Beyond a series of security nets:
applying STAMP & STPA to port security
The MIT Faculty has made this article openly available.
Please share
how this access benefits you. Your story matters.
Citation
Williams, Adam D. “Beyond a Series of Security Nets: Applying
STAMP & STPA to Port Security.” Journal of Transportation Security
8, no. 3–4 (November 17, 2015): 139–157.
As Published
http://dx.doi.org/10.1007/s12198-015-0161-y
Publisher
Springer US
Version
Author's final manuscript
Citable link
http://hdl.handle.net/1721.1/103805
Terms of Use
Article is made available in accordance with the publisher's
policy and may be subject to US copyright law. Please refer to the
publisher's site for terms of use.
1
Beyond a Series of Security Nets:
Applying STAMP & STPA to Port Security
Adam D. Williams
1Senior Systems Engineer
Sandia National Laboratories
2Albuquerque, NM
PhD Candidate, Engineering Systems Division
Massachusetts Institute of Technology
77 Massachusetts Avenue, Rm-33-408
Cambridge, MA
adwilli@mit.edu
505-264-5246
ABSTRACT (199 words)
Port security is an increasing concern given the significant role of ports in global commerce and today’s increasingly complex threat environment. Current approaches to port security mirror traditional models of accident causality – ‘a series of security nets’ based on component reliability and probabilistic assumptions. Traditional port security frameworks result in isolated and inconsistent improvement strategies. Recent work in engineered safety combines the ideas of hierarchy, emergence, control and communication into a new paradigm for understanding port security as an emergent complex system property. The ‘System-Theoretic Accident Model and Process (STAMP)’ is a new model of causality based on systems and control theory. The associated analysis process – System Theoretic Process Analysis (STPA) – identifies specific technical or procedural security requirements designed to work in coordination with (and be traceable to) overall port objectives. This process yields port security design
specifications that can mitigate (if not eliminate) port security vulnerabilities related to an emphasis on component reliability, lack of coordination between port security stakeholders or economic pressures endemic in the maritime industry. This article aims to demonstrate how STAMP’s broader view of causality and complexity can better address the dynamic and interactive behaviors of social, organizational and technical components of port security.
KEYWORDS: security, ports, port security, STAMP, STPA, systems theory, complex system
ACKNOWLEDGEMENTS
I would like to thank Dr. Nancy Leveson (MIT Professor of Aeronautics and Astronautics and Engineering
Systems), my PhD Committee Chair, for posing this important question as part of my Engineering Systems Division PhD general exam. I would also like to thank the rest of my PhD committee – Dr. John Carroll (MIT Professor of Behavioral and Policy Sciences and Engineering Systems) and Dr. Matthew Bunn (Harvard Professor of Practice) – for their guidance and insights. In addition, I thank Sandia National Laboratories for supporting my doctoral research into improving security of complex, socio-technical systems. I look forward to expanding the application of STAMP and STPA to security in this domain and others. Lastly, I want to thank the anonymous reviewer and editors for their insightful comments and helpful questions on my original manuscript. This research was funded by Sandia National Laboratories under its Doctoral Studies Program.
1
The views expressed herein are those of the author and do not reflect the official policy, position or recommendation of Sandia National Laboratories, the National Nuclear Security Administration, the Lockheed Martin Corporation, the U.S. Department of Energy or the U.S. Government.
2
SAND2015-7409 J. Unclassified, unlimited release. Sandia National Labratories is a multi-program laboratory managed and operated by Sandia Corporation, a wholly owned subsidiary of Lockheed Martin Corporation, for the U.S. Department of Energy’s National Nuclear Security Administration under contract DE-AC04-94AL85000
2
Total Word Count: 5012
I. INTRODUCTION
The range of threats – from using containers to smuggle weapons of mass destruction to attacking liquefied natural gas tankers to cyber-attacks that cripple port information systems – facing ports is only rivaled by the scale of the consequences resulting from a security incident. For example, Burns (2013) estimates the devastating economic losses from an attack on the Port of Los Angeles/Long Beach will approach half a billion dollars after just a week. In today’s increasingly complex threat environment, port security has undergone a fundamental shift from a pre-9/11 anti-crime to a post-9/11 anti-terrorism focus (U.S. Department of Homeland Security, 2005b). Current responses to improving security around ports include a Congressional mandate to scan 100% of all incoming cargo containers for nuclear or radiological material (Barnes, 2014), fusing intelligence gathering into risk management to increase ‘maritime domain awareness’ (U.S. Department of Homeland Security, 2005b), and voluntary policy agreements trading economic incentives for earlier and more comprehensive data collection of container contents (Frittelli, 2005; O’Connell, 2009).
Such attempts at enhancing port security may be insufficient or ineffective, as U.S. Secretary of Homeland Security Jeh Johnson describes the 100% container scanning mandate as ‘highly improbable, hugely expensive [and] not the best use of taxpayer resources to meet this country’s port and homeland security needs’ (Barnes, 2014). And, as Akhtar, et. al. (2010) argue, securing U.S. ports is a complex problem because it ‘is a particular challenge to predict the number and nature of future attacks since terrorists are adaptive to the security measures implemented’ (p. 183). The current paradigm for mitigating these port security complexities is a ‘series of security nets that provide layers of protection necessary to effectively manage security risks’ (U.S. Department of Homeland Security, 2005a, p. 3).
This article first provides a summary of relevant work in the area of port security analysis, including a discussion of related challenges and shortcomings. The next section introduces STAMP – a framework founded on a new
causality model that has been proven effective for evaluating system safety across technical domains – and argues its utility in evaluating port security. The primary aim of this article – a preliminary analysis that demonstrates
3
recommendations for improving port security. Lastly, this article will end with a discussion of relevant conclusions for evaluating and improving security at ports.II. LITERATURE REVIEW
Port security in the United States is governed by a series of laws (Coast Guard and Maritime Transportation Act, 2004, Intelligence Reform and Terrorism Prevention Act, 2004, Maritime Transportation Security Act, 2002) designed to identify insufficiencies in, define regulatory standards for and increase implementation of port security. In addition, the SAFE Port Act of 2006 introduced more stringent port personnel security expectations, established additional security tasks as part of normal port operations, expanded the concept of port security to include the international supply chain and codified many of the current port security programs (Security and Accountability for
Every (SAFE) Port Act, 2006). From these national laws comes the federal requirement to create (and regularly
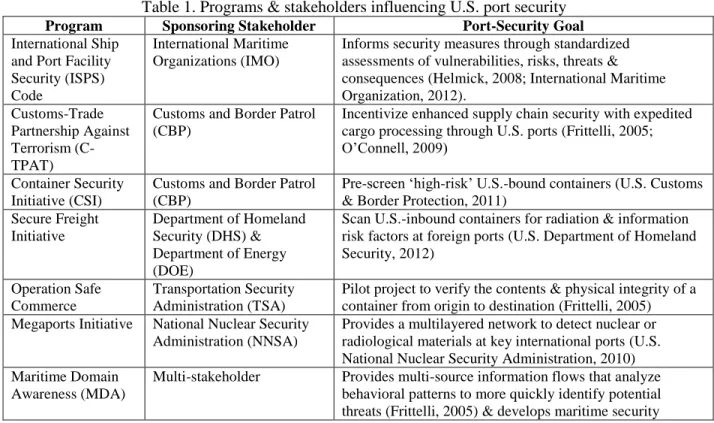
update) a National Strategy for Maritime Security (NSMS). The NSMS gives the objective of port security as using ‘layers of protection and defense in depth that effectively mitigates critical system security risks’ (U.S. Department of Homeland Security, 2005a, p. 3) to prevent terrorist, criminal or hostile acts on port-related populations or infrastructures. Additional programs for U.S. port security range from voluntary to bilateral governmental agreements (Table 1).
Table 1. Programs & stakeholders influencing U.S. port security
Program Sponsoring Stakeholder Port-Security Goal
International Ship and Port Facility Security (ISPS) Code
International Maritime Organizations (IMO)
Informs security measures through standardized assessments of vulnerabilities, risks, threats & consequences (Helmick, 2008; International Maritime Organization, 2012).
Customs-Trade Partnership Against Terrorism (C-TPAT)
Customs and Border Patrol (CBP)
Incentivize enhanced supply chain security with expedited cargo processing through U.S. ports (Frittelli, 2005; O’Connell, 2009)
Container Security Initiative (CSI)
Customs and Border Patrol (CBP)
Pre-screen ‘high-risk’ U.S.-bound containers (U.S. Customs & Border Protection, 2011)
Secure Freight Initiative Department of Homeland Security (DHS) & Department of Energy (DOE)
Scan U.S.-inbound containers for radiation & information risk factors at foreign ports (U.S. Department of Homeland Security, 2012)
Operation Safe Commerce
Transportation Security Administration (TSA)
Pilot project to verify the contents & physical integrity of a container from origin to destination (Frittelli, 2005) Megaports Initiative National Nuclear Security
Administration (NNSA)
Provides a multilayered network to detect nuclear or radiological materials at key international ports (U.S. National Nuclear Security Administration, 2010) Maritime Domain
Awareness (MDA)
Multi-stakeholder Provides multi-source information flows that analyze behavioral patterns to more quickly identify potential threats (Frittelli, 2005) & develops maritime security
4
Analytical approaches to port security are similarly varied. A risk management approach seeks to minimize the product of the probability of attack (e.g., threat), the conditional probability of a successful attack (e.g.,vulnerability) and the expected value of losses (e.g., consequences) (Akhtar, Bjørnskau, & Veisten, 2010; Ghafoori & Altiok, 2012). Another risk-management based approach uses decision-tree analysis and heuristic, subjective risk and consequence estimates to graphically compare expected values of resilience strategies for various natural, technological or human disruption (Mansouri, Nilchiani, & Mostashari, 2010). Assuming accurate knowledge of income, cost of security and probability of adversaries exploiting a port to (trans)ship dangerous cargo, (Gkonis & Psaraftis, 2010) use game theory to optimize assumed rational decisions to purchase equipment that enables 100% scanning of cargo. Akhtar, et al. (2010) use Monte Carlo simulations based on subjective assessments of uncertainty distributions for key variables (e.g., the frequency of adversary attack) to assess the benefit and risk reduction of security measures implemented at Norwegian seaports. Burns (2013) offers econometric models to optimally allocate security resources across supply chains composed of an ever widening disparity of socio-economically successful countries. It seems, however, that these initiatives have not significantly improved port security ‘to fundamentally reduce the vulnerability of the cargo containers as a means of terrorism’ (Stephen Flynn as quoted in Frittelli, 2005, p. 15).
The methods described above also lack discussion of social and political influences on port security. For example, Congressional mandates and economic pressures yield scenarios wherein delays associated with cargo inspection become so unacceptable that shipping companies employ tactics for evading or bypassing such security protocols (Chatterjee, 2003). Post-9/11 traditional approaches to port security tend to fixate on protecting against external threats (e.g., terrorists) at the expense of identifying ‘potentially serious flaws in the [port] system’ (O’Connell, 2009, p. 145) itself or ensuring information flows across interagency interfaces to decision-makers (U.S. Department of Homeland Security, 2005a). Inconsistent and disparate port security metrics (‘overall vulnerability index’ (Chatterjee, 2003) or risk reduction (Akhtar et al., 2010), for example) lead to additional confusion between espoused national security standards and site-specific security implementation (Frittelli, 2005). Port security is also hampered by assuming the U.S. Coast Guard can effectively implement large scale anti-terrorist programs that fall well outside of its legacy of preventing drug smuggling and cargo theft (Chatterjee, 2003). Lastly, Frittelli (2005)
5
describes tension between those who view port security as a national concern and federal budget issue (e.g., ports) and those who view port security as a facility concern and a port budget issue (e.g., federal stakeholders).Put into this context, there are drawbacks to current approaches to port security. Where defense-in-depth concepts provide mathematically tractable analysis, the underlying assumptions are untenable. Such methods assume rational adversaries will attack along the path of least resistance and that security system optimization can be achieved (Garcia, 2007; Ghafoori & Altiok, 2012). Security is thus reduced to a set of probabilities that can be compared to show improvements between base and upgraded system cases (Akhtar et al., 2010). Designing security on such a ‘Swiss Cheese’ model (Reason, 1997) also represents adversary actions as a set of randomly occurring, independent processes at each layer of security nets. But the 9/11 or ‘26/11’ terrorist attacks in New York and Mumbai
demonstrate adversary actions to disrupt port operations are likely to be neither random nor independent. Current methods inadequately account for the daily practices and operations that can degrade port security implementation – even arguing that ‘it is almost impossible to assess the organizational factors independently’ (Mansouri et al., 2010, p. 1127). Lastly, these approaches frame port security as a reaction of components to an assumed non-zero
probability of external stimuli. The absence or low frequency of regular adversary action can lead to a negative cycle of security practice implementation fatigue in operational personnel and threat escalation in security personnel at ports (Sagan, 2004).
These traditional port security lenses result in such improvement strategies as enhanced adherence to security regulations (e.g., compliance); increased flexibility and resilience in technological components to mitigate disruption(e.g., redundancy); and improved training (e.g., certification). These isolated measures do not consider security as an ‘organizational problem, where vulnerabilities are created by the design and processes inherent to the [port] itself’ (Gould, Macharis, & Haasis, 2010, p. 293). Additionally, considering ports as part of a ‘maritime transportation system’ allows stakeholders to more easily identify and reduce natural, technological, organizational and human disruptions to operations (Mansouri, Sauser, & Boardman, 2009). What is needed is a port security framework that identifies (and helps mitigate) both exogenous and endogenous pathways for intentional port disruptions to prevent quickly escalating economic impacts (and, in some cases, harm to or loss of life).
6
III. METHODOLOGY
Reframing port security in terms of systems, control and organization theories can alleviate these shortcomings. Systems theory introduces two concepts germane for port security: hierarchy and emergence. Hierarchy refers to the separations of and connections between levels of complexity within a system. Emergence refers to the phenomenon where behaviors at a given level of complexity are inexplicable by the behavior of its components. Thus, emergent properties act as constraints on the actions of components at the lower levels (Leveson, 2012). Hierarchy and emergence help explain the fact that a system can have a ‘secure’ component, but itself not be secure (e.g., a ‘smart container’ protects the goods inside it, but itself can still be stolen). Taken together they suggest that port security is dependent on enforcing constraints on security components to guide emergent behaviors within a hierarchical system away from vulnerable states.
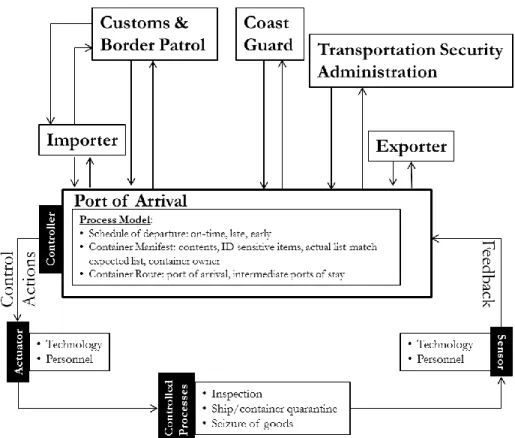
Likewise, control theory uses control loops to describe the communication of pertinent information between components within and across levels in a hierarchy (Leveson, 2012). A typical loop follows a control action from a controller (the initiator) to the actuators (the controlled variables) to the controlled processes (the components or systems that need to change) to the sensors (the measured variables) and back to the controller. Control and communication suggest that security results from how well security-related control actions navigate between the decision-maker (e.g., controller) and the implementer (e.g., controlled process) – both within the same and across different hierarchical system levels.
Lastly, organization theory can help overcome a lacking discussion of social influences on port security noted in current approaches (e.g., Gould et al., 2010; Helmick, 2008). Organization theory suggests structure emerges from implicit assumptions and perceptions that drive recurrent, daily employee behaviors (Giddens, 1984; Orlikowski, 2000; Schein, 1996). Restated, organizations are structured by recurring operations at the individual level that work toward (or against) collective level objectives – suggesting that social influences on security can also be represented in terms of emergence and hierarchy. Port security, then, is a system property that emerges from communicating control actions among a hierarchical system consisting of social and technical components. Representing port operations in terms of emergence, hierarchy, control, communication and daily actions allows port security to be
7
analyzed as a system-level property shaped by social and organizational influences not accounted for in a series of security nets.Recent work in the discipline of engineered safety combines systems, control and organization theory into a new paradigm for understanding security at ports. This new security framework is based on System-Theoretic Accident Model and Process (STAMP) which provides a new causality model for analyzing (and designing against) safety accidents, especially those involving complex, socio-technical systems (Leveson, 2012). STAMP defines a system as interrelated components that use information and feedback loops to maintain dynamic equilibrium through internal and external disturbances to achieve its objective. Safety is then seen as an emergent system property defined as adequately enforcing design constraints through control actions to avoid unacceptable losses. Such losses can result from flawed interactions between physical components, engineering activities, operational mission, organizational structures and social factors (Leveson et al., 2006). Unacceptable losses occur when the system enters a hazardous state and experiences a worst-case scenario (Leveson, 2012).
Rather than focus on estimating the risk of such external scenarios (e.g., Akhtar et al., 2010; Ghafoori & Altiok, 2012), STAMP emphasizes elements of system design that can control migration of the system into hazardous states. Security then becomes eliminating, minimizing or mitigating migration of the system into vulnerable states – shifting the analytical paradigm from preventing failures to enforcing security control actions (Williams, 2013; Young & Leveson, 2013, 2014). More specifically, port security is recast as a control problem to surmount ‘component failures [e.g., inoperable assessment cameras or modified and unannounced security protocols], external disturbances [e.g., external adversary attack or reduction of security related budget/resources], or dysfunctional interactions among system components [e.g., resistance to adhere to security protocols or competing
objectives between security and operational management]’ (Leveson et al., 2006, p. 20).3
Moving beyond concentric layers of security to deter, prevent and respond to terrorist threats (U.S. Department of Homeland Security, 2005b), STAMP analyzes port security as the avoidance of vulnerabilities in terms of three
8
fundamental concepts: control actions, hierarchical levels of control and process models. Control actions serve as constraints by which higher levels within a port influence activities at lower levels. The presence (or lack) of security at one level imposes constraints on the behaviors of the components at a lower level to ensure that the port avoids vulnerable states. Hierarchical structures help visualize how security control actions are communicated via reference and feedback channels between levels in a system. Process models (e.g., ‘mental maps’ or digital abstractions) contain knowledge of the current state of port operations and the processes that can change this state. This model is used by a controller (either human or automation) to determine what and when control actions need to be issued (Leveson, 2012; Leveson et al., 2006). By extension, STAMP deems port security as the timelycommunication of control actions across hierarchical structures composed of controllers with consistent process models to ensure avoid migrating into vulnerable system states.
In summary, STAMP combines hierarchy, emergence, control, communications and daily actions to reframe port security as an emergent system property. Security events are seen to result from interactions between system components (e.g., security technologies and facility operators) that violate security control actions (e.g., ignoring an increased number of alarms from the newly installed intrusion detection system). This analytical paradigm shift away from ‘risk-based methodologies’ (e.g., Maritime Transportation Security Act, 2002) allows analysis and design to eliminate, minimize or reduce more of the dynamic complexities present in today’s port security
environment. The next section overviews a preliminary analysis demonstrating the application of a STAMP-based approach to port security.
IV. ANALYSIS
Though similar in name to other systems approaches (e.g., Gkonis & Psaraftis, 2010; Mansouri, 2009; U.S. Department of Homeland Security, 2005a), STAMP incorporates a broader definition of security, emphasizes security control actions over probabilities and treats security as inextricably linked to overall system objectives. Security then moves away from linear cause and effect thinking toward enforcing requirements on port operations that influence system objectives. For example, the mission of a generic port could be stated as facilitating the movement of commercial goods with the lowest financial cost and minimum risk to people or property. The literature (Frittelli, 2005; Gould et al., 2010) suggests that unacceptable losses for ports include containers or
9
transport used for criminal or terrorist purposes; inefficiencies in supply chain from government regulations or initiatives; rising costs from disrupted flow of goods or services; seizure of ships or ports for hostages; and, use of ships as vectors for causing damage to critical infrastructure. STAMP restates these as the unacceptable, system losses shown in Table 2.Table 2. STAMP-based description of system losses for port security
Losses Descriptions
L1 Human serious injury or loss of life L2 Significant damage to the port system
infrastructure L3 Significant loss of revenue
STAMP identifies high level losses as resulting from safety hazards (Leveson, 2012), but Gould, et. al. (2010, p. 291) suggest that security vulnerabilities for a port also ‘refer to weaknesses…that make it susceptible to loss due to an undesired event.’ Restated in STAMP terms, a port security loss occurs with the interaction of a vulnerable state and a worst case set of scenarios – including adversary actions. As such, the STAMP causality model translates high level losses into related vulnerable system states, as shown below in Table 3.
Table 3. Representative set of STAMP vulnerable states & related unacceptable losses for port security
Vulnerable States Related Losses
(V1) Unauthorized individuals accessing port system infrastructure
L1, L2, L3 (V2) Unverified cargo sitting inside a
shipping container
L1, L2, L3 (V3) Uncoordinated implementation of
inspection procedures
L1, L2, L3
If the port system migrates into any of these vulnerable system states, one additional external event or adversary action could lead to a high level system loss. For example, if an unauthorized individual armed with explosives accessed the docks of a given port, the port could experience a loss. If this same individual with explosives was not allowed to access the docks the system would be less likely to experience a loss.
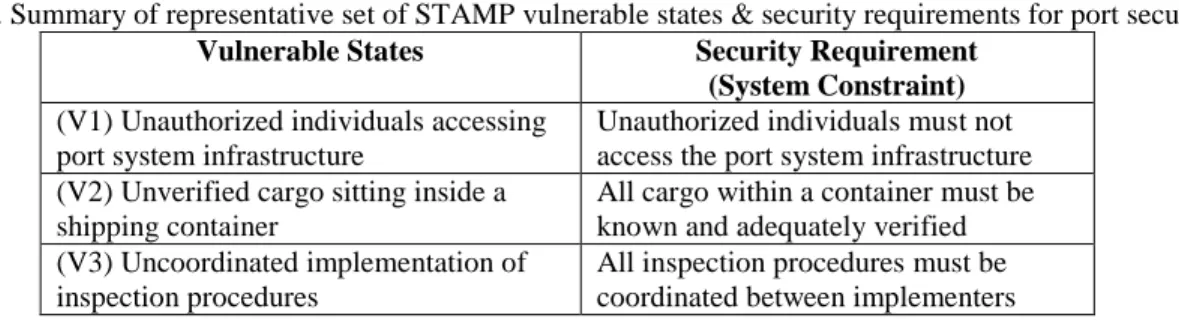
Per systems, control and organization theory, these vulnerable states help identify requirements for the behavior of the system necessary to avoid the identified losses. For STAMP, these security requirements are more than component reliability specifications and act as physical and procedural constraints (Table 4) on port system design
10
and operations to avoid the port migrating into vulnerable states. These high level security constraints become the benchmark for weighing the benefit of any system structure or operational change on security.Table 4. Summary of representative set of STAMP vulnerable states & security requirements for port security.
Vulnerable States Security Requirement (System Constraint)
(V1) Unauthorized individuals accessing port system infrastructure
Unauthorized individuals must not access the port system infrastructure (V2) Unverified cargo sitting inside a
shipping container
All cargo within a container must be known and adequately verified (V3) Uncoordinated implementation of
inspection procedures
All inspection procedures must be coordinated between implementers
To implement the derived security requirements above, STAMP requires an understanding of the security responsibilities of various stakeholders. The lack of a singular federal entity responsible for port operations (let alone for port security) results in a complicated and convoluted network of relationships between port, local, state and federal entities. (NOTE: Details on interactions between local, state and federal stakeholders were not included in order to keep this control structure as generic as possible – and because such data approaches the realm of sensitive information.) More specifically for port security, ‘a typical cargo import into the U.S. requires 30 forms and applications, to be handled by a minimum of 25 law enforcement, commercial and financial entities, such as the port authorities, customs officials, U.S. Coast Guard/Homeland Security, cargo carriers (show owners, truckers), freight forwarders, warehouses and other entities in the logistics chain’ (Burns, 2013, 332-333). As such generic security-related responsibilities for port-related entities are described in Table 5 below.
11
Table 5. List of stakeholders & respective responsibilities related to port security.Port Security-Related
Stakeholder Port Security-Related Responsibilities
International Maritime Organization
Maintains the International Ship and Port Facility Security (ISPS) Code (United Nations stakeholder)
U.S. Congress Sets port security related policy & legislation for the U.S. U.S. Department of
Transportation
Lobbies, funds & sets regulations for the Maritime Administration U.S. Department of
Homeland Security
Lobbies, funds & sets regulations/operations for the U.S. Customs & Border Patrol, Coast Guard and Transportation Security Administration
U.S. Customs & Border Patrol
Inspects containers & ships while in port; checks crew and ship passenger lists
U.S. Coast Guard
Lead agency for maritime security that inspects ships before they arrive in port (e.g., in U.S. territorial waters); protects Naval ships while in port, credentials mariners & approves security plans
U.S. Transportation Security Administration
Provides crew credentialing, background investigations & advanced container/ship screening procedures (only where the Transportation Worker Identification Credential program exists)
Maritime Administration Provides security planning guides, ‘Maritime Security Reports’ and security training standards & curricula (civilian stakeholder)
Importer Declares goods/containers received and maintains transparent shipping records Port of arrival Reports any ship/container of concern and provides resources (e.g., time) for above
agencies to perform any necessary inspections
Port of departure Reports any ship/container of concern and provides resources (e.g., time) for above agencies to perform any necessary inspections
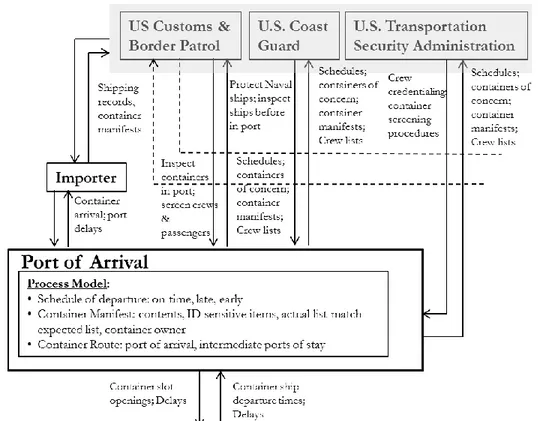
Exporter Declares goods/containers shipped and maintains transparent shipping records STAMP illustrates this litany of physical and procedural port security-related responsibilities in systems theory terms with a hierarchical control structure (Leveson, 2012). Fig. 1 partially (and Appendix A more fully) illustrates the high level control structure derived with STAMP for port security and includes descriptions of communications flowing between system levels. For security related responsibilities of port security stakeholders, decisions are based on the information (illustrated by solid lines in Fig. 1) that updates the current understanding of each process model variable. The process model variables of concern for port security are fairly consistent between all
stakeholders, and thus were only listed for the ports of arrival and departure (see Appendix A). The dashed lines represent the desire (per the Container Security Initiative) to extend a similar set of security responsibilities for the U.S. Customs & Border Patrol to ports of departure for containers destined for the United States.
[Fig. 1 Here]
STAMP’s related analysis technique, the System-Theoretic Process Analysis (STPA), expands the representation of Fig. 1 by abstracting real port security operations into functional control loops (Leveson, 2012). Depicting port security operations as actual, versus intended, practices is similar to structuration theory that argues organizational
12
structure is not derived from formal charts but emerges from recurrent daily action (Giddens, 1984; Orlikowski, 2000). Fig. 2, below, illustrates such a functional high level control loop for port security.[Fig. 2 Here]
Within the constraints provided by higher levels in a port security control structure (Appendix A) and loop (Fig. 2), a controller (e.g., the port of arrival) issues a security control action – based on its current process model – to an actuator (e.g., security-related technology or personnel). This actuator implements a controlled process (e.g., inspection or seizure of goods) based on the control action. The completion of this controlled process is registered by a sensor (e.g., security-related technology or personnel). This sensor information becomes feedback that updates the controller’s process model regarding the original control action. STAMP and STPA use the control loop to derive security control actions (Table 6) designed to prevent migration into vulnerable system states. For example, proper enforcement of a given security control action (e.g., ‘count the items in a container for verification against the cargo manifest list’) helps the system not violate the related security constraint (e.g., ‘all cargo within a container must be known and adequately verified’) and avoid the vulnerable state (e.g., ‘unverified cargo sitting inside a shipping container’) that could lead to system loss (e.g., ‘human serious injury or loss of life’).
Table 6. Representative set of vulnerable states, system constraints & example security control action for port security
Vulnerable States Security Requirement (System Constraint)
Example Security Control Action
(V1) Unauthorized individuals accessing to port system infrastructure
Unauthorized individuals must not access the port system
infrastructure
Check the access credential of any individual entering the container security area
(V2) Unverified cargo sitting inside a shipping container
All cargo within a container must be known and adequately verified
Count the items in a container for
verification against the cargo manifest list (V3) Uncoordinated
implementation of inspection procedures
All inspection procedures must be coordinated between
implementers
Coast Guard communicates completion of a successful inspection to Customs & Border Patrol
From here, STPA consists of two major steps (Leveson, 2012). In STPA step one each security control action is analyzed to identify possible violations that lead to vulnerable system states. Such vulnerable system states result when incorrect security control actions are issued; required security control actions are not issued; security control actions are provided too early or late; or security control actions are stopped too soon (or too late) to be adequately enforced. Table 7 below provides an example of STPA step one for the port security control actions identified above.
13
Table 7. Representative set of STPA Step 1 - representative security control action violations for port securityExample Security Control Actions
Command Needed & Not Provided
Command Not Needed & Provided
Command Given Too Early/Late or in Wrong Order Command Stopped Too Soon/Engaged Too Long
Check the access credential of any individual entering the container security area *Unauthorized individual accesses container storage area [V1, V3] *Already credentialed person is re-checked (e.g., different agency or badge) [V3] *Check credential after individual in container storage area (e.g., too late/wrong order) [V1, V3]
*Not Applicable (a binary command)
Count the items in a container for verification against the cargo manifest list
*Unknown items sitting in a
container in the port infrastructure [V2]
*Known items being counted introduces unneeded/unjustified delay into the system [L3]
*Counting before having the manifest list (e.g., too early/wrong order) [V2, V3]
*Counting after container in port (e.g., too late/wrong order) [V2, V3]
*Stopping the count before fully checked (e.g., stopping too soon) [V2]
*Taking so much time to complete the count that other containers bypass the count (e.g., engaged too long) [V2, V3] Coast Guard communicates completion of a successful inspection to Customs & Border Patrol
*Coast Guard does not communicate their inspection, therefore both stakeholders inspect the container or ship [V3, L3]
* Coast Guard does communicate their inspection, Border Patrol allows other/similar container or ship needing inspection to continue without it [V2, V3]
*If Coast Guard communicated their inspection too late, both stakeholders inspect ship or container [V2, V3]
*Not Applicable (a binary command)
Fig. 3 below shows where and how security control action violations disrupt the control loop and the process model of the controller.
[Fig. 3 Here]
STPA step two then derives specific scenarios that could cause the theorized security violations (Table 7) to occur. For security applications, these scenarios include identifying possible environmental events and specific adversary actions that combine with vulnerable system states to cause a loss (Leveson, 2012; Williams, 2013; Young & Leveson, 2014). The security literature suggests that adversaries rely on three general strategies (Garcia, 2007): stealth, deceit and force. Stealth actions rely on the adversary’s ability to violate security control actions without being detected – blackmailing a container inspector to forge an inspection, for example. Deceit actions require the adversary to violate security control actions by fraudulently representing illicit persons, goods or actions as
legitimate (e.g., ‘hiding in plain sight’) – using a counterfeit identification badge or filing a falsified cargo manifest, for example. Force actions rely on the use of an advantage or strength to overwhelm a security force or facility –
14
using a cement truck full of explosives to drive through fences and gain access to the container storage area, for example. Table 8 below offers some examples of how each of these strategies can lead to security control action violations.Table 8. Representative set of STPA Step 2 - adversary actions for port security
Security Control Action Violations
Adversary Action: Stealth Adversary Action: Deceit
Adversary Action: Force
*Unauthorized individual accesses container storage area [V1, V3]
*Cutting hole in a fence without triggering any related alarm to access the container storage area
*Using a forged badge to access the container storage area
*Using a vehicle to drive through/over barriers to the container storage area *Known items being
recounted introduces unneeded/unjustified delay into the system [L3]
*Remotely accessing the inspection list and adding containers that do not need to be counted
*Switching labels between a container of concern and a container that does not need the extra count
*Holding inspectors at gun point until additional (unneeded) counts are completed *Both Coast Guard and
Customs & Border Patrol inspect the container or ship [V3, L3]
* Jam the communications channels between Coast Guard and Customs & Border Patrol causing both to inspect the container
assuming the other has/will not
*Spoof the communications channels between Coast Guard and Customs & Border Patrol indicating the other has/will not inspect the cargo or ship
*This strategy is not likely to be employed for this security control action violation
These adversary actions can be mapped onto the functional control loop to illustrate how a specific, scenario-generated adversary action can disrupt the system’s ability to enforce its security control actions, as shown in Fig. 4 below.
[Fig. 4 Here]
Whereas traditional approaches to port security (Akhtar et al., 2010; Burns, 2013; Ghafoori & Altiok, 2012; Gkonis & Psaraftis, 2010) seek to estimate the probabilities of adversary actions (like those listed in Table 7), STPA views adversary actions in the context of security control actions. Since STPA derives adversary actions (e.g., using a forged badge to access the container storage area) as subsets of security control action violations (e.g., unauthorized individual accesses container storage area), eliminating or minimizing such violations by enforcing security control actions (e.g., check the access credential of any individual entering the container security area) reduces the migration of a port into a vulnerable state (e.g., unauthorized individuals accessing port system infrastructure) and decreases the occurrence of unacceptable losses (e.g., human serious injury or loss of life). This section demonstrated how STAMP and STPA are applied to port security and introduces how this analysis can produce useful
15
V. RESULTS & RECOMMENDATIONS
STAMP and STPA provide a rigorous process that orients port security toward identifying component (technical or procedural), systemic and interactive security control action violations. For example, a policy of counting items against a manifest is replaced by a systemic focus on verifying container item counts to eliminate the STPA-derived security control action violation ‘counting after container in port’ (from Table 7). Similarly, the security enhancing capabilities of radiation or thermal scanning technologies are tempered if communications between the U.S. Coast Guard (who inspects ships) and U.S. Customs & Border Patrol (who inspects containers) are unclear or conflict. STPA identifies how establishing communication protocols between relevant port security stakeholders can
eliminate (or at least reduce) the security control action violation ‘neither Coast Guard nor Customs & Border Patrol inspect the container or ship’ (from Table 7). While a more detailed analysis will provide additional security control actions for a specific port, this preliminary analysis is a demonstration of successfully applying STAMP and STPA to port security. Furthermore, even this preliminary and high level STAMP and STPA analysis offers a set of recommendations to improve port security not previously captured in the literature.
First, the emphasis from expanding the concentric layers of security around ports should be refocused toward identifying controllable procedures to eliminate security control action violations. For example, rather than adding more inspection points during the journey of a given container (in order to offset low success rates of individual inspections) design an inspection process that is systematic and dynamic. Such an inspection process should be escalatory, with different leading indicators (e.g., threshold weight mismatches, unexpected gamma radiation detected or inexplicable thermal signatures) informed by STPA Step 1 violations (Table 7) resulting in increased levels of inspection.
Second, STPA provides an analytical framework for supporting security experts who believe ‘that security be “embedded” into everyday business practices’ (Frittelli, 2005, p. 21). This analysis suggests the role of humans in port security should be abstracted as hierarchical (functional) control structures in contrast to current approaches that reduce the role of humans to (estimated) probabilities related to the successful completion of security procedures. Figs 2-4 and Tables 5-7 suggest that port security emerges from implementing security control actions – ‘check the
16
access credential of any individual entering the container security area (Table 6)’, for example – in the recurrent work practices of port facility employees.Third, the focal point of port security should not be specific initiatives like trading expedited service at a U.S. port of arrival for increased transparency on cargo manifest information from international exporters. Such initiatives are problematic given the inability of ports to control the level of detail provided by and the assumed accuracy of the exporter. STAMP argues that security emerges from enforcing control actions within the port, not from
incentivizing external influences to reduce port vulnerability. More specifically, STPA (Table 7) suggests that port security is improved by funding a systematic, robust process for matching container item counts to manifest lists before containers are in port and not just funding more comprehensive exporter veracity programs (e.g., C-TPAT). Rather than sponsoring the assumed transparency of an outside actor, STPA provides a framework that identifies how resources can be funneled into reducing the potential for security control action violations (Table 7) that a less-than-forthright exporter might cause.
Fourth, STPA’s functional control structure (Appendix A) helps overcome the inherent port security deficiencies that exist in the absence of a coordinated regulatory body. Current approaches can help increase the efficiency for each stakeholder’s area of responsibility (Table 2), but there is little to no consideration of (or mitigation for) interaction effects. In contrast, STPA identifies security requirements that can be implemented (e.g., establishing a specific Coast Guard communication protocol of a successful ship inspection [from Table 4]) to deconflict and minimize the vulnerabilities resulting from such problematic interactions (e.g., the U.S. Customs & Border Patrol duplicating this cargo inspection).
Fifth, current approaches to port security are hamstrung by economic pressures exerted on the port system by relevant stakeholders. STPA clearly identifies revenue loss as an unacceptable security loss for the system and illustrates how economic pressures influence security via the functional control structure. Rather than being an obstacle to funding or justification for not adhering to security protocols, preventing revenue loss and stakeholder economic pressures become parameters fundamental for designing security constraints on the behavior of the port system.
17
VI. DISCUSSION & CONCLUSIONS
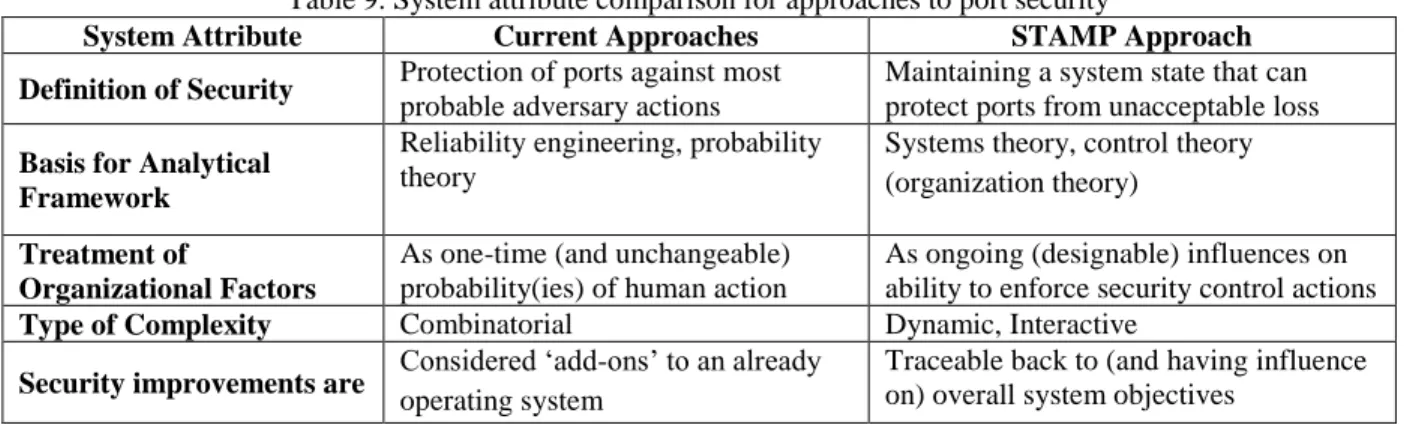
The primary contribution of this article is a demonstration of how to apply STAMP and STPA to port security. Current approaches to port security rely on ‘defense-in-depth,’ concentric layers of port security measures and the logic that placing even ‘weak’ layers in series increases the cumulative probability of stopping a threat or mitigating a specific vulnerability. Invoking probability theory (e.g., namely the independence and randomness of events), this ‘Swiss Cheese’ model of security suggests that each security layer can have vulnerabilities as long as they do not present a path through all security measures (Reason, 1997). CSI, C-TPAT, SFI, MDA and Megaports are results of this logic of extending the concentric layers of protection around ports. In contrast, STAMP models security as adherence to control actions and STPA provides a rigorous process to identify – and design against – potential violations (e.g., vulnerable states) to maintain secure port operations. This preliminary analysis demonstrates how STAMP’s broader view of causality and complexity better addresses the dynamic and interactive behaviors of social, organizational and technical components of port security lacking in the current literature. Unlike other approaches, in STAMP and STPA security is an emergent complex, sociotechnical system property traceable to overarching port objectives. Table 9 below summarizes the comparison between STAMP and current approaches to port security.
Table 9. System attribute comparison for approaches to port security
System Attribute Current Approaches STAMP Approach Definition of Security Protection of ports against most
probable adversary actions
Maintaining a system state that can protect ports from unacceptable loss
Basis for Analytical Framework
Reliability engineering, probability theory
Systems theory, control theory (organization theory)
Treatment of
Organizational Factors
As one-time (and unchangeable) probability(ies) of human action
As ongoing (designable) influences on ability to enforce security control actions
Type of Complexity Combinatorial Dynamic, Interactive
Security improvements are Considered ‘add-ons’ to an already
operating system
Traceable back to (and having influence on) overall system objectives
This research introduces a new logical argument that can result in a paradigm shift in port security away from preventing failures (what a facility cannot control) and toward enforcing security control actions (what a facility can control). Though preliminary in nature, the limitations of this analysis inform the direction of future port security
18
research. Generalizability of these results can be expanded by comparison against security incidents at a specific port or across ports. Additional fidelity in how port security is implemented (e.g., a more detailed hierarchical control structure) and how port security-related decisions are made (e.g., more detailed security control loops) is also needed. Lastly, a better understanding of how ‘security’ is defined by various port employees (e.g., their process models) will enhance the effectiveness of this preliminary STAMP and STPA analysis.Maritime security expert Dr. Stephen Flynn asserts a need to rethink port security because the current set of approaches ‘falls short in providing a way to weigh the relative value of the many security initiatives advanced by the US government since 9/11…[they] simply [outline] all the initiatives and [assert] that they represent a
comprehensive strategy’ (Helmick, 2008, p. 20). STAMP and STPA provide a mechanism for such a comprehensive strategy. By invoking system, control and organizational theory, security is redefined as an emergent complex system property at the intersection of security technology, organizational influences, international maritime statutes and economic pressures. More specifically, the previous section illustrates how STAMP and STPA can better address the dynamic, socio-technical complexity of port security in the 21st century.
19
VIII. APPENDIX A
20
IX. REFERENCES
Akhtar, J., Bjørnskau, T., & Veisten, K. (2010). Assessing security measures reducing terrorist risk: inverse ex post cost-benefit and cost-effectiveness analyses of Norwegian airports and seaports. Journal of Transportation
Security, 3(3), 179–195.
Barnes, D. (2014). DHS Shifts Nuclear-Screening Focus to “High-Risk” Cargo. Retrieved June 13, 2014, from http://www.nti.org/gsn/article/dhs-shifts-nuclear-screening-focus-high-risk-cargo/
Burns, M. G. (2013). Estimating the impact of maritime security: financial tradeoffs between security and efficiency. Journal of Transportation Security, 6(4), 329–338.
Chatterjee, A. (2003). An Overview of Security Issues Involving Marine Containers and Ports. In Proceedings of the
82nd Annuial Meeting of Transportation Research Board. Washington, D.C.
Coast Guard and Maritime Transportation Act (2004). Public Law Number 108-293, 118 Stat. 1028.
Frittelli, J. (2005). Port and Maritime Security: Background and Issues for Congress. CRS Report for Congress,
RL31733. Washington, D.C.
Garcia, M. L. (2007). Design and Evaluation of Physical Protection Systems (Second, p. 370). Boston: Butterworth-Heinemann.
Ghafoori, A., & Altiok, T. (2012). A mixed integer programming framework for sonar placement to mitigate maritime security risk. Journal of Transportation Security, 5(4), 253–276.
Giddens, A. (1984). The Constitution of Society: Outline of the Theory of Structuration (p. 438). Cambridge, UK: Polity Press.
Gkonis, K. G., & Psaraftis, H. N. (2010). Container transportation as an interdependent security problem. Journal of
Transportation Security, 3(4), 197–211.
Gould, J. E., Macharis, C., & Haasis, H.-D. (2010). Emergence of security in supply chain management literature.
Journal of Transportation Security, 3(4), 287–302.
Helmick, J. S. (2008). Port and maritime security: A research perspective. Journal of Transportation Security, 1(1), 15–28.
Intelligence Reform and Terrorism Prevention Act (2004). Public Law Number 108-458, 118 Stat. 3638.
International Maritime Organization. (2012). Guide to Maritime Security and the ISPS Code (2012th ed.). London: IMO Publishing.
Leveson, N. (2012). Engineering a Safer World: Systems Thinking Applied to Safety. Cambridge, MA: MIT Press. Leveson, N., Dulac, N., Zipkin, D., Cutcher-gershenfeld, J., Carroll, J., & Barrett, B. (2006). Engineering Resilience
into Safety-Critical Systems. In E. Hollnagel, N. Leveson, & D. R. Woods (Eds.), Engineering Resilience:
Concepts and Precepts (pp. 1–22). Hampshire, England: Ashgate Publishing, Ltd.
Mansouri, M., Nilchiani, R., & Mostashari, A. (2010). A policy making framework for resilient port infrastructure systems. Marine Policy, 34(6), 1125–1134.
21
Mansouri, M., Sauser, B., & Boardman, J. (2009). Applications of systems thinking for resilience study in maritimetransportation system of systems. In 3rd Annual IEEE International Systems Conference. Maritime Transportation Security Act (2002). Public Law Number 107-295, 116 Stat. 2064. O’Connell, J. (2009). C-TPAT: major challenges. Journal of Transportation Security, 2, 137–147.
Orlikowski, W. J. (2000). Using Technology and Constituting Structures: A Practice Lens for Studying Technology in Organizations. Organization Science, 11(4), 404–428.
Reason, J. T. (1997). Managing the Risks of Organizational Accidents. Ashgate Publishing, Ltd.
Sagan, S. (2004). The Problem of Redundancy Problem: Why More Nuclear Security Forces May Produce Less Nuclear Security†. Risk Analysis, 24(4), 935–946.
Schein, E. H. (1996). Culture: The Missing Concept in Organization Studies. Administrative Science Quarterly,
41(2), 229.
Security and Accountability for Every (SAFE) Port Act (2006). Public Law Number 109-347, 120 Stat. 1884. U.S. Customs & Border Protection. (2011). Container Security Initiative: In Summary. Washington, D.C. U.S. Department of Homeland Security. (2005a). Maritime Transportation System Security Recommendations for
the National Strategy for Maritime Security.
U.S. Department of Homeland Security. (2005b). The National Strategy for Maritime Security. Washington, D.C. U.S. Department of Homeland Security. (2012). Secure Freight Initiative. Retrieved August 12, 2014, from
http://www.dhs.gov/secure-freight-initiative
U.S. National Nuclear Security Administration. (2010). Office of the Second Line of Defense: Megaports Initiative. Washington, D.C.
Williams, A. D. (2013). System Security: Rethinking Security for Facilities with Nuclear Materials. Transactions of
the American Nuclear Society, 109, 1946–1947.
Young, W., & Leveson, N. G. (2013). Systems Thinking for Safety and Security. In Proceedings of the 2013 Annual
Computer Security Applications Conference (ACSAC). New Orleans, LA.
Young, W., & Leveson, N. G. (2014). An Integrated Approach to Safety and Security Based on Systems Theory.
22
Fig. 1 Portion of hierarchical control structure for port security (showing representative control actions flowing down and feedback flowing up)
23
24
Fig. 3 Illustration of mapping STPA Step 1 violations of the representative security control action ‘count items in a container’ onto a high level port security control loop
25
Fig. 4 Illustration of mapping STPA Step 2 adversary actions (in italics) resulting in the STPA Step 1 violations of the representative security control action ‘count items in a container’ onto a high level port security control loop
27
Fig. A-1 Hierarchical control structure for port security (showing representative control actions flowing down and feedback flowing up).