Core Technology Through
A Case Study of Handwritten
Enterprise Launch:
Signature Verification
by Burl Amsbury S.M., Electrical Engineering (1988) S.B., Electrical Engineering (1988) Massachusetts Institute of TechnologySubmitted to the System Design and Management Program in Partial Fulfillment of the Requirements for the Degree of
Master of Science in Engineering and Management at the
Massachusetts Institute of Technology June 2000
@ 2000 Burl Amsbury
The author hereby grants to MIT permission to reproduce and to distribute publicly paper and electronic copies of this thesis document in whole or in part.
A x"
Author: Bur Amsbury
(- -- n^,;rn onnr-hnnnmnment Proarafn
Thesis Sapervis'or: DrfDaniel Frey V
Professor of Aeronautics & Astronautics
LFM/SDM Co-Director: Dr. Thomas A. Kochan George M. Bunker Professor of Management
MASAHSET
1NTI1T
MASSACHUSET TS INSTITUTE
OF TECHNOLOGY
JUN 1 4 0
LFM/SDM Co-Director: Dr. Paul A. Lifga&e
Professor of Aeronautics & Astronautics and Engineering Systems
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
by
Burl Amsbury
Submitted to the System Design and Management Program June 2000 in Partial Fulfillment of the
Requirements for the Degree of Master of Science in Engineering and Management
ABSTRACT
Tomorrow's design teams will be diverse and distributed. They will be integrated via the Internet, using engineering and management tools that allow them to transmit among themselves legally binding and safety-critical data and documents. It is essential that an Internet
infrastructure that provides a high level of security be in place. Presently, the weak link in network security is the password. When documents are digitally signed using a private key as part of an asymmetric encryption algorithm, access to that key is typically gained with knowledge of a password only. This thesis proposes a system whereby biometric data becomes part of the digital signature, tying the sender's identity to the digital signature in real time. A trusted third party-a Biometric AuthorityTM-verifies the identity of the sender by comparing the biometric data contained in the digital signature with that in a proprietary database.
Since biometric data is, in the end, just a number, it would be possible to hack a biometric data collection system and falsify the biometric data just like a password or private key. For biometric data to really be secure, it should be data that varies from valid sample to valid sample.
Handwritten signatures are the most practical example of this type of data. If two samples of handwritten signatures are identical, it is virtually certain (especially when signatures are
nominally captured dynamically) that at least one of them is a forgery. To be considered valid, a signature should not be too different from an enrollment population of samples, nor should it be identical to any previous samples. This thesis outlines technology that may be adapted to optimally choose the features of a dynamically captured handwritten signature in such a way that the identification error requirements and the network security requirements may be met. This algorithm follows from an application of Robust Design methodologies.
Thesis Supervisor: Daniel D. Frey
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Table of Contents
I
Introduction...51.1 Problem s w ith PKI... 6
1.2 Biom etric Authority TM (BA) ... 8
2 N etwork Security ... 9
2.1 Exam ple N etwork Security Applications... 9
2.2 Public K ey Infrastructure (PKI) ... 10
2.2.1 W eb of Trust ... 11
2.2.2 Digital Certificates ... 12
2.2.3 Certificate Authorities... 12
2.3 Digital Signatures... 13
2.4 Docum ent Encryption and Decryption ... 17
3 Problem s with Current Status ... 22
4 Proposed Solution... 23
4.1 Biom etric Authority M ... 25
4.2 Enrollm ent... 27
4.3 Identity V erification... 27
4.4 Inform ation Flow ... 28
5 Technology ... 30
5.1 Existing Biom etric Technologies... 30
5.1.1 Handwritten Signature V erification (H SV)... 30
5.1.2 Voice V erification... 31
5.1.3 Face Geom etry ... 31
5.1.4 Finger Scan ... 31
5.1.5 Hand Geom etry... 32
5.1.6 Iris Recognition... 32
5.1.7 Retina Scan ... 33
5.1.8 K eystroke Dynam ics... 33
5.1.9 A Com parison of Biom etric Technologies ... 33
5.2 Robust Design Methods Applied to Pattern Recognition... 34
5.2.1 Function of the Im age Recognition System ... 35
5.2.2 Extracting Features U sing W avelets... 37
5.2.3 Classifying Im ages Using M ahalanobis Distances ... 38
5.2.4 Robust Design Procedure... 40
5.2.5 Results... 43
5.2.6 Confirm ation... 45
5.2.7 Sum m ary... 46
5.3 A M ore Robust Classification M ethod ... 46
5.3.1 Feature Extraction... 47
5.3.2 Feature Evaluation ... 48
5.3.3 Sum m ary ... 58
5.4 Handwritten Signature Verification (HSV) Technology ... 58
5.4.1 Challenges... 58
5.4.2 N ew Technology... 59
6 Certificate Authority Business M odel ... 61
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
6.2 VeriSign ... 62
6.3 Som e Other N etwork Security Com panies ... 63
6.3.1 Pretty Good Privacy... 63
6.3.2 InterTrust Technologies ... 63
6.3.3 SAFLINK Corporation ... 63
7 Proposed Biom etric AuthorityTM Revenue M odel... 65
8 Sum m ary... 67
9 Bibliography ... 68
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
"We need the killer application for PKI. Just what that will be, I don't know."'
1
Introduction
As networks become ubiquitous in our increasingly "connected" economy, the security of the data being transmitted on them is becoming more and more a concern. Organizations are coming to rely on networks-extranets, intranets, virtual private networks (VPNs), the Internet-in the normal course of business. Networks are less an option and more a necessity for many... increasingly so. In particular, it is difficult to imagine a healthy organization today that does not have access to, and take advantage of, the Internet. But as soon as something becomes necessary, it also becomes a target for crime. And besides criminal misuse of data, many individuals (especially in the United States) are concerned with issues of personal privacy.
In general, linking a document indelibly to an individual sender affords the following
advantages2
* Authenticity. Assures the receiver that the sender is who he says he is. e Integrity. Affords both sender and receiver the opportunity to verify that the
document received is exactly the same as the one sent.
e Nonrepudiation. Denies the sender the ability to deny that he actually sent the
document.
* Legal significance. It serves to remind the sender of the importance and legal implications of the document in question, thereby presumably reducing frivolous document transmission.
Alex van Someren, president and CEO, nCipher, quoted in "Security Roadmap", SC
Magazine, www.scmagazine.com, December 1999.
2 Turban, Efraim; Lee, Jae; King, David; Chung, H. Michael, 2000, Electronic
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
The existing Public Key Infrastructures (PKIs) meet these needs with some success. However, in reality a PKI provides a link between an originating document and the password, Personal Identification Number (PIN), or private key of the alleged sender. If the key is compromised (or more commonly the password used to access the encryption software that uses the key), the link is not valid. Biometric data can be used to add an additional layer of security by verifying the sender's identity with something he is (fingerprint, signature, iris pattern, etc.) rather than with something he knows (password or PIN) or has (smart card or token).
1.1 Problems with PKI
New products will be developed by just-in-time collaborations of globally distributed teams linked seamlessly by Web-based tools and processes. The collaborations will be formed by means of a "services marketplace" where lead
firms will find the world's best "knowledge purveyors"-suppliers of information, components, and support services.3
A fundamental requirement for the widespread acceptance the model outlined in the
vision statement (see lead quote for this section) for MIT's Center for Innovation in Product Development (CIPD) is the ability of team members to believe beyond a reasonable doubt that their teammates are who they say they are. Other examples of enterprises that will require high levels of network security are: many forms of e-commerce; distance-learning ventures; and government agencies, such as the military forces, Patent and Trademark Office (PTO), and voter registration administration.
Today, network security is dealt with using a PKI, which depends on asymmetric
encryption technology. Digital signatures are meant to prove to the receiver of a digitally signed document that the sender is who he claims to be. The document and the sender's private encryption key are used to create the digital signature. The private key has a counterpart, called a public key, which can be used to decrypt data encrypted with the
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
private key, but cannot be used to encrypt as a replacement for the private key. The idea is that the receiver, using the sender's public key, decrypts the digital signature that could only have been encrypted by the owner of the associated private key. The problem is that it could have been the holder of the private key instead the original owner. The private key could have been compromised-it is just a file stored on a (often portable) storage medium. To use the key in an attempt to masquerade as the true owner only requires knowledge of the owner's password.
"Security? You want the truth? Okay. Sure you're going to have hackers here and there. And viruses. But you want to know what's going to hurt more? Passwords. I mean it... Someone has to get rid of them. I don't know what with. I know it can't be smartcards. People lose those too."4 Passwords are not considered very secure. The weak link in today's network security infrastructure is the password.
An analogy that underlines the lack of true security provided with a system like the one described above: It is like accepting an already-signed check (one not signed in the presence of the vendor) from a customer that shows a social security card as proof of identity.
To tie a person to his digital signature in real time, a biometric solution is needed. The biometric data used today include fingerprints, voiceprints, dynamically captured handwritten signatures, iris scans, retina scans, hand geometry, face geometry, and key patterns. Incorporation of such data and devices into the existing infrastructure has been slow. Reasons for this include a lack of technology maturity, the cost of the hardware required, the fact that hardware is required (many people are not anxious to add another peripheral to their systems), and privacy issues. There are really two types of privacy concerns. One is with the ownership and privacy of the data itself. The second is the physical invasiveness of some of the technologies, particularly the retina and iris scans.
4 An IT officer, speaking on condition of anonymity, quoted in "Security Roadmap", SC
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Bur Amsbury, June 2000
Another problem often not mentioned in existing literature is the fact that biometric data is just a number and as such, can be stolen as any other number or password. What is needed is biometric data that is consistently associated with a single person, but varies enough from capture to capture that an algorithm can tell it is unique to a person and
unique to a particular capture.
1.2 Biometric Authority
TM(BA)
I have argued that, in cases where a high level of security is desired, the system needs to
provide for minimum delay between physical identity verification and digital signature validation. And I have argued that the physical identity verification must be done biometrically. These requirements may be answered with the creation of what we are calling a Biometric AuthorityTM.
The function of the BA is to take as input a biometric data sample and return either yes/no verification or a confidence level. The data will be sent to the BA by the entity that wishes to verify a digital signature (the receiver of a digitally signed document). The BA will compare and contrast this sample data with other samples it owns in a central database. These samples are initialized with enrollment samples provided by the sender at the time of enrollment. Enrollment is also when initial physical identity verification is done. The enrollee is asked to supply several samples of biometric data corresponding to his local system's capabilities. For example, the biometrics may be electronically
captured handwritten signatures, thumbprints, or voice prints.
The Biometric AuthorityTM is envisioned as a new key piece of Internet security infrastructure. It would be implemented as an Application Server Program (ASP) and likely prove most useful initially serving a business-to-business (B2B) role.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
2 Network Security
"In terms of its security infrastructure, the World Wide Web is rotten at the core."5
2.1 Example Network Security Applications
Examples of networks that may require levels of security not reachable with the existing PKIs are:
e Virtual Private Networks (VPNs) that transport commercial design data among extended team members. It is important that design changes (to software code or hardware) be traceable at the time of transmission to the authorized designer. This can be a matter of legal import, both in matters of product liability and in matters of intellectual property.
* In addition, VPNs carry an increasing amount of proprietary information. In
1999, Fortune 1000 companies sustained losses of more than $45 billion from
thefts of their proprietary information. Online copyright theft is rising to epidemic proportions, threatening the creative industries while inhibiting the development of electronic commerce. Losses due to Internet piracy are estimated at nearly $11 billion each year.6
* Matters of national security. So-called tactical networks that carry data in real time to members of our armed forces engaged in battle must be protected aggressively.
* Government agencies that deal with huge networks of personal private data. For example, the PTO does an increasing amount of business over networks. The Census Bureau and the Internal Revenue Service (IRS) are two more examples.
5 Randy Sandone, president and CEO of Argus Systems Group, quoted in "Computer Crime Spreads", SC Magazine, www.scmagazine.com, April 2000.
6 Taken from a PricewaterhouseCoopers report, quoted in "Security Roadmap", SC Magazine, www.scmagazine.com, April 2000.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
The U.S. Postal Service may soon become involved in matters of Internet security as a certificate authority (CA).
e Medical information is more and more commonly shared among hospitals and other medical facilities over networks. There is considerable concern regarding the privacy of this data. Another similar example is insurance data.
* Electronic commerce, in business-to-consumer form and in business-to-business, is a clear example of a situation that begs for better security. The FBI has
reported that cases of computer-related security breaches have risen by almost 250 percent in the past two years. Dollar losses, associated with various computer crimes and theft of intellectual property, were estimated to be in the $250 billion-range in 1997.7
2.2 Public Key Infrastructure (PKI)
There are two broad categories of electronic encryption: symmetric and asymmetric. In symmetric schemes, the "key" or code number used to encrypt the data is the same as the key used to decrypt it. Therefore, in order to give someone the ability to decrypt a secured document, one must also give him or her the power to encrypt a document. Such a system is useful only when there are a very few mutually trusting key holders.
Asymmetric schemes have a separate key for encrypting and decrypting. It is therefore possible to give someone the ability to decrypt a message without giving away the encryption key. There are two main ways to use asymmetric keys. They both involve a private key and a public key. They differ in which is used to encrypt and which is used to decrypt.
To create a digital signature, the sender uses his private key to encrypt a hashed version of the document being signed. The receiver uses the public key (available publicly, of
7 Armstrong, Illena, April 2000, "Computer Crime Spreads", SC Magazine, www.scmagazine.com.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
course) is used to decrypt (verify) the signature. A public key can only decrypt data encrypted with the matching private key. The idea is that the private key can only be used by the entity to which it was issued, thereby serving as proof that the sender is who he claims to be. Note that the original document is sent "in the clear." It is not
encrypted. The purpose of a digital signature is merely to allow the receiver to verify the identity of the sender.
To send an encrypted document, theoretically one could encrypt it using the public key of the intended receiver. The only entity able to decrypt the document would then be the holder of the receiver's private key and associated password. In practice, it is not done quite like that (see Section 2.4), but the complementary nature of the two ways to use asymmetric key pairs holds true.
2.2.1 Web of Trust
When the receiver of a digitally signed document decrypts the signature and finds that the name of the person associated with the private key is the same as the name claimed by the sender, she is said to have verified the signature. In fact, though, she has verified reliably that the sender used a private key which at one point was issued to a single person (or entity). She has not really verified that the present holder of the key is the one to whom it was issued. That is the nature of the essential problem with PKI and the issue that this thesis addresses.
Moreover, how does the receiver even know that the private key in question was really issued to whom she thinks? She did not see it happen, in general. She has to go on the word of someone who did. The "word" of someone who did is typically just another message saying so. Well, how does she know she can trust the word of this third party?
By verifying the third party's digital signature. Clearly, this is circular reasoning, but the
result, given enough players in the network, is what is known as a "web of trust." If everyone is careful to only sign the public keys of individuals that they physically saw receive the associated private key, then eventually the web of trust is inter-networked
enough to provide reasonable assurance that the private key was really issued to the right person.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
For some of its low-end personal security products, the company Pretty Good Privacy (PGP) relies on a web of trust made up of everyday citizens. No individual has
fundamentally more or less authority or credibility than another. This web of trust, in one form or another, is the backbone of PKIs.
2.2.2 Digital Certificates
In higher-end schemes, particularly those relied upon in business-to-business transactions, the trusted third party may not be a peer. There are companies whose business it is to act as the trusted third party. They issue digital documents to applicants in exchange for solid (sometimes physical) identification and money. These documents (called "digital certificates") contain at least the recipient's name, public key, the expiration date of the certificate, and the digital signature of the issuer. The issuer in these cases is called a certificate authority (CA).
2.2.3 Certificate Authorities
A handful of commercial organizations have managed to win over enough certificate
customers that the organization's assurance of a digital signer's identity is widely
considered proof that the private key was issued to the proper person. (There may still be some question as to the identity of the current holder of the private key.)
One example of such an organization is VeriSign. There are others and together they form their own web of trust. For example, the certificates issued by VeriSign are digital documents that need to be digitally signed. VeriSign's digital signature may be verified using another digital certificate from, say, Entrust. For relatively lower levels of security, VeriSign may sign its own certificates. The receiver is then left to decide for himself what level of trust he places in VeriSign. Likewise, some large well-known
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
A hierarchy of CAs is envisioned and partly in place, but it is not clear who will act as
higher authorities in such a hierarchy. Cross-certification is becoming popular for international EC.
2.3 Digital Signatures
A digital signature, in conjunction with a digital certificate, is meant to provide a means
for the receiver of a document to authenticate the identity of the sender. It also provides assurance to the receiver that the sender cannot later claim that the document was
unauthorized (renouncing or repudiating the document). This works because the sender's identity is in theory linked to the document by the signature.
Figure 1 illustrates the idea.
8 Turban, Efraim; Lee, Jae; King, David; Chung, H. Michael, 2000, Electronic
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Sender
Receiver
Document
Hash Function
#############
Hash Value
(or "Message Digest")
Encrypt with
Sender's Private Key
Digital Signature Sender's Digital Certificate Document Hash Function ~~re_Compar If same, signature is valid. (?) / / I I 4 0-*~ / Decrypt with / Sender's Public Key
4k
Digital Signature'4
(copy of) Sender's Digital Certificate
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
On the sender's end, the user supplies a document file, a certificate file, and a password to software that performs the following functions:
1) The document is "hashed" using a hash function. The result is a hash value or "message digest." The hash value is a number of fixed length. It is typically much shorter than the document, but long enough that it is extremely unlikely for two different documents to result in the same hash value.
2) The hash value is encrypted using the sender's private key, to which the software has access when supplied with a) the physical location of the key (for example, Drive 'C', Directory "Secret") and b) the user's password. The result of the encryption is the digital signature.
The original document, the digital signature, and a copy of the sender's digital certificate are sent to the intended receiver via a network connection. The receiver also gets the unencrypted original document (via email, for example). To verify that the document is actually from whom it purports to be, she enters into her verification software the
received document file, the sender's certificate, and the signature. Her software performs these functions:
1) The document is hashed using the same hash function. Note that there is a requirement for compatibility between the two users' software.
2) The sender's public key, taken from his digital certificate, is used to decrypt the signature. The result of the decryption is also a hash value.
3) If the two hash values created are the same, then the sender's document is
unquestionably linked to the sender's password and the file that contains his private key. The assumption is that the sender himself is in turn linked to the password and private key file.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Sender
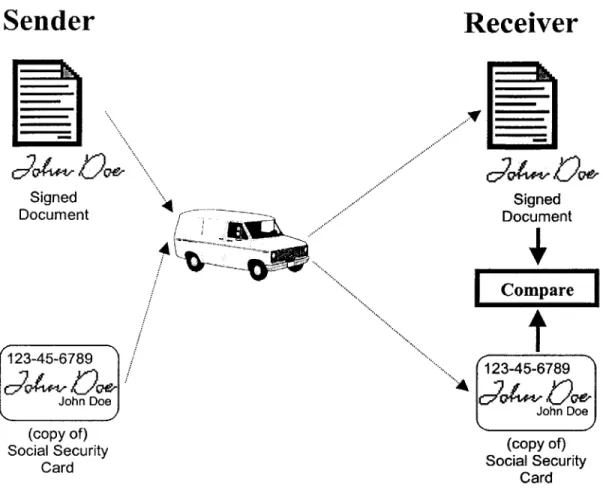
Signed Document 123-45-6789 John Doe (copy of) Social Security CardReceiver
.. '9
Figure 2. An Analogy for Digital Signatures
In this metaphor, a document is signed (with a real signature), but not in the presence of the intended receiver. The document is sent to the receiver along with a signed copy of the sender's social security card, which is issued by a trusted authority (the United States
government) and contains the sender's name and identifying code number (social security number). The receiver is left to compare the signature on the document to the one on the
card to verify the identity of the sender. She may choose to interrogate the government to confirm that the social security number on the card is indeed linked to the name of the
alleged sender. For many transactions, this level of security is acceptable. For others, it is not. Signed Document Compare 123-45-6789 John Doe (copy of) Social Security Card
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
2.4 Document Encryption and Decryption
Document encryption is used to keep the contents of a document secret, unlike digital signatures, which are used to authenticate the identity of the sender but allow
transmission of the document in the clear. Encryption is an additional layer of security. It would not make sense to use document encryption without including a digital
signature. The basic scheme for encryption and decryption is shown in Figure 3 and Figure 4.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Sender
Hash VlHash
Functionc ##
igi# Sn a
Hash Value Encryp~t with Digital Signature (or "Message Digest") Sender's Private Key
Sender's Digital Certificate From Receiver Receiver's Digital Certificate Encrypt with -Symmetric Key Encrypt with ... 1
Receiver's Public Key
Digital Envelope
To Receiver Encrypted Document
Figure 3. Document Encryption (Sender) [Turban 20001
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Receiver
Hash Function #############
To Sender Hash Value
Document (or "Message Digest")
Receiver's Digital Certificate
Decrypt with
One-:. time Symmetric Ke
L
...-...-... C o m p a r
Encrypted Document Senders Digital
Certificate From Sender
Digital Envelope Decrypt with
Receiver's Private Key
Digital Signature Decrypt with Hash Value
Sender's Public Key
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Refer to Figure 3. Document Encryption (Sender).
1) A digital signature is created in the same manner described previously.
2) The document, the digital signature, and the sender's digital certificate are concatenated and encrypted using a standard symmetric encryption key. The result is the encrypted document. A symmetric key is typically used only once, and then discarded. Documents are encrypted this way because the encryption algorithms using symmetric keys are more efficient (faster) than the ones using asymmetric keys. For large documents, the time difference can be significant.
3) The symmetric key itself, a number much shorter than the document, is encrypted
with the receiver's public key. The result is called a digital envelope. No one other than the holder of the receiver's private key and password can access the key that will be used to decrypt the document.
4) The digital envelope and the encrypted document are sent to the receiver.
For an illustration of the logistics on the receiving end, refer to Figure 4. Document Decryption (Receiver).
1) The digital envelope is decrypted using the receiver's private key. The result is
the one-time symmetric key.
2) The symmetric key is used to decrypt the encrypted document. The result of that is: a) the document, b) the sender's digital certificate, and c) the sender's digital signature.
3) The digital signature is verified in the normal way.
The advantage of dealing with a Biometric AuthorityTM is not affected by whether or not a document is encrypted. The BA adds a layer of security to the signature verification process whether or not the associated document was encrypted. Therefore, this thesis does not describe biometric authorization in the context of document encryption, only in
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
the context of digital signatures. It is enough to say that the two concepts (document encryption and biometric authorization) are compatible.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
3 Problems with Current Status
The receiver of a digitally signed document may be assured of the signature's validity by a trusted third party. The third party, whether it is a well-known certificate authority or another individual in the receiver's "web of trust", cannot in general vouch for the identity of the person using the sender's signature at the moment the document was signed. All that a forger really needs is a copy of the file containing the alleged sender's private key and the password with which to gain access. The file is no more or less difficult to obtain than any physical item, like a real key. The password is also not particularly secure. According to a survey conducted at a 1996 hackers conference, 72 percent of the hacker respondents said that passwords were the "easiest and most common hack" used.9 This is because people are often not particularly careful with them-they write them down, use them for multiple purposes, and fail to change them often.
In short, the weak links in PKIs are the password or PIN and the physical security of the encryption key. It is not the number of bits in the key or the type of algorithm used to encrypt. It comes down to the fact that there is a time delay between a) the physical linking of signature and person, and b) the validation process by which the signature is verified. The time delay may be as much as several months. During that time, the key and password have been exposed to compromise. The more that exposure time can be reduced, the more secure the system becomes. Ideally, the time would be a matter of seconds.
For systems that require a level of security such that access may be granted in exchange for something the person has and something the person knows, PKI is perfectly adequate. For systems that require more, real-time validation-something the person is-is all that
is really available. For that, biometrics are required.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
4 Proposed Solution
"I think a lot of companies or people believe security is about encryption, and in
fact, that's really the easiest part of security. What really drives the Internet is the ability to know who you're dealing with, ensure it's confidential, and then have
people confirm transactions that they can't get out of."'*
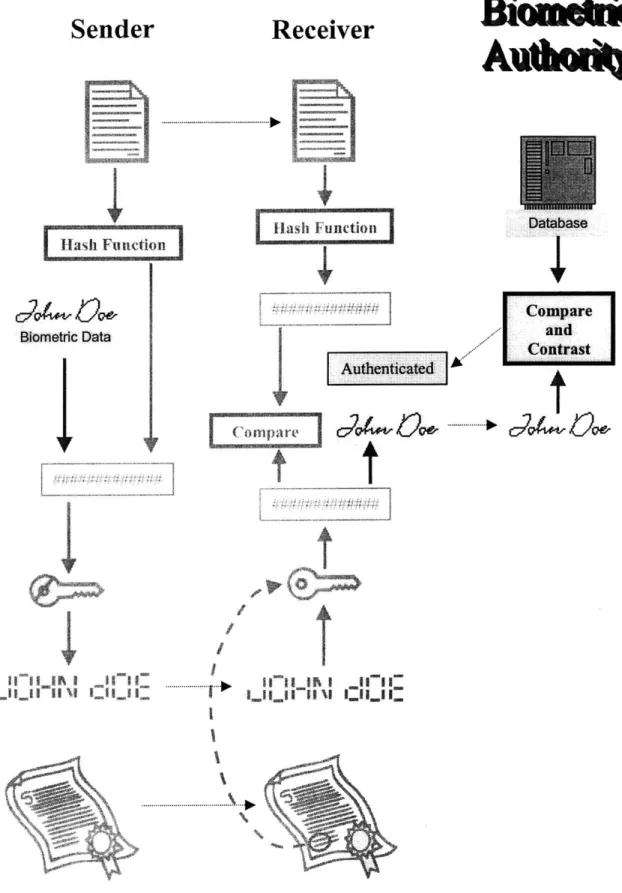
In the physical world, a picture ID with a signature on it is required as proof of identity. Two such IDs are required if the transaction is really important. We propose that an equivalent layer of security be added to the existing Internet security infrastructure. Figure 5 illustrates what such a layer would look like in the abstract.
10 Entrust CEO John Ryan, quoted in "Entrust CEO John Ryan Discusses the Rapid Growth of the Internet Security Market on The IT Radio Network", Business Wire, www.businesswire.com, March 30, 2000.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Sender
Receiver
BiOfl
lash Function Database
sh Finction Compare Data and Contrast Authentiae m.t 2.2 *~.!
t
-pro
I II XI ~ I~- S .... ... I ... 1 11 IC IIJIIi
ii i 5
.1Figure 5. Proposed Biometric AuthorityTm H a
Biometric
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
4.1 Biometric Authority
TMIf you have some complex software, keep it from the bad guys with some simple software."
In Figure 5, the existing procedure by which digital signatures are generated and verified (see Figure 2) is shown in faded colors. The Biometric AuthorityTM layer is bright. This layer operates as follows:
1) Biometric data (in this case, an electronically-captured handwritten signature) is
processed by appropriate hardware. The resulting features (possibly encrypted with the BA's public key) are added to the hash value associated with the document to be sent.
2) The receiver of the digital signature decrypts it as always. The result is a hash value used for comparison as before, plus the biometric data features from the sender.
3) The receiver transmits these features to the BA.
4) The BA checks the biometric data received against its database. The database contains several previous submissions from the same sender. (At the very least, these previous submissions would be the initial set of samples provided during the sender's enrollment.) The BA checks that a) the sample's important features match closely those of the samples provided, and b) the sample's features are not duplicates of previous samples.
5) The BA transmits to the receiver of the digitally signed document a message that communicates the BA's level of confidence that the sender is who he says he is.
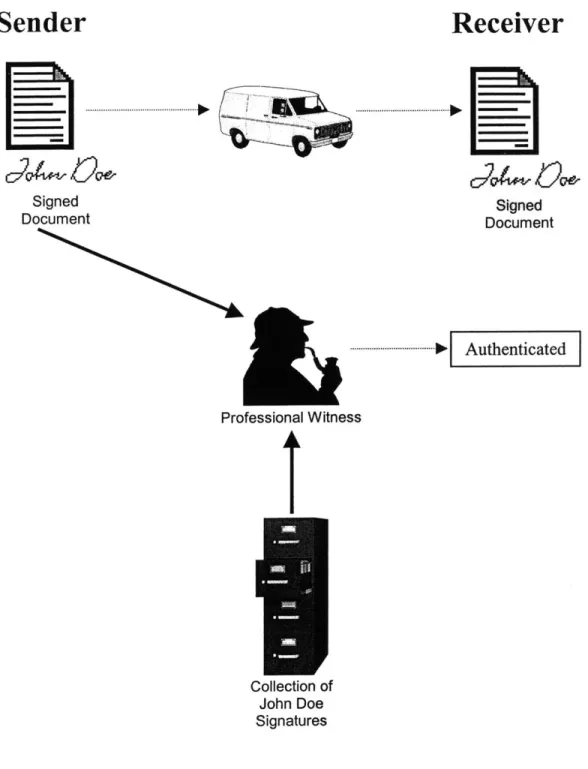
A corresponding metaphor for our proposed security infrastructure is shown in Figure 6.
Treese, G. Winfield; Stewart, Lawrence C., 1998, Designing Systems for Internet Commerce. Reading, Massachusetts: Addison Wesley Longman.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Sender
Signed DocumentReceiver
Signed Document ... A uthenticated Professional Witness Collection of John Doe SignaturesFigure 6. An Analogy for the Biometric AuthorityTM
In our mnetaphor, the sender signs his document as always, but does so in the presence of a trusted third-party witness. This professional witness has on file a collection of
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
receiver. The witness (the Biometric AuthorityTM) checks the signature against his database and informs the receiver of his conclusions regarding its validity.
4.2 Enrollment
Enrollment is the process by which the sender of a biometrically enhanced digital signature initially submits his biometric data. Several samples (on the order of five) are required. This data will constitute the database entries against which candidate signatures (transmitted from the receiver of a digital signature) are compared for validation. With each valid signature the BA sees, another sample is added to its database. The
confidence score returned to the receiver is affected not only by the position of the new sample within the existing database population's feature space (see Section 5.2), but also the size of the population for a given customer (sender).
4.3 Identity Verification
Perhaps the most important aspect of the enrollment process is the method of personal identification. We envision three possible choices for the customer, resulting in three corresponding security level ratings and at least three pricing structures.
Lowest. At this level, we use a method of identification the same as certificate
authorities such as VeriSign commonly use today. This enrollment process could take place entirely online via our secure website. The user would supply credit card
information, address, telephone numbers, the full names of family members, and perhaps their social security number. Using currently available methods (credit card purchase patterns, for example), the Biometric AuthorityTM would establish a relatively high confidence that the person is who he says he is. The biometric data would then be linked to his identity in the BA's database.
Medium. Here, we tie biometric data to a person's identity established as in the above
case, but only in the physical presence of a trusted authority or enrollment officer. The enrollment officer will be an employee of the corporate client. The client must have previously established a position of trust. The corporation may choose and monitor their own enrollment officer, who will enroll other members of the corporation's staff. The
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
corporation will be held responsible for the enrollment officer's professional conduct and trustworthiness.
Highest. This level of security is established in a way very similar to the medium-level case, with the exception being that the enrollment officer is an employee of the Biometric AuthorityTM. This official would be very highly paid, with an impeccable record of integrity. The costs, of course, will be passed on to the customers who choose this highest level of security. The enrollment may be done locally or at the BA headquarters.
4.4 Information Flow
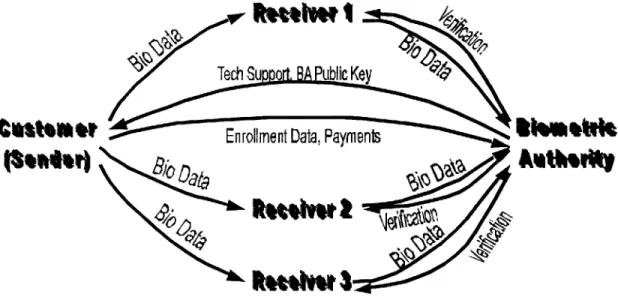
Figure 7 shows the flow of goods and services between parties.
Tech Su o ublic Key
Enrollment Data. Payments
Figure 7. Biometric AuthorityTM Information Flow
The customer supplies enrollment data-shown in black along with other less frequent transactions-to the BA. In exchange for payments, the BA supplies technical support and periodically updates its public key. The BA's public key may in some cases be used to encrypt biometric data at the sender's locale. Upon receipt, the BA will decrypt the data with its private key.
The normal, more frequent data flow is shown in dark blue. It consists of: biometric data contained in modified digital signatures flowing from the customer to its various
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
receivers; biometric data from the receivers to the BA; and a verification score supplied to the receivers by the BA.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
5 Technology
5.1 Existing Biometric Technologies
There are several biometric technologies on the market. They are in different stages of development and deployment, each with different advantages and disadvantages. This section outlines each of the options presently available.'2
5.1.1 Handwritten Signature Verification (HSV)
A number of hospitals, pharmacies and insurance firms use DSV to authenticate
electronic documents. Other applications include U.K. Employment Services and Ginnie Mae mortgage form processing.
Although it is considered one of the less accurate biometrics, there are minimal public acceptance issues. The only hardware required is the graphics tablets, which are
available in the $50 range. Software cost varies with application. Our research group is actively pursuing the accuracy problem (see Sections 5.2 and 5.3).
5.1.1.1 Advantages of HSV
Handwritten Signature Verification has several advantages that, we believe, outweigh its perceived accuracy problem. For one, the natural variations that occur between
signatures by the same person-and are a cause for the problem of accuracy-are also a potential source of security (see Section 1.1). The same is true of voiceprints and perhaps face geometry.
Signatures have the added benefits of wide public acceptance and minimal intrusiveness. No one gives a signature unwillingly and we all understand the legally binding nature of a signature. Face geometry may be analyzed without the person's permission;
voiceprints have not historically been accepted (at least in the U.S.) as having legal standing compared to a written signature.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
5.1.2 Voice Verification
The user states a given pass phrase and the system creates a template based on numerous characteristics, including cadence, pitch, tone. Background noise greatly affects how well the system operates.
Speaker verification is primarily used in applications where identity must be verified remotely over telephone lines. It is used to access voice mail systems at the University of Maryland, to deter cellular phone fraud by GTE, and to activate credit cards by
telephone. It is also used to verify the identity of parolees under home incarceration.
The software and hardware costs are minimal.
5.1.3 Face Geometry
This technology uses a standard off-the-shelf camera to acquire the image of a face from a few feet. The systems are designed to compensate for glasses, hats, and beards.
There are a number of identification applications with face recognition, including driver's licenses in Illinois, welfare fraud in Massachusetts, and INS pilots. Face recognition is used in InnoVentry's ATM's to verify the identity of check cashers. FaceVACS is an
automated safe deposit system using face recognition. The US/Mexico border crossing project, SENTRI, used Visionics face recognition in conjunction with voice verification. India Oil Company uses Miros face recognition for a time and attendance application. There are also consumer applications that replace passwords for Windows NT and 98
login with face recognition.
Public acceptance is relatively high and system cost is low at $100 per site for the software.
5.1.4 Finger Scan
Fingerprint scanning is fast becoming a popular method of identity verification. There are a number of financial applications, including ATM verification at Purdue Employees Federal Credit Union and verification of customers at the teller window at Conavi Bank in Colombia. Compaq is shipping an Identicator finger scan unit with it computers.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Woolworth retail stores in Australia use Identix finger scan to verify the identity of
80,000 employees. The Turkish parliament uses finger scan to verify government
officials when they vote.
There is some resistance to the idea of submitting a fingerprint, because some feel they are being treated as a criminal. The idea seems to be gaining acceptance, however.
Units range in cost from a hundred to a few thousand dollars, including hardware and software, depending upon the configuration.
5.1.5 Hand Geometry
Hand geometry has been used for physical access and time and attendance at a wide variety of locations, including Citibank data centers, the 1996 Atlanta Olympics, and New York University dorms. Lotus Development Corporation uses hand geometry to verify parents when picking up children from daycare. The University of Georgia uses hand geometry to verify students when they use their meal card. The Immigration and Naturalization Services department of the U.S. government has rolled out an unmanned kiosk to expedite frequent travelers through customs. The system can currently be found in 8 airports, including San Francisco, New York, Newark, Toronto, and Miami.
The finger/hand geometry systems do not raise many privacy issues and the technology is easy to use. They are still relatively expensive, at $1500 per unit.
5.1.6 Iris Recognition
The iris is an excellent choice for identification: it is stable throughout one's life, it is not very susceptible to wear and injury, and it contains a pattern unique to the individual.
A pilot project outfitted some automatic teller machines (ATMs) in England with iris
recognition systems. A number of employee physical access and prisoner identification applications are in use, including correctional facilities in Sarasota, Florida and
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Iris scanning raises two key public acceptance issues: intrusiveness and ease of use. Technology is advancing such that both concerns are being addressed, but widespread use is still some years in the future.
IiScan plans to release home and office products in the first half of 2000, and hopes to break the $500 price barrier.
5.1.7 Retina Scan
Retina scanning looks at the pattern of blood vessels in a person's eye. It is even less well developed than iris scanning and requires the user to place his or her eye very close to the scanner. This makes it more intrusive than other systems.
5.1.8 Keystroke Dynamics
Verification is based on the concept that the rhythm with which one types is distinctive. It is a behavioral verification system that works best for users who can "touch type". Currently NetNanny is working to commercialize this technology.
5.1.9 A Comparison of Biometric Technologies
Figure 8 is a chart that compares the above biometric technologies on four points:
intrusiveness, accuracy, cost, and effort. Intrusiveness and effort are important factors in determining public acceptance. Accuracy and cost are factors important to the company using the technology, as is the higher-level concern of public acceptance.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Zephyr":
Analyis
Key Stro M Dynaenics Ham Gownety
Fae Geoetry.DnneSnnn
Rotina 8n FlrigEW Sean
Its $can 6QMie@aa
0 CopyrghtI Intematnal 6io8 etrte Group wwwbt4,metrkc rotpXm
0
UtyW4 f _*A~qUrutCy *Colo40 efforFigure 8. Comparison of Biometric Technologies (Reprinted with permission from International Biometric Group, a New-York based consulting firm)
5.2 Robust Design Methods Applied to Pattern Recognition
The core technology upon which our signature recognition algorithm is based has its roots in pattern recognition. Handwritten signatures can be viewed as "noisy" patterns. The noise is mostly a result of the fact that people do not sign their name exactly the same way twice. Prof. Daniel Frey of MIT's Aeronautic & Astronautic Department has
developed an approach to image recognition that uses robust design methods to help select the features best employed for classification. Historically, one of the biggest problems facing the development of handwritten signature verification (HSV) algorithms
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
has been the need to reduce the feature set while reducing both false positive and false negative error rates.13
The remainder of Section 5.2 is an adaptation of Prof. Frey's paper "Application of Wavelets and Mahalanobis Distances to Robust Design of an Image Classification System".1 4
This image recognition algorithm uses wavelet transforms to extract features from images. These features were used to construct Mahalanobis spaces for each type of image in a set. The system classifies noisy images by comparing the Mahalanobis
distance to all of the image types in the set and selecting the image type with the smallest distance. The system was tested using gray-scale bitmaps of four famous portraits. Robust Design methods were employed to optimize the selection of image features used to construct the Mahalanobis space. The optimized system employs only 14 coefficients for classification and correctly classifies more than 99% of the noisy images presented to it.
5.2.1 Function of the Image Recognition System
This image recognition base case was originally developed as a case for use in teaching robust design and Mahalanobis distances. The system classifies gray-scale 5
representations of fine art prints-given a bitmap, it should respond with the title of the artwork represented. For purposes of this study, Prof. Frey chose four well-known portraits: DaVinci's "Mona Lisa", Whistler's "Portrait of the Artist's Mother", Peale's
13 Gupta, Gopal and McCabe, Alan, 1997, "A Review of Dynamic Handwritten Signature Verification", James Cook University, Townsville, Queensland, Australia.
14 Frey, Daniel D., 1999, "Application of Wavelets and Mahalanobis Distances to Robust Design of an Image Classification System", presented at ASI's 17th Annual Taguchi Methods Symposium, Cambridge, Massachusetts.
1 In gray-scale images, a value of zero represents black while a value of 255
represents white. All the integers between are smoothly varying shades of gray between these extremes.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
"Thomas Jefferson", and Van Gogh's "Self Portrait with Bandaged Ear". The low-resolution bitmaps (32x32) used in the study are depicted in the top row of Figure 9.
In practice, if one were given an image to identify, various types of noise would likely affect it. In the case of images, sources of noise might include lack of focus, white noise or "snow" introduced during transmission, and off-center framing. Further, it may be desirable to correctly identify the image without prior knowledge of whether the image is
a negative or a print. To simulate such noise conditions, the following operations in the following order were performed on each image to be classified:
1. The position of the image in the "frame" was shifted by -2, -1, 0, 1, or 2 pixels with equal probability. The shift was made both horizontally and vertically but the amount of the shift in the x and y directions were probabilistically independent.
2. The images were transformed into a negative with probability 0.5.
3. The image was blurred by convolving the image with a pixel aperture whose size
varies randomly among 3, 4, and 5 pixels square.
4. The image was superposed with "snow" by switching each pixel to white with probability 0.75.
Examples of the effects of these noises are depicted in Figure 9. The first row contains bitmaps of all four portraits without noise. Below each portrait are three noisy versions of the same portrait. The degree of noise is intended to be severe enough to make classification of the images difficult.
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
IF
46 Z9.I r.A S 4:L J e 01 e Jw", --Jr. 16 r z-;- % ; k VU-0 .4. k WeIFigure 9. The Images of Fine Art Prints Before and After Application of Noise Factors
5.2.2 Extracting Features Using Wavelets
This section introduces wavelets and their application to image recognition. The goal is to provide just enough background to allow the reader to understand the Robust Design case study. The treatment will therefore be qualitative. For a more detailed mathematical introduction to wavelets in engineering, the reader may wish to refer to Williams and Amaratunga.16
A wavelet transform is a tool that cuts up data, functions, or operators into different
frequency components with a resolution matched to its scale.17 Therefore, wavelets are useful in many applications in which it is convenient to analyze or process data
hierarchically on the basis of scaling.
16 Williams, J. R. and K. Amaratunga, 1994, "Introduction to Wavelets in Engineering",
International Journal of Numerical Methods Engineering, vol. 37, pp. 2365-2388.
17 Daubechies, I., 1992, Ten Lectures on Wavelets, CBMS-NSF Regional Conference
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
Given the power of wavelets in extracting key features of an image based on a hierarchy of scales, Prof. Frey chose to employ them in the Robust Design of an image recognition system. The next section describes the way that the matrix of wavelet coefficients was used to construct Mahalanobis spaces used to classify images.
5.2.3 Classifying Images Using Mahalanobis Distances
The Mahalanobis distance is a statistical measure of similarity of a set of features of an object to the set of features in a population of other objects. To compute the distance, one must construct a Mahalanobis space by computing the mean vector (pi) and
covariance matrix (1) of the features in the training population. The Mahalanobis distance of any object within the space is a scalar that can be computed given a vector of features f by the formula
MD
(f)= (f - p) E- (f -I)t(1) nwhere n is the number of elements in the feature vector f.
Objects can be classified using the Mahalanobis distance by constructing two or more Mahalanobis spaces. Classification is accomplished by computing the Mahalanobis distance in each space and selecting the shortest distance. In effect, this procedure allows one to determine which class of objects is statistically most similar to the object to be classified.
Prof. Frey applied Mahalanobis spaces and wavelets to image recognition by using wavelet coefficients as the elements of the feature vector f. For each of the four portrait types (Mona Lisa, Whistler's Mother, Jefferson, and Van Gogh) he took the following steps:
" Created a training population of 74 noisy images using the noise factors described in
Section 5.2.1.
" Took the two-dimensional wavelet transform of each noisy image based on the
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
* Selected a subset of the wavelet coefficients (the approach for selecting this subset will be described in Section 5.2.4) and assembled them into a vector.
* Computed the mean vector and covariance matrix of the population.
50 401 0 0 30 20 10 0 10 20 30
Distance to Mona Lisa
40 50
o 0 0 Individual Mona Lisas
X X X Individual Whistler's Mothers Threshold
Figure 10. The Mahalanobis Distances Applied to Classification of Two Fine Art Images
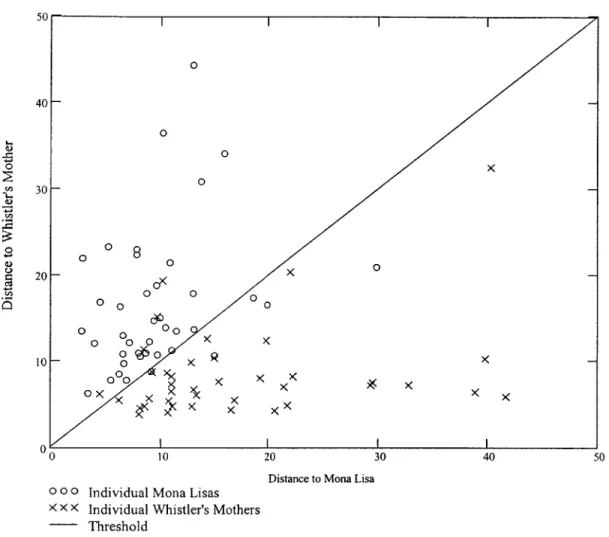
To illustrate how Mahalanobis spaces constructed in this manner can be used for
classification, consider the following example. The first 8x8 coefficients of the wavelet transform were used to construct the Mahalanobis space for the Mona Lisa and for Whistler's Mother. Then, a test population of forty noisy copies of both portraits was produced. The Mahalanobis distance of each portrait in the test population was computed
in both spaces. Figure 10 graphically displays the results. The Mahalanobis distance of any noisy image to the Mona Lisa is plotted on the x-axis while the distance to Whistler's Mother is plotted on the y-axis. Circles represent the images created by adding noise to
0 0 0 0 0 0 8 0 0 - -< 0 0 0 0 0 0 0 0 0 0 0 0 X 0 0 0 R 0 00 O X X X X X X
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
the Mona Lisa while the images derived from Whistler's Mother are represented by X's. The Mona Lisa points tend to lie in the upper left because they are more similar to the training population derived from Mona Lisas. There is however considerable scatter among the test population of Mona Lisas due to the degree of noise applied. A similar pattern is evident in the test population of Whistler's Mothers except that, as one would
expect, they tend to lie in the lower right.
To classify an object, one may compute the Mahalanobis distance of that object within two or more spaces and select the class for which the distance is lowest. For the two-way classification task in Figure 10, this procedure implies that those points above the
diagonal line are classified as Mona Lisa while those below the line are classified as Whistler's Mother. As Figure 10 shows, this will result in occasional mistaken classifications. In this case, the error rate is about 10%.
The classification procedure described above was expanded to a four-way classification system by making bitmaps of the other two portraits, constructing their Mahalanobis spaces, and generating test populations. For the same set of noise factors, the error rate rose to 37%. In general, a classification task becomes more difficult as one increases the number of possible classes to which the objects may belong.
In some cases, reducing the set of features in the vector f will reduce the error rate. Reducing the number of features also tends to increase the speed of the classification task
and lowers the required size of the training population since the covariance matrix cannot be inverted unless the training population is at least the square of the length of the feature vector. This suggests that some systematic and efficient means of selecting the features would be of significant value. Taguchi has shown that orthogonal array experiments can serve this purpose well and several case studies have been published on the technique. The next section documents an adaptation of Taguchi's method to optimizing the image classification system.
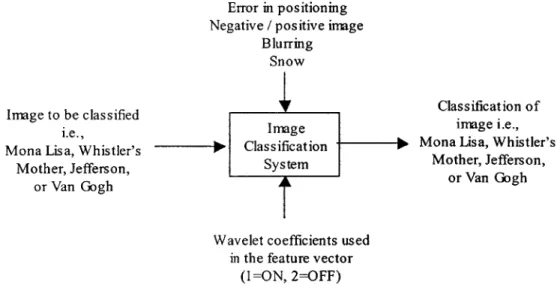
5.2.4 Robust Design Procedure
This section documents the application of Robust Design methods to select a set of wavelet coefficients for more effective classification of noisy images. The P-diagram for
Core Technology Through Enterprise Launch: A Case Study of Handwritten Signature Verification
Thesis, MIT's System Design and Management Program Burl Amsbury, June 2000
the system is depicted in Figure 11. The signal factor is the image to be classified. As discussed in Section 5.2.1, the ideal function of the system is to provide the title matching the signal image despite the noise factors.
The noise factors are the positioning errors, blurring, and snow discussed in Section
5.2.1. Rather than inducing noise through an outer array, we induced noise by
performing 20 replications of each type of image. The reason for this choice is that the "snow" is actually 322 separate noise factors so that the outer array would be excessively large.
As discussed in Section 5.2.3, the wavelet coefficients are the control factors that may be used to make the system more robust. The control factors each have two levels, level 1 implies the corresponding wavelet coefficient is "on" (included in the feature vector) and level 2 implies the corresponding wavelet coefficient is "off' (removed from the feature vector). In principle, there are 322 possible control factors to consider. To make the experiment size more manageable, we chose to investigate only the wavelet coefficients in the upper left 8x8 sub-matrix of the 32x32 matrix of wavelet coefficients. The number of control factors was thus reduced to 82 or 64. The number of features was further reduced to 63 to fit the experiment into the L64 (263) by eliminating the wavelet
coefficient in the lower right hand corner of the matrix.
Error in positioning Negative / positive image
Blurring Snow
Image to be classified Classification of
i.eImage image i.e.,
Mona Lisa, Whistler's - -- Classification Mona Lisa, Whistler's
Mother, Jefferson, System Mother, Jefferson,
or Van Gogh or Van Gogh
Wavelet coefficients used
in the feature vector (l=ON, 2=OFF)
![Figure 1. Digital Signatures [Turban 2000]](https://thumb-eu.123doks.com/thumbv2/123doknet/14495133.526692/14.918.138.774.104.999/figure-digital-signatures-turban.webp)