Any correspondence concerning this service should be sent
to the repository administrator:
tech-oatao@listes-diff.inp-toulouse.fr
This is an author’s version published in:
http://oatao.univ-toulouse.fr/22649
To cite this version: Astsatryan, Hrachya V. and Grogoryan, Hayk and
Gyulgyulyan, Eliza and Hakobyan, Anush and Kocharyan, Aram and
Narsisian, Wahi and Sahakyan, Vladimir and Shoukourian, Yuri and
Abrahamyan, Rita and Petrosyan, Zarmandukht and Aligon, Julien Weather
Data Visualization and Analytical Platform. (2018) Scalable Computing:
Practice and Experience, 19 (2 special). 79-86. ISSN 1895-1767
Official URL
DOI :
https://doi.org/10.12694/scpe.v19i2.1351
Open Archive Toulouse Archive Ouverte
OATAO is an open access repository that collects the work of Toulouse
researchers and makes it freely available over the web where possible
Satisfiability
of
general
intruder
constraints
with and
without
a
set
constructor
✩
Tigran
Avanesov
a,
Yannick
Chevalier
b,
Michael
Rusinowitch
c,
Mathieu Turuani
ca SnT,UniversitéduLuxembourg,Luxembourg b UniversitéPaulSabatier&IRITToulouse,France cINRIANancy–GrandEst&LORIA,54600Villers-lès-Nancy,France
a
b
s
t
r
a
c
t
Keywords: ACI Deducibilityconstraints Dolev– Yaodeductionsystem Multipleintruders Security
Many decision problems on security protocols can be reduced to solving deductionconstraints expressingwhetheran instance ofa given message pattern can be constructed by the intruder. Most constraint solving procedures for protocol security rely on two properties of constraint systems called monotonicity and variable-origination. In this work we relax these restrictions by giving a decisionprocedureforsolvinggeneralintruderconstraints(thatdo not havetheseproperties)thatstays inNP. Theresult isalsovalid modulo an associative, commutative and idempotent theory. The procedure can be applied to verify security protocols in presence ofmultipleintruders.
1. Introduction
Detecting flaws in security protocol specifications under the perfect cryptography assumption in the Dolev–Yao intruder model is an approach that has been extensively investigated in recent
✩ The work presented in this paper was partially supported by the FP7-ICT-2007-1 Project no. 216471,
“AVANTSSAR: Automated Validation ofTrust and Security of Service-oriented Architectures”(http://www.avantssar.eu) and FP7-ICT Project no. 256980, “NESSoS: Network of Excellence on Engineering Secure Future Internet Software Services and Systems” (http://www.nessos-project.eu).
E-mailaddresses: tigran.avanesov@uni.lu (T. Avanesov),yannick.chevalier@irit.fr (Y. Chevalier),michael.rusinowitch@inria.fr (M. Rusinowitch),mathieu.turuani@inria.fr (M. Turuani).
years (Armando et al., 2014; Groza and Minea, 2013; Viganò, 2012; Meadows, 2011; Blanchet, 2009; Guttman, 2007; Arapinis and Duflot, 2007; Turuani, 2006). In particular, symbolic constraint solving has proved to be a very successful approach in the area. It amounts to expressing the possibility of mounting an attack, e.g. the derivation of asecret, as a listof steps where for each step an instance of themessage patternawaited accordingtothe protocol has tobe derived fromthe currentintruder knowledge. These stepscorrespond in general to the progressionof the protocol execution, upto the last onewhich isthe secretderivation.
EnrichingthestandardDolev–Yaointrudermodelwithdifferentequationaltheories(Comon-Lundh and Shmatikov, 2003; Comon-Lundh, 2004; Basin et al., 2005; Chevalier and Rusinowitch, 2010; Baskar et al., 2010; Escobar et al., 2011) like exclusive OR, modular exponentiation, Abelian groups, etc. (Liu and Lynch, 2011; Erbatur et al., 2011; Malladi, 2012; Chevalier et al., 2005; Küsters and Truderung, 2008) helps to find flaws that could not be detected considering free symbols only. A particularly useful theory is the theory of an ACI operator (that is associative, commutative and idempotent)since itallowsone toexpress sets in cryptographicprotocols.
Up to the exception of Mazaré (2005), all proposed algorithms rely on two strong assumptions about theconstraints tobe processed:
•
knowledge monotonicity, reflecting the fact that the intruder could see everythingthat occurred before andforgot nothing;•
variableorigination, reflectingthateach variationin the protocol is introducedby the intruder.Constraintssatisfyingthesehypothesesarecalled well-formedconstraints intheliterature.Well-formed constraints are sufficient to solve security problems in the standard case where a single Dolev–Yao intruderisassumed.However,wewillsee thatin somesituationsitcanbe quiteusefultorelaxthese hypothesesand considergeneralconstraints,thatis constraintswithout the restrictionsabove. General constraints naturally occurwhenconsideringsecurity problems involvingseveral non-communicating Dolev–Yao intruders (see § 2.1). Note that if intruders can communicate during protocol execution, themodel becomesattack-equivalenttoonewithauniqueDolev–Yaointruder(Syversonetal.,2000). A discussion on a multiple non-collaboratingattackers model as well as interestingexamples canbe foundin Fiazza et al. (2012).
1.1. Contributionsofthepaper
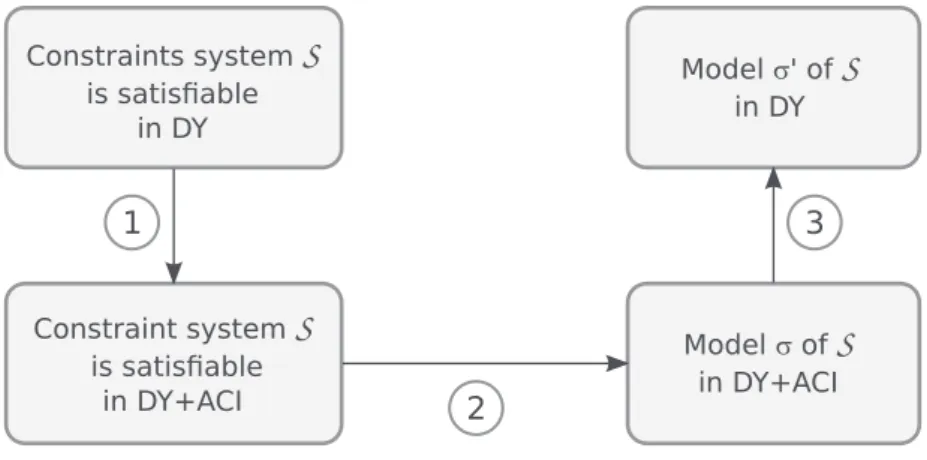
First, wewill showthatas forthe standardcase,inthismoregeneral frameworkit isstill possible to derive an NP decision procedure for detecting attacks on a bounded number of protocol sessions (Sections 5, 4). Second, our result extends previous ones by allowing non-atomic keys (which is an important feature for protocol design as it is common to build symmetric keys from shared secrets) and theusageof anassociativecommutativeidempotent operator(Sections 3, 4) thatcanbeused for instancetomodelsetsofnodesinXMLdocument(see§2.2).Thisextensionofwell-formedconstraint systems may seemtrivial but athirdcontribution of thispaper is todemonstrate thisisnot the case by consideringsubtermdeduction systems whichare akin tothe Dolev–Yaodeductionsystem, but in which the equational theory can be any subterm convergent one. Whereas the decidability of well-formed constraint systems for subterm deduction systems is well known, see e.g. Baudet (2005), we prove in Appendix A thatthe satisfiability of general constraint systems is not decidable for subterm deduction systems. Finally we will sketch several applications of our results to security analysis in Section 2.
1.2. Relatedwork
The decisionprocedure for satisfiability of well-formed constraint systems can be used to decide the insecurity of cryptographic protocols with a bounded number of sessions (Rusinowitch and Tu-ruani, 2003). In this domain, several works deviated from the perfect cryptography assumption and started to consider algebraic properties of functional symbols.For example properties of XOR opera-tor and exponentiationwere consideredin Lynchand Meadows (2004), Chevalier et al. (2005,2008),
Dougherty andGuttman (2013) andtogether withhomomorphicsymbolin Delaune (2006). Aclassof monoidal equational theories was studied in Delaune et al. (2008) including the ACUI theory which is quite similar to the ACI theory discussed in the present work, but the absence of a unit element in ACI seems to put the ACI theory out of scope of their method. MoreoverDelaune et al. (2008) do not show the NP complexity of their procedure. We note that in Chevalier et al. (2007) the authors showed the NP-completeness for the AC theory, while Dolev–Yao deduction system was extended with a rule x
·
y→
x, where·
is an AC symbol. We will examine the ACI theory within the similar deductionsystem.Note alsothatsome algebraicproperties(like associativeand commutativesymbol) make the insecurityproblemundecidable (Bursuc etal., 2007).Allthe decidability resultsmentioned above consider systems of constraints with two restrictions namely knowledge monotonicity (the left-hand side of a constraint representing the current knowl-edge of the intruder is included into the left-hand side of the next one) and variable origination (variable appears first in the right-hand sideof some constraint): thislimitation is not impeding the solution of usual protocol insecurity problems since the constraints generated with anactive Dolev– Yaointruderareoftherequiredtype.Anattempttoswervefromwell-formedconstraintswasmadein
Mazaré (2005) where the knowledge monotonicity was relaxed to define“quasi well-formed” whose satisfiability is proven to be in NP. This result was later extended in Mazaré (2006) to general con-straint systems but under the provision thatall keys are atomic, anhypothesis thatpermits to guess at the start of the procedure which keys are availableat which step to the intruder. However to our knowledge no extension of Dolev–Yaodeductionsystemto non-atomicsymmetric keyor toalgebraic properties has been shown decidable for general constraint systems. Moreover, satisfiability of well-formed constraints with the ACI theory was not considered before. We have presented our results without proofs in a conference paper (Avanesov et al., 2010). In this long version we give detailed proofs. We believethatthey canbe useful forreadersthatwanttostudygeneral constraintsfor other intrudertheories.
2. Motivatingexamples
2.1. Protocolanalysiswithseveralintruders
Security analysis of a protocol is usually conducted in the worst possible case: a single intruder
(or acoalitionof severalintruders,butable toshareinformation fasterthannormal communications) controls all the network. Howeversome protocols,especially routing protocols, are designed to work through different, non-communicating sub-networks. A relevantanalysis of such protocols musttake into account that the security of the protocol depends on the (correct) assumption that some com-munications arenot possible.Inthese casesone needstoconsider aless powerful intruder, or rather a collectionthereof,that still controls some parts of the networkbut remains completely ignorant of what happensin other parts.
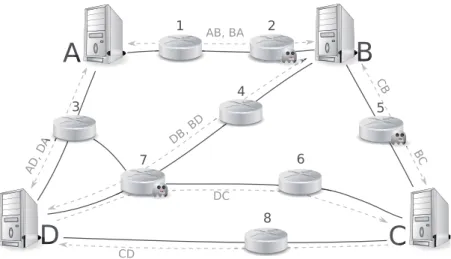
Suppose several agents ( A
,
B. . .
, see Fig. 1) execute a protocol i.e. a specified finite sequence of message emissions or receptions. Due to their (long distance) layout they have to transmit data throughrouters(1,
2,
3. . .
).Theroutingtables of allhonestrouters/agents arestatic(messagesfollow always the samepath). Somerouters(2,
5,
7)may be compromised: anintrudermanaged toinstalla device controlling input and output of the router or implanted there his malicious code. A message circulated via such an untrusted channel (e.g. D B) is consumed by the corresponding compromised device (localintruder) (7) thereby increasing his knowledge. Moreover, a local intrudercan forge and emit to an endpoint (C,
B,
D) of any channel he controls (B D,
D B,
DC ) any message he can build usingthe contentofhismemoryand someavailabletransformations specifiedby adeductionsystem. Becauseofthenetwork topologymaliciousroutershavenomeanstocommunicate(thereareno links between them, neither direct nor via other routers), but at some point the intruder can gather the knowledge of all thecompromisedrouters(by physicallycollectingdevices orreadingtheirmemory). Inthisframeworkthe Coordinatedattackproblem is todecidewhetheritispossibletoinitially give instructions to compromisedrouters (e.g. by reprogramming maliciousdevices) toforce anexecution such that honest agents following the protocol will reveal some secret data to the intruder (i.e. the intrudercan deduceit usinginformation collected at the endfromall local intruders).Fig. 1. Untrusted routers.
2.1.1. Thecoordinatedattackproblem
We give here asemi-formal description of the problem and some directions to solve it. A formal model canbe foundin Avanesov etal. (2010) or Avanesov (2011).
First weintroducesome notations anddefinitions thatwillbe detailed in thetechnicalpart ofthe paper (§ 3).
2.1.1.1. Messages Weconsidermessagesasfirst-ordertermsbuiltfromasetoffunctionsymbols(such asencryption,pairing,etc.),asetofconstants
A
(representingelementarypiecesof data:texts,public keys,namesofagents,etc)and asetofvariablesX
. LetT
bethe setofall possibleterms.Foratermt wedenote by Vars
(
t)
the set of all variables in t. A termt is agroundterm, if Vars(
t) = ∅
. Theset of groundtermsis denotedbyT
g.We defineasubstitution
σ
= {
x17→
t1,
. . . ,
xk7→
tk}
(where xi∈ X
and ti∈ T
) tobe the mappingσ
: T → T
, suchthattσ
is atermobtained by replacing,forall i,eachoccurrence of avariable xi by the corresponding term ti. If T⊆ T
, then by definition Tσ
= {
tσ
:
t∈
T}
. A substitutionσ
is groundif for any i
∈ {
1, . . . ,
k}
, ti is ground.2.1.1.2. Agents We will call honest communicating parties agents. Every agent is identified by its name.We denote theset ofagent namesby A.
2.1.1.3. Channels Any two agents a and b communicate through a directed channel a
⇀
bimple-mentedas aqueue. Thesent messages are storedin aqueuetobe processed in orderof arrival.
2.1.1.4. Agents’behavior Eachagenthasaspecificsequenceofactionstoexecute.Everyactioniseither of reception type ?fr (expectinga messager from agent f ) or emission type
!
ts (sending amessages to anagentwithnamet). Here r ands aretermsrepresentingmessagepatterns. Forexample,if the sequence of actionsof agenta is ?baenc
(
X,
pka) ,
!
caenc(
X,
pkc)
(where X is avariable and pka,
pkc are constants denotinga public key of a and a public key of c correspondingly and aenc(
u,
v)
is an asymmetricencryption of u withkey v) then a waits untilhe/she receives some messaget matchinga pattern aenc
(
X,
pka)
on a channel b⇀
a and sends a message aenc(
Xσ
,
pkb)
on channel a⇀
c, whereσ
is a substitution satisfying t=
aenc(
X,
pka)
σ
. For instance, if a receives aenc(
s,
pka)
, i.e. some atomic value s asymmetrically encrypted with a public key of a pka, then the corresponding substitutionσ
is{
X7→
s}
anda sendstoc thevalueof s reencryptedwithpublickey pkc ofc.Onthe other hand, it couldbeσ
= {
X7→
pair(
b,
s)}
if b sent aenc(
pair(
b,
s) ,
pka)
. Note that if the message does not match the expected pattern, the agent stops this execution. Once a variable is instantiated on areception, its value canbe used in thefollowing agentactions.Table 1
DYdeductionrules.
Composition rules Decomposition rules t1,t2→enc(t1,t2) enc(t1,t2) ,t2→t1 t1,t2→aenc(t1,t2) aenc(t1,t2) ,priv(t2) →t1 t1,t2→pair(t1,t2) pair(t1,t2) →t1
t1,priv(t2) →sig(t1,priv(t2)) pair(t1,t2) →t2
2.1.1.5. Intrudermodel We assume that some communication channels are controlled by N local
in-trudersfromaset
I
= {
Ii}
i=1,...,N and nochanneliscontrolledbymorethanone intruder.Givensome channel c,we denotebyι
(
c)
the localintruder thatcontrols c whenthereis one.Every intruder I is given some initial knowledge K0I thatis a set of ground terms. Once an agent sends amessage via a channelcontrolled by an intruder, the intruderreads it and blocks it. Reading the message means extending intruder’s current knowledge with this message. An intruder control-ling a channel can generate a message from his knowledge using deduction rules and send it to its endpoint.
We nowspecifythe intrudercapabilities.
Definition2.1. Arule is atuple of termswrittenas s1
,
. . . ,
sk→
s,where s1,
. . . ,
sk,
s are terms. Ade-ductionsystem
D
is asetof rules.As an example of deduction system, we refer to a version of the classical Dolev–Yao deduction system (DY)presented in Table 1.
From now to the endof this section rules are assumed to belong to a fixed deduction system
D
and that terms are evaluated modulo a congruence on terms
≡
E by an equational theory (a set ofequationsbetween termstogether withthe properties ofequality)
E
.Given two sets of ground terms E, F and arule l
→
r, we write E→
l→r F iff F=
E∪ {
s}
, s≡
E rand l
⊆
E,where l is asetof terms.We write E→
F iffthereexistsrule l→
r suchthat E→
l→r F .Definition2.2.A derivation D is a finite sequence of finite sets of ground terms E0
,
E1,
. . . ,
En such that E0→
E1→ · · · →
En, where Ei=
Ei−1∪ {
ti}
, for all i∈ {
1, . . . ,
n}
. A termt isderivablemoduloanequationaltheory
E
fromasetofterms E iffthere existsaderivation D=
E0,
. . . ,
En suchthat E0=
Eand there exists s
∈
En such that s≡
E t. We denote by derE(
E)
the set of terms derivable from Emodulo
E
. A setof terms T isderivable from E, iff T⊆
derE(
E)
.Whentheequational theory
E
is clearfromcontextwe write Der(
E)
instead of derE(
E)
, andsim-ilarlyomitanyreferencetoit. Informally,alocalintrudermay buildnewmessages fromthemessages he knows by applying the deduction rules(e.g. concatenate two messages he knows). At each step a local intruderhavingrecordedmessages t1
,
. . . ,
tn cansend amessagem if m∈
Der({
t1, . . . ,
tn})
.2.1.1.6. Protocolexecution Givenasetofprotocol participants(agents)withtheirsequencesof actions to execute, communication channels and local intruders each one with some initial knowledge, the course of events develops as follows. Each agent access channels connecting her to other agents. To sendamessagetoBobAliceinsertsthemessageinthequeuerepresentingthechannel,andtoreceive itBobtakesthefirstmessageinthe queueand matchesitagainstthepattern oftheawaitedmessage. An intruderCharlie controlling the channel mayadd, remove,read or reorder as hewishes messages in the queue.
2.1.1.7. Offlinecommunication Atsome executionpointinitially specified,thecurrent knowledgeof all localintrudersissharedin ordertoderive asecretwhichprobablytheycannot deduceseparately.We consider our intruder model is reasonable for covering situations where offline interactions between intruders are time-consumingand may be detected and therefore they take placewhen the protocol is over, when the honestagents havefinished toexecute theirroles.
2.1.1.8. Coordinatedattackproblem We are now able to define what is an attack by several local in-truderson aprotocol.
Coordinated attack problem (CAP)
Input: A finite set of agents A, list of actions per agent
{h
a,
lai}
a∈A, a set of local intrudersI
=
{
Ii}
i=1,...,N each with initial knowledge K0Ii, and a partial functionι
that assigns at most onein-truder
ι
(
c)
toeach channelc and some sensitivedatagiven asaground term s.Output: Yes iff there is a sequence of actionsperformed by agents and local intruders such that, at some point,from theunion ofintruders knowledge it ispossibleto derive s.
2.1.2. ReductionoftheCAPtothesatisfiabilityofaconstraintsystem
We sketch in this section a non-deterministic reduction of the coordinated attackproblem to the satisfiability of a constraint system. Briefly put, this reduction guesses an ordering of messages sent and received by the agents. Each intruder diverts all the messages put in a queue he has access to, and allmessages receivedby agentsare actuallysentbythe intruder.Aguessedexecutionmay be in-feasibleifthealgorithmguesses anorderingin whichanintruderwhomustsendamessageisunable toconstruct amessage matching the awaitedmessagepattern. We thusintroduce constraints impos-ing that given a set E of messages known by an intruder, he has to construct amessage matching a pattern t.
Definition2.3.Let
E
be an equational theory, E be a set of terms and t be a term. We define the couple(
E,
t)
denoted E✄
t to be aconstraint moduloE
. A constraintsystemmoduloE
is asetS
= {
Ei✄
ti}
i=1,...,nwheren is anon-negative integerand Ei
✄
ti is aconstraintmoduloE
for i∈ {
1,
. . . ,
n}
.A ground substitution
σ
is amodel of constraint moduloE
E✄
t (orσ
satisfies this constraint) if tσ
∈
Der(
Eσ
)
. A ground substitutionσ
is a model of a constraint systemS
moduloE
if it satisfies all the constraints ofS
. In order to simplify notations, when the equational theoryE
is clear from context wewill omitany referenceto it.Toexpress the problemwithconstraints we first guessanorder in whichthe agents executetheir actionssinceseveralinterleavingsarepossible.Once theorderisfixed,webuildtheconstraintsystem
S
(initially empty)incrementally by progressing in the actionlist:•
Agenta executes!
bt onchannela⇀
b:·
if a⇀
b is controlled by I we increase the knowledge of Intruder I with t by setting KI:=
KI
∪ {
t}
;·
otherwisewe put t directlyin the channelqueue.•
Agenta executes?bt on channelb⇀
a:·
if b⇀
a is controlledby I we add a constraint KI✄
t intoS
expressing the fact thatIntruder I knowing KI mustsend amessage compatiblewith theexpected message patternt;·
otherwise we must ensure thatthe first message m in the queue of b⇀
a is compatible with theexpected pattern t,i.e.mσ
=
tσ
, whereσ
is agroundsubstitution satisfying all other con-straintsinS
.For thecase ofDY deductionsystemwe canencodethisequationby aconstraint{
enc(
m,
k)} ✄
enc(
t,
k)
for some atom k1 since we can prove they admit the same solutions. We addthe constraint toS
and remove m fromthe queue.Finally, weadd
(
S
I∈IKI
)
✄
s toS
which expressesthe offline communication phase:Secret s can bededuced fromthe unionof localintruders knowledge.
It is clear thatif there existsa substitution
σ
thatsatisfiesS
then CAP has asolution. Conversely an attack for the CAP ordersand instantiates the message patternsin the descriptionof the protocol withasubstitutionσ
, which satisfies the constraintsystemconstructedas above.Fig. 2. Example illustrations.
We give an example below and will show in Sections 3 and 4that the satisfiability of constraint systems isin NP inthe caseof theDolev–Yaodeduction theoryand itsextension withan associative-commutative idempotent operator. This kind of operator can be useful to model messages in XML format as isshown in next subsection.
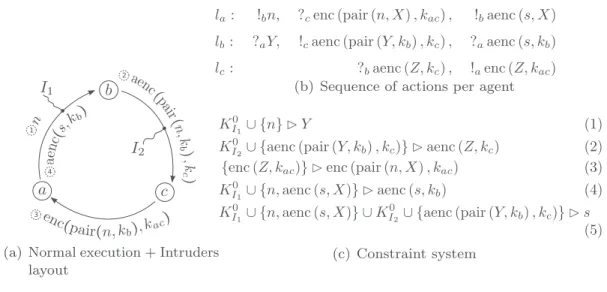
2.1.3. Example
Supposethreeagents a
,
b,
c execute aprotocolwhose normal executionis shownin Fig. 2(a). Each agent follows his sequence of actions shown in Fig. 2(b). Agent a wants to send a secret s to b. He asks b to send her public key kb to c, that will forward it to a. Nonce n permits a to correlate the message fromc with hisrequest.The agents are connected by three directed channels: channel a
⇀
b is controlled by local in-truder I1, channel b⇀
c is controlled by local intruder I2, while channel c⇀
a is secure (free from intruders).We assume that the two local intruders have as initial knowledge a pair of fresh public/private keys and public keys ofall participants: K0I
1
=
K0
I2
= {
ki,
priv(
ki) ,
ka,
kb,
kc}
.The question we ask is whether the local intruders I1 and I2 can cooperate in such a way that joiningtheir finalknowledge they canderive s, althoughtheyhave nomeans tocommunicateduring the protocol execution.
Following the sequence of actions shown in Fig. 2(a), we obtain the constraint system shown in Fig. 2(c). First a sendsn which isintercepted by I1. Theknowledge of I1 becomes KI1
=
K0I1
∪ {
n}
. Then I1 mustbuildfromhisknowledge amessagethatcanbeaccepted byb. Thisisexpressed in (1).Once b accepts this message, he executes his next action: emission of a message on channel b
⇀
c.This message is intercepted by I2 and his knowledge becomes KI2
=
K0
I2
∪ {
aenc(
pair(
Y,
kb) ,
kc)}
. Now, I2 must send a message to c on behalf of b (2). Then c accepts a message sent by I2,it sends his reply to a which should be compatible with the expected pattern: enc
(
Z,
kac) =
enc(
pair(
n,
X) ,
kac)
. This fact is encoded into (3). Then a sends a message to b intercepted by I1(KI1
=
K0
I1
∪ {
n,
aenc(
s,
X)}
) and I1 must generate a message acceptable by b (4). Finally, in (5) we specify thatfromthe common knowledge of I1 and I2 one may deduce asecrets.Theobtained constraint systemhas no solution as wellas any other constraintsystems generated from different interleaving of actions executed by the agents. We conclude that there is no coordi-nated attack under the given hypothesis. On the other hand, if I1 and I2 can communicate, or the
same intruder controls both channels a
⇀
b and b⇀
c, a simple attack can be mounted: once the intruderreceives n onchannela⇀
b, hegeneratesthe message aenc(
pair(
n,
ki) ,
kc)
and sends itviab
⇀
c; c accepts itand sends messageenc(
pair(
n,
ki) ,
kac)
to a whichmatches the expected pattern. Thus, a will send via a⇀
b a message aenc(
s,
ki)
which is intercepted by the intruder and can be decomposed using priv(
ki)
. Theintrudercanalso finalizethe actionsof b bysendinghim,e.g., n andFig. 3. Ordering an item scenario.
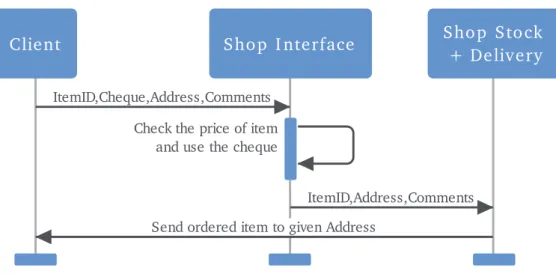
2.2. AttacksexploitingXMLformatofmessages
We proposeawaytomodelsomeattacksbasedonanXML-representationof messages.Adifferent technique to handle this kind of attacks was presented in Chevalier et al. (2007) which considers multisets of XMLnodes, while in thisworkthe notion of setis takenas abasis.
We consider an e-shop that accepts e-cheques, and we suppose that it is presented by a Web Service usingthe SOAPprotocol for exchanging messages.
It consistsof two services:
(1) thefirst exposesthe listof goodsfor salewiththeir pricesand processestheordersby accepting payment;
(2) thesecondis adeliveryservice;it receivesinformationfrom thefirst oneabout successfullypaid orders,and sendsthe ordered goods tothe buyer.
A simple scenario for ordering items is shown in Fig. 3. First, a client sends an order using the e-shop interface that consists of an item identifier, e-cheque, delivery address and some comments. Then, the first serviceof thee-shop checkswhethertheprice of the ordered item corresponds tothe received cheque. If it does, the service consumes the cheque and forwards the order to the stock-/delivery service (without the used e-cheque). Stock and Delivery service prepares a parcel for the ordered item and sends it to given address. The comment is automatically printed on the parcel to givesome information tothe postmanabout, for example, delivery time or accessinstructions.
Suppose Alice has an e-cheque for 5
e
. She can buy a simple pen (with ItemID simple) but she likes verymuchamoreexpensivegilded one(with ItemIDgilded). CanwehelpAlice togetwhatshe wants forwhat she has?Let us formalize the behavior of scenario players. We will write
(
t1· . . . ·
tn)
(or equivalently· (
t1, . . . ,
tn)
) an XML message where t1,
. . . ,
tn are XML nodes. We model the fact that the nodes are not duplicated and their order is meaningless by assuming that·
is associative commuta-tive and idempotent. Identifiers starting with a capital letter are considered as variables; numbers and identifier starting from lower-case letter are considered as constants. We model a delivery of item with some ItemID to address Address with comments Comments by the following message: sig((
ItemID·
Address·
Comments),
priv(
ks))
— a message signature produced by e-shop, where ks its public key and priv(
ks)
is the corresponding private key,such that no one canproduce thismessage except the shop. We abstract away from the procedure of checking the item price and will suppose that Shop Interface expects a 5e
e-cheque for Item “simple”. For simplicity we assume only two items.ForShopInterface we have:
?Client
(
simple·
cheque5·
IAddr·
IComm);
!
Delivery(
simple·
IAddr·
IComm).
For ShopStock/Delivery we have:?Interface
(
DItemID·
DAddr·
DComm);
!
Clientsig((
DItemID·
DAddr·
DComm),
priv(
ks)) .
Alice initiallyhas:simple
,
gilded:
identifiers of items;cheque5
:
an e-cheque for 5e
;addr
:
her address;cmnts
:
residence digital code;ks
:
a public key of the shop.Nowwe build a mixedconstraint system (derivation constraints and equations) to knowwhether Alice can dowhat she wants:
{
gilded,
simple,
cheque5,
addr,
cmnts,
ks} ✄
(
simple·
cheque5·
IAddr·
IComm)
(
simple·
IAddr·
IComm) =
ACI(
DItemID·
DAddr·
DComm)
{
gilded,
simple,
cheque5,
addr,
cmnts,
ks,
sig
((
DItemID·
DAddr·
DComm),
priv(
ks))} ✄
sig
((
gilded·
addr·
DComm),
priv(
ks))
(6) (7) (8) The constraint (6) shows that Alice can construct a message expected by the shop from a client. Constraint (7) represents a request from the first to the second service of the shop: the left-hand side is amessage sent by the interface serviceand the right-hand sideis a message expected by the stock/delivery subservice;≡
ACI meansthatthesemessages mustbecompatible (moduloACI).Thelast constraint shows that from the received values Alice can build a message that models a delivery of item withItemIDgilded.To solve it, we first get rid of syntactic equationsby applying the most general unifier; and then of equationsmodulo ACI(t1
=
ACIt2) by encoding them into a deducibility constraint (as it wasdonein § 2.1.2).
Then, oneof the solutions is:
IAddr
7→
addr IComm7→(
gilded·
cmnts)
DItemID
7→
gilded DAddr7→
addrDComm
7→(
simple·
cmnts)
From this solution we see that Alice can send an ill-formed comment (that contains two XML-nodes), and the Delivery service parser can choose an entry with ID gilded. An attack-request can look likethis:
<
ItemID>
simple<
/ ItemID>
<
Cheque>
cheque5<
/ Cheque>
<
Address>
addr<
/ Address>
<
Comments>
cmnts<
/ Comments>
<
ItemID>
g i l d e d<
/ ItemID>
The parser of the first service can return the value of the first occurrence of ItemID:
<
ItemID>
simple
<
/ItemID>
, whilethe parserofthe secondone,beingadifferentsoftware,canreturn<
ItemID>
gilded<
/ItemID>
.This attack is possible if Alice constructs a request “by hand”, but a similar attack is probably feasibleusinganXML-injection: Alicewhen fillingarequestformentersinsteadof hercommentsthe following string:
cmnts
<
/ Comments>
<
ItemID>
g i l d e d<
/ ItemID><
Comments>
and in the resulting requestwe get:
<
ItemID>
simple<
/ ItemID>
<
Cheque>
cheque5<
/ Cheque>
<
Address>
addr<
/ Address>
<
Comments>
cmnts<
/ Comments>
<
ItemID>
g i l d e d<
/ ItemID><
Comments>
<
/ Comments>
This kind of XML-injection attack wasdescribedin OWASPFoundation (2008). 3. SatisfiabilityofgeneralDY
+
ACI constraintsystemsIn Section 2 we have shown how to reduce the problem of protocol insecurity in presence of several intruders to solving a system of general deducibility constraints. In this section we present a decision procedure for the satisfiability of general constraint systems where the Dolev–Yao de-duction system is extended with some deduction rules for an associative-commutative-idempotent symbol(DY
+
ACI).We consider operators for pairing, symmetricand asymmetricencryptions, signa-ture,hashingand anACI operator thatwillbe used as asetconstructor.As for the proof structure, after introducing the formal notations and some basic properties, the mainsteps toshow the decidabilityare as follows:
(1) We present analgorithmfor solvingthe derivabilityproblemin the DY
+
ACI model;(2) Weprovethatforcheckingintruderconstraints satisfiabilityitissufficienttoconsidernormalized constraintsand normalized substitutions;
(3) Weshowthatasatisfiablenormalizedconstraintsystemadmitsatleastoneconservative solution, thatisasubstitution
σ
thatmapseachvariableoftheconstraintsystemtoasetofsubtermsfrom theconstraint system(instantiated withσ
) and privatekeys;(4) We give aboundon the size of aconservative solution, and, as aconsequence, we obtain decid-ability.
3.1. Formalintroductiontotheproblem
First we would like to note that we omit the proofs of some statements that we find intuitive. In any case the detailed proofs may be found in Avanesov (2011) (particularly in Lemma 4, p. 33). Though thenotionsof termsand subtermsarestandardin thelitterature,theyare notnecessarily the most convenient when working withequational theories. Accordingly, in this sectionand in addition to the standard notions, we introducethe sets of Subterms and Quasi-subterms of aterm. The notion of subterm of a term t is the standard one, whereas quasi-subterms are subterms of the flattening of t by successive applications of associativity rules. The notions of subterms and quasi-subterms are equivalent on normalized terms, but one of the difficulty of handling an equational theory is to analyzetheirinterplay when instantiating and normalizing atermmodulothisequationaltheory.We also provideafew technicallemmasto address thisquestion in thissubsection.
Definition 3.1.Let
A
be a set of atoms, andX
be a set of variables. LetF
be the minimal set of functional symbols containing: binary symbols pair,
enc,
aenc,
sig,
apply,
·
2, unarysymbols priv,
·
1,and for all i
∈ N
+ an i-nary symbol·
i. The set of termsT (A,
X )
is a minimal set satisfying:A
⊆ T
,X ⊆ T
, ift1,
. . . ,
tk are termsand f isak-ary symbolfromF
then f(
t1,
. . . ,
tk)
∈ T
. Tobe shortwe writeT
instead ofT (A,
X )
.By sig
(
p,
priv(
a))
we mean a signatureof message p withprivatekey priv(
a)
thatdoesnot con-tain a message itself (the message p together with its signature with private key priv(
a)
can be modeled as pair(
p,
sig(
p,
priv(
a)))
).We consider the following family of function symbols (indexed by their fixed arities):
S
i∈N+
{·
i}
. Symbol·
i has a list of i terms as its arguments. Since the arity can be inferred from the number of arguments, we write· (
t1,
t2)
as a shortcutfor·
2(
t1,
t2)
,· (
t1,
t2,
t3)
as ashortcut for·
3(
t1,
t2,
t3)
andso on.
We denote dom
(
σ
)
the domain{
x1, . . . ,
xn}
of a substitutionσ
= {
x17→
t1, . . . ,
xn7→
tn}
and img(
σ
) =
dom(
σ
)
σ
=
S
x∈dom(σ)
{
xσ
}
its image.The cardinalityof aset P isdenoted by|
P|
.We denote bin any element of
{
enc,
aenc,
pair,
sig,
apply}
. The root of a term t∈ T
is denoted root(
t)
and is defined as follows:root
(
t) =
bin,
if t=
bin(
p,
q) ;
·,
if t= · (
L) ;
priv,
if t=
priv(
p) ;
t,
if t∈
X
∪
A
.
We denote the i-thterm of alist of terms L as L
[
i]
and we write t∈
L if t occursas anelement of L. We alsodefinetwo binaryrelations⊆
and≈
on lists asfollows: L1⊆
L2 iffeveryelement of L1is anelement of L2; L1
≈
L2 iff L1⊆
L2 and L2⊆
L1 (weuse thesame definitionif L1 or L2 is aset).InDefinition 3.2wepresent algebraicpropertiesofthe
·
symbol(denotedas AC I),thatare consid-ered togetherwiththeDolev–Yaodeductionsysteminthissection.Intherestof thispaper deduction constraints are always modulothisACI equationaltheory.Definition3.2. We define
≡
AC I tobe the congruence relation onT
generatedby the equational the-ory AC I:{· (
y) =
y,
· (
y1,
y1) = · (
y1) ,
· (
y1,
y2) = · (
y2,
y1)} ∪
S
∞n=1
©· ¡
t1, . . . ,
tk, ·
¡
tk+1, . . . ,
tm¢ ,
tm+1, . . . ,
tn¢ = · (
t1, . . . ,
tn)
ª
0≤k<m≤n.
Since
·
isvariadic,theassociativityproperty isexpressedaboveasaninfinitesetof flatteningrules.Definition3.3. Thesetofelements of atermt
∈ T
isdenoted elems(
t)
and defined by:elems
(
t) =
(
S
p∈Lelems
(
p)
if t= · (
L) ;
{
t} ,
otherwise.We extend elems
()
to setsof termsor lists of terms T by elems(
T) =
S
t∈Telems
(
t)
.Example1.The set of elements of t
= · (
a, · (
b,
a,
pair(
a,
b)) ,
pair(· (
b,
b) ,
a))
is elems(
t) = {
a,
b,
pair(· (
b,
b) ,
a) ,
pair(
a,
b)}
.Definition3.4.Let
≺
be a strict total order onT
such that the question whether p≺
q can be an-swered in polynomial time.Definition3.5.The normalform of aterm t (denoted by
p
tq
) and a set of terms T (denoted byp
Tq
) is defined in amutually recursive way(ontheir size)by:(1)
p
tq =
t,if t∈ X ∪ A
;(3)
p
priv(
t)q =
priv(p
tq)
; (4)p· (
L)q =
·
¡
L′
¢ ,
if|p
elems(
L)q| >
1 and L′≈ p
elems(
L)q
and for all i
<
j,
L′[
i] ≺
L′[
j];
t′,
ifp
elems(
L)q =
©
t′ª
(5)
p
Tq = {p
tq :
t∈
T}
We say atermt is normalized ifft
= p
tq
.We note right away that
|
Tσ
|
≤ |
T|
and|p
Tq|
≤ |
T|
and two terms are congruent modulo the ACI properties of ′′.
′′ iff they have the samenormal form. Inparticular the following equalitieshold:p· (
t,
t)q = p
tq
,p· (
t1,
t2)q = p· (
t2,
t1)q
,p· (· (
t1,
t2) ,
t3)q = p· (
t1, · (
t2,
t3))q = p· (
t1,
t2,
t3)q
.Notealsothatnormalizationisidempotent:
pp
tqq = p
tq
.Moreovertheequivalencerelation≡
AC I isclosedundersubstitution (seeBaaderand Nipkow,1998),i.e.t1
≡
AC I t2impliest1σ
≡
AC I t2σ
.Therefore,we obtain t
≡
AC Ip
tq
and tσ
≡
AC Ip
tq
σ
, and thenp
tσ
q = pp
tq
σ
q
. Furthermorep
tσ
q = pp
tq
σ
q =
p
tp
σ
qq = pp
tq p
σ
Given its importance we turn thislastproperty into alemma. Lemma1. Foranytermt andsubstitution
σ
wehavep
tσ
q = pp
tq p
σ
Example2. InExample 1 we have
p
tq = · ({
a,
b,
pair(
a,
b) ,
pair(
b,
a)})
.We give some useful propertiesof elems
(·)
functionwithrespect to normalization.Lemma2.Foranytermt,
p
elems(
t)q =
elems(p
tq)
.Proof. Thisstatementis trivial,if t
6= · (
L)
. Otherwise,lett= · (
t1, . . . ,
tn)
.(1) If
p
elems(
t)q = {
p}
, where p6= ·
¡
Lp¢
. Then
p
tq =
p and then elems(p
tq) =
elems(
p) = {
p} =
p
elems(
t)q
;(2) If
p
elems(
t)q = {
p1, . . . ,
pk}
, k>
1, where pi6= · (
Li)
for all i. Thenp
tq = · (
L)
, where L≈
{
p1, . . . ,
pk}
. That meansthatelems(p
tq) =
S
p∈{p1,...,pk}elems
(
p) = {
p1, . . . ,
pk}
.✷
Lemma3.Foranytermst1
,
. . . ,
tm,wehavep· (p
t1q , . . . , p
tmq)q = p· (
t1, . . . ,
tm)q
Proof. Follows fromthe definitionof normal formand Lemma 2.
✷
Lemma4.Fortermst1
,
. . . ,
tm,wehave:elems
(p· (p
t1q , . . . , p
tmq)q) =
elems(· (p
t1q , . . . , p
tmq)) =
S
i=1,...,melems
(p
tiq)
Proof. We get the first equality by applying Lemma 2: elems
(p· (p
t1q , . . . , p
tmq)q) = p
elems(·(
p
t1q,
. . . ,
p
tmq))q
and then from Definition 3.3 and Lemma 2 we have that elems(· (p
t1q , . . . , p
tmq))
is a setof normalizedterms. Thesecond equalitydirectly followsfrom Definition 3.3.✷
We introducenowquasi
−
subterms as subtermsoftermsflattenedby applicationsof associativity rules.Definition3.6.The setof quasi-subtermsof termt is defined as follows:
QSub
(
t) =
{
t},
if t∈
X
∪
A
;
{
t} ∪
QSub(
t1) ,
if t=
priv(
t1) ;
{
t} ∪
QSub(
t1) ∪
QSub(
t2) ,
if t=
bin(
t1,
t2) ;
{
t} ∪
S
If T isasetof termsthen QSub
(
T) =
S
t∈TQSub
(
t)
. IfS = {
Ei✄
ti}
i=1,...,n isaconstraintsystemthenQSub
(S) =
S
t∈Sn
i=1Ei∪{ti}QSub
(
t)
.Example3. ReferringtoExample 1, we have
QSub
(
t) = {· (
a, · (
b,
a,
pair(
a,
b)) ,
pair(· (
b,
b) ,
a)) ,
a,
b,
pair(
a,
b) ,
pair(· (
b,
b) ,
a) , · (
b,
b)}.
Notealso thatQSub
(
QSub(
t)) =
QSub(
t)
and s= p
sq
for all s∈
QSub(p
tq)
. Letus nowdefinethe setSub(
t)
of subterms of aterm t.Definition3.7. Lett be aterm. We define Sub
(
t)
as follows:Sub
(
t) =
{
t},
if t∈
X
∪
A
;
{
t} ∪
Sub(
t1) ,
if t=
priv(
t1) ;
{
t} ∪
Sub(
t1) ∪
Sub(
t2) ,
if t=
bin(
t1,
t2) ;
{
t} ∪
S
p∈LSub
(
p) ,
if t= · (
L) .
If T is a set of terms, then Sub(
T) =
S
t∈TSub
(
t)
. IfS = {
Ei✄
ti}
i=1,...,n is a constraint system, wedefine Sub
(S) =
S
t∈Sn
i=1Ei∪{ti}Sub
(
t)
.Example4. ReferringtoExample 1, we have Sub
(
t) =
QSub(
t) ∪ {· (
b,
a,
pair(
a,
b))}.
Lemma5.Foranytermt andsubstitution
σ
,Sub(
tσ
) =
Sub(
t)
σ
∪
Sub(
Vars(
t)
σ
)
.Proof. By induction on
|
Sub(
t)|
• |
Sub(
t)| =
1.·
t∈ A
. As tσ
=
t and Vars(
t) = ∅
, the statementbecomestrivial;·
t∈ X
. Then Sub(
t)
σ
=
tσ
, Vars(
t) = {
t}
; and as for any term p, p∈
Sub(
p)
, we have Sub(
tσ
) = {
tσ
} ∪
Sub(
tσ
)
.•
Suppose thatfor anyt: |
Sub(
t)| <
k (k≥
1),the statementis true;•
Given atermt: |
Sub(
t)| =
k,k>
1. Letus consider all possiblecases:·
t=
bin(
t1,
t2)
. Then tσ
=
bin(
t1σ
,
t2σ
)
and Vars(
t) =
Vars(
t1) ∪
Vars(
t2)
. Sub(
tσ
) = {
tσ
} ∪
Sub
(
t1σ
) ∪
Sub(
t2σ
) = (
as|
Sub(
ti)| <
k)
= {
tσ
} ∪
Sub(
t1)
σ
∪
Sub(
Vars(
t1)
σ
) ∪
Sub(
t2)
σ
∪
Sub
(
Vars(
t2)
σ
) = {
tσ
} ∪
Sub(
t1)
σ
∪
Sub(
t2)
σ
∪
Sub((
Vars(
t1) ∪
Vars(
t2))
σ
) =
Sub(
t)
σ
∪
Sub
(
Vars(
t)
σ
)
;·
t=
priv(
t1)
. The proof isthe sameas for the previouscase;·
t= · (
t1, . . . ,
tm)
. Then tσ
= · (
t1σ
, . . . ,
tmσ
)
and Vars(
t) =
S
i=1,...,mVars(
ti)
. Then we have Sub(
tσ
) = {
tσ
} ∪
S
i=1,...,mSub
(
tiσ
) = (
as|
Sub(
ti)| <
k)
= {
tσ
} ∪
S
i=1,...,m(
Sub(
ti)
σ
∪
Sub(
Vars(
ti)
σ
))
= {
tσ
} ∪
S
i=1,...,mSub(
ti)
σ
∪
Sub¡¡S
i=1,...,mVars(
ti)
¢
σ
¢
=
Sub(
t)
σ
∪
Sub(
Vars(
t)
σ
)
.✷
Theinclusion relationbetween elems
(·) ,
QSub(·)
and Sub(·)
is statedin Lemma 6.Lemma6.Lett beaterm.Thenelems
(
t) ⊆
QSub(
t) ⊆
Sub(
t)
Fornormalizedterms, theset of its subtermscoincideswiththe setof its quasi-subterms: Lemma7.Foranynormalizedtermt,QSub
(
t) =
Sub(
t)
.Table 2
DY+ACI deductionrules.
Composition rules Decomposition rules
t1,t2→ penc(t1,t2)q enc(t1,t2) ,t3→ pt1q, if t2≡AC It3 t1,t2→ paenc(t1,t2)q aenc(t1,t2) ,priv(t3) → pt1q, if t2≡AC It3 t1,t2→ ppair(t1,t2)q pair(t1,t2) → pt1q
t1,priv(t2) → psig(t1,priv(t2))q pair(t1,t2) → pt2q
t1, . . . ,tm→ p· (t1, . . . ,tm)q · (t1, . . . ,tm) → ptiqfor all i
t1,t2→ papply(t1,t2)q
• |
Sub(
t)| =
1. Then t∈ X ∪ A
, and thus, QSub(
t) =
Sub(
t) = {
t}
;•
Supposethatfor any t: |
Sub(
t)| <
k (k>
1), QSub(
t) =
Sub(
t)
;•
Givenaterm t: |
Sub(
t)| =
k,k>
1. We need toshow thatQSub(
t) =
Sub(
t)
.·
t=
bin(
t1,
t2)
. Then QSub(
bin(
t1,
t2)) = {
t} ∪
QSub(
t1) ∪
QSub(
t2) = (
as|
Sub(
ti)| <
k)
= {
t} ∪
Sub
(
t1) ∪
Sub(
t2) =
Sub(
t)
;·
t=
priv(
t1)
. Then QSub(
priv(
t1)) = {
t} ∪
QSub(
t1) = {
t} ∪
Sub(
t1) =
Sub(
t)
;·
t= · (
L)
. As t is normalized,∀
p∈
L, root(
p) 6= ·
. Then elems(
L) ≈
L. Thus, we have QSub(
t) =
{
t} ∪
S
p∈elems(L)QSub(
p) = {
t} ∪
S
p∈LQSub(
p) = {
t} ∪
S
p∈LSub(
p) =
Sub(
t)
.✷
Lemma8.Foranytermt,QSub
(p
tq) = p
QSub(
t)q
.Proof. By induction on
|
Sub(
t)|
.• |
Sub(
t)| =
1. Then t∈ A
∪ X
. As QSub(
t) = {
t}
and t= p
tq
, the statementholds;•
Supposethatfor any t: |
Sub(
t)| <
k (k>
1), thestatement istrue;•
Givent such that|
Sub(
t)| =
k,k≥
1, letus considerall possiblecases:(1) t
=
bin(
t1,
t2)
. On the one hand, QSub(
t) = {
t} ∪
QSub(
t1) ∪
QSub(
t2)
. On the other hand,p
tq =
bin(p
t1q , p
t2q)
and then, QSub(p
tq) = {p
tq} ∪
QSub(p
t1q) ∪
QSub(p
t2q)
. Then, asQSub
(p
tiq) = p
QSub(
ti)q
, we have thatQSub(p
tq) = p
QSub(
t)q
; (2) t=
priv(
t1)
. Theproof is the sameas for previouscase;(3) t
= · (
L)
.WehaveQSub(
t) = {
t} ∪
S
p∈elems(L)QSub
(
p)
;FromLemma 2wehaveelems(p· (
L)q)
= p
elems(· (
L))q
, and then we obtain QSub(p· (
L)q) = {p· (
L)q} ∪
S
p∈elems(p·(L)q)QSub
(
p) =
p{· (
L)}q ∪
S
p∈elems(·(L))QSub
(p
pq) =
(by supposition)= p{· (
L)}q ∪
S
p∈elems(·(L))
p
QSub(
p)q =
p{· (
L)} ∪
S
p∈elems(·(L))QSub
(
p)q = p
QSub(
t)q
.✷
Lemma9.Foranytermt,Sub
(p
tq) ⊆ p
Sub(
t)q
.Proof. From Lemma 7 we have Sub
(p
tq) =
QSub(p
tq)
. By Lemma 8 we obtain QSub(p
tq) =
p
QSub(
t)q
and by Lemma 6 we have QSub(
t) ⊆
Sub(
t)
. Thus, Sub(p
tq) ⊆ p
QSub(
t)q ⊆ p
Sub(
t)q
.✷
3.2. Dolev–YaodeductionsystemmoduloACIWe definea Dolev–Yao deductionsystem modulo ACI (denoted DY
+
ACI). It consists of composi-tion rules and decomposition rules, depicted in Table 2 where t1,
t2,
. . . ,
tm∈ T
(i.e., we consider an infinite systemhavingafiniterepresentationgivenin thetable). Notethatrule enc(
t1,
t2) ,
t3→ p
t1q
,if t2
≡
AC It3 is equivalent to enc(
t1,
t2) , p
t2q → p
t1q
, sinceit is always possibleto normalizeterm t3(and obtain
p
t3q = p
t2q
) using, e.g. t3,
t3→ p
pair(
t3,
t3)q
and sincep
pair(
t3,
t3)q =
pair(p
t3q , p
t3q)
we candecompose itby obtaining
pp
t3qq = p
t3q
.We introduce two restrictions todefine asubset of valid groundterms. Thefirst one follows from the semantics of the functional symbol sig: its second argument must always be a private key. The second one is imposed in order to simplify our reasoning for solving constraint systems: we only consider atomicasymmetricprivatekeys (thisis notareallimitation for many applications).
Definition3.8. Agroundterm t isvalid ifffor any subterm s
∈
Sub(
t)
:(1) s
=
sig(
p,
q) =⇒ p
qq =
priv¡
q′¢
for some q′;
(2) s
=
priv(
p) =⇒ p
pq ∈ A
We suppose hereinafter that the considered constraint system
S
contains at least one atom, i.e. QSub(S) ∩ A
6= ∅
. Otherwise we add a dummy constraint{
a} ✄
a toS
which will be satisfied by any substitution. We define priv(
T) = {
priv(
t) :
t∈
T}
for a set of terms T . We define Vars(S) =
S
ni=1Vars
(
Ei) ∪
Vars(
ti)
. We say thatS
isnormalized, iff for all t∈
Sub(S)
,t is normalized.Example5. Wegiveaexampleofgeneralconstraintsystemandits solutionwithinDY
+
ACI deduction system.S
=
½
enc(
x,
a) ,
pair(
c,
a) ✄
b· (
x,
c)
✄
a¾
,
where a
,
b,
c∈ A
and x∈ X
. One of its solutionswithin DY+
ACI isσ
= {
x7→
enc(
pair(
a,
b) ,
c)}
. Definition3.9. Let T= {
t1, . . . ,
tk}
be anon-empty setof terms.Then we defineπ
(
T)
as follows:π
(
T) = p· (
t1, . . . ,
tk)q .
We remark that
π
({
t})
= p
tq
andπ
(
T)
= p
π
(
T)q
. Note also thatπ
(
t1,
. . . ,
tk)
can be interpreted as aset ofterms. The termsderivablefromπ
(
t1,
. . . ,
tk)
are derivable fromt1,
. . . ,
tk and vice-versa. Lemma10.LetT beasetoftermsT= {
t1, . . . ,
tk}
.Thenπ
(
T)
∈
Der(p
Tq)
andp
Tq ⊆
Der({
π
(
T)})
.FromLemma 3 we derive another property:
π
(
T)
=
π
(p
Tq)
. Lemma11.π
(
T1∪ · · · ∪
Tm)
=
π
({
π
(
T1), . . . ,
π
(
Tm)})
Proof. Fromdefinitionof
π
andLemma 2, wehaveelems(
π
(
Ti)) = p
elems(
Ti)q
.Nextπ
({
π
(
T1),
. . . ,
π
(
Tm)})
= p· (
L)q
where L≈ p
elems({
π
(
T1), . . . ,
π
(
Tm)})q
= p
[
i=1,...,mp
elems(
Ti= p
[
i=1,...,m elems(
Ti)q
Onthe other hand
π
(
T1∪ · · · ∪
Tm)
= p·
¡
L′¢
q
, where L′≈ p
S
i=1,...,melems(
Ti)q
.✷
3.3. SolvingthederivabilityproblemofDY+
ACIThe decidability of the derivability problem for DY has been extensively studied (see e.g. Amadio and Lugiez, 2000 for the atomic keys case, and Rusinowitch and Turuani, 2003 for the complex keys case) and is known to be polynomial. Also, we note that the derivability problem when the set of symbols only containsthe dot
·
and constantsis trivial, for in thiscase aconstraint E✄
t is satisfiedif, and only if, the constants occurring in t also occur in E (proof left to the reader). Then the com-bination algorithm of Chevalierand Rusinowitch (2005) yieldsdirectly the decidability of derivability for the DY