Authentication and consensus overhead in vehicular ad hoc networks
Texte intégral
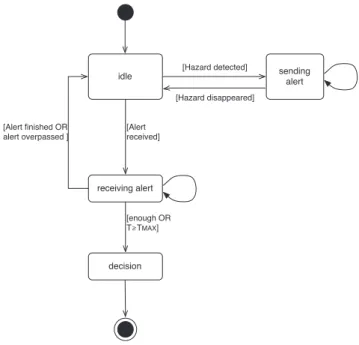
Figure

![Fig. 2 WAVE safety message format [30]](https://thumb-eu.123doks.com/thumbv2/123doknet/3523320.103082/7.892.460.817.116.421/fig-wave-safety-message-format.webp)

Documents relatifs
Differential Harnack estimates for backward heat equations with potentials under an extended Ricci flow, Adv.. The (logarithmic) Sobolev inequalities alonf geometric flow
We first prove that, surprisingly, even when all nodes transmit at the same power, finding a simple unicast path that guarantees enough remaining energy locally at each node in
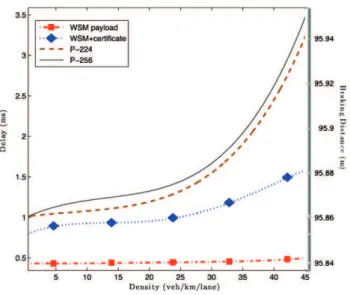
For higher values, using the localization algorithm leads to an increase in the end-to-end delay and to significant packet loss due to an excessive delay (5 % of packets with a
Galbraith, Lin, and Scott [9] and the author [26] have already con- structed families of endomorphisms equipped with a convenient ready-made basis; in this work, we generalize
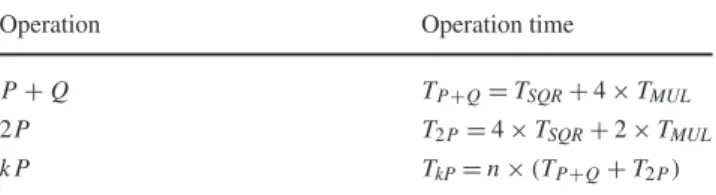
In Section 5 we analyze the complexity of the blockwise product for two polynomials supported by monomials of degree at most d − 1: if A contains Q in its center, then we show
Matériaux constitutifs des écrans cathodiques Les écrans à tube cathodique sont composés de matériaux divers et variés, principalement du métal et des polymères synthétiques pour
Le premier parle sur la théorie de décision et le choix de la loi a priori et a posteriori motivé par des applications de calcul de la puissance bayésienne et la taille
trade secrets and intellectual property rights are but a partial defence against disclosure and may be relied on only to the extent strictly necessary to protect