Cryptographic error correction
Texte intégral
Figure
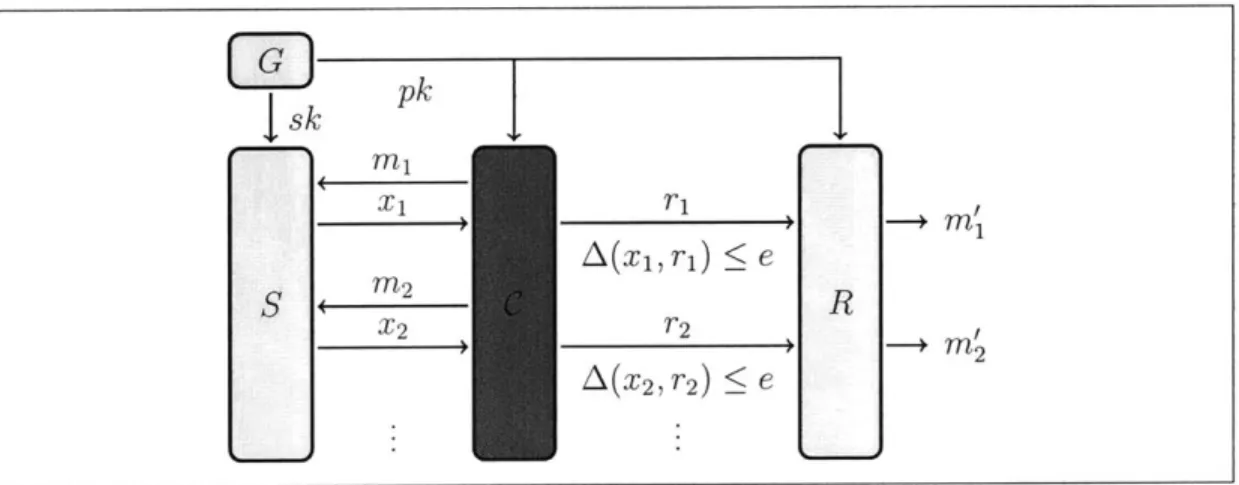
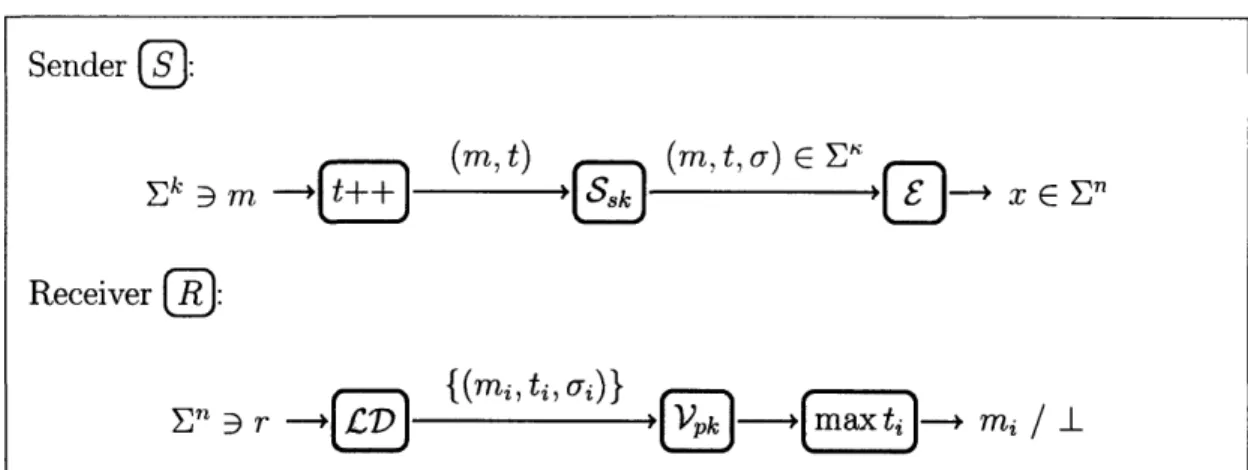

Documents relatifs
A digital signature scheme is said to be vulnerable to destructive ex- clusive ownership property (DEO) If it is computationaly feasible for an intruder, given a public verification
Le droit de la preuve face à l'informatique et à la télématique Amory, Bernard Published in: Le notariat et l'informatique Publication date: 1985 Document Version le PDF de
Keywords: Software visualisation tool, context- oriented programming language, dynamic adaptation, feature and context models, user study.. Copyright c 2019 for this paper by
In §2 we observe that current ransomware gets random numbers from a small set of functions, called Cryptographically Secure Pseudo Random Number Gener- ator (CSPRNG), that
Signers may not be initialized by public keys and may sign data in UTF-8 Strings, byte arrays, or ByteBuffers.. Signers must be initialized with a keyset containing a primary status
We represent protocols as processes in the spi calculus and state their security properties in terms of coarse-grained notions of protocol equivalence.... 2.3 Examples using
Sort and random functions. 440 Compute the quantization of the Euclidean metric. 502 Plot performance bounds for a convolutional code. 504 Executable: Find dfiee for