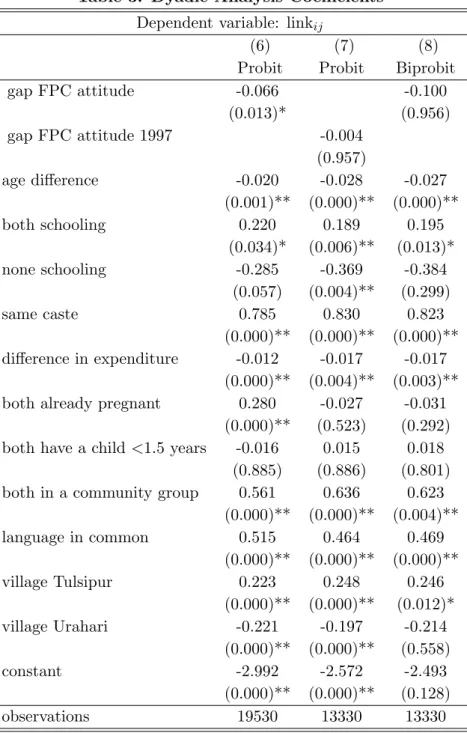
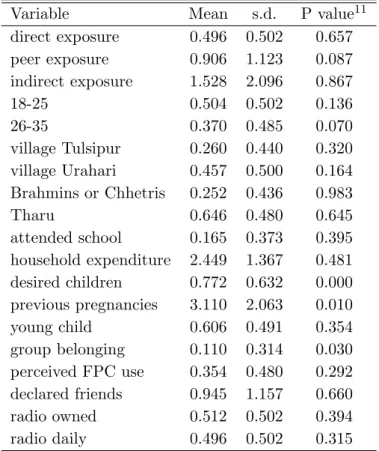
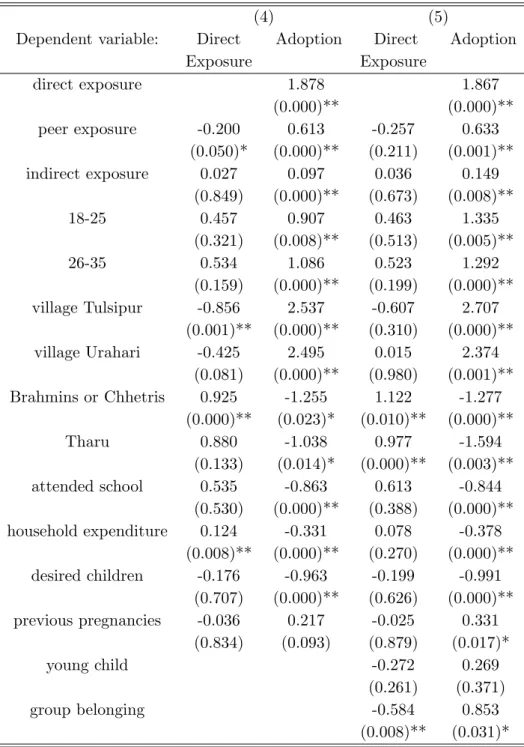
Educational programs in rural Nepal: Peer communication and information spillovers
Texte intégral
Figure



Documents relatifs
The conference has been organized by the World Health Organization Regional Office for the Eastern Mediterranean, and the Pakistan Association of Medical Editors (PAME), in
F requency is the number of the forecasts issued by an analyst for the firm during the quarter of concern; Age (age of the forecast) is the number of days between the forecast issue
Nanopublications can be used to expose any data type whatsoever, in- cluding quantitative and qualitative data, experimental data as well as hypothe- ses, novel or legacy data and
The main claim of the talk is that our research in Information Systems Engineering has to adopt clearly the research paradigms used in classical engineering fields (mechanical,
Les deux m´ ethodes retenues dans le cadre de ce travail sont la m´ ethode spectrale it´ erative pour pr´ edire le comportement vibratoire de la transmission (carter inclus) ` a
Given the nearly total absence of empirical data about bird mortality as a result of roadside maintenance operations, we chose a modelling approach to estimate incidental
Keywords: Information retrieval, Named entity task, Transducer cascades,
Our journey in Wuala’s « social storage » allows us to conclude that the main beneficiary of the co- existence of P2P technology at the layer of safeguard and