Morphological Detection of Malware
Texte intégral
Figure

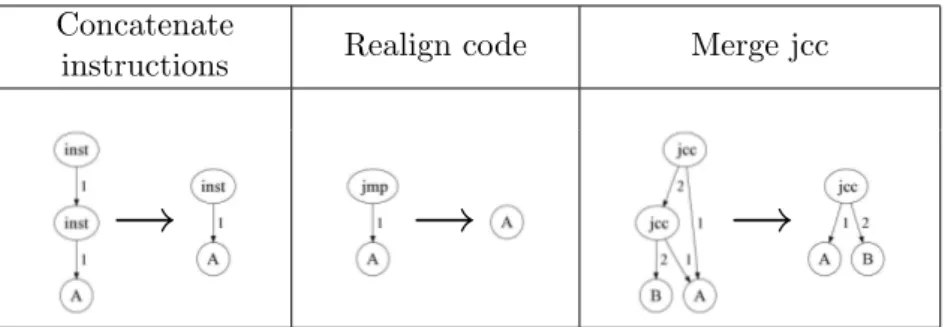
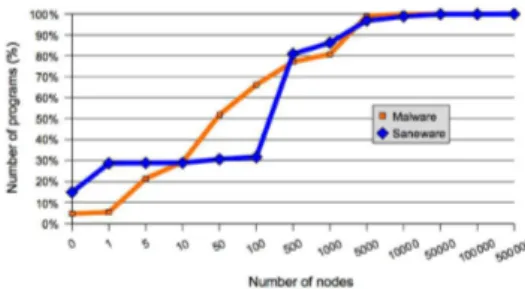

Documents relatifs
This note provides a detailed computation of the Ext-algebra for a very specific finite dimensional algebra, namely a Brauer tree algebra associated to a line, with no
Wood density at 12% moisture is the ratio between the mass New formula and conversion factor to compute basic wood density of tree species using a global wood
La dynamique de la végétation des trouées dépend étroitement de la superficie de-; ouvertures et de l'état de dégradation de la végetation environnante La
L’archive ouverte pluridisciplinaire HAL, est destinée au dépôt et à la diffusion de documents scientifiques de niveau recherche, publiés ou non, émanant des
of three steps: sort the image elements (pixels); then run the modified union- find algorithm to compute a tree encoded by a parent function; last modify the parent function to
At this scale, long range molecular forces stratify liquids [19] and the ratio between tube diameter and sap film thickness allows us to consider tube walls as plane surfaces
For the comparison of the results with the simple SOM technique and the IENN method, the results of the publica- tion of Chac´on et.al. With the IENN method 9 clusters with
More- over, as discrete trees can be associated with Lukasiewicz paths by the the Lukasiewicz correspondence, stable trees can be associated likewise with stable, spectrally