A Card-less TEE-Based Solution for Trusted Access Control
Texte intégral
Figure

Documents relatifs
A relevant feature of our approach is that the right to access a resource R can be transferred from the subject who is the current right holder, say S i , to another subject, say S j
Noting with satisfaction the progress so far achieved by Member States and the Organization in implementing national and regional health strategies;.. Further noting
Transformation & Engineering of Enterprises involves the use of methods and techniques from business process management, business engineering, business-IT alignment,
Our activities are located on three levels: (a) the re-engineering of the system’s access control policy is lo- cated at the policy level, (b) the framework level summarizes
Our physical access control system uses the OASIS consortium’s eXtensible Access Control Markup Language (XACML) standard [1] and the W3C’s Voice eXtensible
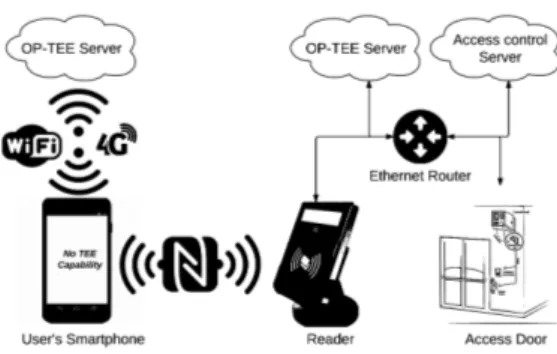
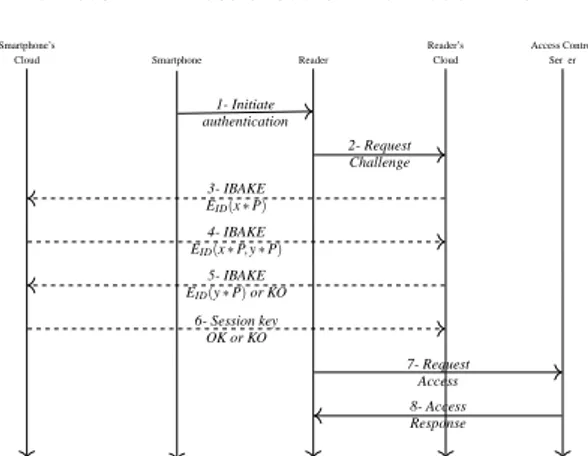
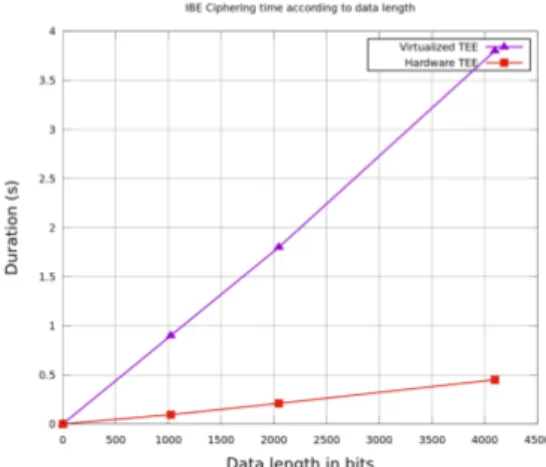
Our secure access control system is based on Trusted Execution Environment (TEE) in the cloud and Identity Based Encryption (IBE) mechanisms.. The authentication protocol deployed
Among the priority issues there are those concerning existing approaches and models for electronic educational resources delivery within the hybrid cloud-based
The 9 th TEE (Transformation & Engineering of Enterprises) series of workshops is an evolution, and merger, of the successful PRET and AppEER workshops (which merged into TEE