HAL Id: tel-02536478
https://tel.archives-ouvertes.fr/tel-02536478
Submitted on 8 Apr 2020HAL is a multi-disciplinary open access archive for the deposit and dissemination of sci-entific research documents, whether they are pub-lished or not. The documents may come from teaching and research institutions in France or abroad, or from public or private research centers.
L’archive ouverte pluridisciplinaire HAL, est destinée au dépôt et à la diffusion de documents scientifiques de niveau recherche, publiés ou non, émanant des établissements d’enseignement et de recherche français ou étrangers, des laboratoires publics ou privés.
David Gerault
To cite this version:
David Gerault. Security analysis of contactless communication protocols. Other [cs.OH]. Université Clermont Auvergne, 2018. English. �NNT : 2018CLFAC103�. �tel-02536478�
En premier lieu, je tiens à remercier Pascal, pour son encadrement tout au long de cette thèse. Il a dépassé de loin ce qu’on est en droit d’attendre d’un directeur de thèse. Il a toujours été disponible et extrêmement réactif, peu importe l’heure, pour travailler, relire ou conseiller. Après ces trois années, je n’ai toujours pas compris comment il arrivait encore à trouver le temps de dormir. J’ai beaucoup appris auprès de lui, tant sur le plan professionel que personnel. Merci Pascal.
Bien que Pascal soit mon directeur de thèse “officiel”, j’ai également eu la chance d’être en-cadré, pour la partie cryptanalyse et programmation par contraintes, par Christine et Marine. Je ne saurais assez les remercier pour la patience et la pédagogie dont elles ont fait preuve.
Au cours de cette thèse, j’ai eu l’occasion de travailler avec plusieurs co auteurs, que je remercie également: Cristina, Ioana (j’attends toujours mon nouveau chapeau en papier), Jean-Marc (grand maître des probabilités), Sébastien, Gildas, Siwei, Hardik, et Manik.
Bien sûr, je remercie Kasper Rasmussen, María Nayya-Plasencia, Yves Deville et Cédric Lau-radoux d’avoir bien voulu faire partie de mon jury.
Plus personellement, je remercie ma famille, en premier lieu ma grand mère, pour son soutien inconditionel tout au long de ce parcours: sans elle, cette thèse n’aurait peut être jamais vu le jour. Je remercie aussi ma mère Christine pour son aide et ses encouragements au cours de la période de rédaction, et mon frère Cyril.
Pendant ces trois années, j’ai pu compter sur le soutien et l’amitié de mon grand frère de thèse, Xavier. Des sessions de travail au tableau, ou il m’a initié aux joies de la sécurité prouvable, aux squattages de canapé mutuels, fous rires et autres chansons, cette thèse n’aurait pas été la même sans lui.
Et puis, bien sûr, après le grand frère de thèse, le petit: merci Matthieu, pour tes conseils avisés dans tous les domaines, les leçons de danse en Croatie, et tout le reste.
Je remercie également toute l’équipe du séminaire des doctorants pour cette expérience en-richissante: Hamadoun, Giacomo, Loukhmen, Sylvestre et Mouna.
Je remercie les collègues, plus particulièrement les membres (et anciens membres) du bureau B6, ainsi que les “stagiaires” (Marie-Caroline et Gauthier), et bien sûr Coco, pour la bonne humeur partagée au cours de ces années.
Merci à mes amis danseurs, pour les moments de lâcher prise Ô combien necessaire pendant cette longue aventure qu’est la thèse: Lélie (aka partner), Guillaume (dépositaire de bien trop de dossiers), Alex (courage pour la dernière ligne droite), Gaelle (bretonne chaotique), et tous les autres, et tout particulièrement Mathilde (qui m’a demandé plus souvent ou en était la rédaction que qui que ce soit, y compris Pascal) pour son incroyable joie de vivre, sa capacité à me faire rire en toutes circonstances, et ses incursions dans ma playlist.
Contents v
List of Figures ix
List of Tables xi
1 Introduction 3
1.1 Introduction . . . 3
1.2 Part 1: Distance Bounding Protocols . . . 5
1.2.1 Relay Attacks, or the Chess Grand Master Problem . . . 5
1.2.2 Solving the Chess Grand Master Problem: Distance Bounding Protocols . . . 6
1.2.3 Challenges and Contributions . . . 7
1.3 Part 2: Using Constraint Programming for Cryptanalysis . . . 7
1.3.1 Challenges and Contributions . . . 8
1.4 Outline . . . 8
1.5 Publications . . . 9
1.5.1 Presented in This Manuscript. . . 9
1.5.2 Other Publications . . . 9
2 Cryptographic Tools 11 2.1 Introduction . . . 11
2.2 Notations. . . 12
2.3 Encryption . . . 12
2.3.1 Symmetric Key Encryption Scheme . . . 12
2.3.2 Public Key Encryption Scheme . . . 13
2.3.3 IND-CCA2security . . . 13
2.4 Message Authentication . . . 14
2.4.1 Message Authentication Codes . . . 14
2.4.2 Digital Signature . . . 14
2.4.3 Group Signature . . . 14
2.4.4 Unforgeability . . . 15
2.5 Others. . . 17
2.5.1 Pseudo Random Functions . . . 17
2.5.2 Cryptographic Hash Function . . . 18
2.5.3 Zero-knowledge Proof of Knowledge . . . 18
2.5.4 Commitment . . . 18
2.5.5 Union Bound . . . 18
I Distance Bounding Protocols 19 3 Introduction to Distance Bounding 21 3.1 Introduction . . . 21
3.3 Threats Against Distance Bounding Protocols . . . 24
3.3.1 Distance Fraud (DF) . . . 25
3.3.2 Distance Hijacking (DH) . . . 25
3.3.3 Terrorist Fraud (TF) . . . 25
3.3.4 Terrorist frauds in noise resistant protocols . . . 26
3.3.5 PRF programming attacks . . . 27
3.4 Classical Protocols . . . 28
3.4.1 Brands and Chaum: Protocol 1 . . . 28
3.4.2 Brands and Chaum: Protocol 2 . . . 29
3.4.3 Brands and Chaum: Protocol 3 . . . 29
3.4.4 Reid et al.. . . 29
3.4.5 Fischlin and Onete . . . 30
3.5 Formalism for Distance Bounding . . . 31
3.5.1 Formal Definition of DB Protocols . . . 31
3.5.2 Formal models: The DFKO Framework . . . 33
3.5.3 Prover Anonymity. . . 39
3.5.4 Introduction to Proofs . . . 39
3.6 Conclusion. . . 40
4 Provably Secure Distance Bounding Protocols 41 4.1 Introduction . . . 41
4.2 Contributions . . . 42
4.3 Related Work. . . 43
4.4 Common Features and Differences of the Two Designs . . . 44
4.5 SPADE . . . 45
4.5.1 Protocol Description . . . 45
4.5.2 Properties . . . 47
4.5.3 The presence of the backdoor. . . 54
4.5.4 PRF Programming Attacks. . . 55
4.6 TREAD . . . 56
4.6.1 Protocol Description . . . 56
4.6.2 Protocols . . . 58
4.6.3 Properties . . . 59
4.6.4 Recent attacks against SPADE and TREAD . . . 64
4.7 Conclusion. . . 65
5 Hardware Based Terrorist Frauds 67 5.1 Introduction . . . 67
5.2 Directional Terrorist Frauds . . . 68
5.2.1 Attacks . . . 68
5.2.2 Discussion . . . 69
5.3 Impossibility Results for Terrorist Fraud Resistance . . . 70
5.3.1 The tamper-proof Device Attack . . . 70
5.3.2 Another Definition for Terrorist Fraud Resistance . . . 71
5.3.3 Black-box Provers and PUFs . . . 73
5.4 Conclusion. . . 73
II Using Constraint Programming for Cryptanalysis 75 6 Using Constraint Programming for Cryptanalysis 77 6.1 Introduction . . . 77
6.2 Related Key Differential Cryptanalysis. . . 80
6.2.2 Related Key Differential Cryptanalysis. . . 81
6.3 Constraint Programming . . . 82
6.4 Modelling the Search for Optimal Related Key Differential Characteristics on Word Oriented Block Ciphers With CP . . . 83
6.4.1 Search algorithm . . . 83
6.4.2 Modelling the Cipher Operations . . . 83
6.5 Conclusion. . . 87
7 Related Key Differential Cryptanalysis of AES with CP 89 7.1 Introduction . . . 89 7.2 The AES. . . 90 7.3 Our CP Models . . . 93 7.3.1 S1Basi c . . . 93 7.3.2 S1Di f f . . . 96 7.3.3 S1XOR . . . 100
7.3.4 Comparison of S1XORwith S1Di f f . . . 103
7.4 CP model for Step 2. . . 105
7.4.1 Variables . . . 105
7.4.2 Constraints . . . 105
7.5 A different two-step decomposition . . . 108
7.6 Conclusion. . . 110
8 Related Key Differential Cryptanalysis of Midori with CP 113 8.1 Introduction . . . 113
8.2 Midori . . . 115
8.3 CP Model for Step 1. . . 116
8.3.1 Variables . . . 117 8.3.2 Constraints . . . 118 8.4 Step 2 . . . 120 8.4.1 Variables . . . 120 8.4.2 Constraints . . . 121 8.5 Results . . . 122
8.6 Related Key Differential Attacks against Midori . . . 126
8.6.1 Related-Key Differential Attacks . . . 126
8.6.2 Midori64 . . . 126
8.6.3 Midori128 . . . 128
8.7 Conclusion. . . 128
9 Conclusions 129
A Rijndael’s Finite Field Multiplication Tables III
B The SBoxes of Midori128 VII
C Related-Key Differential Characteristics For Midori IX
C.1 Midori64 . . . IX C.1.1 Recovery of WK . . . IX C.1.2 Recovery of K0 . . . XVII C.2 Midori128 . . . XIX
3.1 Structure for terrorist fraud resistance . . . 23
3.2 Protocol: Hancke and Kuhn . . . 23
3.3 Classical countermeasure against terrorist fraud. . . 26
3.4 Protocol: Brands and Chaum 1 . . . 28
3.5 Protocol: Brands and Chaum 2 . . . 29
3.6 Protocol: Brands and Chaum . . . 30
3.7 Protocol: Reid et al .. . . 31
3.8 Protocol: Fischlin and Onete . . . 32
4.1 Protocols: SPADE . . . 46
4.2 Backdoor mechanism of SPADE . . . 47
4.3 Protocols: TREAD . . . 57
5.1 Directional terrorist fraud . . . 69
7.1 The AES. . . 91
7.2 AES state representation . . . 91
7.3 AES MixColumns matrix . . . 92
8.1 Midori state representation . . . 115
8.2 Midori . . . 115
8.3 Midori64 SBox . . . 116
8.4 Midori MixColumns matrix . . . 116
4.1 Comparison of privacy preserving protocols . . . 44
7.1 Comparison of S1Di f f and S1XOR . . . 104
7.2 Results of Choco for solving Step 2 . . . 107
7.3 Results with the shifted decomposition . . . 109
7.4 4-round related-key differential characteristic for AES-128. . . 110
7.5 14-round related-key differential characteristic for AES-256 . . . 110
8.1 Summary of the attacks against Midori . . . 114
8.2 Results for Midori64 . . . 123
8.3 16-round related-key differential characteristic for Midori64 . . . 124
8.4 Results for Midori128 . . . 124
8.5 20-round related-key differential characteristic for Midori128. . . 125 A.1 Lookup table for multiplication by 2 in Rijndael’s Galois field . . . III A.2 Lookup table for multiplication by 3 in Rijndael’s Galois field . . . IV A.3 Lookup table for multiplication by 9 in Rijndael’s Galois field . . . IV A.4 Lookup table for multiplication by 11 in Rijndael’s Galois field . . . IV A.5 Lookup table for multiplication by 13 in Rijndael’s Galois field . . . V A.6 Lookup table for multiplication by 14 in Rijndael’s Galois field . . . V B.1 The S0SBox of Midori128 . . . VII B.2 The S1SBox of Midori128 . . . VII B.3 The S2SBox of Midori128 . . . VIII B.4 The S3SBox of Midori128 . . . VIII C.1 16-round related-key differential characteristic for Midori64 . . . IX C.2 16-round related-key differential characteristic for Midori64 . . . X C.3 16-round related-key differential characteristic for Midori64 . . . X C.4 16-round related-key differential characteristic for Midori64 . . . XI C.5 16-round related-key differential characteristic for Midori64 . . . XI C.6 16-round related-key differential characteristic for Midori64 . . . XII C.7 16-round related-key differential characteristic for Midori64 . . . XII C.8 16-round related-key differential characteristic for Midori64 . . . XIII C.9 16-round related-key differential characteristic for Midori64 . . . XIII C.10 16-round related-key differential characteristic for Midori64 . . . XIV C.11 16-round related-key differential characteristic for Midori64 . . . XIV C.12 16-round related-key differential characteristic for Midori64 . . . XV C.13 16-round related-key differential characteristic for Midori64 . . . XV C.14 16-round related-key differential characteristic for Midori64 . . . XVI C.15 16-round related-key differential characteristic for Midori64 . . . XVI C.16 16-round related-key differential characteristic for Midori64 . . . XVII C.17 16-round related-key differential characteristic for Midori64 . . . XVII
C.18 16-round related-key differential characteristic for Midori64 . . . XVIII C.19 16-round related-key differential characteristic for Midori64 . . . XVIII C.20 16-round related-key differential characteristic for Midori64 . . . XIX C.21 20-round related-key differential characteristic for Midori128. . . XX C.22 20-round related-key differential characteristic for Midori128. . . XXI C.23 20-round related-key differential characteristic for Midori128. . . XXII C.24 20-round related-key differential characteristic for Midori128. . . XXIII C.25 20-round related-key differential characteristic for Midori128. . . XXIV C.26 20-round related-key differential characteristic for Midori128. . . XXV C.27 20-round related-key differential characteristic for Midori128. . . XXVI C.28 20-round related-key differential characteristic for Midori128. . . XXVII C.29 20-round related-key differential characteristic for Midori128. . . XXVIII C.30 20-round related-key differential characteristic for Midori128. . . XXIX C.31 20-round related-key differential characteristic for Midori128. . . XXX C.32 20-round related-key differential characteristic for Midori128. . . XXXI C.33 20-round related-key differential characteristic for Midori128. . . XXXII C.34 20-round related-key differential characteristic for Midori128. . . XXXIII C.35 20-round related-key differential characteristic for Midori128. . . XXXIV C.36 20-round related-key differential characteristic for Midori128. . . XXXV
Introduction
Authentication, in which an entity acknowledges another, is one of the most fundamental applica-tions of cryptography. Nowadays, authentication is increasingly often performed with contactless devices. Contactless authentication has become omnipresent in our world. Be it on the workplace, where access cards are replacing traditional keys to open the doors, or in our personal life, when we use contactless payment, most of us are regularly confronted to the contacless technologies. The large scale deployment of contactless authentication brings a strong incentive to scrutinize its security, as attacks against contacless communication protocols could impact all aspects of our lives, from professional (with access cards) to personal (with contactless payment). The goal of this thesis is to study the security of contactless communications, and in particular, contactless authentication.
1.1 Introduction
At the core of the security of contactless communications protocols lies the question of secure
authentication. Authentication is the set if techniques that permits an entity, referred to as the verifier, to validate the legitimacy of another entity, called the prover. Authentication is generally
performed for the prover to obtain access to a given service from the verifier, for instance, access to a building. Authentication protocols define the messages to be exchanged, and the acceptance rules. If we take a very simple scenario, in which a guard asks visitors a passwords before opening the door for then, the protocol is the following: the guard asks for the passwords, and the visitor responds. If the password given by the visitor is correct, then the guard opens the door. Otherwise, the guard chases the visitor. In this case, the prover is authenticated using something he knows. This is one of the three authentication mechanisms that are usually employed. Authentication is generally achieved by verifying something:
• The prover owns, for instance an access card; • the prover knows, for instance, a secret handshake; • the prover is, for instance, through his fingerprints.
Nowadays, in a contactless context, authentication is performed using a device the prover owns. For instance, in the Passive Keyless Entry and Start (PKES) technology, the traditional car key is replaced by a smart key. Smart keys are contactless devices: when a user holding one is close to the car, the car authenticates him as legitimate, and the door open. The technology that is used by contactless authentication protocols is called RFID, for Radio Frequency IDentification. An RFID exchange involves a tag, who plays the role of the prover, and a reader, who acts as the verifier. The most widely used kind of RFID tags is passive tags, which have no battery and re-ceive power from the verifier during the exchange. Their wide usage is due to their very limited cost (a few cents), compared to active tags, which have their own power source. Passive tags are typically less powerful, and it is believed that further improvements in technology will not aim at
making them more powerful, but cheaper [Juels, 2006]. Hence, authentication protocols designed for RFID need to face the challenge of being secure, while working with low computational power. The design of lightweight authentication protocols, suitable for low power RFID tags, is difficult: most proposals have serious security flaws [Avoine et al., 2015]. At the other end of the spectrum, modern smartphones are generally equipped with an NFC chip. NFC is a subset of RFID, which op-erates on short distances, and in which the entities involved are not restricted to being either a tag or a reader, but can be both. Therefore, computational power is no longer necessarily a limitation for contactless authentication protocols. It should however still be taken into account, depending on the application. Another challenge for the security of contactless protocols is that the commu-nications between the prover and the reader are sent in the air, so that any passive adversary with an antenna can read the messages exchanged. In contrast, eavesdropping wired communications requires more intrusive techniques, so that there is more surface of attacks on contactless devices. Hence, security is challenging to achieve for contactless authentication protocols.
The security of authentication protocols is defined with regards to an adversary, who tries to defeat the protocol. Defeating the protocol can have various meanings. The first one is of course obtaining unauthorised access to a service. The basic goal of an authentication protocol is to pre-vent this kind of attacks. However, other threats must be taken into account. For instance, legit-imate provers could try to cheat on the protocol, by helping an unauthorised accomplice to gain access to a service. For instance, consider a public transportation system, which is accessed to with a contactless card. The card authenticates the user. A user should not be able to permit other people, who did not pay for a card, to authenticate on their behalf and use the public transporta-tion. Finally, authentication protocols are sometimes required to protect the privacy of users. By privacy, we mean that, given the messages exchanged in two executions of the protocol, it should be difficult to determine whether the two executions were performed by the same user or not. We believe that privacy is highly relevant for contactless authentication. By relating two different ex-ecutions of a protocol to the same user, an adversary can possibly infer a lot about the private life of the user. For instance, if the transaction history of a contactless payment system is leaked, and if the adversary is capable of linking which execution corresponds to a given device, then he prac-tically obtains a location history of an individual. Indeed, if a honest user performed a contactless payment in a shop, then one can deduce he was in that shop. Location history can give a lot of in-formation about a person, and even when no identifier is attached to the logs, it can be sufficient for an attacker to obtain the home or work address, and even identity and social links, of an indi-vidual [Krumm, 2009]. Such information can be used for criminal purpose, such as robbery (while the user is at work), or blackmailing, for instance if the adversary identifies suspicious behaviour from the user. The more data the adversary has, the more he can infer about users. In particular, the adversary can be a big company, with access to the logs for several services. Therefore, we be-lieve that contactless authentication protocols should protect the privacy of their users, both with respect to external adversary who obtain some logs, and with respect to the verifiers themselves.
Authentication protocols, such as the Needham-Schroeder [Needham and Schroeder, 1978] protocols, use cryptographic building blocks, for encrypting or authenticating messages. Hence, there are two aspects to the security of an authentication protocol. The first one is the protocol in itself: if it has logical flaws, then it can be defeated. For instance, the Needham-Shroeder proto-cols are vulnerable to attacks: in [Denning and Sacco, 1981], the authors show how an adversary can defeat one of the protocols by replaying messages observed in a previous execution. The sec-ond aspect to the security of authentication protocols is the security of the cryptographic building blocks that compose it. For instance, if the protocol uses encryption, but the encryption scheme is not secure, then the protocol might be insecure. The search for vulnerabilities in cryptographic primitives is called cryptanalysis. In this thesis, we study both the security of the authentication protocols themselves, and of the cryptanalysis of the primitives that compose them. In the first part of this manuscript, we consider the case of distance bounding protocols, which were intro-duced to counter relay attacks, in which an adversary passively relays the messages exchanged between the prover and the verifier to illegally authenticate. In the second part, we propose to use
Constraint Programming (CP), a declarative programming paradigm, to evaluate the security of a cryptographic primitive called block ciphers.
1.2 Part 1: Distance Bounding Protocols
In this section, we introduce the first part of the thesis.
1.2.1 Relay Attacks, or the Chess Grand Master Problem
In 1976, Conway wrote the tale of "the little girl who played [...] against two Chess Bandmasters [...].
How was it that she managed to win one of the games? Anne-Louise played Black against Spassky. White against Fisher. Spassky moved first, and Anne-Louise just copied his move as the first move of her game against Fisher, then copied Fisher’s reply as her own reply to Spassky’s first move, and so on" [Conway, 1976]. This little story, known as the Chess Grand Master Problem, paved the way for a very rich area of research on relay attacks. It sets a very interesting problem: by simply relaying the moves from one player to the other without them being aware of the trick (for instance by having them sit in two different rooms, or playing the games via postal mail), someone can win or obtain a draw even without knowing the rules of chess.
However, relay attacks are not only a problem for chess players. An authentication protocol can be seen as a two-player game between a prover and a verifier. If an adversary relays the messages from one to the other, then he can win the game against the verifier and authenticate successfully. Eleven years after the first mention of the Chess Grand Master Problem, Desmedt ap-plied relay attacks, under the name of Mafia Fraud, against a security protocol [Desmedt et al., 1987]. In his example, the Mafia Fraud is performed against a payment protocol ran on a credit card. The victim wants to pay for his meal in a mafia owned restaurant. The employees of the restaurant, who are malicious, can hijack this payment, and relay it to buy expensive jewellery. To do so, the employees build a fake card reader and a fake card, that are able to communicate with each other from a distance, for instance via a radio link. One of the employees presents the fake reader to the victim for his payment, while a second one presents the fake card at the jewellery store. Both employees then just let the fake card and reader forward to each other the messages they receive. By this manipulation, the victim believes that his card is performing the payment protocol with the restaurant through the reader, when the card is actually communicating with the reader at the jewellery store due to the relaying. As for the Chess Grand Master Problem, the employees do not need to know anything about the secrets involved in the payment protocol in use, as long as they are able to relay the messages.
At the time when it was introduced, this attack was somehow mitigated by the fact that the card had to be inserted into a reader. Performing a relay attack required the victim to be willing to actively take part in the payment, which could limit the large scale applicability.
On the other hand, in contactless payment solutions, no action from the card owner is re-quired. It suffices that the card is close enough to a reader to start the protocol, as it automati-cally responds when it is solicited. Moreover, relaying messages does not require any suspicious equipment anymore, as smartphones can be used both as fake readers and as contactless payment means. Relay attacks can indeed be performed with off-the-shelf smartphones, on actual payment protocols, as shown by Vila and Rodriguez in [Vila and Rodríguez, 2015]. For instance, an attacker can approach his smartphone close enough to the pocket where the victim stores his card, instead of having to ask the victim to insert his card in a terminal. On the other side, an accomplice of the attacker would just present his own smartphone as a means of payment to the reader of the jew-ellery store, with both phones communicating through a network. Relay attacks were also used to steal cars, by relaying messages between a smart key and a car [Francillon et al., 2011]. Since then, significant research effort was put in solving relay attacks, in particular through distance bounding, for instance [Dürholz et al., 2011,Boureanu et al., 2015,Debant et al., 2018].
1.2.2 Solving the Chess Grand Master Problem: Distance Bounding Protocols
In their 1991 paper [Beth and Desmedt, 1991], Beth and Desmedt proposed to use time measure-ments for solving the Chess Grand Master Problem. The idea is to predefine a time interval t between each move. If one of the player does not play his move exactly t units of time after the previous move was played, then the other player detects there is a fraud. The first protocol relying on time measurements was introduced by Brands and Chaum in 1993 [Brands and Chaum, 1994]. The aim of this protocol is to estimate the distance between the prover and the verifier: in the event of a relay attack, it is likely that the victim is far away from the verifier. For instance, for a contact-less payment, the prover should be no further than a few centimetres from the reader. To bound the distance, the round trip time of the messages exchanged during the protocol is measured by the verifier. Typically, the verifier starts a clock, sends a cryptographic challenge, and stops the clock when it receives the response. The measured time∆t corresponds to twice the time it takes for a message to go from the prover to the verifier (or vice versa), plus the time taken by the prover to reply. To transform this time into a distance, it suffices to observe that no information can travel faster than the speed of light c. Hence, then d = ∆t·c
2 is an upper bound on the distance between the prover and the verifier. If the prover was any further than d, then it would mean that the mes-sages travelled faster than light, which is assumed impossible. Consequently, if d is short enough, according to a predefined, application dependant bound dmax, then the verifier gains the insur-ance that the prover is close enough. In other words, there is a time bound tmax, corresponding to a distance bound dmax, such that, if∆t> tmax, then the verifier rejects the prover. Time based distance bounding is currently the most studied solution to relay attacks.
However, it is noteworthy that other approaches were proposed, even though they are out of the scope of this thesis. In his seminal paper [Desmedt, 1988], Desmedt proposed that the prover computes his exact location on earth, signs it, and sends it to the verifier. The inconvenient to this approach is that it requires to trust the prover not to cheat. In addition, it requires a safe localisation system, which is not trivial to realise. In particular, using the GPS technology does not seem to be a robust solution [Gorjón and van Iterson, 2015]. Another option is to measure the strength of the signal received by the verifier [Krumm and Horvitz, 2004]: since it decreases as the distance increases, it gives indications on the distance of the prover. However, an attacker can amplify the signal to make the prover appear closer to the verifier, and defeat this system. Sim-ilarly, several solutions [Urien and Piramuthu, 2014] based on sensing the local environment (for instance the air temperature) were proposed, with the idea that if the prover was actually close to the verifier, then it would sense similar values. This approach however fails if the adversary is able to manipulate the value that is being sensed, which can be relatively easy. To prevent relay attacks, one can also isolate the prover inside a Faraday cage [Bengio et al., 1991] during the proto-col, to make sure that it cannot communicate with external entities. While efficient, this solution is not very user friendly, and limits the usability of the system. Finally, radio frequency fingerprint-ing [Rasmussen and Capkun, 2007] can be used. It identifies the devices based on variations in the signal features due to imperfections in the manufacturing process. However, such fingerprinting can be counterfeited [Danev et al., 2010], which renders this approach impractical.
Hence, distance bounding protocols seem to be the most promising option to defeat relay attacks. More than 40 distance bounding protocols exist in the literature [Brelurut et al., 2016,
Gildas et al., 2017], and most of them are vulnerable to at least one form of attacks. There ex-ists 4 main types of attacks against distance bounding protocols, some performed by outsiders, and some by legitimate users. These attacks are called Mafia Fraud (MF), Distance Fraud (DF), Distance Hijacking (DH) and Terrorist Fraud (TF). A mafia fraud is performed by an external ad-versary, who tries to authenticate in the presence of a far away honest prover. In a distance fraud, the attacker is a legitimate, far away prover, who tries to authenticate from a distance. In a distance hijacking, the legitimate, far away prover additionally uses honest provers, located close to the ver-ifier, to authenticate from a distance. Finally, in a terrorist fraud, he is helped by an accomplice, located close to the verifier.
1.2.3 Challenges and Contributions
Designing secure protocols is challenging, as shown by the small portion of distance bounding protocols in the literature that are resistant to all attacks. In a survey [Brelurut et al., 2016], we showed that among the 42 studied protocols, only 10 were not known to be vulnerable to at least one of the classical threats against distance bounding protocols. Formal security models, such as DFKO [Dürholz et al., 2011], provide a framework, in which the security of a protocol can be proven. This proof ensures that the protocol is secure with regards to the threats as defined in the model. However, it is notoriously difficult to formalise, terrorist fraud [Fischlin and Onete, 2013a]. Several formal models for terrorist fraud exist, e.g., [Dürholz et al., 2011,Boureanu et al., 2015,
Fischlin and Onete, 2013a], and most are designed specifically to prove the security of one par-ticular protocol. Provable terrorist fraud resistance generally involves the introduction of intricate mechanisms, or even backdoors [Fischlin and Onete, 2013a], that only serve for the proof to work. In the first part of this thesis, we study the problem of provably TF-resistant distance bounding, with or without privacy. We present two of our protocols, SPADE and TREAD [Bultel et al., 2016,
Avoine et al., 2017], which use novel techniques to attain provable terrorist fraud resistance, and various degrees of privacy. We then present a generic terrorist fraud, which contradicts the security proofs of most existing distance bounding protocols (to the best of our knowledge, it concerns all protocols but [Igier and Vaudenay, 2016]). This terrorist fraud exhibits attack possibilities that are not considered in the security models. We propose a new terrorist fraud definition, called One-Step Terrorist Fraud (OSTF) that accounts for this attack.
1.3 Part 2: Using Constraint Programming for Cryptanalysis
Authentication protocols, including distance bounding protocols, use cryptographic primitives as building blocks. One of the most versatile cryptographic primitives, which can be used to build other ones, is block ciphers. Block ciphers are symmetric encryption schemes, which encrypt mes-sage blocks of fixed size into ciphertexts of fixed size. Block ciphers can be used to build other use-ful cryptographic primitives, such as hash functions, pseudorandom functions and message au-thentication codes, which are defined in Chapter 2. We chose to study the security of the primitives used in contactless authentication protocols through the security of block ciphers. For a block ci-pher, being secure means that it is difficult for an adversary to recover the secret key used to en-crypt messages. The en-cryptanalysis of block ciphers is a very active research field. Cryptanalysing a block cipher typically involves bounding its security against generic, known attacks. For instance, one of the most famous type of attacks is differential cryptanalysis [Biham and Shamir, 1991]. In a differential attack, the adversary exploits biases in the distribution of the XOR difference of cipher-texts obtained by ciphering messages with a given XOR difference under the same key. An example of bias could be the following: if two messages differing only in the last bit are encrypted with the same key (under a given block cipher), then there is a high probability that the two resulting ci-phertexts will differ in their last bit too. Most of the time, the biases are not that obvious, so the cryptographers must study the propagation of plaintext differences through the cipher to deter-mine which difference propagation path, or differential characteristic, is the most likely to occur. By doing so, they estimate the probability of the best differential, i.e., an input difference mapped to an output difference. Modern block ciphers typically operate on 64- or 128-bit plaintexts, so that trying all possible input/output difference pairs is intractable. Hence, the search for optimal differential characteristics is difficult. However, a clever branch and bound approach can tackle it [Matsui, 1994]. It is however more difficult when we also consider differences in the key, as in
related key differential cryptanalysis. In a related-key differential attacks, the attacker can obtain
the encryption of messages of his choice with the secret key, but also with related keys, which have a relation of his choice with the secret key. This kind of attacks is particularly relevant when a block cipher is used to build other primitives. For instance, Microsoft’s Xbox uses a hash function built from a block cipher, TEA [Wheeler and Needham, 1995]. An attack on the hash function, due to a vulnerability of TEA in the related-key setting, permitted a hack of the system [ZDNet, 2002].
1.3.1 Challenges and Contributions
Performing related key differential cryptanalysis requires studying how differences in the mes-sage and in the key propagate through the ciphering process, in order to find the optimal related key differential characteristics. The size of the search space is very large: for AES, the encryption standard, the messages are 128 bits, and the key is 128 bits or more, so that exhaustive search is intractable. Dedicated search algorithms, which avoid exhaustive search by using strategies to reduce the search space, exist, e.g., [Biryukov and Nikolic, 2010, Fouque et al., 2013]. However, designing such algorithms is time consuming, and results in large and difficult to maintain code. On the other hand, declarative paradigms, in which the developer simply states the problem, and the search is left to a dedicated solver, are sometimes used for cryptanalysis [Mouha et al., 2012,
Sun et al., 2014,Derbez and Fouque, 2016]. The most used paradigm is Mixed Integer Linear Pro-gramming (MILP).
In the second part of this thesis, we use Constraint Programming (CP) to perform related key differential cryptanalysis on two block ciphers: the standard AES [Daemen and Rijmen, 2002] and the lightweight block cipher Midori [Banik et al., 2015]. Constraint programming is a declarative framework which was previously not used for cryptanalysis. It is more generic than MILP: in MILP, the problems need to be expressed as set of linear equations, while in CP, there is no such limita-tion. The resolution methods are also different.
1.4 Outline
In Chapter 2, we introduce the notations we use through the thesis, as well as the cryptographic primitives that we use and their security properties, and some useful mathematical notions. In Chapter 3, we give an introduction to distance bounding protocols, and define the associated at-tacks. We present the DFKO [Dürholz et al., 2011] framework, in which we perform our security proofs, and the proof methodology. In Chapter 4, we present two of our distance bounding proto-cols: SPADE [Bultel et al., 2016] and TREAD [Avoine et al., 2017]. The research problem that these protocols aim to solve is provable terrorist fraud resistance, and how to combine it with privacy. SPADE is fully anonymous, and uses a previously known mechanism to grand provable terrorist fraud resistance. TREAD has 3 instances, two of which are concerned with privacy and anonymity, and implements a novel technique for provable terrorist fraud resistance. We give the security proofs of both protocols. In Chapter 5, we present an impossibility result for terrorist fraud re-sistance, in the form of a generic terrorist fraud. This attacks works for every protocols in which the prover can be cloned. Provers can typically always be cloned, unless hardware measures make them physically uncloneable, for instance by using a temper-proof device which prevents the user from accessing the secret key, or by using physically uncloneable function. We then define a new terrorist fraud resistance notion, which takes this impossibility result into account. Chapter 6 in-troduces the search for optimal related key differential characteristics using constraint program-ming. We present the problem that we solve, the methodology that we use, as well as the tools and the experimental setup. Chapter 7 presents our CP models and results for the related key crypt-analysis of the AES. We build up from a naive modelling, with which the search is intractable, to an efficient model, using a different decomposition, that performs significantly better (less than 24 hours versus several weeks) than the state of the art methods. Moreover, we find related key differ-ential characteristic which are better (in terms of probability) than the ones that were previously published. Finally, in Chapter 8, we present our CP models for the related key cryptanalysis of Midori [Banik et al., 2015], a lightweight block cipher [Gérault and Lafourcade, 2016] that comes in two versions: Midori64 and Midori128. Using CP, we find the optimal related key differential characteristics for both versions within a few minutes. With these related-key differential charac-teristics, we present key recovery attacks with practical complexity: 236operations for Midori64, and 244for Midori128.
1.5 Publications
In this section, we present the list of the articles we published during this thesis. 1.5.1 Presented in This Manuscript
The articles that we present in this manuscript are the following:
A Prover-Anonymous and Terrorist-Fraud Resistant Distance-Bounding Protocol [Bultel et al., 2016] A Terrorist-fraud Resistant and Extractor-free Anonymous Distance-bounding Protocol [Avoine et al., 2017] Fine-Grained and Application-Ready Distance-Bounding Security [Boureanu et al., 2018]
Constraint Programming Models for Chosen Key Differential Cryptanalysis [Gerault et al., 2016] Revisiting AES related-key differential attacks with constraint programming [Gérault et al., 2018] Combining Solvers to Solve a Cryptanalytic Problem [Gerault et al., 2017a]
Using Constraint Programming to solve a Cryptanalytic Problem [Gerault et al., 2017b] Related-Key Cryptanalysis of Midori [Gérault and Lafourcade, 2016]
1.5.2 Other Publications
Some of our publications are left out of this thesis. We briefly present them. Their titles and ab-stracts are given below.
Survey of Distance Bounding Protocols and Threats [Brelurut et al., 2016]: NFC and RFID are technologies that are more and more present in our life. These technologies allow a tag to communicate without contact with a reader. In wireless communication an intruder can always listen and forward a signal, so he can mount a so-called worm hole attack. In the last decades, several Distance Bounding (DB) protocols have been introduced to avoid such attacks. In this context, there exist several threat models: Terrorist Fraud, Mafia Fraud, Dis-tance Fraud etc. We first show the links between the existing threat models. Then we list more than forty DB protocols and give the bounds of the best known attacks for different threat models. In some cases, we explain how we are able to improve existing attacks. Then, we present some advice to the designers of the DB protocols and to the intruders to mount some attacks.
Breaking and fixing the HB+DB protocol [Boureanu et al., 2017]: The HB protocol and its HB+ successor are lightweight authentication schemes based on the Learning Parity with Noise (LPN) problem. They both suffer from the so-called GRS-attack whereby a man-in-the-middle (MiM) adversary can recover the secret key. At WiSec 2015, Pagnin et al. proposed the HB+DB protocol: HB+ with an additional distance-bounding dimension added to de-tect and counteract such MiM attacks. They showed experimentally that HB+DB was resis-tant to GRS adversaries, and also advanced HB+DB as a distance-bounding protocol, dis-cussing its resistance to worst-case distance-bounding attackers. In this paper, we exhibit flaws both in the authentication and distance-bounding layers of HB+DB; these vulnerabil-ities encompass practical attacks as well as provable security shortcomings. First, we show that HB+DB may be impractical as a secure distance-bounding protocol, as its distance fraud and mafia-fraud security-levels scale poorly compared to other distance-bounding protocols. Secondly, we describe an effective MiM attack against HB+DB: our attack refines the GRS-strategy and still leads to key-recovery by the attacker, yet this is not deterred by HB+DB’s distance bounding. Thirdly, we refute the claim that HB+DB’s security against pas-sive attackers relies on the hardness of the LPN problem. We also discuss how (erroneously) requiring such hardness, in fact, lowers HB+DB’s efficiency and its resistance to authentica-tion and distance-bounding attacks. Drawing on HB+DB’s design flaws, we also propose a
new distance-bounding protocol – BLOG. It retains parts of HB+DB, yet BLOG is provably secure, even – in particular – against MiM attacks. Moreover, BLOG enjoys better practical security (asymptotic in the security parameter).
Verifiable Private Polynomial Evaluation [Bultel et al., 2017]: Delegating the computation of a polynomial to a server in a verifiable way is challenging. An even more challenging problem is ensuring that this polynomial remains hidden to clients who are able to query such a server. In this paper, we formally define the notion of Private Polynomial Evaluation (PPE). Our main contribution is to design a rigorous security model along with relations between the different security properties. We define polynomial protection (PP), proof unforgeability (UNF), and indistinguishability against chosen function attack (IND-CFA), which formalises the resistance of a PPE against attackers trying to guess which polynomial is used among two polynomials of their choice. As a second contribution, we give a cryptanalysis of two PPE schemes of the literature. Finally, we design a PPE scheme called PIPE and we prove that it is PP-, UNF- and IND-CFA-secure under the decisional Diffie-Hellman assumption in the random oracle model.
Analysis of AES, SKINNY, and Others with Constraint Programming [Sun et al., 2017]: Search for different types of distinguishers are common tasks in symmetric key cryptanalysis. In this work, we employ the constraint programming (CP) technique to tackle such problems. First, we show that a simple application of the CP approach proposed by Gerault et al. leads to the solution of the open problem of determining the exact lower bound of the number of ac-tive S-boxes for 6-round AES-128 in the related-key model. Subsequently, we show that the same approach can be applied in searching for integral distinguishers, impossible differen-tials, zero-correlation linear approximations, in both the single-key and related-(twea)key model. We implement the method using the open source constraint solver Choco and ap-ply it to the block ciphers PRESENT, SKINNY, and HIGHT (ARX construction). As a result, we find 16 related-tweakey impossible differentials for 12-round SKINNY-64-128 and con-struct an 18-round attack on SKINNY-64-128 (one target version for the crypto competition https://sites.google.com/site/skinnycipher announced at ASK 2016). Moreover, we show that in some cases, when equipped with proper strategies (ordering heuristic, restart and dynamic branching strategy), the CP approach can be very efficient. Therefore, we suggest that the constraint programming technique should become a convenient tool at hand of the symmetric-key cryptanalysts.
Cryptographic Tools
In this section, we present the mathematical and cryptographi notions that we use in our algorithms and proofs.
Contents
2.1 Introduction . . . 11
2.2 Notations. . . 12
2.3 Encryption . . . 12
2.3.1 Symmetric Key Encryption Scheme . . . 12
2.3.2 Public Key Encryption Scheme . . . 13
2.3.3 IND-CCA2security . . . 13
2.4 Message Authentication . . . 14
2.4.1 Message Authentication Codes . . . 14
2.4.2 Digital Signature . . . 14
2.4.3 Group Signature . . . 14
2.4.4 Unforgeability . . . 15
2.5 Others. . . 17
2.5.1 Pseudo Random Functions . . . 17
2.5.2 Cryptographic Hash Function . . . 18
2.5.3 Zero-knowledge Proof of Knowledge . . . 18
2.5.4 Commitment . . . 18
2.5.5 Union Bound . . . 18
2.1 Introduction
In Part I of this manuscript, we are concerned with provable security. In provable security, the ad-versary is assumed to be polynomially bounded, i.e., he can only perform a number of operations that is a polynomial in a security parameter λ. Hence, a scheme is said to be secure if the success probability of an adversary diminishes exponentially as the security parameter increases. In other words, a scheme is secure if the success probability of any adversary is a negligible function of the security parameter. Intuitively, a negligible function is a function that goes exponentially smaller as the security parameter increases. Stated differently, the function is negligible if it is smaller than the inverse of any polynomial in λ. More formally:
Definition 1. Negligible function A function f : N → R+is negligible if for all positive integer c, there exists an integer Nc, such that for all x > Nc, f (x) < xc.
We use the notation neg l (λ) to denote the set of negligible functions of λ.
For instance, a distance bounding protocol uses cryptographic keys and nonces (random num-bers). Their sizes, as well as the number of rounds, are chosen to be polynomial in the security parameter. Similarly, for the primitives we define in this section, the size of the keys is dependant on the security parameter.
In order to prove that the success probability of an adversary is negligible, we sometimes need to use abstractions, such as the Random Oracle Model (ROM). The ROM is an abstraction in which there exists a random oracleH(·), which maintains a listHL: this oracle is used to produce random values from its input. When querried with a given input i , it does the following:
• If i is querried for the first time, return a random value o and add the couple (i ,o) to a listHL • If i was querried before, i.e., ∃(i′,o) ∈HL,i = i′, then it returns the corresponding o.
In other words, it behaves like a hash function that returns truely random values. A hash function in the random oracle model is simply a hash function implemented with a random oracle.
After this brief introduction to provable security, we define the notations, cryptographic primi-tives and mathematical notions that we use. Note that a more complete definition of most of these primitives can be found in [Goldreich, 2006].
2.2 Notations
We define the notations that we use through the thesis. ⊕ is the bitwise xor operation.
a||b denotes the concatenation of two bitstrings a and b.
¯ ¯ ¯ ¯ ¯ ¯
i ∈[0;n](ai) denotes the concatenation of the values ai, for i from 0 to n.
x← E denotes the uniform random choice of a value from the set E.$
HW(a) denotes the hamming weight of a bitstring a, i.e., the number of ones in a. HD(a,b) denotes the hamming distance between two bitstrings a and b, i.e., HW(a ⊕ b). #X denotes the cardinality of the set X.
Pr [E] denotes the probability for the event E to occur.
2.3 Encryption
Encryption schemes use a cryptographic key to transform a message m into a ciphertext c, such that only the recipient, knowing the appropriate decryption key, can recover m from c. Encryption schemes can be symmetric or public key. If the scheme is symmetric, the encryption and decryp-tion key are the same. If the scheme is public key, the messages are encrypted with a public key, and decrypted with a secret key..
2.3.1 Symmetric Key Encryption Scheme
A symmetric key encryption scheme is an encryption scheme in which the same key is used for encryption and decryption.
Definition 2 (Symmetric Key Encryption). A symmetric key encryption schemeSKEis a triplet of algorithms (SKE.gen,SKE.enc,SKE.dec) such that :
SKE.gen(1λ): returns a secret key x.
SKE.encx(m): returns a ciphertext c from the message m and the key x. SKE.decx(c): returns the plaintext m such thatE.encx(m) = c.
2.3.2 Public Key Encryption Scheme
In a public key encryption scheme, the key used to encrypt the messages is public: everyone can use it to encrypt a message. On the other hand, the decryption key is secret.
Definition 3 (Public Key Encryption). A public key encryption schemePKEis defined by:
PKE.gen(1λ) returns a public and private key pair (pk, x).
PKE.encpk(m) returns the ciphertext c from the message m and the public key pk. PKE.decx(c) returns the plaintext m such thatE.encpk(m) = c.
2.3.3
IND
-CCA2
securityTheIND-CCA2notion was formalized for public key encryption schemes in [Bellare et al., 1998], and was later extended to symmetric schemes in [Bellare and Namprempre, 2000]. The authors of [Bellare and Namprempre, 2000] consider a notion they callIND-CCA, but mention in the paper that it corresponds to the notion ofIND-CCA2used for public key encryption.
Definition 4 (IND-CCA2- Symmetric key). LetSKE= (SKE.gen,SKE.enc,SKE.dec) be a symmetric
key encryption scheme. SKE is said to be indistinguishable against adaptive chosen ciphertext
attack (IND-CCA2) when for any adversary A = (A0,A1), the advantage AdvINDA,SKE-CCA2(1
λ) = ¯ ¯ ¯ ¯ ¯ Pr " k←SKE.gen(1λ),b $ ← {0,1}
b′← ASKE.enck(LRb),SKE.deck
0 (λ) : b = b′ # −12 ¯ ¯ ¯ ¯ ¯
is negligible, where the oraclesSKE.enck(LRb),SKE.deckare defined as:
SKE.enck(LRb(m0,m1)): returns SKE.enck(mb) on the message pair (m0,m1), for a random but
fixed bit b.
SKE.deck(c): returns ⊥ if c has been generated bySKE.enck(LRb), andSKE.deck(c) otherwise. Definition 5 (IND-CCA2- Public key). LetPKE= (PKE.gen,PKE.enc,PKE.dec) be a public key
encryption scheme. PKEis said to be indistinguishable against adaptive chosen ciphertext attack
when for any adversary A = (A0,A1), the advantage
AdvINDA,PKE-CCA2(1 λ) = ¯ ¯ ¯ ¯ ¯ Pr " (pk, x) ←PKE.gen(1λ),b $ ← {0,1}
b′← APKE.encpk(LRb),PKE.dec
x(pk,λ) : b = b′ # −12 ¯ ¯ ¯ ¯ ¯
is negligible, where the oraclesPKE.encpk(LRb),PKE.decxare defined as:
PKE.encpk(LRb(m0,m1): returnsPKE.encpk(mb) on the message pair (m0,m1), for a random but
fixed bit b.
PKE.decx(c): returns ⊥ if c has been generated byPKE.encpk(LRb) returns ⊥, andPKE.decx(c)
2.4 Message Authentication
We consider three kinds of message authentication schemes:MAC, digital signature and dynamic group signature. In aMAC, a tag authenticating a message is generated and verified with the same secret key. In digital signature schemes, the signing key is private and known only to the signer, whereas the verification key is public. In group signature schemes, each member of the group knows a private signature key, and a public verification key permits to verifiy that the signature was generated by a member of the group. We sometimes abuse language and consider MAC schemes as (symmetric) signature schemes.
The security properties we use are the unforgeability, and the anonymity for group signatures. 2.4.1 Message Authentication Codes
A MAC is an authentication scheme in which the keys used to authenticate and verify identical and secret.
Definition 6 (Message Authentication Code). A message authentication codeMACis a triplet of algorithms (MAC.gen,MAC.tag,MAC.ver) such that :
MAC.gen(1λ): returns a secret key x.
MAC.tagx(m): returns a tag σ from the message m and the key x. MAC.verx(s,m): returns a verification bit v from the tag σ and the key x. 2.4.2 Digital Signature
Digital signatures use a secret signature key, and a public verification key.
Definition 7 (Digital Signature). A digital signature schemeSIGis a composed of the three following algorithms: (SIG.gen,SIG.sig,SIG.ver), such that :
SIG.gen(1λ): returns a signature/verification key pair (x,vk), where x is secret andvkis public. SIG.sigx(m): returns a signature σ from the message m and the signing key x.
SIG.vervk(s,m): returns a verification bit v from the signature s and the verification keyvk. 2.4.3 Group Signature
In a group signature scheme, the signers are treated as a group. Each member of the group has a personal signing key that he uses to sign a message anonymously on behalf of the group. An entity, called group manager, has the power to open, i.e., deanonymise, a signature. A more complete definition is given in [Bellare et al., 2003].
Definition 8 (Group Signature). A group signature schemeG-SIG, using a user list Ui, is defined by:
G.gen(1λ) returns a group/master key pair (gpk,msk) and sets the user listUL. The verification key
isgpk.
G.sigx
i(m) returns a group signature σ on the message m, such thatG.opemsk(σ,m,UL,gpk) = Ui
G.vergpk(σ,m) outputs 1 if and only if σ is valid for the message m and the key xiof a non-revoked
user, and 0 otherwise.
A group signature can be dynamic. In this case, new members can be added to the group, and members can be revoked. More specifically, an entity, called a group manager, adds new members. Additionally, a revocation algorithm is needed. A revoked user listRLis added, as well as the following algorithms:
G.joinmsk(i ,gpk,UL) is a protocol between a user Ui(usinggpk) and a group manager GM (using gpkandmsk). Uiinteracts with GM to get his signing key xi, while GM outputs a valueregi and adds UitoUL.
G.revmsk(i ,RL,UL,gpk) computes revocation logsrevi for user Ui, usingregi,gpkandmskand moves UifromULtoRL.
The verification algorithm is modified to include the revoked user list:
G.vergpk(σ,m,RL) outputs 1 if and only if σ is valid for the message m and the key xi of a non-revoked user, and 0 otherwise.
In this thesis, we only use dynamic group signature schemes. When we mention a group sig-nature scheme, we implicitely assume that it is dynamic.
2.4.4 Unforgeability
The unforgeability property of a message authentication scheme states that an adversary cannot generate a valid signature or MAC without knowing the corresponding key. For digital signatures and MAC schemes, this notion is known as Existential UnForgeability under Chosen Message At-tack (EUF-CMA). For group signatures, a stronger notion (full-traceability) exists: it states that no user or coallition therof can produce a signature that opens to the identity of a honest user. This distinction needs to be introduced, since in the context of a group signature, a user might try to forge a signature on bealf of another one, for instance to build an alibi. This dishonest user knows more information than a classical adversary, since he knows a singing key. TheEUF-CMA no-tion was first defined for digital signatures in [Goldwasser et al., 1983], and then for MAC schemes in [Bellare et al., 1994]. Full traceability for group signatures was defined in [Bellare et al., 2005].
The unforgeability experiment is defined as follows:
Definition 9 (EUF-CMA(MAC)). Let A be an adversary, and MAC be a MAC scheme. In the
ExpForgeA,MAC(λ) experiment, the challenger creates (x) usingMAC.gen(1λ), initializes an empty list Σ, and gives A access to a signing oracle:
MAC.Tag(·,·) returns a MAC σ, usingMAC.tagxm and adds the pair (m,σ) toΣ.
Then, A outputs a message m∗and a signatureσ∗. A wins (and the challenger outputs 1) if the
two following conditions are satified: (m∗,σ∗) 6∈ΣandMAC.verx(s,m) = 1
The advantage of an adversary A in the unforgeability experiment,AdvForgeMAC(λ), is defined as AdvForgeA,MAC(λ) =Pr[Exp
Forge
A,MAC(λ) = 1]
and the advantage on the experiment as
AdvForgeMAC(λ) = max A ∈Poly(λ){Adv
Forge
A,MAC(λ)}.
A MAC schemeMACis unforgeable ifAdvForgeMAC(λ) is negligible.
For digital signature schemes, the security game is essentially the same, except that A has access to the verification keyverk, since it is public.
Definition 10 (EUF-CMA(digital signature)). Let A be an adversary, andSIGbe a digital signature scheme. In theExpForgeA,SIG(λ) experiment, the challenger creates (x, pk) usingSIG.gen(1λ), sends pk
to A , initializes an empty listΣwhich contains all oracle produced signatures, and gives A access
to a signing oracle:
SIG.Sign(·,·) returns a signature σ, usingSIG.sigx(m) and adds the pair (m,σ) toΣ.
Then, A outputs a message m∗and a signatureσ∗. A wins (and the challenger outputs 1) if the
two following conditions are satified: (m∗,σ∗) 6∈ΣandSIG.verx(s,m) = 1
The advantage of an adversary A in the unforgeability experiment,AdvForgeSIG (λ), is defined as AdvForgeA,SIG(λ) =Pr[ExpForgeA,SIG(λ) = 1]
and the advantage on the experiment as
AdvForgeSIG (λ) = max A ∈Poly(λ){Adv
Forge
A,SIG(λ)}.
A digital signature schemeSIGis unforgeable ifAdvForgeSIG (λ) is negligible.
For dynamic group signature schemes, the experiment is a bit more complex, since it includes attacks from group members. It is defined as full traceability.
Definition 11 (Full Traceability (Dynamic Group Signatures)). LetG-SIG= (G.gen,G.sig,G.ver) be
a group signature scheme. In the full traceability experiment for an adversary A ExpTraceA,G-SIG(λ), the
challenger creates (UL,RL,msk,gpk) usingG.gen(1λ), givesgpkto A , and sets the listsCUandΣ,
for corrupted users and oracle-issued signatures. During a first phase, phase A has access to the following oracles:
G.joinmsk(i ,gpk,UL) creates UiusingG.joinmsk(ID,gpk,UL).
G.joinCmsk(i ,gpk,UL,RL) creates a corrupted user Uiby usingG.joinmsk(ID,gpk,UL), adding Uito
CUand returning its secret key xito A .
G.join(i ) simulates the corruption of a user Ui by returning its secret key xito A and adding it to CU.
G.revmsk(i ,RL,UL,gpk) revokes UiusingG.revmsk(ID,RL,UL,gpk).
G.sigxi(m) returns a signature σ on behalf of Ui, usingG.sigxi(m) and adds the pair (m,σ) toΣ.
G.opemsk(σ,m,UL,gpk) opens a signature σ and returns Uito A , usingG.opemsk(σ,m,UL,gpk).
Then, during a guessing phase, A outputs a message m∗and a signatureσ∗. A wins (and the
challenger outputs 1) if and only if:
(m∗,σ∗) 6∈ΣandG.vergpk(σ∗,m∗,RL) = 1, G.opemsk(σ∗,m∗,UL,gpk) 6∈CU\RL.
The advantage of an adversary A in the full traceability experiment,AdvTraceG-SIG(λ), is defined as AdvTraceA,G (λ) =Pr[ExpTraceA,G (λ) = 1]
and the advantage on the experiment as
AdvTraceG (λ) = max A ∈Poly(λ){Adv
Trace
A,G (λ)}.
Anonymity
Anonymity is a property of group signature schemes: if a group signature scheme is anonymous, then no one, except for the opening authority, can find out which user produced a signature within a group. The anonymity experiment for dynamic group signature schemes is defined as follows. Definition 12. LetG-SIG= (G.gen,G.sig,G.ver) be a dynamic group signature scheme. In the anonymity
experiment for an adversary A ExpAnonA,G-SIG(λ), the challenger first usesG.gen(1λ) to create the lists
and keys (UL,RL,msk,gpk), givesgpkto A , and sets the listsCUandΣ. During a first phase, A has access the following oracles:
G.joinmsk(i ,gpk,UL) creates UiusingG.joinmsk(ID,gpk,UL).
G.joinCmsk(i ,gpk,UL,RL) creates a corrupted user Ui by usingG.joinmsk(ID,gpk,UL), adding Uito
CUand returning its secret key xito A .
G.join(i ) Simulates the corruption of a user Ui by returning its secret key xi to A and adding it to CU.
G.revmsk(i ,RL,UL,gpk) revokes UiusingG.revmsk(ID,RL,UL,gpk).
G.sigxi(m) returns a signature σ on behalf of Ui, usingG.sigxi(m) and adds the pair (m,σ) toΣ.
G.opemsk(σ,m,UL,gpk) opens a signature σ and returns Uito A , usingG.opemsk(σ,m,UL,gpk). A selects two identities (ID0,ID1). IfID0andID1∈CU, the challenger stops. Otherwise, he picks
b← {0,1}.$
Then, during the guessing phase, A cannot useG.corandG.rev on ID0 orID1 anymore, but
gains access to a new oracle:
G.sigb simply returnsG.sigsskIDb(m). The signature produced by this oracle cannot be theG.ope
oracle.
A outputs b′and the challenger returns the boolean value (b = b′). A’s advantage in this experiment is defined as
AdvAnonA,G (λ) = ¯ ¯ ¯ ¯ Pr[ExpAnonA,G (λ) = 1] − 1 2 ¯ ¯ ¯ ¯
and the advantage on the experiment as
AdvAnonG (λ) = max A ∈Poly(λ){Adv
Anon
A,G(λ)}.
A group signatureG-SIGis anonymous ifAdvAnonG-SIG(λ) is negligible.
2.5 Others
In this section, we present pseudorandom functions, hash functions, zero-knowledge proofs of knowledge, commitment schemes, and the union bound.
2.5.1 Pseudo Random Functions
A pseudo random function (PRF) is a keyed function the output of which cannot be efficiently distinguished from that of a random function on the same domain. This primitive was defined, and an example (GGM) was given, in [Goldreich et al., 1986].
Definition 13 (Pseudo Random Function). A family of functions PRFs: {0,1}k → {0,1}l, indexed by
• There is an efficient algorithm (polynomial in the security parameter) for computing PRFs(x),
given s and x;
• For any A given oracle access to the function, the probability of distinguishing PRFs(·) from a
random function1 f : {0, 1}k→ {0,1}l is negligible.
2.5.2 Cryptographic Hash Function
Definition 14 (Hash Function). A hash function family H is a function H : K × M → Y, where K is a
key space, M is a message space and Y is a digest space.
A cryptographic hash function HKis required to be collision resistant: for an adversary know-ing the key K, it should be difficult to find two messages that have the same image. The latest standard hash function is SHA-3 [Bertoni et al., 2013].
Definition 15. Collision Resistance A hash function family H is collision resistant if the probability Pr [K← K;(M,M$ ′) ← A (K) : M 6= M′∧ HK(M) = HK(M′) is negligible.
2.5.3 Zero-knowledge Proof of Knowledge
Zero-knowledge proofs of knowledge were introduced in [Goldwasser et al., 1989]. A zero-knowledge
proof of knowledge schemeZKPis a protocol that allows a prover to convince a verifier that he
knows a secrete value x, such that a relation r , involving x, is true. This is denotedZKP[x : r ]. The properties of a ZKP are the following.
Correctness: If the prover knows the solution x, then he is able to convince the verifier. Soundness: If r is wrong, then the prover is not able to convince the verifier.
Validity: If the prover does not know the secret x, then he is not able to convince the verifier. Zero-knowledge: No information about the secret x leaks during the protocol.
2.5.4 Commitment
A commitment scheme permits a prover to commit to a value v, without revealing v. Later, he can
open this commitment, i.e., reveal v, and prove that v is the value that was used to generate the
commitment. A simple commitment is a hash v: it does not allow to recover v, but can be easily verified once v is revealed. Commitment schemes were first formalised in [Brassard et al., 1988]. Definition 16 (Commitment Scheme). A Commitment schemeCOMis composed of a pair of algo-rithms (COM.commit,COM.open) such that:
COM.commit(v,r ): returns a commitment c to the value v, using the random value r . COM.open(c,r ): returns the value v such thatCOM.commit(v,r ) = c.
2.5.5 Union Bound
The union bound is a useful upper bound for the probability of an event occuring at least once [Kallenberg, 2002]. It states that, for any finite or countable set of events, the probability that at least one of the events
happens is no greater than the sum of the probabilities of the individual events. More formally, for a set of events {Ei|i ∈ [1;k]}, we have
Pr [[k i =0 Ei] ≤ k X i =0 Pr [Ei].
Introduction to Distance Bounding
Contents
3.1 Introduction . . . 21
3.2 General Structure of Distance Bounding Protocols . . . 22
3.3 Threats Against Distance Bounding Protocols . . . 24
3.3.1 Distance Fraud (DF) . . . 25
3.3.2 Distance Hijacking (DH). . . 25
3.3.3 Terrorist Fraud (TF) . . . 25
3.3.4 Terrorist frauds in noise resistant protocols . . . 26
3.3.5 PRF programming attacks . . . 27
3.4 Classical Protocols . . . 28
3.4.1 Brands and Chaum: Protocol 1 . . . 28
3.4.2 Brands and Chaum: Protocol 2 . . . 29
3.4.3 Brands and Chaum: Protocol 3 . . . 29
3.4.4 Reid et al.. . . 29
3.4.5 Fischlin and Onete . . . 30
3.5 Formalism for Distance Bounding . . . 31
3.5.1 Formal Definition of DB Protocols . . . 31
3.5.2 Formal models: The DFKO Framework . . . 33
3.5.3 Prover Anonymity. . . 39
3.5.4 Introduction to Proofs . . . 39
3.6 Conclusion . . . 40
In a relay attack, an intruder defeats an authentication protocol by relaying the messages between the verifier and a far away prover. Distance bounding protocols are a classical countermeasures to relay attacks. In this chapter, we present the threats associated to distance bounding, and some protocols of the literature. We then present the formalism associated with distance bounding pro-tocols, as well as the DFKO [Dürholz et al., 2011] security model, which we use to prove the security of our protocols, which are presented in Chapter 4.
3.1 Introduction
Distance bounding protocols were introduced to counter relay attacks, in which an adversary relays the messages between a prover and a verifier. Since the introduction of the first proto-col [Brands and Chaum, 1994], many designs for distance bounding appeared in the literature. In a survey [Brelurut et al., 2016], we showed that among the 42 studied protocols, only 10 had


![Figure 3.4: The first Distance Bounding protocol proposed by Brands and Chaum in [Brands and Chaum, 1994]](https://thumb-eu.123doks.com/thumbv2/123doknet/14592081.542550/40.892.132.742.714.1097/figure-distance-bounding-protocol-proposed-brands-chaum-brands.webp)
![Figure 3.5: The second Distance Bounding protocol proposed by Brands and Chaum in [Brands and Chaum, 1994]](https://thumb-eu.123doks.com/thumbv2/123doknet/14592081.542550/41.892.232.679.358.633/figure-second-distance-bounding-protocol-proposed-brands-brands.webp)
![Figure 3.6: The third Distance Bounding protocol proposed by Brands and Chaum in [Brands and Chaum, 1994], in which COM is a commitment scheme](https://thumb-eu.123doks.com/thumbv2/123doknet/14592081.542550/42.892.113.754.105.488/figure-distance-bounding-protocol-proposed-brands-brands-commitment.webp)
![Figure 3.7: The Distance Bounding protocol proposed by Reid et al. in [Reid et al., 2007], where MAC is a MAC scheme used as a PRF.](https://thumb-eu.123doks.com/thumbv2/123doknet/14592081.542550/43.892.168.744.104.482/figure-distance-bounding-protocol-proposed-reid-reid-scheme.webp)
![Figure 3.8: The Distance Bounding protocol propoposed by Fisclin and Onete in [Fischlin and Onete, 2013b]](https://thumb-eu.123doks.com/thumbv2/123doknet/14592081.542550/44.892.161.714.105.588/figure-distance-bounding-protocol-propoposed-fisclin-onete-fischlin.webp)
![Figure 4.1: SPADE [Bultel et al., 2016], an anonymous TF resistant protocol built from a public key encryp- encryp-tion scheme E , a hash funcencryp-tion H and a group signature G.](https://thumb-eu.123doks.com/thumbv2/123doknet/14592081.542550/58.892.172.704.348.695/figure-spade-bultel-anonymous-resistant-protocol-funcencryp-signature.webp)
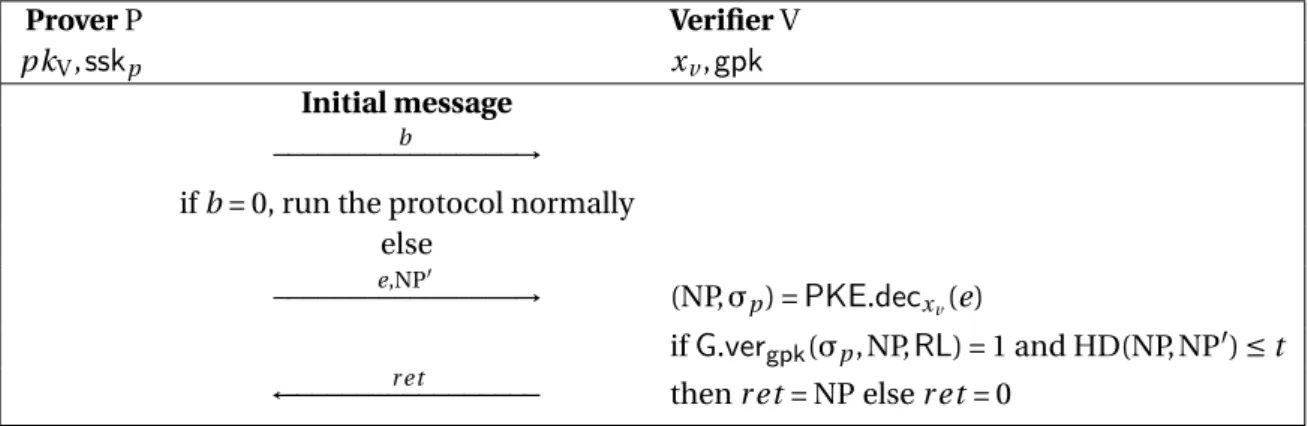
![Figure 4.3: TREAD [Avoine et al., 2017], a generic and provably secure DB construction built from an IND - CCA2 -secure encryption scheme E and an EUF - CMA -secure signature scheme (or a traceable group signature) S .](https://thumb-eu.123doks.com/thumbv2/123doknet/14592081.542550/69.892.129.820.104.576/figure-avoine-provably-construction-encryption-signature-traceable-signature.webp)