Towards a Privacy Risk Assessment Methodology for Location-Based Systems
Texte intégral
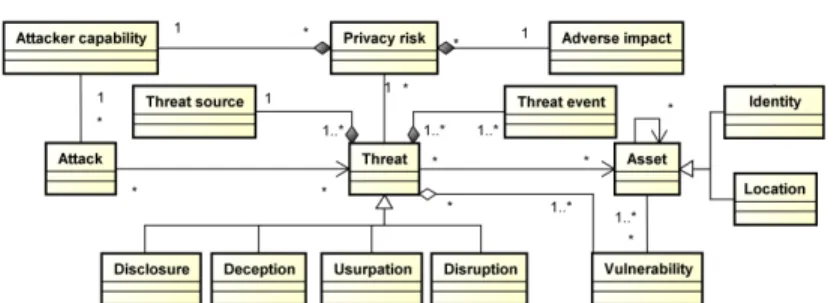
Figure
![Fig. 1. Risk management process adapted from ISO 27005 [6].](https://thumb-eu.123doks.com/thumbv2/123doknet/14423943.513822/3.918.255.668.840.948/fig-risk-management-process-adapted-iso.webp)
Documents relatifs
Following a survey conducted in 2011 re- garding the use of human and social sciences in fifteen public organisations in Europe and North America in charge of risk assessment
Model Based Risk Assessment of Procedures and Systems for Aircraft Trajectory Management.. Lucia Sanz, Andra Tonie, Christel Seguin, Rémi Delmas, Pierre Bieber,
This study creates a custom built risk assessment and management for the subsea rigged spool in all 3 phases from the end of manufacturing till commissioning operations in the
Taken together, the results show that contact with wastewater retained in one reservoir and meeting WHO guidelines for restricted irrigation was associated with an increased risk
Eavesdropping-based identifier disclosure attack Lack of IP/MAC address confidentiality Lack of user's identity confidentiality Identity spoofing attack Lack of messages
Two methods – Information System Security Risk Management (ISSRM) [5] [14] and Bayesian Network Based Attack Graph (BN- BAG) [10] [18] – are used to assess the information
In addition, its robustly built body, non-migratory behaviour, aggressive territorial defence, large clutch size, multiple broods, few predators and high chick
Thanks to the joint convergence result on the tail expectile and quantile processes, in Theorem 1, we derive the joint asymptotic normality of both empirical inter- mediate