrial 2 0.10 3,580 569 26 0 3 0.10 8,320 680 94 0 4 0.10 1,392 600 35 0 6 0.10 6,093 558 69 0 7 0.10 48,470 6850 395 0 Total 67,855 9,257 619 0
Table 2: Customer portion of physical consequences for transmission line 4.
3.4 Value Tree and Constructed Scales
As described in Reference 23, the value tree is based on multi-attribute utility theory (MAUT) and provides a hierarchical view of the impact each failure scenario may have on the stakeholders. The value tree consists of three levels in which the top level is the overall impact, or value, of a failure scenario (Figure 1). The second level breaks this overall impact into broad categories called impact categories (IC). The ICs are further reduced in the third level to specific aspects, called performance measures (PM), that specifically describe the various ways consequences result in impacts to the stakeholders. Each PM is divided into various levels of impact called the constructed scales (CS). The levels of the CSs represent the amount of impact the physical consequences have on the stakeholder through each PM. The levels for each CS range from no impact to complete impact to the PM.
The value tree is constructed using stakeholder input regarding the ways in which they may be affected by system failures. This is done by the stakeholders defining the ICs, PMs, and CS that make up their value tree. Once the value tree is formed, the
stakeholders' view of importance regarding each IC, PM, and CS is modeled. The importance modeling is done by assessing the stakeholders' beliefs using pairwise comparisons. These comparisons are then used in calculating the weights for the ICs, PMs, and each level in the CSs. The IC and PM weights represent their contributions to the overall impact. The weight of a CS level represents the amount of impact felt by the
September 2006
stakeholders when the physical consequences result in that level. Since the impacts felt by the stakeholders are negative impacts, the amount of impact is referred to as the disutility.
For each failure scenario, the physical consequences result in a CS level being impacted for each PM. The PM weights and disutility is then used to determine the overall impact felt by the stakeholder. The overall impact of a scenario is called its performance index (PI) and is used in the component ranking process.
The construction of the value tree and its weights used for the present work are presented here as an example of this methodology. The CSs used in this work are then
discussed followed by an example of the process used to determining the PI of each failure scenario.
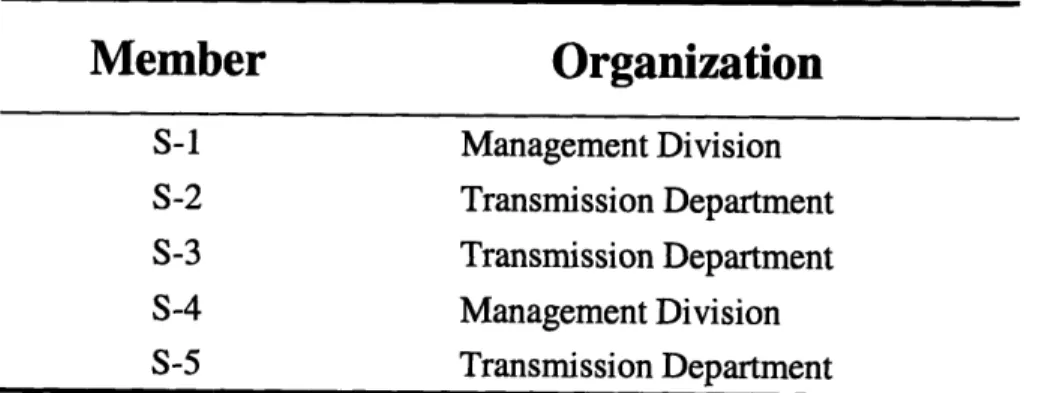
The stakeholders that participated in the construction of the value tree are five members of a regional electric utility company affiliated with the management and transmission departments at the company, Table 3. They worked together to form the
value tree in a workshop. Input for the weights associated with the value tree was provided independently by each member. The input provided by the senior participating member, referred to as S-1, will be the primary input for this work and is presented as the example in this section. The input provided by the remaining four members (S-2 through S-5) will be discussed in the next section and used as a sensitivity analysis on the
application of the methodology.
Member
Organization
S-1 Management Division S-2 Transmission Department S-3 Transmission Department S-4 Management Division S-5 Transmission DepartmentTable 3: Participating members' affiliation with the electric utility company.
Anthony Koonce NSE September 2006
Figure 1 contains the value tree that represents the consensus of the five stakeholders (excluding the weights). Economics, Image, Health & Safety, and
Environment were defined as the ICs and were deemed sufficient to encompass all
possible impacts felt by the company following a failure in the power grid. Economics was divided into Lost Revenue, which accounts for the financial impacts due to power not supplied during an outage, and Repair/Replace, which is the cost associated with
restoring the failed component. Image defines the impacts to the company's image following an outage and was split into the company's Political, Public, and Customer image. Political defines the impact system failures have on the local, state, and federal authorities which may propose additional regulations on electric generating and
transmission companies. Public refers to the general public's view of and confidence in the company's ability to provide reliable power. Customer defines the company's relationship with non-residential customers and is assumed to be directly tied to the customer's incurred cost due to a power outage. Health & Safety was divided into
General Public and Utility Workers. General Public is meant to account for the effects on the public when power outages affect medical facilities, emergency response services, transportation networks, and daily life conveniences such as heating and cooling a home.
Utility Workers accounts for the increased safety concerns of the company regarding its
employees that are responsible for repairing the failed component. Environment was assigned a single PM which is Fauna. Fauna defines the affect failure scenarios have on the wildlife in the region with specific consideration to fish population associated Hydro-Electric generation.
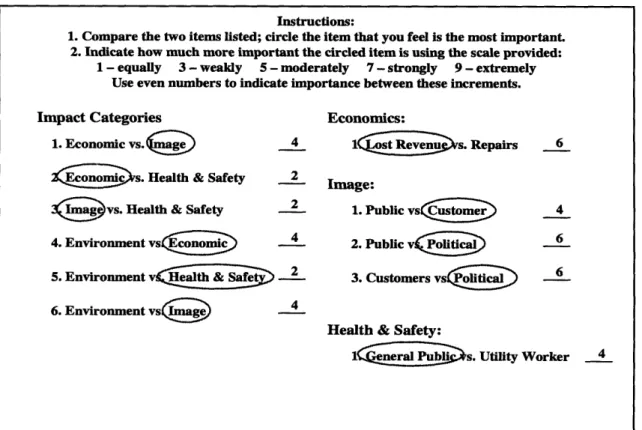
To evaluate the weights present in the value tree, the participating members were provided surveys in which they performed pairwise comparisons between the ICs. They first identified which ICs they felt were more important and to what extent. This process is shown in Figure 4 (using the input provided by S-1). For example, this stakeholder judges that the IC Health & Safety is equally or slightly more important than the IC
Environment. The same stakeholder believes that the PM General Public is weakly to
moderately more important than the PM Utility Workers with respect to Health & Safety.
September 2006 NSE
It is very important to point out that the stakeholders have already been informed about the possible ranges of the consequences and are making their evaluations being fully aware of these ranges. In the present case, it was the consensus that the potential impacts of failures on both Health & Safety and the Environment were very small, unless a major
catastrophic event disrupted a majority of the grid. The stakeholder assessments were made under this assumption.
Figure 4: Survey of stakeholder input.
The stakeholder input is placed into a matrix and the weights are determined using the Analytic Hierarchy Process (AHP) [30]. Although several methods exist in the literature for evaluating weights [31], this method was used because the stakeholders find the pairwise comparisons easier to implement. The AHP results were scrutinized to make sure they represented the stakeholder views.
The CSs used for this work are presented in Table 4 - Table 7. AHP is also used for the determination of the disutility for each level of the CSs. Disutility is a
Instructions:
1. Compare the two items listed; circle the item that you feel is the most important. 2. Indicate how much more important the circled item is using the scale provided:
1 - equally 3 - weakly 5 - moderately 7 - strongly 9 - extremely Use even numbers to indicate importance between these increments.
Impact Categories Economics:
1. Economic vs.4 4 1(i Q Relven s. Repairs 6
Ks. Health & Safety 2 Image:
(iavs. Health & Safety 2 1. Public vs 4
4. Environment vsEconomic 2. Public v(i6
5. Environment v S 2 3. Customers vso 6
6. Environment vs( 4
Health & Safety:
1~us. Utility Worker 4
monotonically non-decreasing function that defines the amount of impact a level in the CS has on its PM. For this reason, the disutilities in each CS range from no impact (0.0000) to complete impact (1.0000) of the PM.
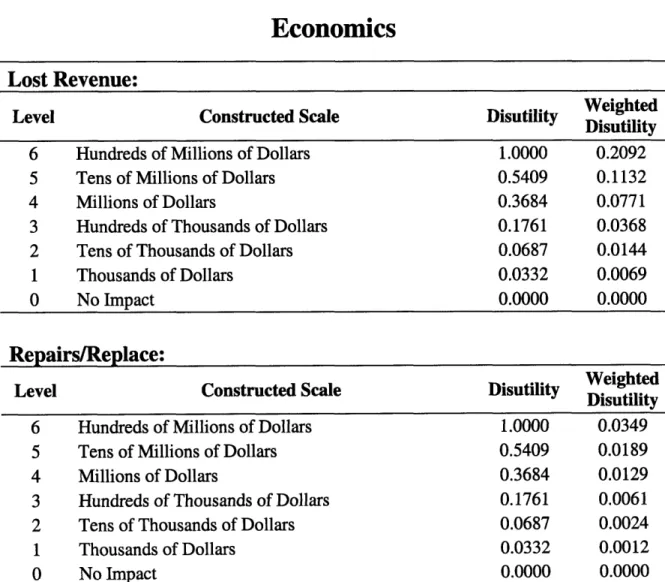
Economics
Lost Revenue:
Level Constructed Scale Disutility eighted
Disutility
6 Hundreds of Millions of Dollars 1.0000 0.2092
5 Tens of Millions of Dollars 0.5409 0.1132
4 Millions of Dollars 0.3684 0.0771
3 Hundreds of Thousands of Dollars 0.1761 0.0368
2 Tens of Thousands of Dollars 0.0687 0.0144
1 Thousands of Dollars 0.0332 0.0069
0 No Impact 0.0000 0.0000
Repairs/Replace:
Level Constructed Scale Disutility WeightedDisutility
6 Hundreds of Millions of Dollars 1.0000 0.0349
5 Tens of Millions of Dollars 0.5409 0.0189
4 Millions of Dollars 0.3684 0.0129
3 Hundreds of Thousands of Dollars 0.1761 0.0061
2 Tens of Thousands of Dollars 0.0687 0.0024
1 Thousands of Dollars 0.0332 0.0012
0 No Impact 0.0000 0.0000
Table 4: Constructed scales for Economics performance measures.
Image
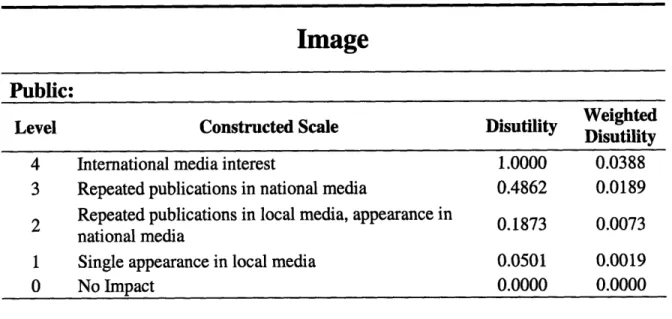
Public:
Weighted
Level Constructed Scale Disutility Weighted
Disutility
4 International media interest 1.0000 0.0388
3 Repeated publications in national media 0.4862 0.0189
2 Repeated publications in local media, appearance in 0.1873 0.0073 national media
1 Single appearance in local media 0.0501 0.0019
0 No Impact 0.0000 0.0000
Political:
Weighted
Level Constructed Scale Disutility Weighted
Disutility
3 Political push for major regulation reform 1.0000 0.3693
2 Moderate political push for additional regulations 0.3606 0.1332
1 Low political influence on industry regulations 0.1604 0.0592
0 No Impact 0.0000 0.0000
Customer:
Level Constructed Scale Disutility eighted
Disutility
5 Billions of Dollars 1.0000 0.0977
4 Hundreds of Millions of Dollars 0.5069 0.0495
3 Tens of Millions of Dollars 0.3317 0.0324
2 Millions of Dollars 0.1492 0.0146
1 Hundreds of Thousands of Dollars 0.0566 0.0055
0 No Impact 0.0000 0.0000
Table 5: Constructed scales for Image Performance Measures.
Health & Safety
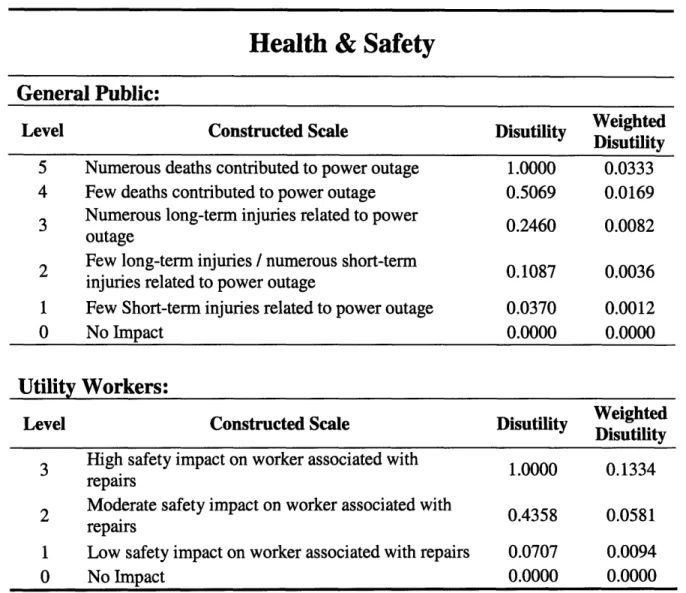
General Public:
Level Constructed Scale Disutility Weighted
Disutility
5 Numerous deaths contributed to power outage 1.0000 0.0333
4 Few deaths contributed to power outage 0.5069 0.0169
3 Numerous long-term injuries related to power 0.2460 0.0082
outage
2 Few long-term injuries / numerous short-term 0.1087 0.0036
injuries related to power outage
1 Few Short-term injuries related to power outage 0.0370 0.0012
0 No Impact 0.0000 0.0000
Utility Workers:
Weighted
Level Constructed Scale Disutility Weighted
Disutility
3 High safety impact on worker associated with 1.0000 0.1334
repairs
2 Moderate safety impact on worker associated with 0.4358 0.0581
repairs
1 Low safety impact on worker associated with repairs 0.0707 0.0094
0 No Impact 0.0000 0.0000
Table 6: Constructed scales for Health & Safety performance measures.
Environment
Fauna:
Weighted
Level Constructed Scale Disutility Weighted
Disutility 3 Extensive impact on wildlife, decades required for 1.0000 0.0834
full recovery
2 Moderate impact on wildlife, few years required for 0.2842 0.0237 full recovery
1 Minor impact on wildlife, recovers quickly with no 0.0686 0.0057 lingering impacts
0 No Impact 0.0000 0.0000
Table 7: Constructed scales for Environment performance measures.
To determine the level in which physical consequences impact the stakeholders, the physical consequences are mapped onto the CSs of each PM. The mapping technique used is determined as shown in Table 8. Sum means that the effects on each customer group are determined and then summed to determine the level of impact. The
consequence matrix follows the approach presented in Reference 21 where the effects on each customer group are determined and then the customer group that results in the highest level of impact is chosen as the representative group for the PM. Component specific means that the level of impact is determined solely by the failed component in the failure scenario. Inspection means that the effects a failure scenario has on the infrastructure itself and not the customers is used to determine the level of impact. An example of each mapping technique is presented here using our example failure scenario (transmission line 4, 21 day time frame) to help clarify the process.
Anthony Koonce NSE September 2006
IC
PM
Mapping Technique
Economic Lost Revenue Sum
Repair/Replace Component Specific
Public Consequence Matrix
Image Political Consequence Matrix
Customers Consequence Matrix
Health & General Public Consequence Matrix
Safety Utility Worker Component Specific
Environment Fauna Inspection
Table 8: PM mapping techniques.
Sum is only used by the Lost Revenue PM. Each customer group has an associated average energy consumption (kWh) and rate charged per unit of energy consumed ($/kWh). The physical consequences give us the number of customers in each group that is affected and the duration of the outage. Using this information we have:
$=
[(N
i)(Ri)
-
ii)](T
(1)
i=l where;
$ is the resulting lost revenue
n is the number of customer groups included in the analysis (four in our case) Ni is the number of customers in group i
Ri is the rate charged to a customer in group i
Ui is the average electric power usage for a single customer in group i T is the duration of the scenario
The lost revenue for our example is $140,525. This results in transmission line 4 being placed in level 3 for Lost Revenue which has a disutility of 0.1761 to the stakeholder (Table 4).
NSE September 2006
The mapping technique "Component Specific" (Table 8) will be illustrated using the Repair/Replace PM. The cost to restore a failed component depends on the
component itself and the way the component failed. The component may be able to be repaired or might be required to be replaced, depending on the level of damage to the component. The cost should include the price of repair parts as well as the cost of equipment used and wages paid due to the man-hours required to restore the component. Company historical data may also be used to evaluate the average cost to restore a type of component and to determine its impact. Here, we assume that the cost to restore a
transmission line does not exceed $50,000 but is no less than $10,000. This assumption is based on the required cost to repair a transmission line by looking at the labor of the worker, equipment operation cost, and material cost associated with the repairs. This puts transmission line 4 into level 2 for Repair/Replace which has a disutility of 0.0687 to the stakeholder.
The consequence matrix requires the construction of a matrix that relates the duration and number of customers affected by a failure scenario to the CS. This is done by evaluating the response of the customer groups to past power outages of various sizes and durations. We use discrete estimates of magnitude and duration of the physical consequences to determine the expected impact level for the CS. The consequence matrix for the Customer PM is provided in Table 9 for our example. The physical consequences for transmission line 4 (Table 2) lead to a level 3 impact based on
Commercial, a level 3 based on S-M Industrial, and a level 0 based on Large Industrial. Since the maximum level among all groups is a level 3 impact, transmission line 4 is put into level 3 with a 0.3317 disutility to the stakeholder (Table 5).
Anthony Koonce NSE September 2006
Commercial S - M Industrial Large Industrial v Duration:
10 hours 1 day I week 10 hours I day 1 week 10 hours 1 day 1 week
5 100,000 50,000 30,000 N/A N/A 4,000 N/A N/A N/A
4 10,000 5,000 3,000 3,000 2,000 400 N/A N/A N/A
3 1,000 500 300 300 200 40 N/A 100 20
0
" 2 100 50 30 30 20 4 15 10 1
U 1 10 5 3 3 2 1 2 1 N/A
0 0 0 0 0 0 0 0 0 0
Table 9: Consequence matrix for Customer PM
The mapping technique "Inspection" is used only in the Fauna PM and is focused on the effects caused during power production increases at Hydro-Electric facilities that result in an impact on the local fish population. As power is increased at the Hydro-Electric generator, more water is forced through the generating house which results in less water that is allowed to bypass. Affecting this ratio of power production and bypass flow has effects on the fish population in the river. For this reason, the amount of power increase at these facilities and the duration of this power increase are the factors that affect this PM. Since the output of the simulation model (load shed vectors) does not give the increase in power production at each generation location, this information is determined through inspection. The difference between the amount of load shed and
generation disconnected from the grid during a failure scenario is used to determine the increase demand placed on the generators remaining connected to the grid. It is also assumed that any increase in demand will be shared among the remaining generators. This difference in the amount of generation disconnected and load shed is used to create a unique consequence matrix for this PM and is presented in Table 10. The values in this matrix represent the amount of excess load that will be placed onto the remaining generators, including the Hydro-Electric facilities. If a failure scenario results in more load shed than generation disconnected, or if the hydro plants are disconnected from the grid, the effect on the Fauna PM is evaluated at a level 0. Transmission line 4 results in a
NSE September 2006
generation lost to load shed of -174 MW which results in a level 0 impact with a 0.0000 disutility to the stakeholder.
Generation Lost - Load Shed (MW) 0 Duration:
10 hours 1 day I week
3 N/A N/A 5000
= 2 1,00 1,000 500
4 1 500 500 100
0 0 0 0
Table 10: Matrix for Fauna PM.
To determine the performance index (PI) of a failure scenario, we use Equation 2 (Ref. 18)
KpM
PIj = widij (2)
i=1
where
PIj is the performance index of failure scenario j wi is the weight of performance measure i
dij is the disutility of performance measure i and failure scenario j KpM is the total number of performance measures
Table 11 gives an overview of the level of impact to each PM along with the PM weights for our example failure scenario (stakeholder S-1). Using the disutilities, PM weights for
S-1, and equation 2, the resulting PI for transmission line 4 is 0.0884. This PI represents
the value transmission line 4 has to S-1.
Anthony Koonce NSE September 2006
PM Level of Weighted
PM Weight Impact Disutility Disutility
Lost Revenue 0.2092 3 0.1761 0.0368 Repair / Replace 0.0349 2 0.0687 0.0024 Public 0.0388 2 0.1873 0.0073 Political 0.3693 0 0.0000 0.0000 Customer 0.0977 3 0.3317 0.0324 General Public 0.0333 0 0.0000 0.0000 Utility Worker 0.1334 1 0.0707 0.0094 Fauna 0.0834 0 0.0000 0.0000
Table 11: Impacts to each PM for transmission line 4.
3.5 Ranking
The work presented up to this point has been focused on determining the value of failure scenarios in the bulk power grid. So far, the first and third questions of risk assessment have been answered. The second question (likelihood) remains to be addressed.
To review before we continue, there were two types of threats addressed by this methodology, random events and minor malevolent acts. As discussed earlier, while the likelihood of random events is determined by the scenario frequency, the likelihood of malevolent acts is not addressed by this methodology but, rather, the susceptibility to an
assumed threat is evaluated (Ref. 18).
For random failures, the frequency of a failure scenario is multiplied by the scenario's value to determine the expected disutility to the stakeholder. As described in Reference 23, the random failures of the infrastructure elements are then ranked
according to their expected disutility.
For malevolent acts, we follow the approach proposed in Reference 18. The "susceptibility" of a component is judged subjectively by accessing the quality of security
September 2006 NSE
measures and openness of the component. Reference 18 proposes six levels of susceptibility to malevolent acts ranging from completely secure (the lowest level) to completely open (the highest level). These susceptibility levels are given in Table 12.
Level Description 5 - Extreme 4 - High 3 - Moderate 2 - Low 1 - Very Low 0 - Zero
Completely open, no controls, no barriers
Unlocked, non-complex barriers (door or access panel) Complex barrier, security patrols, video surveillance Secure area, locked, complex closure
Guarded, secure area, locked, alarmed, complex closure Completely secure, inaccessible
Table 12: Susceptibility levels of infrastructure assets.
As proposed in Referencel8, each component's PI and susceptibility are
combined in order to assign the component to a vulnerability category. This process is illustrated in Table 13. The vulnerability categories are shown in Table 14.
Susceptibility Levels
0.0000 to 0.0049 0.0050 to 0.0299 0.0300 to 0.0499 0.0500 to 0.0999 0.1000 to 0.2499 > 0.2500 zero G G G G G B very low G B B B Y Low G B B Y YO
Moderate G B Y YO
High G B Y0
0
Extreme G B Y O RAnthony Koonce NSE September 2006
Table 13: Susceptibility and value combinations for each vulnerability category.
Susceptibility
Levels
Vulnerability
Category Description
Category
Red This category represents a severe vulnerability in the infrastructure. It is reserved for the most critical locations that are highly susceptible to attack. Red vulnerabilities are those requiring the most immediate attention.
Orange This category represents the second priority for counter-terrorism efforts. These locations are generally moderate to extreme valuable and moderately to extreme susceptible.
Yellow This category represents the third priority for counter terrorism efforts. These locations are normally less vulnerable because they are either less susceptible or less valuable than the terrorist
desire.
Blue This category represents the fourth priority for counter terrorism efforts.
Green This is the final category for action. It gathers all locations not included in the more severe cases, typically those that are low (and below) on the susceptibility scale and low (and below) on the value scale. It is recognized that constrained fiscal resources is likely to limit efforts in this category, but it should not be ignored.
Table 14: Infrastructure asset vulnerability categories for ranking element failures due to malevolent acts.
The present work assesses transmission lines to have an extreme susceptibility (level 5) due to their openness and remote locations. Buses are assessed to have moderate susceptibility (level 3) due to safety fences and possible video surveillance.
Generators are usually located at facilities with security forces and high authorized personnel traffic. For this reason, generators are assessed to have a very low susceptibility (level 1).
Anthony Koonce NSE NSE September 2006September 2006
To complete our example of the failure of transmission line 4, its random failure frequency is 0.39 outages/year. Multiplying this frequency with its PI, we calculate the expected performance index for this transmission line to be 0.03448.
The susceptibility category for transmission lines is extreme and transmission line 4 possesses a moderate PI (0.0884), which results in the line being assigned to the Orange category for vulnerabilities (Table 14).
Anthony Koonce NSE September 2006
4. Discussion
4.1 Stakeholder S-1The input provided by stakeholder S-1 is used to determine the baseline results for the RTS-96 single area grid. S-1 valued Economics and Image as the most important impact categories and this resulted in the Lost Revenue, Political Image, and Customer
Image performance measures being the dominant contributors to the overall value of each
failure scenario. The top ten components ranked by their risk significance with respect to malevolent acts and random events are provided in Table 15 and Table 16, respectively.
An in depth look at the results for the vulnerability rankings showed that there were two major reasons for T-16 and T-17 being placed at the top of the list. These transmission lines connect the upper portion of the grid, where the majority of the generation is located, to the lower portion of the grid. When these lines fail, they limit the amount of power that can be transmitted to the lower portion of the grid causing the transmission lines in the lower portion of the grid to become stressed by increasing their loading. This increased loading results in transmission line T-5 becoming overloaded which then trips and increases the scenario's impact on bus 6. This results in a large number of customers being shed. Transmission lines T-16 and T-17 also have extremely long power outage durations due to their long repair times. This combination of duration
and magnitude causes a high level impact to both Political Image and Lost Revenue. Another interesting result of the vulnerability ranking for S-1 is that the amount of load shed alone does not determine the order in which the components are ranked. This observation is illustrated by the components ranked #6 through #10. The last two
components of the ranking, B-3 and B-4, result in very large load sheds. However, T-14,
T-15, and T-13 result in less load shed but are ranked higher. This is due to the
transmission lines having a much longer duration associated with them. The duration is the key factor here that elevates their impacts to stakeholder S-1.
Anthony Koonce NSE NSE September 2006September 2006