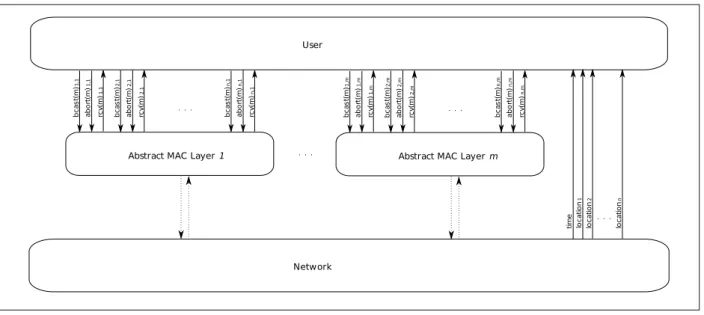
The Abstract MAC Layer
Texte intégral
Figure

Documents relatifs
The chosen value for the link register must be 12 bytes greater than the value of the stack pointer, so that the target program will return to and execute the bytes from the attack
a new medium access control protocol based on slotted ALOHA and called channel aware slotted ALOHA.. In the considered topology, there is a central station, e.g., a receiver node
In this article, we show that the 802.11 MAC protocol is very sensitive to the cell topology leading to spatially unfair situations in terms of channel access (expressed by the
incompatibilities between the various versions of X.500, and as the namespace is consistent, the information in the Directory can be accessed by any implementation. Also, work
As the IP version 9 protocol comes to the end of its useful life, once again due to address space exhaustion, we look back at some of the success of the
So, while the authentication mechanism specified in RIP-2 is less than ideal, it does prevent anyone who cannot directly access the network (i.e., someone who cannot sniff
As additional CipherSuites are defined for TLS which include new key exchange algorithms, the server key exchange message will be sent if and only if the certificate
2 hepatocellular carcinoma; miR-4510, mature microRNA 4510; mRNA, messenger RNA; RAF1, RAF 3 proto-oncogene serine/threonine-protein kinase; SD, standard deviation; siRAF1,