Applying a requirement engineering based approach to evaluate the security requirements engineering methodologies
Texte intégral
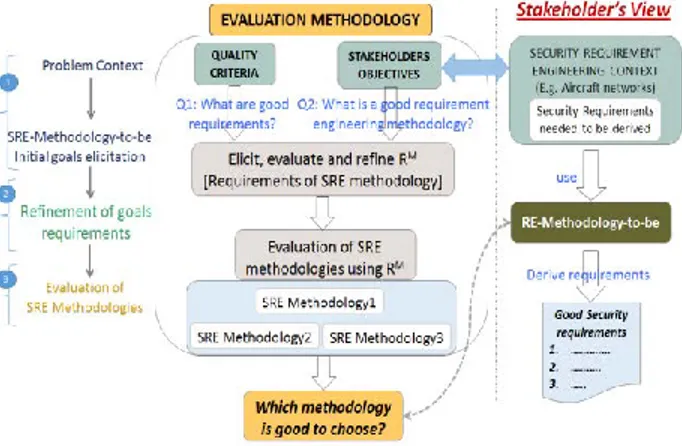
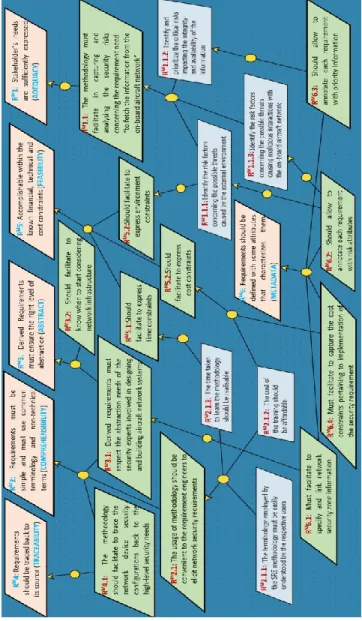
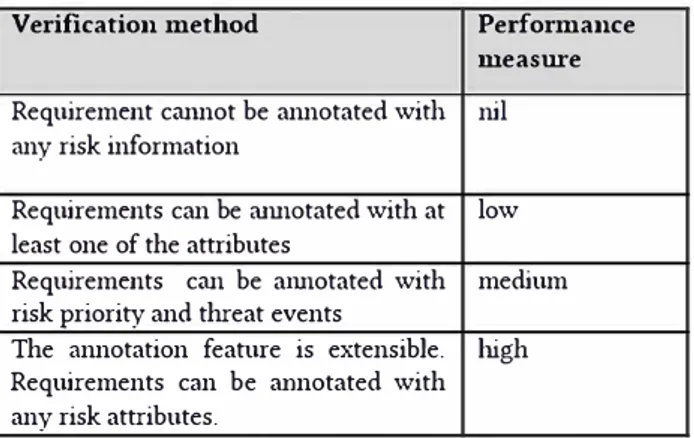
Figure
Documents relatifs
SecBPMN [5] (Secure BPMN) is a modeling language, based on Business Process Modelling and Notation (BPMN), which allows analysts to (i) model business pro- cesses with
Like diagnostic security information and knowledge, prescriptive aspects should be assignable to each security topic as easily and intuitively as possible, and
The other, called ArgueSecure, is a collaborative, browser-based version which allows for distributed risk analysis and security requirements elicitation sessions.. While the
BrainFist proposes a solution to this specific problem of document management by using metadata to maximize the potential use of content.. Furthermore, BrainFist is
Dan Slu ú anschi a tenu à garder la forme des noms propres homériques dans une forme la plus proche possible de l’original grec, en se situant sur ce point à l’opposé de Murnu
Quantification of BC migration defects in stage 10 dapc or dapc1 mutant MARCM mosaic egg chambers in which b-catenin/Arm levels are either lowered in the mutant cells by the use
Beckers, K., Faßbender, S., Heisel, M., K¨ uster, J.C., Schmidt, H.: Supporting the development and documentation of ISO 27001 information security management systems through
We are currently working on SecCo, which will be the socio-technical security mod- elling language for the EU-funded Aniketos project. Aniketos is about ensuring trust- worthiness