Deliverable D2.1 Closed loop fuzzing algorithms
Texte intégral
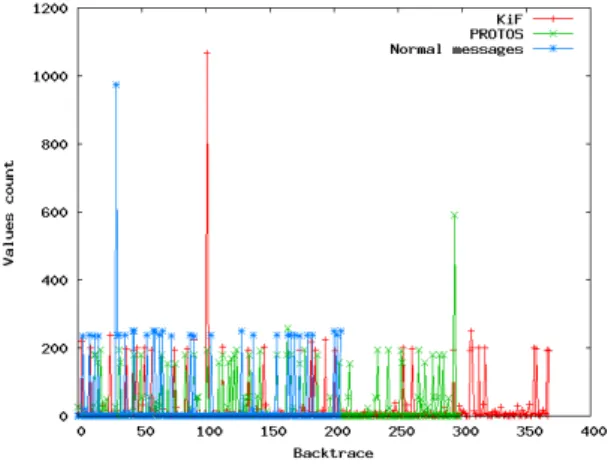
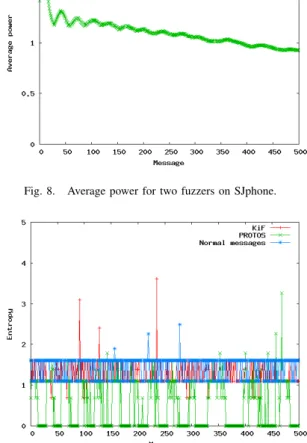
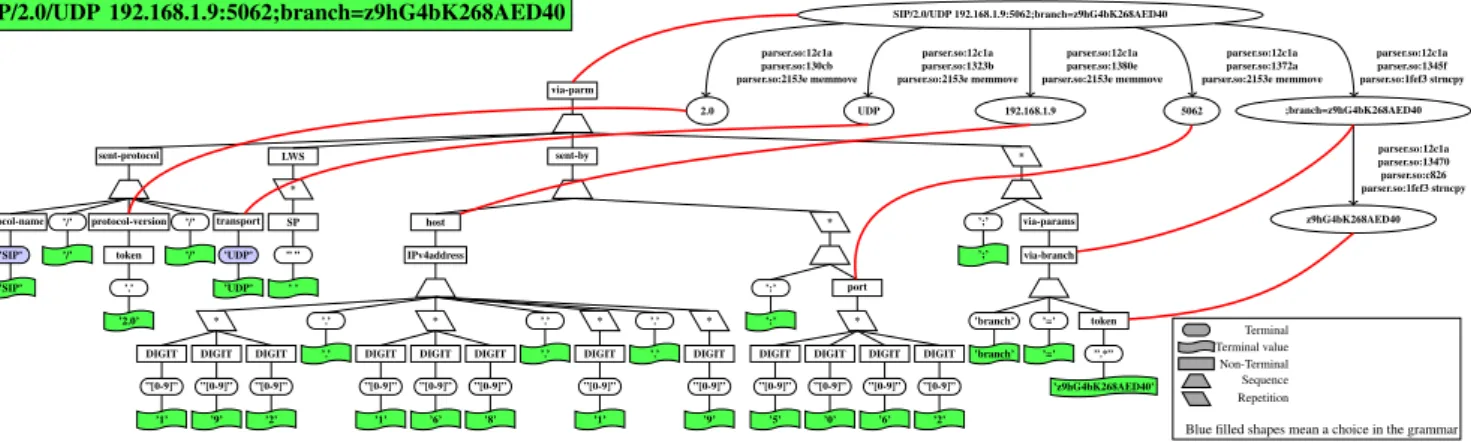
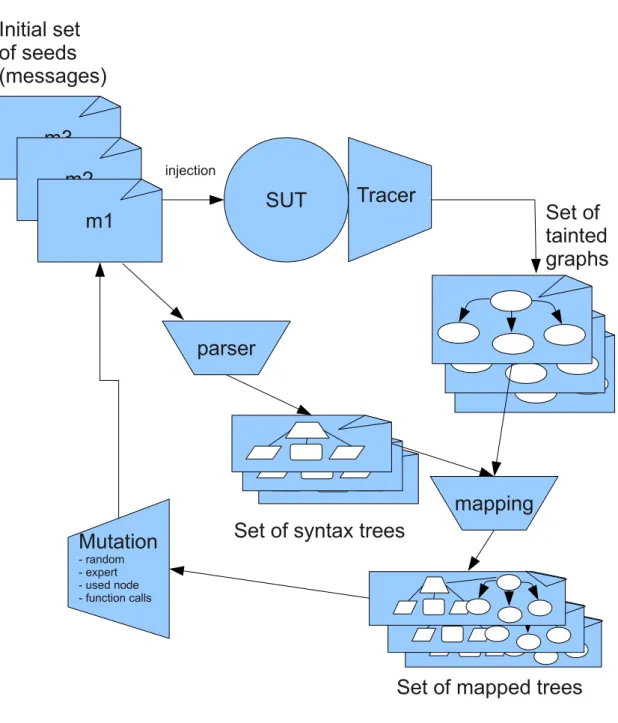
Figure
Documents relatifs
Central questions in the geometry of finite dimen- sional Banach spaces are those of finding the right notion of Minkowski area and, more generally, of invariant area (see Section 2
This new technology was announced by Open Mobile Alliance (OMA) which describes the Smart Card Web Server (SCWS) specification based on the version 1.1 of the HTTP protocol for
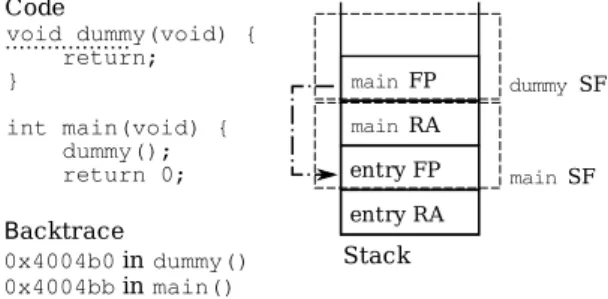
• Using addr2line , address from ndk-stack and binary with symbols , we resolve the crash to a line and method in the sourcode.. HOW TO : DROID-FF :
Starting from the current knowledge based on intestinal metagenomics, we point out on the role of food in shaping gut microbiota composition and functions, which is therefore
Although we have not explored all the cases (the transmission and coupling of a P and general S wave across a lam- ination with non-normal incidence), we are confident that for
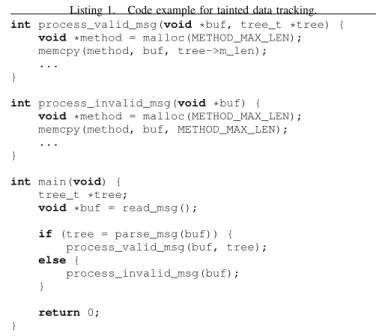
In summary, this thesis aims to develop effective directed fuzzing techniques to detect complex typestate vulnerabilities, like UAF, in binary code of real-world programs in
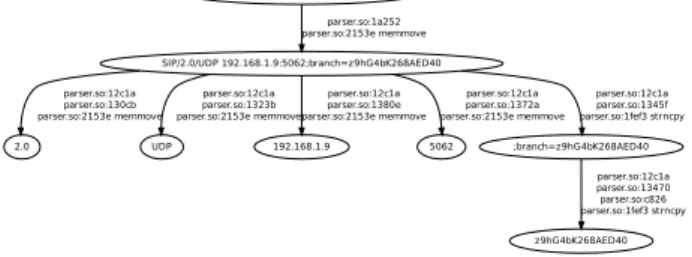
Test Case 7 Within this test case, we try to identify vulnerabilities depending on the value of the length field and the actual value of the payload.. In a first run, we
Fig. The Work Flow Chart in H-Fuzzing Method. H-Fuzzing is composed of two processes: static analysis process and fuzzing process. 1 illustrates the working flow of H-Fuzzing.