Legally Fair Contract Signing Without Keystones
Texte intégral
Figure
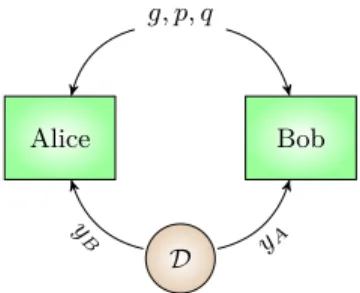


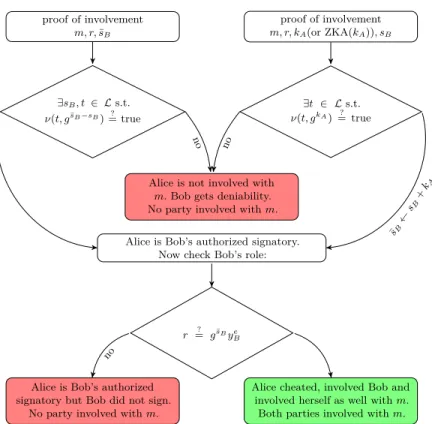
Documents relatifs
to allow signature holders to monitor the verification of a given signature in the sense that any plain signature can be publicly turned into a signature which is only verifiable
In particular, the anonymity property holds unconditionally: even if a client has unlimited computational resources (which means for example that he can obtain the secret keys of
The assumptions of the scheme, the security goals it was tested against, their formalisation, the protocol specification tool set and the model checking technology used here are
Keywords: Designated verifier signatures, Privacy of signer’s identity, Bilinear Diffie-Hellman problems, Exact security, Tight reduction..
This paper presents an efficient verifier-local revocation group signature (VLR-GS) providing backward unlink- ability (i.e. previously issued signatures remain anonymous even after
This is however not the case in the scheme proposed in [HT07]: the final signature is a proof of knowledge of some values computed by the issuer made non-interactive by the
So far, the only apparent way to build a HH-AOS system in the standard model —let alone with constant-size public keys— is to take advantage of aggregate signatures [34, 35] in order
Finally, to demonstrate the feasibility of this attack on the primary dedi- cated signature scheme proposed by Klonowski et al., we also propose the first efficient
