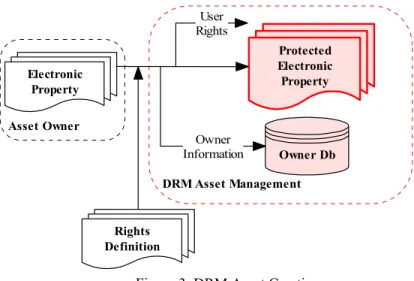
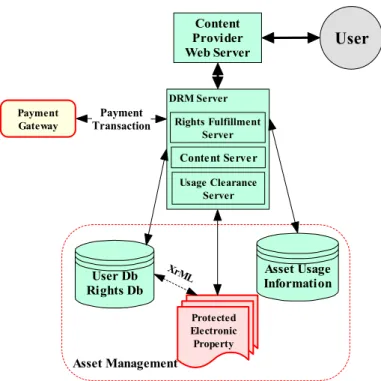
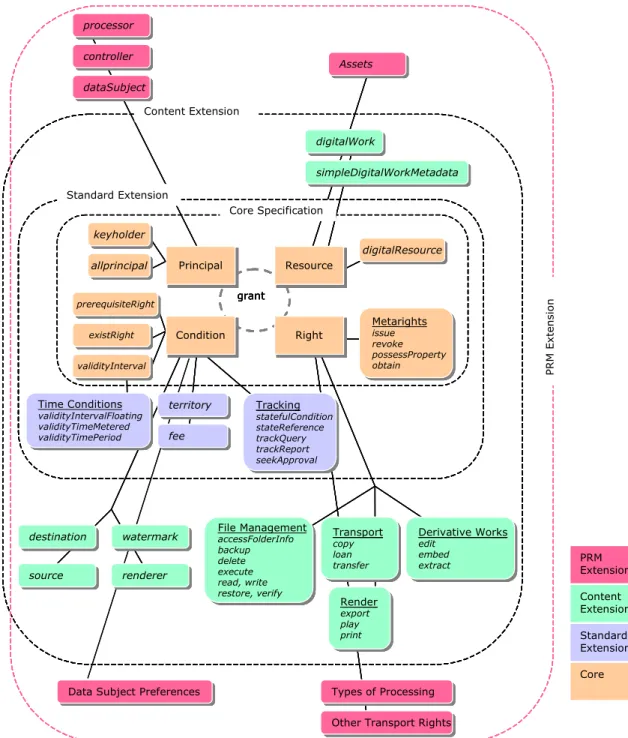
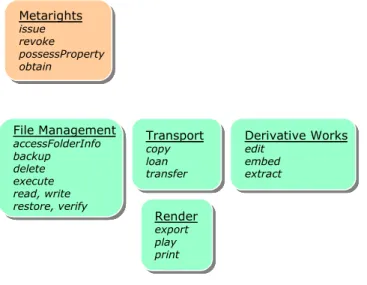
Applying Digital Rights Management Systems to Privacy Rights Management
Texte intégral
Figure


Documents relatifs
Moreover, Cloud Computing based implementation provide a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (e.g.,
Cet article se propose d’inventorier toute la Correspondance, ce fameux « laboratoire » de Flaubert, pour mettre en évidence l’influence que l’ermite de Croisset a eu
In this paper we combine formal tools taken from the Belief Revision and the Non- monotonic Reasoning communities in order to define belief change operators that are appropriate
Template-based activity recognition was compared to statistical learning classifiers such as naive bayes (NB), decision tree (DT), logistic regression (LR) and artificial
defining the complete access control model M Constraints/ Context M’ Constraints/ Context Certificate C defines model M’ which is part of the complete model M M’’ M’’ is part
We therefore recommend that, firstly, the 19 questions we have designed to ensure adherence to Clegg’s 19 Sociotechnical Principles (2000) are used to help
A careful examination of the exemptions from a physical-based approach shows that, beyond the apparent diversity, many of them are similar when considered as material
Our research answers this inquiry by exposing the ways in which contrasting discourses respond to the issue of access inequalities in the artistic labour market, while suggesting