HAL Id: hal-01095549
https://hal.archives-ouvertes.fr/hal-01095549
Submitted on 2 Jul 2015
HAL is a multi-disciplinary open access
archive for the deposit and dissemination of
sci-entific research documents, whether they are
pub-lished or not. The documents may come from
teaching and research institutions in France or
abroad, or from public or private research centers.
L’archive ouverte pluridisciplinaire HAL, est
destinée au dépôt et à la diffusion de documents
scientifiques de niveau recherche, publiés ou non,
émanant des établissements d’enseignement et de
recherche français ou étrangers, des laboratoires
publics ou privés.
Analysis of the Implementation of Utility Functions to
Define an Optimal Partition of a Multicast Group
Joël Penhoat, Karine Guillouard, Tayeb Lemlouma, Mikaël Salaun
To cite this version:
Joël Penhoat, Karine Guillouard, Tayeb Lemlouma, Mikaël Salaun. Analysis of the Implementation of
Utility Functions to Define an Optimal Partition of a Multicast Group. Tenth International Conference
on Networks (ICN’11), Jan 2011, St. Maarten, Saint Martin. �hal-01095549�
Analysis of the Implementation of Utility Functions to Define an Optimal Partition
of a Multicast Group
Joël Penhoat, Karine Guillouard
France Télécom Issy-les-Moulineaux, France
{joel.penhoat; karine.guillouard}@orange-ftgroup.com
Tayeb Lemlouma, Mikaël Salaun
Université de Rennes 1 Rennes, France
{tayeb.lemlouma; mikael.salaun}@univ-rennes1.fr
Abstract— As the optimal use of network resources is a major issue for telecoms operators, we started works aiming to, firstly, improve the utilization of network resources by transmitting the IP packets in multicast when possible, secondly, to adapt the format of the data transmitted in multicast to take into account the context of the members of the multicast group, and thirdly to preserve the Quality of Service when a member of the multicast group moves from a radio network to another radio network. The paper shows, through a scenario, how our work will improve the utilization of the resources and then describes our approach.
Keywords- Handover; Multicast group partition; Resource optimization; User's context; Utility function
I. INTRODUCTION
The optimization of the use of the resources of the networks is a major issue for a telecoms operator because it allows him to reduce his operational expenditure (OPEX). In particular, the improvement of the use of the resources of the radio spectrum is necessary as showed in a study [1] led in 2002 by Federal Communications Commission (FCC). This study showed that in a frequency band the rate of use of the radio resources could vary between 5% and 85%.
According to us, the solutions that aim to optimize the use of the network resources must be implemented in each level of the TCP/IP stack. Moreover, interactions must exist among each solution implemented in each level of the stack, i.e. the optimization is based on cross-layer solutions. In the PHY and MAC layers, the Cognitive Radios [2] are designed to improve the use of the radio spectrum resources by exploiting the radio resources vacated by their owners. In 2004, the FCC has asked the IEEE to implement the Cognitive Radios in the frequency range 54 -698 MHz [3]. The IEEE P802.22 standard [4] meets this demand by allowing the use of vacant TV channels by radio equipments operating without radio licenses. In the IP layer, the multicast transmission of data [5] is a known technique for improving the use of the resources in an IP network because it reduces the number of IP packets transmitted over a network when several receivers must receive the same data. In the transport layer, numerous studies have improved the throughput of TCP by taking into consideration the physical characteristics of the networks. For example, the TCP Westwood protocol [6] improves the throughput of a TCP
connection when the IP packets are transmitted over a radio network.
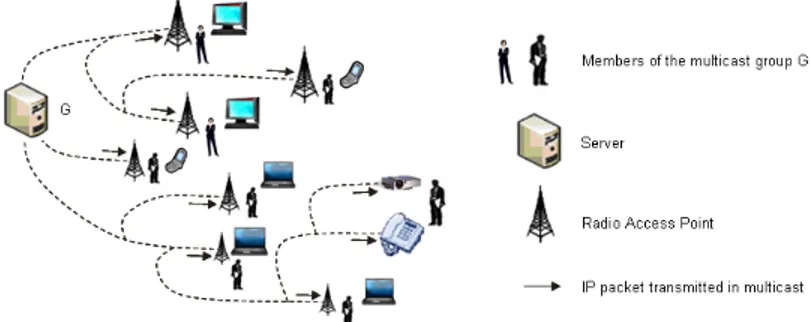
Our study focuses on the improvement of the use of the resources of networks at the IP level by implementing multicast transmissions when the services asked by the users can be transmitted in multicast. During a multicast transmission, all the members of a multicast group (i.e. the users) receive the data in the same format because a multicast transmission does not take into account the heterogeneity of the receivers (mobile phones, laptops, smartphones, tablets), the heterogeneity of the radio networks (GSM, Wi-Fi, WiMAX ...), or the diversity of the profiles of the members of the group (engineer, accountant, student …). The diversity of the receivers, radio networks, or the profiles of the users, are elements that characterize the context of a user. In the article, we use the definition of Abowd et al [7] to define the context of a user. Figure 1 illustrates a scenario in which the members of a multicast group G have different contexts. In addition, as the members of the group may be mobile, their contexts vary during the transmission because they can connect themselves to wireless networks having different characteristics, for example during a handover between a Wi-Fi network transmitting in multicast the IP packets and an Universal Mobile Telecommunications System (UMTS) network transmitting in unicast the IP packets.
Figure 1. Multicast transmission in a heterogeneous context
So, the three objectives of our work are, firstly, to improve the utilization of the resources of the networks by transmitting in multicast the IP packets when possible, secondly, to adapt the format of the data transmitted in multicast to take into account the context of the members of the multicast group, and thirdly to preserve the Quality of
Service (QoS) when a user moves from one radio network to another radio network.
The structure of the article is the following. The second section describes a scenario showing the interest of our works for the telecoms operators. The third section makes an inventory of the works that take into account the context of the users during a multicast transmission and analyzes their loopholes; then the fourth section presents our approach to implement our three objectives. Finally, the fifth section concludes the article and exposes our future works.
II. DESCRIPTION OF A SCENARIO ESTABLISHING A SYNERGY BETWEEN UNICAST AND MULTICAST NETWORKS
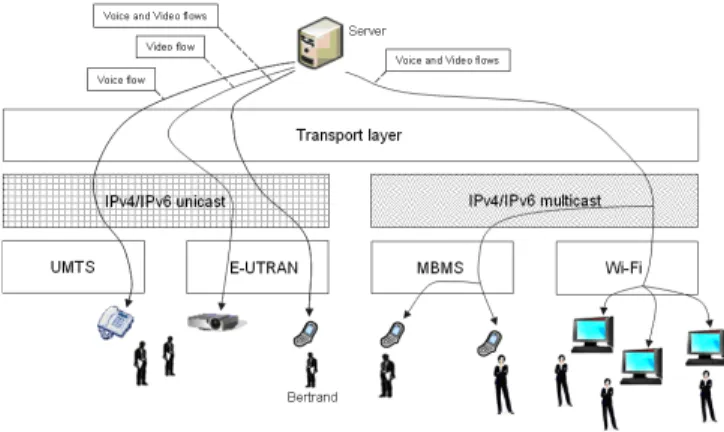
In this section we describe a scenario that could improve the utilization of the resources of the radio networks of a telecoms operator by establishing a synergy between unicast and multicast networks. In our scenario, eight persons, Anatole, Antoine, Bernard, Bertrand, Alice, Bénédicte, Catherine, and Isabelle, take part in a video-conference. The video-conference is made up of a Voice over IP (VoIP) flow and a Video flow. The Video flow is encoded with a Scalable Video Codec [8] that splits the flow into several sub-flows. Our scenario consists of six stages. In the first stage (Figure 2), Anatole and Antoine receive the VoIP flow on a fixed phone and the Video flow on a video-projector.
Figure 2. A scenario describing a synergy between multicast and unicast networks (first stage)
The VoIP flow is transmitted in unicast over a UMTS network that uses IPv4 addresses. The Video flow is transmitted in unicast over an Evolved Universal Terrestrial Radio Access Network [9] that uses IPv6 addresses. The Evolved Universal Terrestrial Radio Access Network is noted E-UTRAN in the figure 2. Bernard, Bertrand and Alice receive the VoIP and Video flows on their smartphones. The VoIP and Video flows are transmitted in multicast over a Multimedia Broadcast Multicast Service network [10] that uses IPv4 addresses. The Multimedia Broadcast Multicast Service network is noted MBMS in the figure 2. Bénédicte, Catherine and Isabelle receive the VoIP and Video flows on their Personal Computers. The VoIP and Video flows are transmitted in multicast over a Wi-Fi network that uses IPv6 addresses. In the second stage (Figure 3), Bertrand moves.
His smartphone, initially connected to the MBMS network, connects itself to the E-UTRAN network. The VoIP and Video flows are transmitted in unicast over the E-UTRAN network that uses IPv6 addresses.
Figure 3. A scenario describing a synergy between multicast and unicast networks (second stage)
In the third stage (Figure 4), Bernard moves. His smartphone, initially connected to the MBMS network, connects itself to the Wi-Fi network. The VoIP and Video flows are transmitted in multicast over the Wi-Fi network that uses IPv6 addresses.
Figure 4. A scenario describing a synergy between multicast and unicast networks (third stage)
In the fourth stage (Figure 5), Bernard, who has a laptop with a Wi-Fi interface, decides to take part in the video-conference via his laptop. Having connected his laptop to the Wi-Fi network, he turns off his smartphone and takes part in the video-conference via his laptop.
Figure 5. A scenario describing a synergy between multicast and unicast networks (fourth stage)
In the fifth stage (Figure 6), the operator who manages the MBMS network notices that the smartphone of Alice is the only device connected to this network. As the smartphone of Alice has a MBMS interface and a Wi-Fi interface, the operator decides that Alice will take part in the video-conference via the Wi-Fi interface of her smartphone without decreasing her QoS. At the end of this operation the resources of the MBMS network are no longer used.
Figure 6. A scenario describing a synergy between multicast and unicast networks (fifth stage)
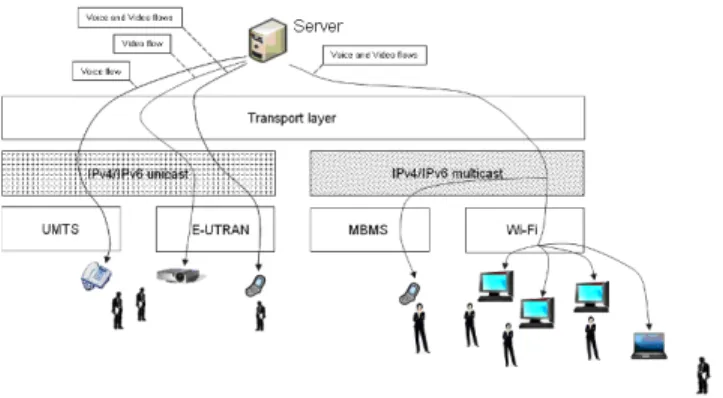
In the last stage of our scenario (Figure 7), Antoine, who has a laptop with a Wi-Fi interface and an E-UTRAN interface, moves. After having turned on his laptop, he receives the VoIP and Video flows via two different interfaces: the VoIP flow is received in unicast via the E-UTRAN interface, while the Video flow is received in multicast via the Wi-Fi interface.
The six stages of our scenario show that a synergy between IPv4/IPv6 unicast radio networks and IPv4/IPv6 multicast radio networks is possible and could interest a telecoms operator. But its implementation raises many questions. Here is a non-exhaustive list of questions. Knowing that the contexts of the members of the multicast group are different, in what format the server should send the data when the IP packets carrying the data are transmitted in multicast? Knowing that the structure of the multicast group may change over time, as we see by comparing the structure of the multicast group between the first and the sixth stage,
how to adapt the format of the transmitted data to reflect these changes? Knowing that the users are mobile, what are the criteria for selecting a radio network during a handover?
Figure 7. A scenario describing a synergy between multicast and unicast networks (sixth stage)
III. IDENTIFICATION AND ANALYSIS OF THE EXISTING WORKS
In this section we identify and analyze the works taking into account the context of the users in a multicast transmission. The first works date from the 1990s. In 1996, McCann et al [11] have proposed to split a multicast group according to the throughput that the terminals of the users can receive. The data flow to be transmitted is encoded in several layers, each layer being transmitted with a certain throughput. The first layer, called the base layer, is necessary to decode the flow, whereas the other layers are used to improve the QoS of the received flow. The QoS of a user is better if the number of layers decoded by his terminal is higher. Each layer is associated with a subgroup of the partition of the multicast group. The subscription to one or several subgroups is made with the Receiver-driven Layered Multicast (RLM) protocol: the terminal of a user chooses to subscribe to one or several subgroups, i.e. to receive one or several layers, according to its decoding capabilities and the available bandwidth in the network. In 2000, Yang et al [12] defined a utility function [13] in the terminal of each user by taking as parameter the throughput received by the terminal. The optimum of the utility function is reached when the throughput received by the terminal is equal to the throughput that it would receive if it was alone in the group. Then, having defined a utility function for each subgroup making up a partition of the multicast group, they mathematically demonstrated that there is a partition, among all the possible partitions, whose sum of the extremums of the utility functions of the subgroups making up the partition is bigger than the sum of the extremums of the utility functions of the subgroups of the other partitions. This partition, which is the optimal partition, is obtained by a centralized process. Several works redefined the utility function implemented in the terminals by Yang et al [12]: Maimour et al [14] modified the function by taking a parameter easier to get than the throughput, namely the transmission delay between the source emitting the flow of
IP packets and each terminal; then Yousefi' zadeh et al [15] chose a utility function continuously differentiable to reduce the complexity of the calculations to realize to obtain the optimal partition. In 2003, Li et al [16] showed that the consideration of the context of the users during a transmission of a video flow in multicast requires a video source having a method of transmission capable of transmitting the flow with various throughputs. Having established a taxonomy of the various methods of transmission of a video flow, they compared the three methods (stream replication, cumulative layering, noncumulative layering) implemented in the processes of partition of a multicast group. From the years 2005, several projects aim to take into account the context of the users in the multicast architectures: in 2008, the C-Mobile project [17] defines a MBMS architecture that takes into account the context of the users; then in 2009, the C-Cast project [18] defines methods for collecting and analyzing the contexts in a multicast architecture.
In the works that we identified, a centralized process calculates the optimal partition from a utility function implemented in each terminal. However, other entities could also implement a utility function: the operators managing networks, the suppliers of a service … Each entity can have its own criteria to define an optimal partition. For example, an operator can define a single multicast group to improve the use of his networks, whereas the users will prefer to define a number of subgroups equal to the number of users for improving the consideration of the contexts of each user. When several entities take part in the partition process, what partition to choose among those proposed by every entity? Who chooses the partition?
Furthermore, in the identified works, the mobility of the users is little studied. The analysis of the mobility requires the following definition. During a handover, when a terminal disconnects itself from a network, this network is called outgoing network; when it connects itself to a new network, this network is called incoming network. The analysis of the existing studies shows two issues. During a handover, what incoming network to choose? Who chooses the network? According to Zdarsky [19], the user chooses the incoming network, while according to Antoniou et al [18], it is the operator managing the network that chooses the incoming network. To take into account the diverse objectives of the entities participating in the selection process, Suciu et al [20] proposed a method called Hierarchical and Distributed Handover (HDHO), and analyzed a scenario composed of three entities, namely a content provider, an operator managing networks, and a user. The objective of the content provider is to choose an incoming network offering a QoS adapted to the flow to be transmitted. The objective of the operator is to choose the least loaded network for transmitting the flow of the content provider. The objective of the user is to choose a network offering the best QoS/Cost ratio for receiving the flow.
It is important to notice that the mobility of a user can cause a new partition of the multicast group due to the variation of the number of the terminals connected to the outgoing and incoming networks. Conversely, a new
partition can cause the mobility of one or more users as shown in the fifth stage of the scenario described in the second section. The works that we identified do not address the interactions that can exist between the partition process of a group and the selection process of an incoming network.
IV. PRESENTATION OF OUR APPROACH
In this section we present our approach to implement our three objectives. The first two objectives seem contradictory. Indeed, the more the number of members in a multicast group is higher, the better the use of network resources. But the more the number of members in a multicast group is higher, the more it will be difficult to take into account the variety of the contexts of the users. It is thus necessary to find a compromise between, on one hand, the multicast transmission of the IP packets and, on the other hand, the consideration of the contexts of the users. Our approach aims at defining several entities that will divide the multicast group into several subgroups according to the context of the users. Three entities, namely the content provider, the operator managing the networks, and the users, are involved in the partition process. The objectives of the three entities are the following ones. The objective of the content provider is to encode his content into one or more different formats according to the encoding processes available on his servers (objective 1); the objective of the operator is to transmit the data in multicast when the multicast transmission is possible and when the consumption of the resources of networks during a multicast transmission of data towards N users is lower than the consumption of the resources of networks during a unicast transmission of data towards N users (objective 2); the objective of the users is to receive the data in a format adapted to their context (objective 3).
The implementation of the third objective is made with the HDHO method. The three entities participating in the selection process of an incoming network are the content provider, the operator managing the networks, and the users. The objective of the content provider is to choose an incoming network offering a QoS adapted to the flow to be transmitted (objective 4). The objective of the operator is to choose the least loaded network for transmitting the flow of the content provider (objective 5). The objective of the user is to choose a network offering the best QoS/Cost ratio for receiving the flow (objective 6). Since our approach is based on the definition of three entities, each with their goals, we must specify how these three entities interact among them to split the multicast group and to select an incoming network during a handover. By referring to the works of Suciu et al [20], we chose the Free Conflict method, the Compromise and Negotiation method, and the Team Enforced method for implementing these interactions.
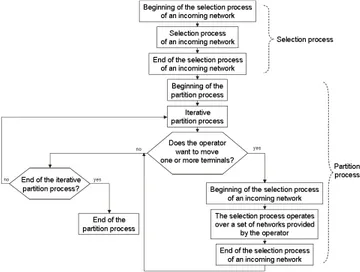
Since the mobility of a user can cause a new partition of the group and as a new partition can cause the mobility of one or more users, the partition process and the selection process interact among them. The interaction between the two processes is described by the heuristic presented in Figure 8. During a handover, the end of the selection process triggers the beginning of the partition process. At each iteration of the partition process, the operator managing the
network can initiate a handover of one or more users to meet its objective. The selected networks must not degrade the QoS of the users.
Figure 8. Heuristic describing the interaction between the selection process and the partition process
Currently we are working on the modules composing the heuristic and we reflect on the way to integrate our approach in a MBMS architecture. Figure 9 shows a possible integration. The objectives of the content provider, namely the objectives 1 and 4, can be implemented in the Broadcast Multicast Service Center (BM-SC) and in the Gateway GPRS Support Node (GGSN). The objectives of the operator, namely the objectives 2 and 5, can be implemented in the GGSN and in the Radio Network Controller (RNC). The objectives of the user, namely the objectives 3 and 6, can be implemented in the user's terminal.
V. CONCLUSION
As the optimization of the use of the resources of the networks is a major issue for telecoms operators, we initiated works that aim to, firstly, improve the use of the resources of the networks by transmitting the IP packets in multicast when it is possible, secondly, adapt the format of the data transmitted in multicast to take into account the context of the users, and thirdly preserve the Quality of Service when a user moves from a radio network towards another radio network. After having shown, through a scenario, how our work would allow to establish a synergy between multicast and unicast networks, we analyzed the works taking into account the context of the users during a multicast transmission. The analysis revealed three loopholes: the terminals of the users are the only entities that participate in the partition process; the mobility of the users is little studied; the listed works do not tackle the interactions that can exist between the partition process and the selection process. Our work, that takes into account these shortcomings, aims to, firstly, define the entities involved in the partition process and the selection process, secondly, define the objectives of these entities, thirdly, define the
partition algorithm according to the objectives of each entity, fourthly, define the interaction between the partition process and the selection process. When these four steps will be made, we will model the partition process and the selection process with OPNET®.
Figure 9. Integration of our approach in a MBMS architecture
REFERENCES
[1] Federal Communications Commission Spectrum Policy Task Force. Report of the Spectrum Efficiency Working Group, 2002.
[2] B.A. Fette, Cognitive Radio Technology (2nd ed). Burlington, MA: Academic Press, 2009.
[3] Federal Communications Commission. Notice of Proposed Rule Making. ET Docket no 04-113, 2004.
[4] IEEE. IEEE Draft Standard for Information technology Telecommunications and information exchange between systems Local and metropolitan area networks Specific requirements Part 22.1: Standard to Enhance Harmful Interference Protection for Low Power Licensed Devices Operating in TV Broadcast Bands, 2009. [5] S. Deering, IETF Network Working Group: RFC 1112. Host
Extensions for IP Multicasting, 1989.
[6] S. Mascolo, A. Grieco, G. Pau, M. Gerla and C. Casetti, End-to-End Bandwidth Estimation in TCP to Improve Wireless Link Utilization. European Wireless Conference, 2002.
[7] G.D. Abowd and A.K. Dey, Towards a Better Understanding of Context and Context-Awareness, LNCS 1707, pp. 304-307, 1999. [8] H. Schwarz, G. Sullivan, T. Wiegand and M. Wien, Text of ISO/IEC
14496-10:200X/FDIS Advanced Video Coding (4th Edition).
International Organisation For Standardisation ISO/IEC
JTC1/SC29/WG11 Coding of Moving Pictures and Audio, 2007. [9] P. Lescuyer and T. Lucidarme, Evolved Packet System (EPS) The
LTE and SAE Evolution of 3G UMTS. Chichester, England: John Wiley & Sons, Ltd, 2008.
[10] R. Huzenlaub, MBMS from A-Z. Karlsruhe, Deutschland: INACOM GmbH, 2006.
[11] S. McCanne, V. Jacobson and M. Vetterli, Receiver-driven Layered Multicast. ACM SIGCOMM, pp. 117-130, 1996.
[12] Y.R. Yang, M.S. Kim and S.S. Lam, Optimal Partitioning of Multicast Receivers. International Conference on Network Protocol, pp. 129-140, 2000.
[13] P. Anand, Foundations of Rational Choice Under Risk (3rd ed). Oxford: Oxford University Press, 2002.
[14] M. Maimour and C. Pham, A RTT-based Partitioning Algorithm for a Multi-rate Reliable Multicast Protocol. Proceedings of the IEEE High-Speed Network and Multimedia Communications Conference, 2003.
[15] H. Yousefi' zadeh, H. Jafarkhani and A. Habibi, Layered Media Multicast Control (LMMC): Rate Allocation and Partitioning. IEEE/ACM Transactions on Networking, 13(3), pp. 540-553, 2005. [16] B. Li and J. Liu, Multirate Video Multicast over the Internet: An
Overview. IEEE Network, pp. 24-29, 2003.
[17] J. Santos, D. Gomes, S. Sargento, R.L. Aguiar, N. Baker, M. Zafar and A. Ikram, Multicast/broadcast network convergence in next generation mobile networks. Computer Networks: The International Journal of Computer and Telecommunications Networking, 52(1), pp. 228-247, 2007.
[18] J. Antoniou, C. Christophorou, C. Janneteau, M. Kellil, S. Sargento, A. Neto, F.C. Pinto, N.F. Carapeto and J. Simoes, Architecture for
Context-Aware Multiparty Delivery in Mobile Heterogeneous
Networks. International Conference on Ultra Modern
Telecommunications & Workshops, 2009.
[19] F.A. Zdarsky and J.B. Schmitt, Handover In Mobile Communication Networks: Who is In Control Anyway? Proceedings of the 30th EUROMICRO Conference, pp. 205-212, 2004.
[20] L. Suciu, M. Benzaid, S. Bonjour and P. Louin, Assessing the
Handover Approaches for Heterogeneous Wireless Networks. 18th
International Conference on Computer Communications and Networks, 2009.