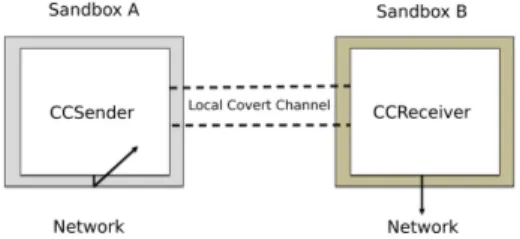
Seeing the Unseen: Revealing Mobile Malware Hidden Communications via Energy Consumption and Artificial Intelligence
Texte intégral
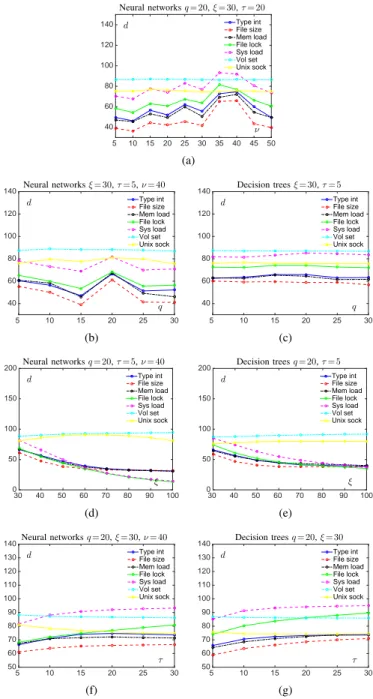
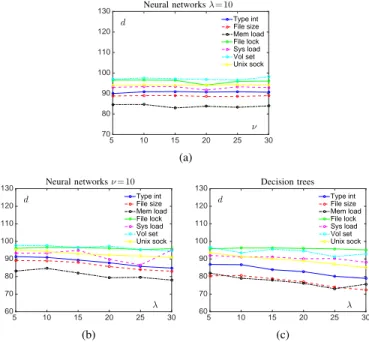
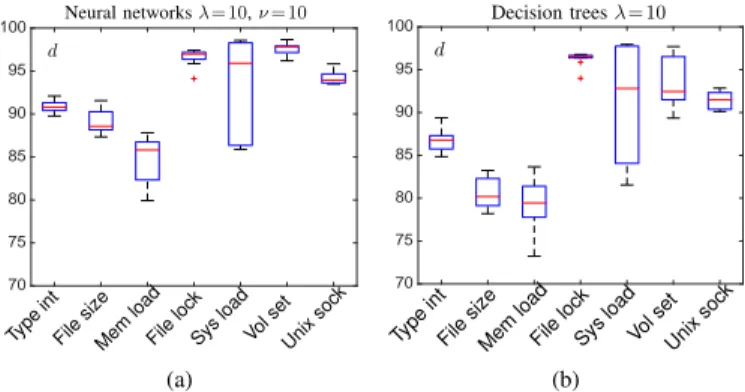
Figure
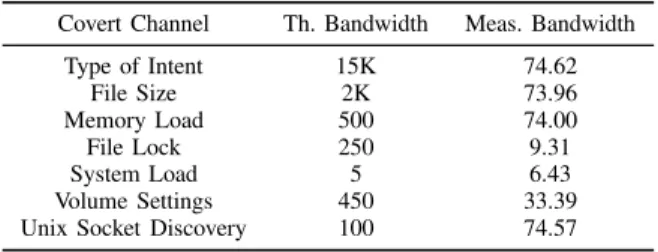
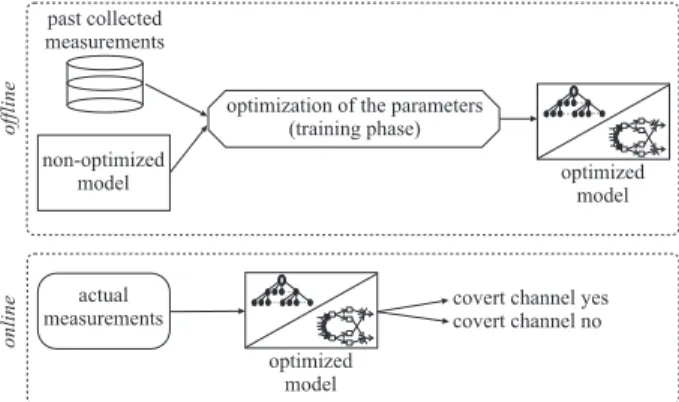
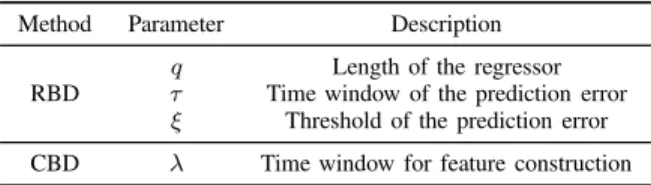
Documents relatifs
Unité de recherche INRIA Rennes : IRISA, Campus universitaire de Beaulieu - 35042 Rennes Cedex (France) Unité de recherche INRIA Rhône-Alpes : 655, avenue de l’Europe - 38334
Key words and phrases: Energy consumption, smart buildings, smart meters, machine learning, random forest, gradient boosting.. Copyright © 2019 for the individual papers by the
We used three methods to improve forecasting energy consumption time series: Support Vector Regression (SVR) [6], a method based on a combination of STL
Nev- ertheless, Big Data technologies and massive clustering techniques are now possible so that the release of a TREC style collection, that is still missing, will help the IR and
We conduct several experiments in order to study the impact of different execution configuration parameters (number of blocks, number of threads per block) and the number of active
2, we have plotted the complex quasiparticle spectrum for strong axial tilt while neglecting the ∝ ω terms in the self-energy, resulting in a flat bulk Fermi ribbon with a
Several technical Key Performance Indicators (KPIs) have been defined to inform users on their building thermal en- ergy consumption, while user-friendly KPIs present energy savings
In order to do so, compare the free energy of a perfectly ordered system with the free energy of a partially disordered case that introduces the less energetic frustrations