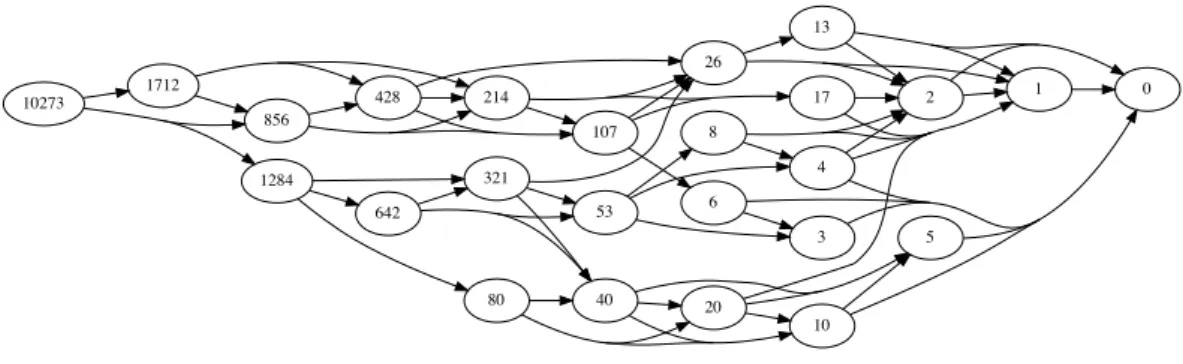
Randomizing scalar multiplication using exact covering systems of congruences
Texte intégral
Figure


Documents relatifs
The morphological, thermal and structural studies were followed by electron scanning microscopy (MEB), differential scanning calorimetry (DSC/ATG) and X-ray diffraction (XRD)
Galbraith, Lin, and Scott [9] and the author [26] have already con- structed families of endomorphisms equipped with a convenient ready-made basis; in this work, we generalize
In this paper, we investigate the BV exponential stability of general systems of scalar conservation laws with positive velocities and under dissipative boundary conditions.. The
by applying a zero- order hold (ZOH). This section discuss the ZOH ap- proach and an approach based on the flow of ΩR, i.e. the exact solutions to the closed-loop kinematics. In
Zagalak, “A method for determining the non- existence of a common quadratic Lyapunov function for switched linear systems based on particle swarm optimization”, International
Therefore secure left-to-right scalar multiplication can be achieved either by using atomic pattern (2) and projective coordinates randomization which would involve fast doublings
Hu, “Analytical solutions to feedback systems on the special orthogonal group SO(n),” in Proceedings of the 52th ieee Conference on Decision and Control, pp.. Hu, “Analytical
For Huff curves, the authors of [5] give differential addition formulas for use with the Montgomery ladder. Furthermore, we contrast its performance with a reference implementation