Memory Efficient Self-Stabilizing k-Independent Dominating Set Construction
Texte intégral
Figure
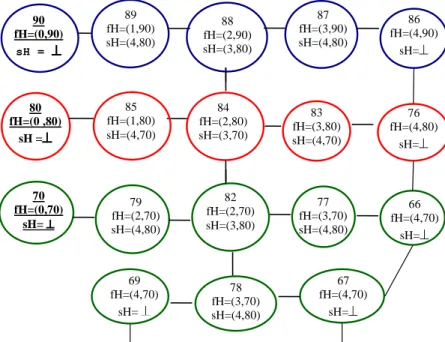
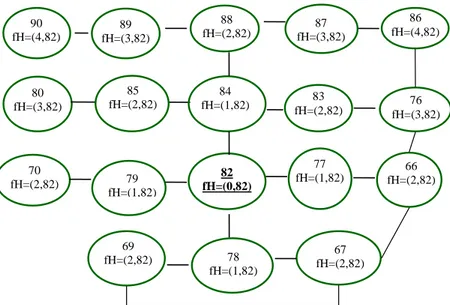
Documents relatifs
But since men cannot accept proposal (Women are not all in phase 1 or 1.5, otherwise the configuration is already C’), the blocking pair is still there and she is not eligible again
As the data are uncertain and imprecise, instead of collecting on each node the data of its neighbors, the purpose of our algorithm is to evaluate a neighborhood confidence using
In conclusion, the composition of these four layers provides us a self-stabilizing algorithm for centers computation or minimum diameter spanning tree construc- tion under
In this paper, we aim to automatically verify self-stabilizing popula- tion protocols for leader election and token circulation in the Spin model checker [8].. We report our
N We successfully model check the self-stabilizing leader election in complete graphs under such a weaker fair- ness condition and the self-stabilizing token circulation in
We complement the study with probabilistic protocols for the uniform case: the first probabilistic protocol requires infinite memory but copes with asynchronous scheduling
Indeed, recently, several self-stabilizing algorithms which work under a distributed unfair daemon have been shown to have an exponential stabilization time in moves in the worst
NBUIFNBUJDBM PCKFDU DBMMFE B HSBQI JU JT DPODFSOFE JO EFTJHOJOH GBTU BMHPSJUINT UP QBSUJUJPO JU UIF HSBQI JOUP UIF NBYJNVN OVNCFS PG DPOOFDUFE DPVQMFT ćJT JT LOPXO JO HSBQI UIFPSZ BT