Practices in the Squale Quality Model (Squale Deliverable 1.3)
Texte intégral
Figure
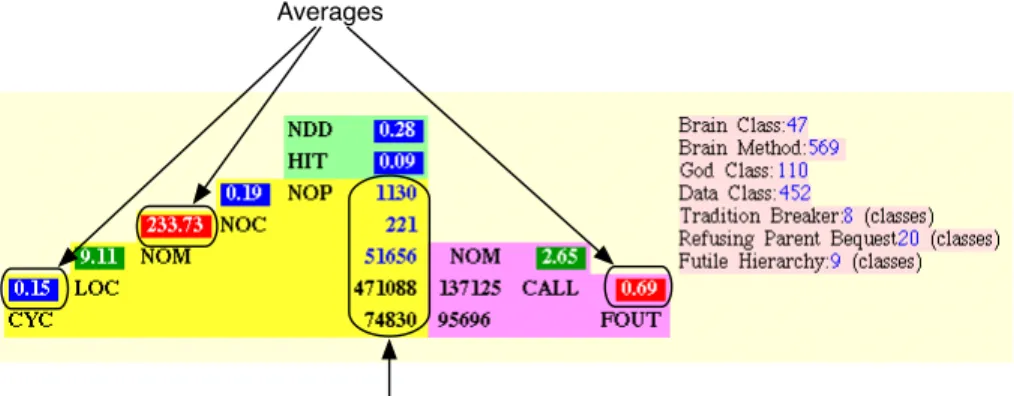


Documents relatifs
SecBPMN [5] (Secure BPMN) is a modeling language, based on Business Process Modelling and Notation (BPMN), which allows analysts to (i) model business pro- cesses with
We plan to apply the presented method, together with a light-weight ISO 31000 conform risk analysis, in future real-world security assessments. The idea is to develop a questionnaire
The proposed approach provides a flexi- ble event calculus based composition design, that allows for modeling different temporal (response time, time-units and other) and
Hennie Kruger North-West University, South Africa Wai Sze Leung University of Johannesburg, South Africa Dan Likarish Regis University, Colorado, USA Javier Lopez University of
Security Models Lecture 1 Security Notions Different Adversaries..
3 Conclusion: Under this assumption there does not exist an adversary in polynomial time which can break the security of the scheme.. Application: ElGamal is IND-CPA secure under
This article presents a technique to specify UML security stereotypes, aiming to guide developers by annotating vulnerable model parts and to allow the automatic security test
With the current SQL model, each organization must grant a warehouse administrator Read (and Grant-Read) permissions on their exported data – only then can someone define and
