Model-based Specification and Validation of Security and Dependability Patterns
Texte intégral
Figure

Documents relatifs
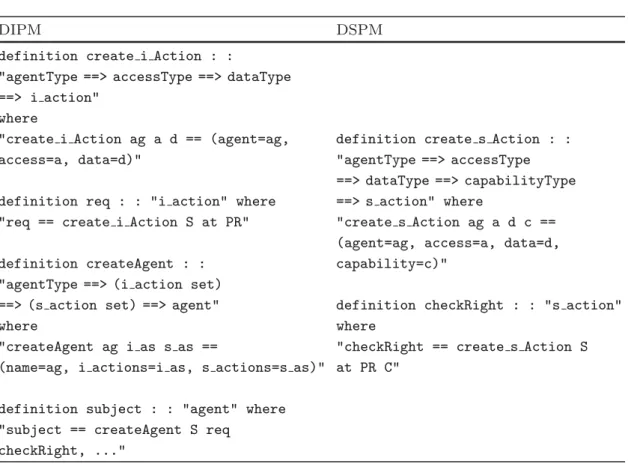
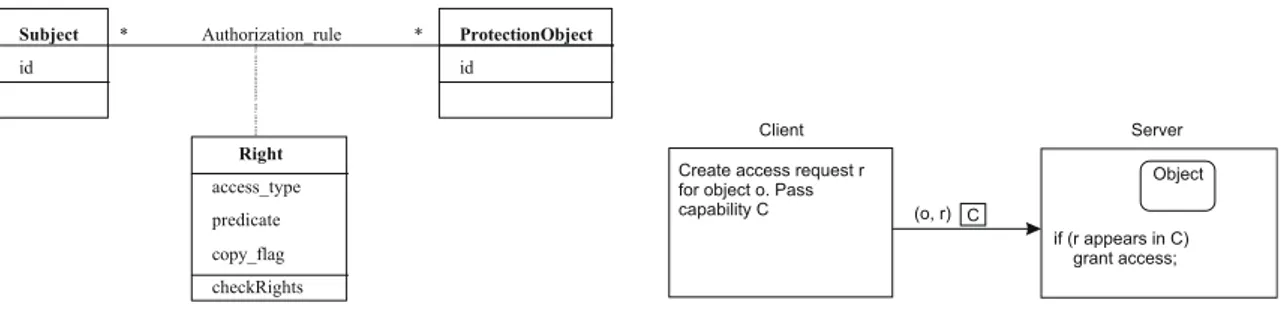
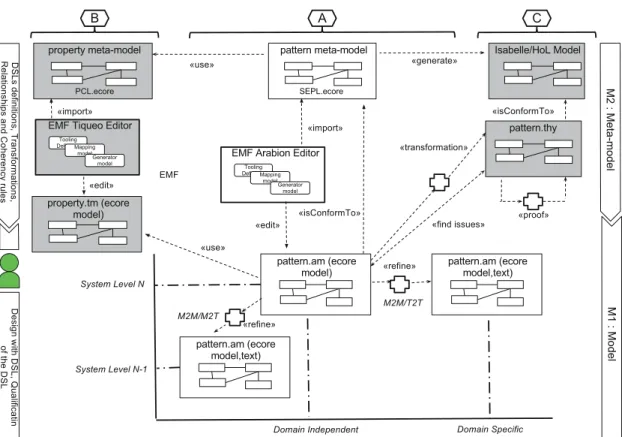
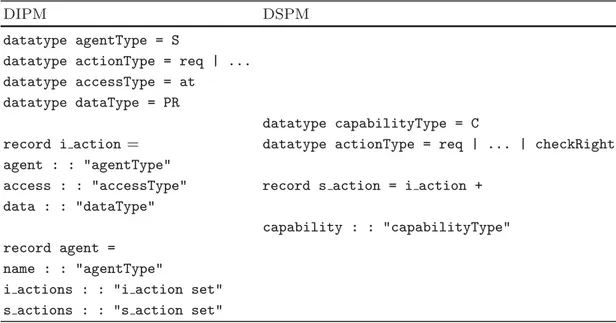
The contribution of this work is twofold: 1 An improvement of our previous pattern modeling language for representing security pattern in the form of a subsystem providing
Lima et al. [ 72 ] verify UML 2.0 sequence diagrams by mapping each fragment into a process in PROMELA code where the send/receive event are specified by a communication
/ La version de cette publication peut être l’une des suivantes : la version prépublication de l’auteur, la version acceptée du manuscrit ou la version de l’éditeur. Access
Mahloojifar, “A low-complexity adaptive beamformer for ultrasound imaging using structured covariance matrix,” IEEE Transactions on Ultrasonics, Ferroelectrics, and Frequency Control
The localized enrichment of Skittles and Pten acts to increase PI(4,5)P 2 levels at the anaphase equator, further promoting Moe recruitment at the equator and release at the
Aphanomyces euteiches cell wall fractions containing novel glucan-chitosaccharides induce defense genes and nuclear calcium oscillations in the plant host Medicago truncatula...
In this case, the method from [BCO+07] for the asymptotically efficient resolution of the vector version of (4) as a function of n gives rise to an overhead of O(r), due to the
deposition using mixed bimetal precursors containing methoxy-substituted β-diketonates are determined by the precursor composition. Thermal properties of a precursor are