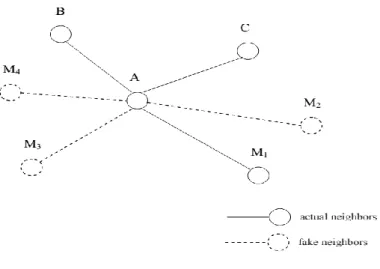
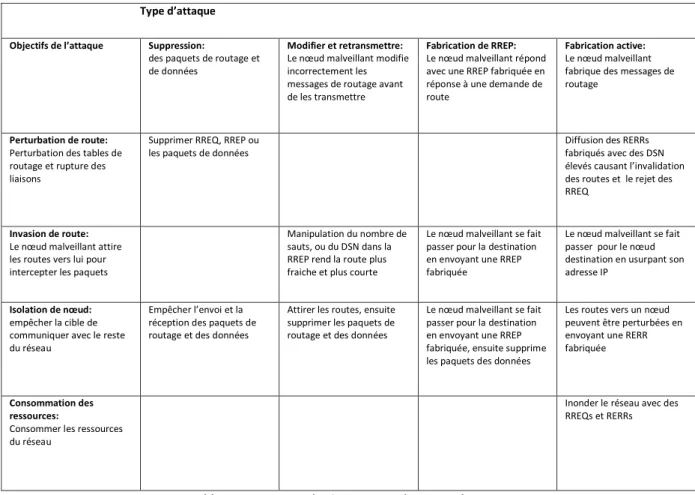
Détection d'intrusion et sécurisation du routage dans les réseaux Ad hoc
Texte intégral
Figure


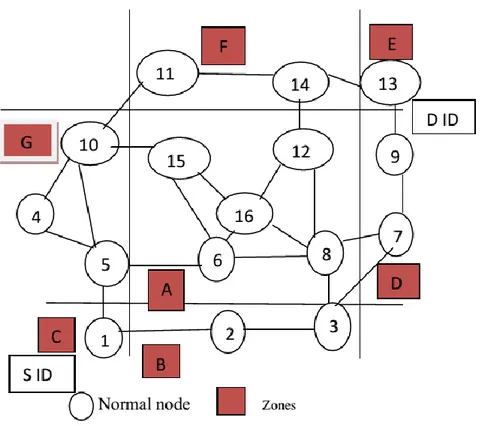
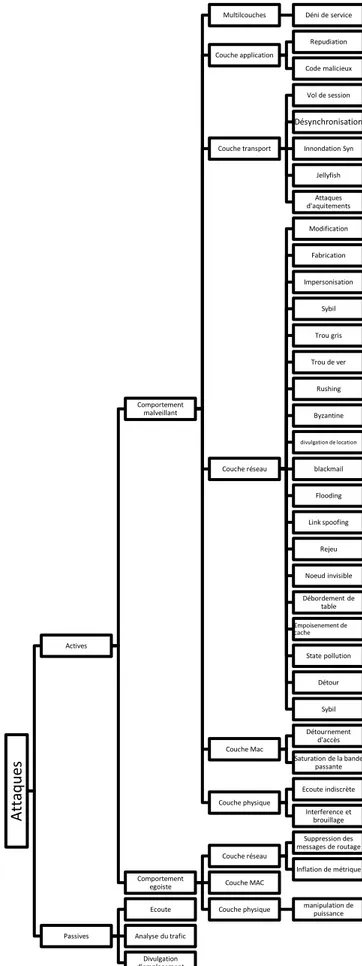
Outline
Documents relatifs
Jacques Meunier. Analyse spectrale de la lumière diffusée par les fluctuations thermiques d’un interface liquide. Etude de l’anhydride carbonique près du point critique. Dynamique
In the context of company specific environmental jolts that demands environmental engagements, this finding is coherent with the natural resource based view
Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of
Wolfmann, Cyclic code aspects of bent functions, in Finite Fields: Theory and Applications, AMS series ”Contemporary Mathematics” volume 518, 363-384, 2010.
des comptabilités complètes pour la période 1730 à 1756, des registres de correspondance active, les lettres reçues, presque sans lacune, de 1717 jusqu’à la fin,
In order to determine plausible miss costs, we reasoned as follows. The production server from which our trace was collected had an in-memory cache of 4 GB [12], i.e.
To determine whether there are differences in acid-induced neuronal activity between 25°C and 35°C, we activated ASICs by extracellular acidification from 7.4 to moderately acidic
The human rights of women include their right to have control over and decide freely and responsibly on matters related to their sexuality, including sexual and reproductive