Quantifying Studies of (Pseudo) Random Number Generation for Cryptography
Texte intégral
Figure
![Figure 2.1: Schematic diagram of a general communication system [SW49].](https://thumb-eu.123doks.com/thumbv2/123doknet/2648790.59881/17.892.204.707.160.369/figure-schematic-diagram-general-communication-sw.webp)

Documents relatifs
In Tim Güneysu, Gregor Leander, and Amir Moradi, editors, Lightweight Cryptography for Security and Privacy — LightSec 2015, volume 9542 of Lecture Notes in Computer Science,
A Noetherian integrally closed integral domain of Krull dimension 1 is called a Dedekind ring.. We can now conclude from our previous work the following local characterisation
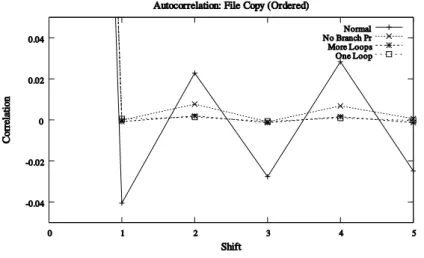
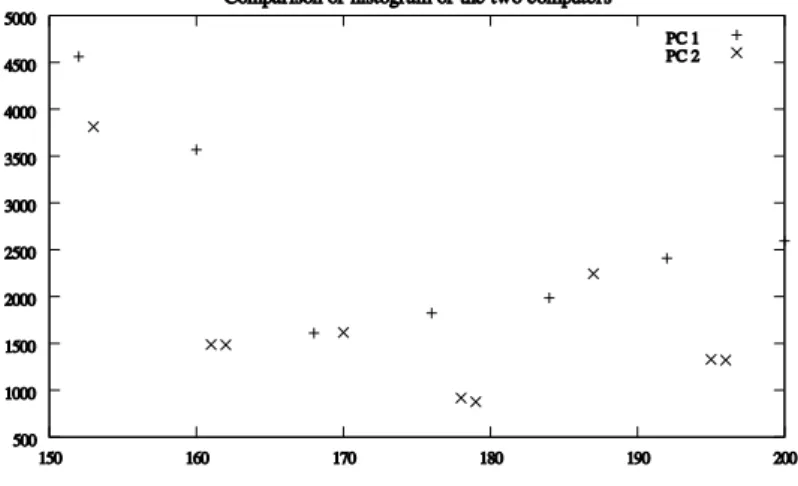
Other types of tests for RNGs include tests based on the closest pairs of points among n points generated in the hypercube, tests based on random walks on the real line or over
Other types of tests for RNGs include tests based on the closest pairs of points among n points generated in the hypercube, tests based on random walks on the real line or over
• Verification algorithm V is a probabilistic polynomial time algorithm which given a public key P, a digital signature s, and a message m, returns 1 (i.e ”true”) or 0 (i.e
Moreover, to justify that the successive digits of π (or any other given real number) in a given base b can be taken as random, it would be good to know that this sequence of digits
Yuri Gurevich has made fundamental contributions to the broad spectrum of logic and computer science, including decision procedures, the monadic theory of order, abstract
The volume then includes an article by Maria Teresa Sans Bertran (“Repertori i usos lingüístics d’un alumne intern d’origen marroquí d’un centre penitenciari