Abstract
This paper examines the reasons citizens would choose to accept or non-accept/reject public e-services. The approach taken was based on the model of acceptance of technology in households (MATH) and on the two factors theory. The research model was measured with data gathered in two phases, via interviews with open-ended questions in the first stage, and through survey with questionnaire in the second phase. Results of the qualitative and the quantitative studies show that only a small percentage of Lebanese intended to accept government e-services. Perceived usefulness (PU), perceived government support (PGS), computer self efficacy (CSE), and perceived government influences (PGI) are the key drivers of the e-services acceptance intention (AI). For the non-intenders, barriers like fear of government control (FGC), lack of trust in the secu-rity (TSEC), lack of trust in the privacy (TPRI), lack of support (PGS), and lack of knowledge (CSE) were most significant. In the two studies, the fear of gov-ernment control (FGC) was the most important deter-minant, both in terms of frequency and in terms of importance. The willingness to use the public e-services will be present if governments can develop trust relationships with individuals, assure them that their financial details are secure, that these services will respect the privacy of citizens, and she will not use e-services in order to increase control.
Key-words:
E-government, e-services acceptance, MATH, TPB, ICT acceptance intention, ITA e-Gov Model
.
influence
the
acceptance or rejection
of public e-services in
Lebanon
Référence : 22
Antoine
HARFOUCHE
Maitre de Conférence au CREPA
Université Paris-Dauphine
Place du Maréchal de Lattre de Tassigny 75775 PARIS Cedex 16
Tél. : +33 (0)1 44 05 44 05 Fax : +33 (0)1 44 05 49 49
Antoine.harfocuhe@dauphine.fr
Stephane Bourlitaux-Lajoinie
Maitre de Conférences à l‟IAE de Tours, Labora-toire CERMAT
Directeur du M2 Marketing des Services Tel : + 33 (0)2 47 36 10 42
Introduction
Research in information systems (IS) is concerned with identifying the factors that facilitate or impede the accep-tance and rejection (or non-accepaccep-tance) (Bagozzi 2007) of e-services by citizens. Researchers seek to understand the user‟s behavior by placing the individual at the center of the inquiry. Understanding why people accept or reject e-services or other information and communication tech-nologies (ICTs) is one of most challenging issues in this domain.
While ICTs acceptance in the workplace and at home has been studied extensively, little systematic research has been conducted to understand the determinants of accep-tance of online public services by citizens. Government e-service acceptance by citizens is a substantial global problem. Indeed, research shows that providing e-service access and creating conditions for its usage does not guarantee e-service acceptance by the citizens (Dwivedi et al. 2009; UNDESA 2008; UNPAN 2005). Until today, studies have shown that e-government initiatives have failed to engage citizens. Despite incentives and media campaigns that encourage citizens to go online for gov-ernment transactions, most citizens of developing coun-tries do not use government e-services and prefer to use traditional face-to-face services (UNDESA 2008; UNPAN 2005). Therefore, the success of e-government will depend on whether governments are able to entice citizens to accept and use online public services. Today, in addition to the face-to-face service delivery system, the Lebanese government is introducing the vir-tual channel of service delivery system (VCSDS). This multichannel of service delivery system will allow the government to offer two types of public service: tradi-tional services and online services. As a result, the Leba-nese government is appreciating the need to increase citi-zens‟ awareness regarding the transition to online deli-very of public services. Therefore, the Lebanese govern-ment needs to better understand the factors that affect the e-services acceptance or rejection (or non-acceptance) intention.
According to van Dijk et al. (2008) a theory of the accep-tance of public e-services is lacking. They also asserts that this kind of theory have to be derived from a general theory of acceptance and use of ICTs applied to the spe-cial context of the government to citizens (van Dijk et al. 2008, p. 383). In this article, we begin working on such a theory. Therefore, this paper develops an integral model of individuals‟ intention to accept or reject e-government services (ITA e-Gov Model). It captures the influence of different external and internal factors (enablers and inhi-bitors) on government e-services acceptance/ rejection at the first stages of the acceptance process. Based on the model of acceptance of technology in households
(MATH) conceptualized and measured by Brown and Venkatesh (2001; 2005) and on Cenfetelli (2004) two factors theory, the ITA e-Gov Model focuses on the asso-ciation between (1) public e-services perceived outcomes (2) citizens‟ personal variables, (3) social influences, and (4) contextual factors, and their evaluations in the first stages of the acceptance process. Developed from the theory of planned behavior (TPB, e.g. Ajzen 1991) and the decomposed theory of planned behavior (DTPB, e.g. Taylor and Todd 1995a), MATH is suggested as an ideal framework for understanding ICT acceptance outside the workplace (Hsieh et al. 2008).
The ITA e-Gov Model was designed to capture the rea-sons for acceptance or rejection (or non-acceptance) of public e-services in the Lebanese context. In order to examine the inhibitors and enablers of the citizens‟ inten-tion to accept e-services, data was collected in a first stage from 188 randomly chosen potential Lebanese pub-lic e-service users. In Phase 1, open-ended questions were asked about government e-services acceptance/non-acceptance intention, and about reasons for such accep-tance or non-accepaccep-tance. Then, the 188 answers were double coded based on a start list of beliefs (Miles and Huberman 1984) that included variable definitions se-lected from prior research. After identifying salient be-liefs of public e-services acceptance in Lebanon, the re-search model and the questionnaire were developed. In Phase 2, we used a quantitative method. We surveyed 210 Lebanese potential public e-services users. The aim was to understand the weight that the individual gave to each variable. Therefore, respondents were asked to rate each factor from the salient beliefs from 1 to 7 based on how important it was in their acceptance or non-acceptance decision.
The ITA e-Gov Model could help governments better deploy and manage their ICT investments by better un-derstanding their citizens. Extensive efforts are necessary to increase citizens‟ awareness about the transition to the online delivery of government services. Government communication could incorporate the variables that influ-ence e-service acceptance intention.
In this paper, we begin by reviewing the technology ac-ceptance literature. Then, we review the public e-services acceptance literature. Based on prior research, a start list of beliefs related to public e-service acceptance has been created. After having defined each variable, we compare respondents‟ answers to the start list. Then, we summar-ize the conceptual model of the public e-services accep-tance intention by citizens. Finally, after testing the mod-el, we describe in the conclusion the lessons learned from this study. We also highlight the limitations and future directions.
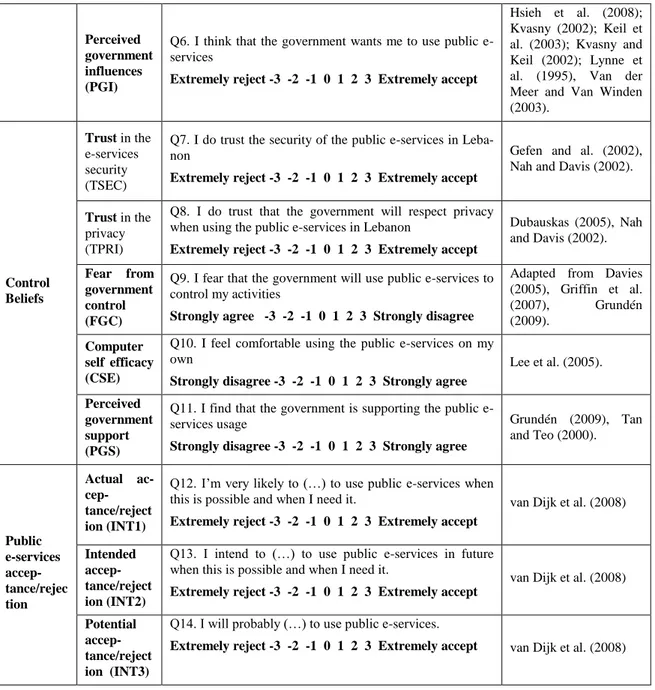
1. Constructs that shape the
pub-lic e-services acceptance process
One of the main reasons of difficulties that developing countries face when implementing e-government, is the low public e-services‟ acceptance and use by citizens (Heeks 1999; Jaeger and Thompson 2003; Moon 2002; Odedra-Straub 2003). Indeed, providing e-service access and creating conditions for its usage (access and e-skills) does not guarantee the acceptance and use of pub-lic e-services by citizens. Research indicates that in de-veloping countries, e-government offerings have failed to capture the imagination of the citizens (Dwivedi et al. 2009). Understanding the reasons of such low acceptance and use may allow opportunities to develop more effec-tive government policies. Thus, success of e-government will depend on how e-governments entice citi-zens to accept and use online public services. Therefore, governments need to better understand the factors that influence the e-services acceptance/rejection by citizens. According to Schwaerz and Chin (2007), ICT acceptance “involves a holistic conjunction of a user‟s behavioral interaction with the ICT over the time and his or her psy-chological understanding/willingness or resis-tance/acceptance that develops within a specific so-cial/environmental/organizational setting. The accepta-tion process may be conceptualized as a temporal se-quence of activities that lead to initial acceptance and subsequent adaptation and continued usage of an ICT by the adopter.
1.1 Factors Influencing ICT
Accep-tance
Key constructs that shape the ICT acceptance process are numerous. Based on Schwaerz‟s and Chin‟s (2007) defi-nition and on diffusion of innovation theory (Rogers 1983), these key constructs are divided to four categories: (1) ICT's perceived attributes and characteristics; (2) so-cial influences and communication concerning the ICT innovation received by the individual from his social environment (3) individual differences and psychological processes, and finally (4) the environmental influences such as contextual factors.
The IS community has deeply investigated the relation between these constructs. Indeed, twenty years ago, Davis presented the most influential and commonly employed theory in this domain (Lee et al. 2003): the technology acceptance model (TAM). This model, presented as a simplified adaptation of the theory of reasoned action (TRA) and the theory of planned behavior (TPB) in the IS context, has became a dominant paradigm (Straub and Burton-Jones 2007). Ten percent of the total journal ca-pacity in the IS field has been occupied with TAM stu-dies (Lee et al 2003). The Journal of the Association of Information Systems has even devoted a Special Issue in 2007 for the TAM research entitled “Quo Vadis TAM”.
But, fourteen years after TAM, by presenting the unified theory of acceptance and use of technology (UTAUT, e.g. Venkatesh et al. 2003) that synthesizes a large number of TAM research, Venkatesh et al., ironically conveyed us back to the TAM‟s origin: the TPB (Benbasat and Barki 2007).
Therefore, in order to explain the reasons for acceptance or rejection (non-acceptance) of e-services by Lebanese, we have selected one of the most useful theories in the ICT voluntary acceptance context: the model of accep-tance of technology in households (MATH, e.g. Brown and Venkatesh 2005; Venkatesh and Brown 2001). The MATH model extends the theory of planned behavior (TPB, e.g. Ajzen 1991) by decomposing the beliefs that comprise the attitude which determine the behavior inten-tion (IA).
We think that MATH is more relevant than TAM because MATH introduces a large number of factors that may influence the acceptance/rejection of ICTs and e-services. MATH allows the integration of more contextual beliefs in the acceptance process. Indeed, according to the MATH, ICT “acceptance intention” (IA) is a weighted function of attitudinal, normative, and the control beliefs structure. Attitudinal, normative, and the control beliefs are decomposed into multi-dimensional beliefs structures.
1.1.1
Attitudinal beliefs
According to TRA, there are two kinds of attitudes: (1) the individual‟s attitude towards the ICT (AICT) and attitude concerning the ICT acceptance and use (Aacp). Attitude toward the ICT represents a summary evaluation of the ICT captured in such attribute dimensions as good/bad, harmful/beneficial, likable/dislikable (Ajzen and Fishbein 2000). Attitude toward ICT acceptance and use (Aacp) is defined as a person's favorable/unfavorable evaluation of the ICT acceptance and use. According to Fishbein and Ajzen (1975), attitudes toward an innova-tion (AICT) do not strongly predict innovainnova-tion accep-tance and use (IA). Only the individual‟s attitude con-cerning the acceptance of an innovation (Aacp) deter-mines its acceptance intention (IA). The individual‟s attitude towards the innovation (AICT) influences the ICT acceptance (IA) indirectly through influencing the attitude concerning ICT acceptance and use (Aacp). The individual‟s attitude toward accepting an ICT (Aacp) is the function of the perceived consequences and out-comes that result from the acceptance and the usage of the ICT. According to the decomposed theory of planned behavior (DTPB, e.g., Taylor and Todd 1995a; 1995b) and to MATH, attitude belief can be decomposed to a set of attitudinal beliefs that derive from the literature which describe the perceived characteristics of an innovation. Indeed, in the Diffusion of Innovation Theory (IDT, summarized in Table 1), Rogers indicates five ICT attributes that are associated with the ICT acceptance
process: relative advantage, compatibility, complexity (or ease of use), observability, and trialability (Rogers 1995).
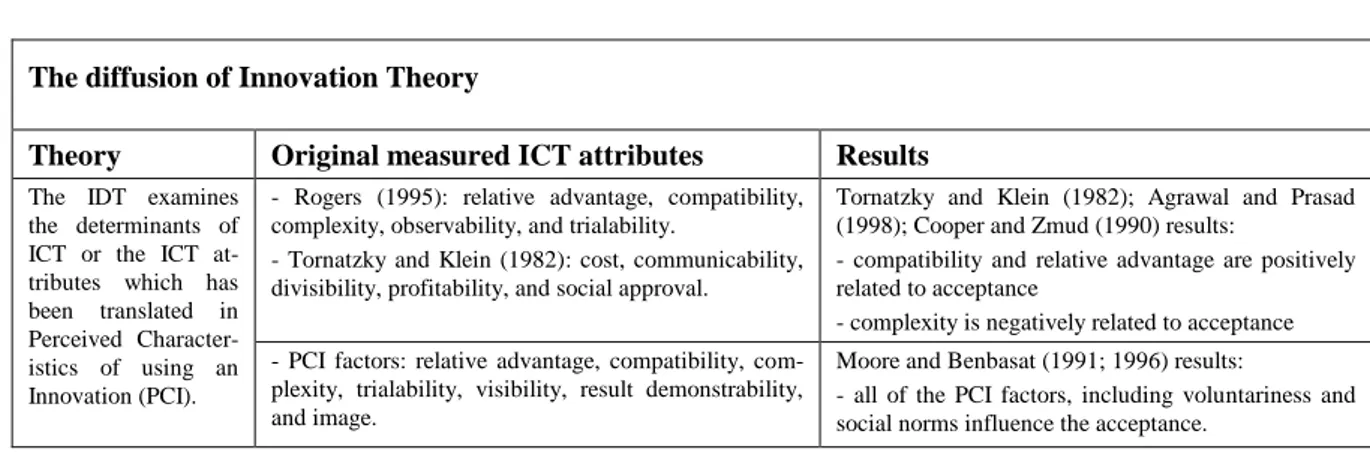
The diffusion of Innovation Theory
Theory Original measured ICT attributes Results
The IDT examines the determinants of ICT or the ICT at-tributes which has been translated in Perceived Character-istics of using an Innovation (PCI).
- Rogers (1995): relative advantage, compatibility, complexity, observability, and trialability.
- Tornatzky and Klein (1982): cost, communicability, divisibility, profitability, and social approval.
Tornatzky and Klein (1982); Agrawal and Prasad (1998); Cooper and Zmud (1990) results:
- compatibility and relative advantage are positively related to acceptance
- complexity is negatively related to acceptance - PCI factors: relative advantage, compatibility,
com-plexity, trialability, visibility, result demonstrability, and image.
Moore and Benbasat (1991; 1996) results:
- all of the PCI factors, including voluntariness and social norms influence the acceptance.
Table 1. This Table resumes the ICT attributes according to the diffusion of Innovation Theory
Tornatzky and Klein (1982), after analyzing 105 research papers related to the IDT, identified five more characte-ristics: cost, communicability, divisibility, profitability, and social approval. But, in their conclusion, they argued that communicability and divisibility are closely related to observability and to trialability.
Based on the TRA‟s (e.g. Fishbein and Ajzen 1975) as-sumption that users think about an ICT in terms of their consequences not their attributes, Moore and Benbasat (1991, p. 195; 1996) redefined the Rogers‟ five variables in terms of usage consequences. They presented the full
set of perceived characteristics of using an innovation (PCI) by adding image and willingness of use, and by dividing observability into visibility and result demon-strability (e.g. Moore and Benbasat 1991, p. 202). They also argued that the relative cost of an innovation (or perceived cost) has a great effect on acceptance behavior. But they did not include it in their research because they were studying the ICT acceptance by employees within organizations. Table 2 summarizes the definition of these concepts.
Perceived characteristics of using an Innovation (PCI)
Concepts Definition Sources Redefined by… as …
Relative advan-tage
The degree to which an innovation is perceived as being better than its pre-cursor.
Rogers‟ IDT (1995, p.15).
Moore and Benbasat (1991) redefined “relative advan-tage” as the degree to which using the ICT innovation is perceived as being better than using its precursor. Compatibility The degree to which an innovation is
perceived as being consistent with the existing values, past experiences, and needs of potential adopters.
Moore and Benbasat (1991) redefined “compatibility” as the degree to which using this ICT is perceived as being consistent with the existing values, needs, and past experiences of potential adopters.
Complexity The degree to which an innovation is perceived as being difficult to under-stand and use.
Moore and Benbasat (1991) redefined “complexity” as ease of use.
Trialability The degree to which an innovation may be experimented with on a limited basis before acceptance.
Moore and Benbasat (1991) redefined “trialability” as the degree to which an innovation ICT may be experi-mented before acceptance.
Observability The degree to which the results of an innovation are visible and communica-ble to others.
Moore and Benbasat (1991) redefined “observability” as the degree to which the results of using the innova-tion ICT are observable to others. They found that “ob-servability” has construct ambiguity problems, so they divided it into visibility and result demonstrability. Cost Introduced by Tornatzky and Klein
(1982)
Tornatzky and Klein (1982)
Moore and Benbasat (1991) redefined it as relative cost or perceived cost.
Communicabil-ity
Closely related to observability. Moore and Benbasat (1991) redefined it as “observabil-ity”.
Divisibility Closely related to trialability. Moore and Benbasat (1991) redefined it as “trialabil-ity”.
Profitability Introduced by Tornatzky and Klein (1982).
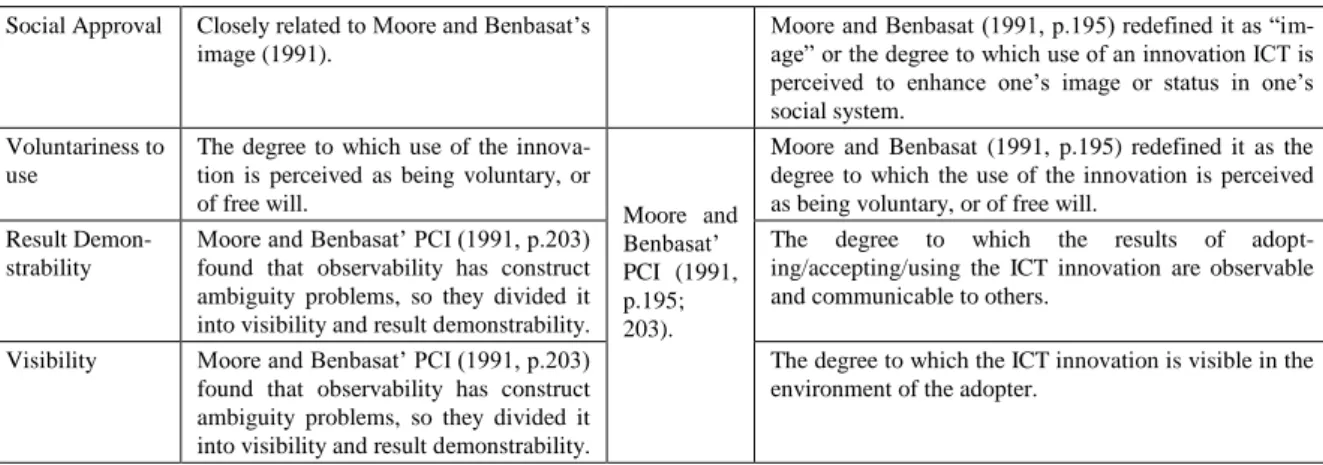
Social Approval Closely related to Moore and Benbasat‟s image (1991).
Moore and Benbasat (1991, p.195) redefined it as “im-age” or the degree to which use of an innovation ICT is perceived to enhance one‟s image or status in one‟s social system.
Voluntariness to use
The degree to which use of the innova-tion is perceived as being voluntary, or
of free will. Moore and Benbasat‟ PCI (1991, p.195; 203).
Moore and Benbasat (1991, p.195) redefined it as the degree to which the use of the innovation is perceived as being voluntary, or of free will.
Result Demon-strability
Moore and Benbasat‟ PCI (1991, p.203) found that observability has construct ambiguity problems, so they divided it into visibility and result demonstrability.
The degree to which the results of adopt-ing/accepting/using the ICT innovation are observable and communicable to others.
Visibility Moore and Benbasat‟ PCI (1991, p.203) found that observability has construct ambiguity problems, so they divided it into visibility and result demonstrability.
The degree to which the ICT innovation is visible in the environment of the adopter.
Table 2 Perceived characteristics of using an Innovation (PCI)
Perceived usefulness (PU) and perceived ease of use (PEU), proposed by Davis (1989) and Davis et al. (1989) in TAM, are attributed to the PCI (Davis 1993; Davis et al. 1989).
Based on the decomposed theory of planned behavior (DTPB), the model of acceptance of technology in households (MATH, e.g. Brown and Venkatesh 2005; Venkatesh and Brown 2001) decomposes the attitudinal beliefs in: utilitarian outcome (UO), hedonic outcome (HO), and social outcomes (SO).
2.1.1.1. Utilitarian outcomes
Utilitarian outcomes (UO) adapt the rational basis for ICT acceptance which is usually characterized by the perceived usefulness of the ICT (Davis 1989; Davis et al. 1989, p.320) to the households‟ context. As summarized in Table 3, PU is equivalent to Rogers‟ “relative advan-tage” (Rogers 1983; Moore and Benbasat 1991), to Com-peau and Higgins‟ “outcome expectations” (1995b), to Davis et al.‟s “extrinsic motivation” (1992), to Thompson et al.‟s (1991) “job-fit”, and to Venkatesh et al.‟s (2003) “performance expectancy”. The utilitarian outcomes (UO) can be defined as the extent to which using an ICT can enhances the effectiveness of user‟s activities.
Utilitarian outcomes
Constructs Similar
constructs
Model Authors Definition
Utilitarian out-comes (MATH, e.g. Brown and Venkatesh 2005; Venkatesh and Brown 2001) Perceived use-fulness (PU)
TAM Davis (1989); Davis et al. (1989, p. 320)
The degree to which a person believes that using a particular system would enhance his or her job per-formance
Performance expectancy
UTAUT Venkatesh et al. (2003, p. 447)
The degree to which an individual believes that using the system will help him or her to attain gains in job performance.
Extrinsic Moti-vation
MM Davis et al. (1992, p. 1112)
The perception that users will want to perform an activity because it is perceived to be instrumental in achieving valued outcomes that are distinct from the activity itself, such as improved job performance, pay, or promotions.
Job Fit MPCU Thompson et al. (1991, p. 129)
The extent to which an individual believes that using an ICT can enhance the performance of his or her job. Relative
advan-tage
IDT Rogers (1983); Moore and Benbasat (1991, p. 195)
The degree to which an innovation is perceived as being better than its precursor.
Outcome ex-pectation
SCT Compeau and Hig-gins (1995b)
The performance related consequences of the behav-ior. Specifically, the performance expectations that deal with job related outcomes.
Table 3. Utilitarian outcomes
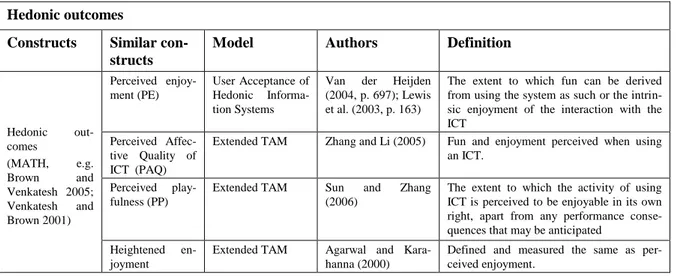
2.1.1.2. Hedonic outcomes (HO)
Hedonic outcomes can be defined as the pleasure derived from the acceptance and usage of an ICT. Hedonic out-comes (HO) adapt hedonic and affective ICT attributes. Indeed, recently, IS scholars have included hedonic crite-ria and affective ICT attributes like: perceived enjoyment
(PE, Van der Heijden 2004; Sun and Zhang 2006), per-ceived affective quality of ICT (Zhang and Li 2005), heightened enjoyment (Agarwal and Karahanna 2000), and perceived playfulness (Sun and Zhang 2006). Table 4 summarizes these constructs that comprise the pleasure or
entertainment potential derived from the interaction with the ICT. Hedonic outcomes
Constructs Similar con-structs
Model Authors Definition
Hedonic out-comes (MATH, e.g. Brown and Venkatesh 2005; Venkatesh and Brown 2001) Perceived enjoy-ment (PE) User Acceptance of Hedonic Informa-tion Systems
Van der Heijden (2004, p. 697); Lewis et al. (2003, p. 163)
The extent to which fun can be derived from using the system as such or the intrin-sic enjoyment of the interaction with the ICT
Perceived Affec-tive Quality of ICT (PAQ)
Extended TAM Zhang and Li (2005) Fun and enjoyment perceived when using an ICT.
Perceived play-fulness (PP)
Extended TAM Sun and Zhang (2006)
The extent to which the activity of using ICT is perceived to be enjoyable in its own right, apart from any performance conse-quences that may be anticipated
Heightened en-joyment
Extended TAM Agarwal and Kara-hanna (2000)
Defined and measured the same as per-ceived enjoyment.
Table 4. Hedonic outcomes
2.1.1.3. Social outcomes
Social outcomes (SO) refer to the image or the power that the ICT acceptance gives to the user within his social group. Social outcomes include the image or status gains, result demonstrability and visibility (Venkatesh and Brown 2001). These construct were defined in Table 2. Karahana et al. (1999), in the decomposed theory of rea-soned action (DTRA, e.g. Karahana et al. 1999) argued that social outcomes play an important role in the accep-tance process especially in the pre-accepaccep-tance period. DTRA results show that visibility and result demonstra-bility are strong predictors of ICT acceptance but only in the first phase of the acceptance process, while percep-tion of image enhancement can predict ICT continued usage in the post acceptance phase. According to MATH, status gains impact on the acceptance of ICT increases with the user‟s age (Brown and Venkatesh 2005).
2.1.1.4. Control outcomes
In addition to the MATH‟s utilitarian outcome (UO), hedonic outcome (HO), and social outcomes (SO), we include the control outcomes (CO). The control outcomes (CO) refer to the perceived characteristics of an ICT re-lated to the control, like compatibility, trialability, rela-tive cost, declining cost, and complexity or PEU. Control outcomes (C0) differ from the perceived behavioral con-trol that refers to the internal personal variables and to the external resources, contextual, and environmental va-riables. Control outcomes are only related to ICT per-ceived characteristics. The most measured and used vari-able between the control outcomes is PEU. As summa-rized in Table 5, PEU is similar to “perceived complexi-ty” (Rogers 1983; Thompson et al. 1991), to “effort ex-pectancy” (UTAUT, Venkatesh et al. 2003), and to Thompson et al.‟s “complexity” (1991).
Perceived ease of use construct
Constructs Similar
constructs
Model Authors Definition
Perceived ease of use (PEU)
The degree to which an individual believes that performing the behavior of interest would be free of effort.
Effort expec-tancy
UTAUT Venkatesh et al. (2003, p. 450)
The degree of ease associated with the use of the system. Perceived complexity IDT Rogers 1983; Thompson et al. (1991)
The degree to which an innovation is perceived as being difficult to understand and use. Complexity MPCU Thompson et al.
(1991, p. 128)
The degree to which an innovation is perceived as relatively difficult to understand and use. Table 5. Perceived ease of use construct according to the TAM (Davis 1989; Davis et al. 1989, p.320).
1.1.2
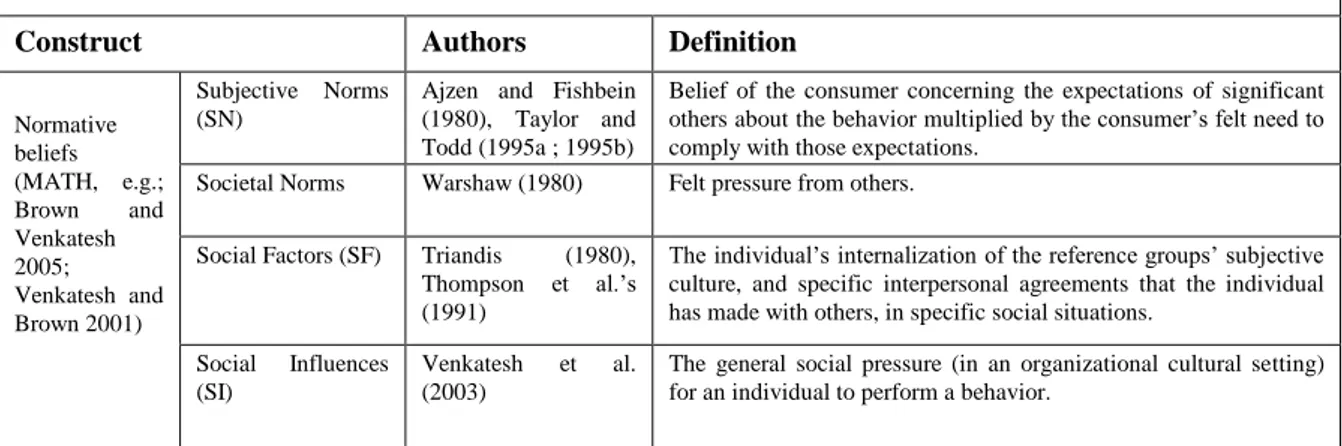
Normative beliefs
Prior research presented evidence that subjective norms and social influences (friends and family influences FFI and workplace referents‟ influences WRI) play a key role in ICT acceptance, especially in the first stages of the acceptance process (Karahana et al. 1999; Thompson et al. 1991; Triandis 1971) and/or when users' knowledge concerning the ICT are vague (Hartwick and Barki 1994).
As summarized in Table 6, the subjective norms construct (TRA e.g. Ajzen 1991, TPB e.g. Fishbein and Azjen 1975; C-TAM-TPB e.g. Taylor and Todd 1995a; 1995b ; and Matheison 1991) is equivalent to the social influ-ences construct (Venkatesh et al. 2003), to the social factors construct (Triandis 1980; Thompson et al. 1991), and to societal norms (Warshaw 1980).
According to Fishbein and Azjen (1975), Ajzen (1991), and Taylor and Todd (1995a; 1995b), a person's
subjec-tive norms (SN) may be influenced indirectly, for exam-ple, when the person infers that others think he or she should use a system, or directly by other individuals, for example, when referents tell the person that they think he or she should use a system. The direct compliance effect of subjective norms (SN) on intention to accept ICT (IA) was identified in TRA, TPB, C-TAM-TPB, and MPCU theories. This has also been proven by Hartwick and Bar-ki (1994) in a mandatory context, but not in voluntary usage contexts. Venkatesh and Brown (2001) have also proven that the acceptance intention (IA) is influenced by messages and stimuli conveyed via mass media and sec-ondary sources like News, Newspapers, TVs, and radios
(Secondary Sources‟ Influences, SSI). In addition, TAM2 reflects the impact of two additional theoretical mechan-isms: internalization and identification. Subjective norms, also, includes the personal network exposure (PNE, e.g. Hsieh et al. 2008; Valente 1995, p. 70) of the potential adopters. Indeed, individuals‟ ICT acceptance intention (IA) can also be influenced by how other members in the individual‟s personal network respond to this ICT inno-vation. The personal network exposure (PNE) accounts for the observed aggregate ICT acceptance behaviors in an individual‟s personal network (Hsieh et al. 2008; Va-lente 1995, p. 70).
Normative beliefs construct
Construct Authors Definition
Normative beliefs (MATH, e.g.; Brown and Venkatesh 2005; Venkatesh and Brown 2001) Subjective Norms (SN)
Ajzen and Fishbein (1980), Taylor and Todd (1995a ; 1995b)
Belief of the consumer concerning the expectations of significant others about the behavior multiplied by the consumer‟s felt need to comply with those expectations.
Societal Norms Warshaw (1980) Felt pressure from others. Social Factors (SF) Triandis (1980),
Thompson et al.‟s (1991)
The individual‟s internalization of the reference groups‟ subjective culture, and specific interpersonal agreements that the individual has made with others, in specific social situations.
Social Influences (SI)
Venkatesh et al. (2003)
The general social pressure (in an organizational cultural setting) for an individual to perform a behavior.
Table 6. Normative beliefs construct.
Consequently, subjective norms (SN) include friends and family influences (FFI), secondary sources‟ influences (SSI), and workplace referents‟ influences (WRI), with personal network exposure (PNE).
1.1.3
Control beliefs
In general, perceived behavioral control (PBC) refers to the user‟s ability to control the behavior. Ajzen (1991) defined Perceived behaviour control (PBC) as both inter-nal psychological determinant related to the target beha-viour and to external resource and contextual constraints. Consequently, PBC results only from the user‟s personal variables and from the contextual factors.
2.1.3.1. Individual differences and
psychologi-cal determinants
Researchers have studied a range of individual user cha-racteristics that influence the acceptance or non-acceptance of the ICT innovation. Between all the indi-vidual characteristics, only one trait variable is specific to ICT and refers to comparatively stable characteristics of individuals which is invariant to situational stimuli: Computer self efficacy (CSE). According to Compeau and Higgins (1995a), computer self efficacy (CSE) can predict ICT acceptance intention (IA). As defined in Ta-ble 7, computer self efficacy (CSE) refers to the individu-al's perceptions of his or her ability to use ICT in the ac-complishment of a specific task (Compeau and Higgins 1995a; 1995b). Computer self efficacy (CSE) is
equiva-lent to computer plaSyfulness (CP, Webster and Martoc-chio 1992; Moon and Kim 2001) and to personal innova-tiveness in ICT (PIIT, Agrawal and Prasad 1998; Agraw-al and Karahanna 2000).
2.1.3.2. Contextual factors
External control factors vary from context to context (Aj-zen 2001) and depend on the situation. External control factors consist of a large number of constructs like: MPCU‟s Thompson et al.‟s (1991) facilitating conditions (Venkatesh et al. 2003), Igbaria et al.‟s (1996) end user support. Hartwick and Barki (1994) proved that control evaluation is also related to the resources available for the individual (such as: money, time, and information) that can be a barrier inhibiting acceptance (such as: low fi-nancial resources, lack of time, or low experience). Control beliefs are also related to trust. Indeed, according to Gefen (2000), trust is a complex, multi-dimensional, context-dependent construct. Trust is necessary for online interactions where personal and financial information exchange goes through the virtual channel of service de-livery system characterized by high uncertainty (Hoffman et al., 1999). It deals with the belief that the trusted party will carry out its obligations (Gefen et al. 2003 a, 2003b). This definition is rooted in Giddens‟ (1994) definition which considers trust as a belief in someone‟s honesty and credibility (Giddens 1994).
In a virtual context, trust refers to the user‟s ability to control the actions of an e-service provider (Nah and Davis 2002). This construct was defined as trust in the privacy of the e-services and trust in the security aspects of e-services (Chen and Barnes 2007; Hernandez and Mazzon 2007; Nah and Davis 2002). The trust in privacy reflects the user‟s confidence in the service provider‟s ability to respect the user's privacy. Trust reveals the citi-zens confidence in the fact that his private information
will not be used by the service provider, or sold to others. The trust in the security aspects of the e-services (Chen and Barnes 2007; Hernandez and Mazzon 2007; Nah and Davis 2002) refers to user‟s confidence in the e-service provider‟s ability to protect and prevent the information from being hacked (Nah and Davis 2002). Table 7 re-sumes the control beliefs.
Control beliefs
Construct Authors Definition
Computer self effi-cacy (Compeau and Higgins 1995a)
Computer playfulness (CP)
Webster and Martocchio (1992); Moon and Kim (2001).
The degree of cognitive spontaneity in microcomputer interactions.
Personal innovativeness in IT (PIIT)
Agrawal and Prasad (1998); Agrawal and Karahanna (2000).
An individual trait reflecting a willingness to try out any new ICT;
End user support (Igbaria et al. 1996)
Facilitating conditions
MPCU‟s Thompson et al. (1991); Venkatesh et al. (2003); Taylor and Todd (1995b).
The control beliefs relating to resource factors such as time and money and ICT compatibility issues that may constrain usage.
End User Support Igbaria et al. (1996).
High levels of support that promotes more favorable beliefs about the system among users as well as MIS staffs.
Trust (Gefen et al. 2003 a, 2003b)
Trust in the security
Chen and Barnes (2007); Hernan-dez and Mazzon (2007); Nah and Davis (2002).
The user‟ confidence over the security aspects of the e-services.
The user‟s confidence in the e-service provider‟s ability to protect the information by preventing it from being hacked.
Trust in the privacy
Chen and Barnes (2007); Hernan-dez and Mazzon (2007); Nah and Davis (2002).
The user‟s confidence in the service pro-vider‟s ability to respect user's privacy. User‟s confidence that his private informa-tion will not be used or sold to others. Table 7. Control beliefs
1.2 Factors Influencing Public
E-services Acceptance
After reviewing large number of beliefs related to ICT acceptance, we will compare it to literature in the e-government research. Our aim is to detect the antecedents that are unique to the e-service context as compared to other voluntary ICT acceptance (e.g., PC acceptance, Internet acceptance).
1.2.1
Attitudinal beliefs and public
e-services
In adapting items from Van Slyke et al. (2004), Bélanger and Carter (2006) measured the impact of the UO (rela-tive advantage), SO (image), and CO (compatibility and ease of use) on the intention to use e-government servic-es. They found that higher level of UO (perceived relative advantage) increases citizens‟ intentions to accept the public e-services. Bretschneider et al. (2003) also demon-strated that the perceived benefit factor (UO) is a major predictor of government e-services. Gilbert et al (2004), Phang et al. (2005) reconfirmed it when they found that perceived usefulness (or UO) of websites was the most significant predictor of senior citizens‟ intention to accept e-government.
Gilbert et al. (2004) confirmed that control outcomes (CO), such as cost and time available, significantly influ-ence willingness to use e-services. Bélanger and Carter (2006) also found that higher levels of perceived image enhancing value of e-government (SO) and higher levels of perceived compatibility (CO) increase citizens‟ inten-tions to accept state e-government services. But contrary to relative advantage, compatibility, and image, they found that higher levels of perceived ease of use are not significantly associated with increased use intentions of e-government services (Bélanger and Carter 2006). By doing so, they confirmed Phang et al. (2005) and Gilbert et al. (2004) results. But we think that Bélanger and Cart-er (2006) had this result concCart-erning ease of use because they tested their model with college students that had an average of nine years of experience with computers. Therefore, we consider that the ease of use is still an im-portant predictor of the acceptance especially when it is the case of a population of normal citizens.
1.2.2
Normative beliefs and public
e-services
Researchers in the IS field have studied the social influ-ences impact on public e-services acceptance. For exam-ple Gefen et al. (2002) found that social influence has a
significant impact on intention to accept public e-services.
In Government to Citizen (G2C), the government plays an important role in facilitating the acceptance of public e-services by citizens (Hsieh et al. 2008). But until today, few studies have examined the governmental direct influ-ences on public e-services acceptance/rejection. Hsieh et al. (2008) have showed that governments may use syste-matic approaches to raise awareness and interest among citizens about public e-services. They can use different media channels, including communicating directly with citizens, to explain the benefits of using ICT and to offer training and technical support (e.g., Kvasny 2002; Van der Meer and Van Winden 2003). From the citizen‟s perspective, these institutional efforts to encourage and facilitate ICT use convey the message that the govern-ment is committed to their interests and has taken their needs and requirements into consideration (Kvasny and Keil 2002). In fact, prior research has revealed that gov-ernment agencies may serve as important referents whose expectation affects individual innovation acceptance (Lynne et al. 1995). Therefore, the government may in-fluence individual‟s acceptance of public e-services. In this research, the governmental influences are represented by the construct: perceived governmental influences (PGI).
1.2.3
Control beliefs and public e-services
Several researchers have studied the impact of control beliefs on the public e-services acceptance by citizens (Warkentin et al. 2002). Results found that between all the control beliefs, trust has the most significant predictor on the intention to accept public e-services (Gefen et al. 2002; Lee et al. 2005). Indeed, Bélanger and Carter (2005) demonstrated that trust has a significant influence on intention. Lee et al. (2005) also confirmed that trust-ing beliefs in government e-services have a significant effect on intention to use public e-services. But they also found that citizen‟s trust in their government have only a marginal effects on trusting beliefs in public e-services (Lee et al 2005). Indeed, other researches also show that only trust related to the public e-services can have an effect on the acceptance intention.Dubauskas‟ (2005) results illustrate that governments are not considering citizen privacy concerns. They also assert that citizen‟s expectations are not being taken into con-sideration by the government when implementing confi-dentiality policies. Therefore, by adapting trust in privacy (Chen and Barnes 2007; Hernandez and Mazzon 2007; Nah and Davis 2002) definition to the G2C context, we define trust as “the citizen‟s perception of the government ability to respect his privacy by preventing the usage of his personal information for other purposes after the transaction has taken place.”
Gefen et al (2002) found that trust was significantly in-fluenced by the security guarantees. Grundén (2009) as-serts that from a citizen perspective, disadvantages with
e-government were related to the increased vulnerability due to security problems that could occur.
Therefore, trust in the security is an important behavior belief in the G2C context. Therefore, we adapt trust in security (Chen and Barnes 2007; Gefen and al. 2002; Hernandez and Mazzon 2007; Nah and Davis 2002) defi-nition to the public e-services context as “the citizen‟s perception of the government ability to protect his per-sonal information from being hacked.”
Other researchers assert that many citizens see in the e-government a way to impose more control. Therefore, they fear from the obvious dangers of abuse of power (Davies 2005). In his much cited book “the Future of democracy” Bobbio (1987) asserts that the new question today is “who controls the controllers? He argues that today, governments can see every gesture and listen to every word or their subjects. According to Grundén (2009) and Griffin et al. (2007), citizen‟s also developed a kind of a fear from the government potential control. Therefore, we define fear from government control as “the worrying from the fact that the government can use the personnel data gathered through e-services in order to increase the control over citizens activities or salaries.” There is also the citizen‟s computer self efficacy which can influence the acceptance. Indeed, according to Lee et al. (2005) computer self efficacy is an important predictor of the public e-services acceptance.
1.3 The e-services acceptance bounded
in the Lebanese context
Unfortunately, there has been no scientific research link-ing Lebanese culture with ICT acceptance. There is only little research that compares Lebanon to other Arab coun-tries. Rose and Straub (1998), Straub, Lock, and Hill (2001), for example, compared ICT acceptance in four Arab countries: Jordan, Saudi Arabia, Lebanon, and Su-dan. They considered these four Arab countries as one unique culture. However, Lebanese culture cannot be considered as a pure Arab culture. Lebanon has a hetero-geneous society characterized by the existing of 18 reli-gious subgroups. Many civil wars in the 19th and 20th centuries have plagued the Lebanese citizens. The diffi-cult history of cohabitation between these different com-munities has created a highly risky and hostile environ-ment (Yahchouchi 2009). Therefore, Lebanese developed tools such the wasta (or connections) as methods that can assure trust in their daily transactions (Colli 2003). To-day, the public services are accessed either through local political leaders or through religious organization. This is a deeply rooted practice among all Lebanese communi-ties. Citizens‟ rights are re-packaged as favours (UNDP 2009).
Lebanese is a religious person who considers his life, at any moment as whatever the Lord wills it to become (Yahchouchi 2009). Religious social norms are deeply embedded in everyday life.
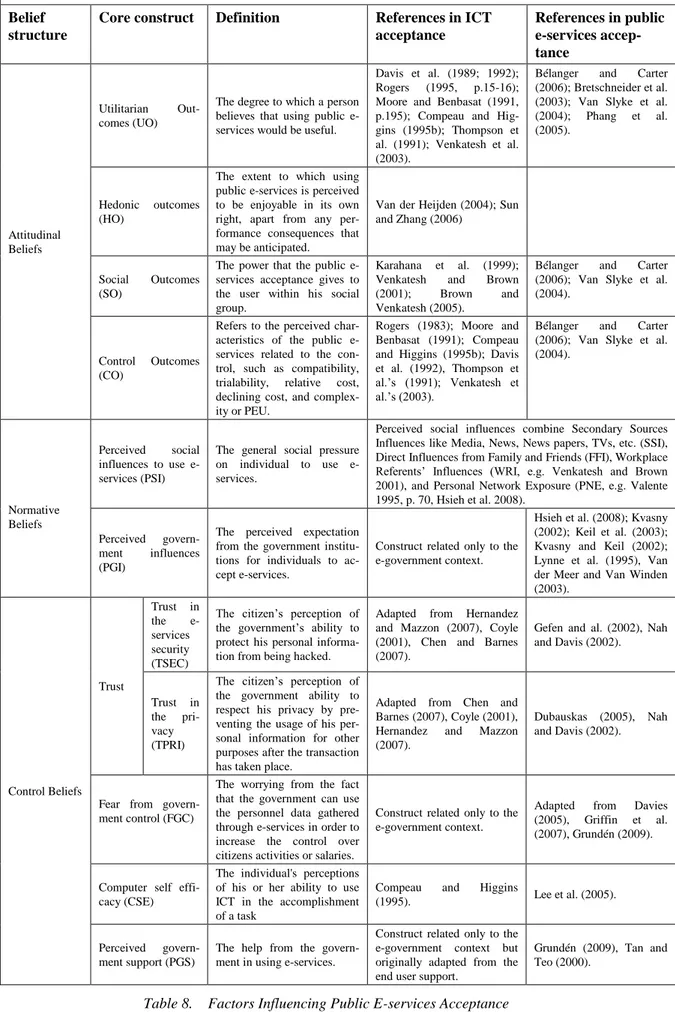
Factors Influencing Public E-services Acceptance Belief
structure
Core construct Definition References in ICT
acceptance References in public e-services accep-tance Attitudinal Beliefs Utilitarian Out-comes (UO)
The degree to which a person believes that using public e-services would be useful.
Davis et al. (1989; 1992); Rogers (1995, p.15-16); Moore and Benbasat (1991, p.195); Compeau and Hig-gins (1995b); Thompson et al. (1991); Venkatesh et al. (2003).
Bélanger and Carter (2006); Bretschneider et al. (2003); Van Slyke et al. (2004); Phang et al. (2005).
Hedonic outcomes (HO)
The extent to which using public e-services is perceived to be enjoyable in its own right, apart from any per-formance consequences that may be anticipated.
Van der Heijden (2004); Sun and Zhang (2006)
Social Outcomes (SO)
The power that the public e-services acceptance gives to the user within his social group.
Karahana et al. (1999); Venkatesh and Brown (2001); Brown and Venkatesh (2005).
Bélanger and Carter (2006); Van Slyke et al. (2004).
Control Outcomes (CO)
Refers to the perceived char-acteristics of the public e-services related to the con-trol, such as compatibility, trialability, relative cost, declining cost, and complex-ity or PEU.
Rogers (1983); Moore and Benbasat (1991); Compeau and Higgins (1995b); Davis et al. (1992), Thompson et al.‟s (1991); Venkatesh et al.‟s (2003).
Bélanger and Carter (2006); Van Slyke et al. (2004). Normative Beliefs Perceived social influences to use e-services (PSI)
The general social pressure on individual to use e-services.
Perceived social influences combine Secondary Sources Influences like Media, News, News papers, TVs, etc. (SSI), Direct Influences from Family and Friends (FFI), Workplace Referents‟ Influences (WRI, e.g. Venkatesh and Brown 2001), and Personal Network Exposure (PNE, e.g. Valente 1995, p. 70, Hsieh et al. 2008).
Perceived govern-ment influences (PGI)
The perceived expectation from the government institu-tions for individuals to ac-cept e-services.
Construct related only to the e-government context.
Hsieh et al. (2008); Kvasny (2002); Keil et al. (2003); Kvasny and Keil (2002); Lynne et al. (1995), Van der Meer and Van Winden (2003). Control Beliefs Trust Trust in the e-services security (TSEC)
The citizen‟s perception of the government‟s ability to protect his personal informa-tion from being hacked.
Adapted from Hernandez and Mazzon (2007), Coyle (2001), Chen and Barnes (2007).
Gefen and al. (2002), Nah and Davis (2002).
Trust in the pri-vacy (TPRI)
The citizen‟s perception of the government ability to respect his privacy by pre-venting the usage of his per-sonal information for other purposes after the transaction has taken place.
Adapted from Chen and Barnes (2007), Coyle (2001), Hernandez and Mazzon (2007).
Dubauskas (2005), Nah and Davis (2002).
Fear from govern-ment control (FGC)
The worrying from the fact that the government can use the personnel data gathered through e-services in order to increase the control over citizens activities or salaries.
Construct related only to the e-government context.
Adapted from Davies (2005), Griffin et al. (2007), Grundén (2009).
Computer self effi-cacy (CSE)
The individual's perceptions of his or her ability to use ICT in the accomplishment of a task
Compeau and Higgins
(1995). Lee et al. (2005).
Perceived govern-ment support (PGS)
The help from the govern-ment in using e-services.
Construct related only to the e-government context but originally adapted from the end user support.
Grundén (2009), Tan and Teo (2000).
These norms have an impact on the citizen‟s beliefs. Therefore, we will present the potential impact of the Lebanese culture on the attitudinal, normative, and con-trol beliefs.
1.3.1
Utilitarian, hedonic, social, and
con-trol outcomes in Lebanon
The Lebanese culture can impact the acceptance or rejec-tion of e-services. This influence goes through the rela-tive importance that a person gives to utilitarian, hedonic, social, and control outcomes in Lebanon.
For example, according to some researchers, Lebanese actions are guided more by his emotional feeling than by calculating reasoning (Weir 2002). This makes his beha-vior unpredictable and little rational. Therefore, the pub-lic e-services acceptance/rejection can results from the hedonic outcomes which reflect the impacts of the affect or feeling in the acceptance process;
In Lebanon, like in most of Arab World, human beha-viour is mostly directed towards the long-term of accu-mulation of prestige, standing, relationship, and respect (Al Omian and Weir 2005). The reason behind this long term objectives is that the status of the individual is de-termined primarily by his image, his family position, and his social contacts. Typical Lebanese statements are “My father knows the minister” or “do you know with whom you are talking?” The individual considers his personal contacts as distinguishing himself from the rest of the society. Therefore, Lebanese, like the other Arab seek membership in those groups that offer them potential for elevating their social standing (Ali 1990; 1995). Because of this, Lebanese social image is considered as very im-portant. Some researchers proved that the Lebanese is ready to adopt a certain behaviors just in order to impress his social group (Neal et al. 2005). Therefore, social out-comes can have an important role in the individual beha-viour. Acceptance or rejection of public e-services can be the result of a
According to Ali (1995), in the Arab culture, the cost may sometimes be the last and least important aspect of the behavior process. There is always the question of the appropriate behaviour that comes first. So in high context culture, if the behaviour is seen as an inappropriate beha-viour or incompatible with the individual cultural values, the behavior is likely to be rejected (Ali 1995).
1.3.2
The role of normative beliefs in
Leb-anon
In Lebanon, relationships are perceived as an important factor in human behaviour. There are also, the relatives, the friends, and the formal and informal groups who have a decisive influence on the individual behaviour in Leba-non (Yahchouchi 2009).
2.3.2.1. Family Influences
In Lebanon, family has a significant influence on the individual behaviour (Fahed-Sreih and Djoundourian 2006). Indeed, Lebanese spend most of his time within his family. It is even common to find several generations of the same family living next door to each other. As the family is considered as an economic unit, family norms and rules play a significant role in the individual behaviour. The family structure is patriarchal. The most influential person is the father. His role is to protect and to provide resources for the entire family. All the family members have to respect the father‟s wishes. Family tra-ditions sanction consultation in the conduct of all aspect of life.
The centrality of the father figure stems from the role of the family as an economic unit, in which the father is the property owner and producer on whom the rest of the family depend.
2.3.2.2. Social influences: Informal Groups, formal groups, and peers
In Lebanon, the individual is influenced mainly by one‟s informal and formal groups. The Lebanese is also influ-enced by his peers, by personal network exposure, and by his workplace referents (Fahed-Sreih and Djoundourian 2006. In the ICT acceptance, Loch et al. (2003) found that social norm was an important factor in explaining the Internet adoption by Arabs. They affirmed that Arab in-dividuals are influenced by whether others are also using Internet.
1.3.3
The role of control beliefs in the
Le-banese context
Between the control beliefs, trust is one of the most in-fluential beliefs in the Lebanese context. Studies show that the Lebanese consumers do not trust the online envi-ronment. This fact is demonstrated by their fear of giving away their personal and financial information because of privacy concern (Jarvenpaa et al. 1999). But studies also show that Lebanese do not trust their government. In-deed, the last UNDP 2009 report shows that more then 62.7 percent of the total population does not trust the Council of Ministers. Only 11.7 percent of the Chiite, 26.5 percent of Orthodox, 30.5 percent of Catholic, 34.5 percent of Maronite, 50.3 percent of Druze, and 64 per-cent of Sunni trusts the Lebanese Council of Ministers (UNDP 2009). Only 52 percent of the Lebanese trust their parliament (UNDP 2009). But according to Lee et al (2005), citizen‟s trust in their government have only a marginal effects on trusting beliefs in public e-services.
2.
Research methods and results
2.1 Discussions of the First Phase
me-thodology and instrument
devel-opment
In the first part of this research we extracted a large num-ber of beliefs from previous research in ICT acceptance and public e-services acceptance. But none of these re-search projects specify which beliefs are operative for the public e-services context in Lebanon. According to TRA, from this large number of beliefs, only a relative small number serves as determinant of the citizen‟s behavioural attitude in a specific context. Depending on the context, researchers need to elicit the salient beliefs from the po-tential adopters (Ajzen 1991; Ajzen and Fishbein 1980; Fishbein and Ajzen 1975).
Taylor and Todd (1995a) did not use this method. They developed the decomposed belief structure for technology acceptance by drawing from previous research in tech-nology acceptance. Their approach was justified on the basis that there is a wealth of existing research on tech-nology acceptance, thus minimizing the need to elicit beliefs afresh for each new technology acceptance setting. We think that the Taylor and Todd (1995a) method does not take into consideration the specificity of the context in which the acceptance process is embedded. Therefore, we prefer Ajzen‟s (1991), Ajzen‟s and Fishbein‟s (1980), and Fishbein‟s and Ajzen‟s (1975) method that better detect the salient beliefs. From Taylor and Todd (1995a), we choose the way they selected their items, measures, or questions related to each belief.
Consequently, we will combine these two methods by proposing a third way: the decomposed salient belief structure for public e-services acceptance. The decom-posed salient belief structure can reflect more the salient beliefs in the e-government context in Lebanon and can help the researcher in finding good measures that have already been tested and retested for internal consistency and reliability. Therefore, based on Fishbein‟s paradigm (Fishbein 1968) and in order to obtain a correct specifica-tion of the causal determinants of the public e-services acceptance intention, we used, in Phase 1, a qualitative method: interviews with open- ended questions. Ques-tions were asked about government e-services acceptance intention or about reasons for non-acceptance intention. Therefore, after explaining the government online servic-es to the intervieweservic-es, the rservic-espondents were asked if they would agree or accept to use government e-services and about influencing factors in their e-services intention acceptance or non-acceptance decision. Regardless of their answer, they were further questioned as to the rea-sons for their choice. Therefore, respondents who ac-cepted government e-services were asked to identify the factors that led to the acceptance of e-services. Similarly, respondents who refused to use e-services were asked to
identify the factors that led to this non-acceptance deci-sion.
Then, open-ended responses were double coded based on a start list of beliefs that included their definitions from prior research (Miles and Huberman 1984, p. 58). The salient beliefs were specified by the respondents. The intercoder reliability was 81 percent, which is well above the minimum of 70 percent identified by Miles and Hu-berman (1984). Through the qualitative data anchored in the trichotomous classification of TPB and MATH, our first study identified the attitudinal, normative, and con-trol salient beliefs related to the public e-services accep-tance in the Lebanese context. These beliefs are salient only in the government to citizen (G2C) context in the Lebanese environment.
Therefore, the decomposed salient belief structure for public e-services acceptance in Lebanon that we devel-oped at the end of the phase one served as reference in the development of the research model and questionnaire. Items or measures were selected from prior research.
2.2 Salient beliefs that influence the
acceptance or rejection of public
e-services in Lebanon
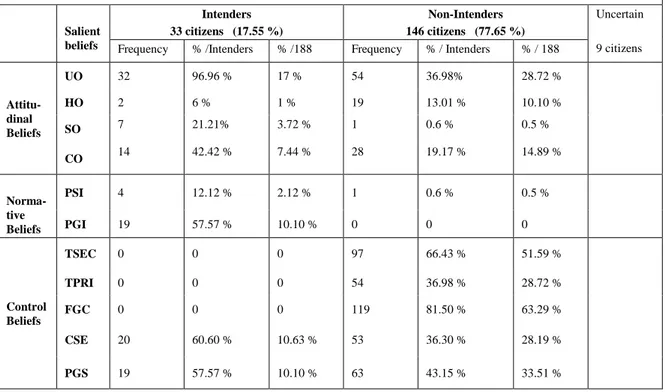
To understand the Lebanese citizen‟s intention decision regarding acceptance or rejection of public e-services, the qualitative data were divided into three categories based on the citizens intentions expressed in the first stage: (1) citizens who intended to accept e-services (intenders), (2) citizens who intended not to accept (non-intenders), and (3) those who were uncertain about their choice.
2.2.1
Salient Beliefs Affecting the
Accep-tance Intention
As presented in Table 9, results show that among 188 citizens, only 33 (17.55 percent) intended to accept gov-ernment e-services. For these 33 intenders, attitudinal beliefs such as utilitarian outcomes (UO, frequency = 96.96 percent of the intenders or 17 percent of the res-pondents), social outcomes (SO, frequency = 21.21 per-cent of the intenders or 3.72 perper-cent of the respondents), and control outcomes represented by the perceived ease of use (CO, frequency = 42.42 percent of the intenders or 7.44 percent of the respondents), normative beliefs such as perceived government influences (PGI, frequency = 57.57 percent of the intenders or 10.10 percent of the respondents), and control beliefs such as perceived gov-ernment support (PGS, frequency = 57.57 percent of the intenders or 10.10 percent of the respondents) and com-puter self-efficacy (CSE, frequency = 60.60 percent of the intenders or 10.63 percent of the respondents) were the most cited key drivers of the e-services acceptance intention (AI).
The behavioral beliefs related to the hedonic outcomes (HO, frequency = 6.06 percent or 1 percent of the
res-pondents), the normative beliefs such as the social influ-ences (SI, frequency = 12.12 percent or 2.12 percent from the respondents) were also cited but by a few number of citizens.
As expected, utilitarian outcomes (UO) were the most salient behavioral beliefs, followed by computer self effi-cacy (CSE), perceived government influences (PGI) and support (PGS).
2.2.2
Salient Beliefs Affecting the
Non-Acceptance Intention
For the citizens who intended to not-accept or reject the government e-services, barriers like fear of the govern-ment control (FGC), lack of trust in the public e-services security (TSEC), lack of trust related to privacy (TPRI), lack of support (PGS), and lack of knowledge (CSE) were most significant. Perceived usefulless (PU) of the
e-service is also an important factor (frequency=54) that impacts the non-intenders‟ decision (frequently men-tioned as perceived privacy and computer self-efficacy). But the fear of government control was the most impor-tant determinant, both in terms of frequency and in terms of importance.
Results also indicated that some factors (fear of govern-ment control, Lack of trust in the privacy, and lack per-ceived security) may act to uniquely impede acceptance of government e-services. According to Cenfetelli (2004), these acceptance inhibitors are beliefs held by a citizen that act solely to impede acceptance intention when present (and perceived) but which have no effect when absent (or not perceived). These acceptance inhibitors are distinguished from acceptance enablers, as being a per-ception for which there is no clear, positively valanced antipole that is psychologically meaningful.
Salient beliefs related to government e-services acceptance/rejection in Lebanon and their indicators
Salient beliefs Intenders 33 citizens (17.55 %) Non-Intenders 146 citizens (77.65 %) Uncertain 9 citizens Frequency % /Intenders % /188 Frequency % / Intenders % / 188
Attitu-dinal Beliefs UO 32 96.96 % 17 % 54 36.98% 28.72 % HO 2 6 % 1 % 19 13.01 % 10.10 % SO 7 21.21% 3.72 % 1 0.6 % 0.5 % CO 14 42.42 % 7.44 % 28 19.17 % 14.89 % Norma-tive Beliefs PSI 4 12.12 % 2.12 % 1 0.6 % 0.5 % PGI 19 57.57 % 10.10 % 0 0 0 Control Beliefs TSEC 0 0 0 97 66.43 % 51.59 % TPRI 0 0 0 54 36.98 % 28.72 % FGC 0 0 0 119 81.50 % 63.29 % CSE 20 60.60 % 10.63 % 53 36.30 % 28.19 % PGS 19 57.57 % 10.10 % 63 43.15 % 33.51 %
Table 9. Salient beliefs related to government e-services acceptance/rejection in Lebanon and their indica-tors
2.3 The e-government services
accep-tance intention model (ITA e-Gov
Model)
Based on the above literature review and discussions, and based on the phase one results, we developed the research model that reflects the various elements involved in the mental processes of Lebanese citizens‟ accep-tance/rejection of public e-services. We developed the ITA e-Gov Model based on MATH (Venkatesh and Brown 2001, Brown and Venkatesh 2005). According to
MATH, ICT acceptance intention (IA) is a weighted function of behavioral attitudinal beliefs (utilitarian, he-donic, social, and control outcomes), normative beliefs, and the control beliefs structure.
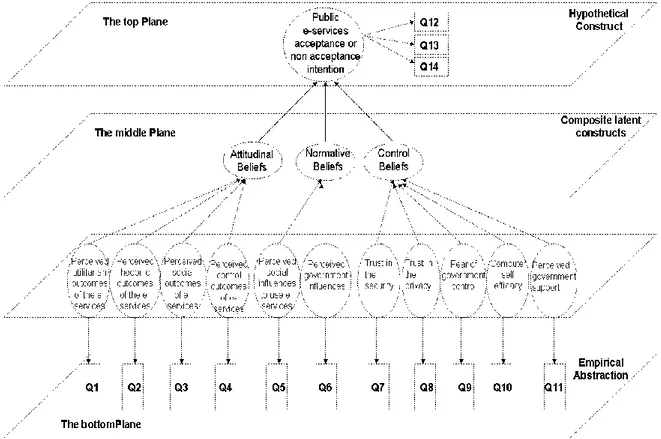
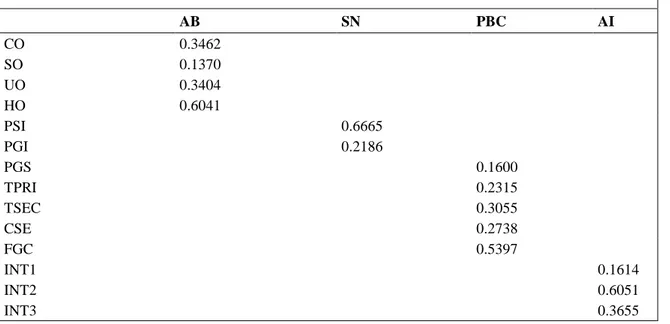
In the ITA e-Gov Model, the government e-services ac-ceptance divide (ACD) is a weighted function of three multidimensional formative constructs (or index): (1) attitudinal beliefs toward accepting public e-services, (2) normative beliefs, and (3) control beliefs.
Figure 1 The research model
As shown in Figure 1, there are several planes represented in our model. The top plane represents the conceptual plan. The middle planes represent first and second-order empirical abstractions. The bottom plane represents the observational plane.
The multidimensional constructs that constitute the mid-dle plane (attitudinal beliefs, normative beliefs, and con-trol beliefs) are usually operationalized by means of ref-lective indicators. These constructs can be better captured if approach from a formative perspective. Indeed, inspec-tion of the items constituting these indexes reveals that the causal priority runs from the indicators to the con-struct. Attitudinal beliefs are formed as a combination of utilitarian (UO), hedonic (HO), social (SO), and control outcomes (CO) of public e-services acceptance. Norma-tive beliefs are formed as perceived government influ-ences (PGI) and subjective norms (SN). Control beliefs are composed from perceived government support/lack of support (PGS), computer self efficacy/non efficacy (CSE), and inhibitors such as: lack of trust in the security (LTSEC), lack of trust in the privacy (LTPRI), and fear of government control (FGC).
2.4 Discussions of the Second Phase
methodology and instrument
de-velopment
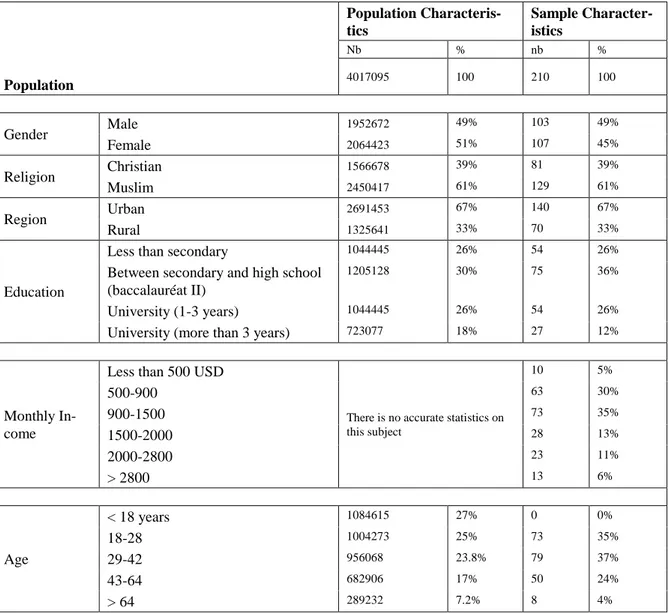
The ITA e-Gov Model was designed to capture the inhi-bitors and enablers behavioral beliefs of public e-services. In order to test the model, data was collected in the Phase 2 from a sample of 210 randomly chosen po-tential Lebanese public e-service users. The sample cha-racteristics are presented in the Table 10.
To achieve a representative sample of the Lebanese popu-lation above 18 years of age, a fixed percentage of man/women, young adults/adults/young-seniors/seniors were required. Interviewees were randomly approached by personal interviews according to their region. This approach by interviews was motivated by the wish to be representative and to fully include the so-called “have-nots” and “knows-nots”. We wanted to know their reasons for non-acceptance and their intension for future use of public e-services. A triple language instrument was used. Respondents were randomly selected in the streets from all the Lebanese regions.
The aim of this questionnaire was to measure the weight or the importance that citizens give to each belief. There-fore, we asked respondents to rate each factor on how important it was in his acceptance or non-acceptance decision, using a scale ranging from 1 (Not Important) to 7 (Very Important).
Population Population Characteris-tics Sample Character-istics Nb % nb % 4017095 100 210 100 Gender Male 1952672 49% 103 49% Female 2064423 51% 107 45% Religion Christian 1566678 39% 81 39% Muslim 2450417 61% 129 61% Region Urban 2691453 67% 140 67% Rural 1325641 33% 70 33% Education
Less than secondary 1044445 26% 54 26%
Between secondary and high school (baccalauréat II)
1205128 30% 75 36%
University (1-3 years) 1044445 26% 54 26%
University (more than 3 years) 723077 18% 27 12%
Monthly In-come
Less than 500 USD
There is no accurate statistics on this subject 10 5% 500-900 63 30% 900-1500 73 35% 1500-2000 28 13% 2000-2800 23 11% > 2800 13 6% Age < 18 years 1084615 27% 0 0% 18-28 1004273 25% 73 35% 29-42 956068 23.8% 79 37% 43-64 682906 17% 50 24% > 64 289232 7.2% 8 4%
Table 10. Population and sample characteristics
2.4.1
The dependent variable
The main dependent variables to be explained were the actual acceptance/rejection, intended accep-tance/rejection, and potential acceptance/rejection of the main public e-services of the Lebanese national adminis-tration in 2008. Therefore, a part of this questionnaire was about the actual, the intended, or the potential accep-tance/rejection of a long list of public e-services proposed by the Lebanese national administration, such as national government information services at www.e-gateway.gov.lb, or downloadable forms at www.informs.gov.lb, websites of ministries presented in Appendix A, tax transaction services or e-taxes, health care e-services, social services and benefits, application for a building permit, appointment to apply for a pass-port, request for a certificate of birth, national identifica-tion card, or citizenship, notificaidentifica-tion of a situaidentifica-tion change (marriage, address change, etc). In these questions we did not distinguish one service from another. E-services were
presented in bulk or as a set of services proposed by the government.
The interviewees were asked if they intended to use pub-lic e-service when this is possible and when they need it. Based on Van Dijk et al. (2008), we added the expression “possible” because all public services are not yet availa-ble in electronic version. We added also the expression “when you need it” because many services/e-services are only needed incidentally (such as a passport renewal). The first three items that measures the intention accep-tance divide: “I‟m very likely to (…) to use public e-services when this is possible and when I need it”; “I intend to (…) to use public e-services in future when this is possible and when I need it”; “I will probably (…) to use public e-services” on a scale going from extremely reject to extremely accept (-3, -2, -1, 0, 1, 2, 3).
2.4.2
The independent variables
In each of three multidimensional independent con-structs, we need to consider all facets of the construct.