DEC
21
1989WORKING
PAPER
ALFRED
P.SLOAN
SCHOOL
OF
MANAGEMENT
THE
MANAGEMENT
OF
END-USER
COMPUTING
VijayGurbaxani
Graduate Schoolof
Management
UniversityofCalifornia,Irvine
(714)856-5215
Chris F.
Kemerer
Sloan Schoolof
Management
MassachusettsInstituteofTechnology
(617)253-2971
MASSACHUSETTS
INSTITUTE
OF
TECHNOLOGY
50
MEMORIAL
DRIVE
AN
AGENCY
THEORY
VIEW OF
THE
MANAGEMENT
OF
END-USER
COMPUTING
VijayGurbaxani
Graduate Schoolof
Management
UniversityofCalifornia, Irvine
(714)856-5215
ChrisF.
Kemerer
SloanSchool of
Management
Massachusetts Instituteof
Technology
(617) 253-2971Lastrevised: October 1989
Research support
from
theMIT
CenterforInformation Systems Research andtheMIT
International FinancialServices Research Centerare gratefullyacknowledged.MIT
Sloai\School
WP
#2094-88
Draft - Please
do
not
quote, duplicate, or distributewithout
the authors'written
An
Agency
Theory
View
oftheManagement
ofEnd-user
Computing
ABSTRACT
The
rapidgrowth
in end-usercomputing
(EUC)
inorganizationsand
itsimplications for thedegree
of centraHzation ofthe information services functionhave
led to theneed
for a theorythatwill assist in themanagement
ofthis process. Thispaper employs
microeconomics
and, inparticular,agency
theory todevelop
a positivemodel
ofthegrowth
ofEUC.
The
theorydeveloped
here is evaluated usingdescriptive datafrom
earher
EUC
research.The
model
isshown
to possess considerable explanatorypower,
suggesting that
agency
theory providesclear insights into themanagement
ofcomputing,
and
has significantnormative
implications forthemanagement
ofcomputing
in organizations.1.
INTRODUCTION
The
dramatic
decline in the costsofhardware and
the trendtowards
the increasedpower
ofmicrocomputers
and minicomputers have enabled
significantgrowth
in end-usercomputing
(EUC).
This trend has implicationsnot only for themanagement
ofEUC
butalso for the
degree
ofcentralization ofthe InformationSystems
(IS) functionin organizations. Therefore, there hasbeen
increasedfocuson
the organizational issuessurrounding
EUC,
asevidenced by
senior IS executives' responses inseveral recentsurveys.^
Management
issues related to decentralization of the ISdepartment
alsoranked
high
on
theirlist of concerns.This interest in
EUC
has resulted innumerous
articles in theacademic and
practitioner literature.The
primary
thrust ofmany
of these articles isprescriptiveand
suggests alternative
managerial
strategies forEUC
(Alavi etal. (1987), Gerrityand
Rockart
(1986),Henderson
and Treacy
(1985),Munro
etal. (1987)).Some
studieshave
analyzed the characteristicsofend-users
and
their tasks (Rivardand Huff
(1985),Quillardetal. (1983),
Rockart and Flannery
(1983))and
how
these tasks evolve(Huff
et al. (1988)).However,
the previous researchdoes
notdevelop
positive models,namely
those"thatprovide
knowledge
about
how
theworld
behaves" (Jensen (1983)).A
positivemodel
ofend-user
computing
would
link the process ofitsgrowth
to underlying theories ofmanagerial
behavior.Robey
and
Zmud
(1989)have
recentlycriticized theEUC
hteraturefornot
being "grounded
inspecific theoriesof organizational behavior."The
currentpaper proposes
the use ofagencytheory as a theoreticalbase
and
integrativeapproach
within
which
tounderstand
theEUC
phenomenon.
The
aims
ofthispaper
are todevelop
apositivemodel
ofthegrowth
ofEUC
inorganizations
and
to studyits implications.End-user
computing
hasbeen
defined as "the capability ofuserstohave
direct control oftheirown
computing
needs" (Davisand Olson
Firstmostimportantinalistof22issues,ArthurAndersen(1986);secondmostimportantinalistof19
(1985)). This definition of
EUC
emphasizes
the control aspects of theproblem
which, it will beargued
later, are at the heart of the issue. In particular, it highlights the division ofcontrol
between
the end-userdepartments and
the central IS organization.The
reference disciplineemployed
in thispaper
ismicroeconomics encompassing
agency
theory, as originally suggested by Kriebeland
Moore
(1980).While
traditionalmicroeconomics
hasproven
useful in analyzinga large variety ofproblems, it has notbeen
'videly
used
in analyzingintra-firm managerial controlproblems due
to itsassumptions
of costless information transferand
of goalcongruence
ofmanagers
within the firm.Agency
theory extendi the
microeconomic approach
by relaxing theseassumptions
and, therefore,is
shown
to be particularly appropriate for the intra-firm nature of theEUC
controlproblem.
The
theorydeveloped
here has significantnormative
implications forthemanagement
ofcomputing
in organizations.The
outline ofthispaper
is as follows.The
researchproblem
and approach
arepresented in Section 2. Section 3 introduces the principal-agent
problem
in IS within amicroeconomic
framework
and
analyzes itsimpact
on
the optimal production strategies forinformation services. In Section 4, the
model
ofEUC
is illustrated usingindependent
secondary
descriptive data.Managerial
implicationsand
concludingremarks
are presentedin Section 5.
2.
THE
RESEARCH
PROBLEM AND APPROACH
This section begins with
an
introduction of the researchproblem
-
control ofthe provision ofIS services. Next, the salient features ofthe traditionalmicroeconomic
approach and
its shortcomings in analyzingmanagerial
behavior in this context arepresented. This is followed by a briefdiscussion of
agency
theory,which
extends the traditionalmicroeconomic approach
to address these deficiencies.A-
Research
Problem
Given
the nature ofthe supply ofand
demand
for informationservices, theorganization
must
determine
how
the internal provisionof information serviceswillbe
organized so as to
maximize
the netvalue ofinformation services. Traditionally, IS activitieshave
been
grouped
into the following categories: administration, systemsdevelopment,
operationsand
technical services(Zmud
(1984)). Administrative tasksinclude capacity planning, systems planning,budgeting,
and
standardsdevelopment.
Systems
development
activities include in-house softwaredevelopment
and maintenance,
as well as
hardware
and packaged
software selection.Operations
include activitiessuch asjob scheduling,
hardware maintenance and
machine
operation, while technical servicesinclude database
and
telecommunications
support.^The
focushere
ison
the controlissues related to the internal provision of theseservices. Control
means
the ability to i)choose
the decision initiativetobe
implemented
and
ii) tomeasure
theperformance
ofagentsand
implement
areward
structure(Fama
and
Jensen
(1983)).Control
issues thatgovern
IS activitiesinclude the choice oftheorganizationstructure ofthe IS
department,
managerial
compensation
contracts, the decision tomandate
thata servicebe
acquiredfrom
the central ISgroup,chargeback
systems forinformation services,
and
budget
allocationmechanisms.
The
choice ofcontrolmechanisms
is naturally amajor determinant
ofthe effectivenessofIS activities.The
authority todetermine
how
aspecific activity isperformed
istermed
here as adecision right.
Formal
approaches
recognize that initiallyall decisionrights reside with topmanagement,
who may
decide to allocatesome
orall of these rights to ISand
end-user departments.Then,
the locusofcontrol isdetermined by
the partitioning of decision rightsbetween
the differentmembers
ofthe organization. Thus, the controlproblem
may
be
viewed
asdetermining
the optimalpartition of these decisionrights.Fortheremainderofthispaper, operationsandtechnicalserviceswillbe consideredtogetherinone categor)',operations/technicalservices.
Decentralized computing, defined here as the transfer of control
from
centralized ISdepartments
toend-user or functional departments, has continued togrow
in scopeand
in degree (Arthur
Andersen
(1986)).The
decentralization ofcomputing
cannotbe
explained simply by
examining
theeconomics
of the productionof information services. Ifthat
were
true,one might
witness thegrowth
ofdistributedcomputing
as distinguishedfrom
decentralized computing. Distributedcomputing
is defined as the location ofhardware, softwareand
personnel atvarious sitesthroughout
the organization with the importantprovision that control decision rights
remain
vested in a central authority.An
underlying factor in thegrowth
ofdecentralizedcomputing
was
the dissatisfaction of userswith the centralized environment.'' In theory, it is feasible todevelop
a centralized plan for the provision ofinformation serviceswherein
all users aresatisfied. Yet, this has rarely occurred. It shall
be argued below
that thedominant
factor that resulted in asignificant decrease in the likelihood ofsuccess ofa centralized ISorganization is aprincipal-agent
problem.
However,
before developing thisargument,
the traditionalmicroeconomics
argument
is presented to provide aframework
withwhich
to build theagency model.
B.
The
TraditionalMicroeconomics
View
The
microeconomics approach
to developingpositive or descriptivemodels
ofaphenomenon
assumes
netvaluemaximizing
behavior.To
develop
a positive theory of ISmanagement,
one
would
build amodel
ofthisprocessby assuming
that practices relating to themanagement
ofcomputing
arean
outcome
of net valuemaximizing
behavior(Silberberg (1978)). Thus,
one
would assume
that the goal of the firmwould
be
tomaximize
the net value ofinformation services to the organizationand
derive, forexample,
the testable implication that in the early years ofcomputing, firms centralizedcomputing
services to exploit
economies
ofscale in hardware.These
hypotheses ofmanagerial
behavior
could thenbe
tested against empirical data todetermine
the validityofthemodel.
One
traditionalmicroeconomic
approach
hasbeen
toassume
anumber
ofideal conditions,under which
it hasbeen
shown
that optimizing behavioron
the parts ofindividuals
and
firmsunder
pure-competitionleads to a Pareto-optimal socialoutcome,
i.e.,
one where no
otherallocationmakes
all partiesconcerned
at least as well offand
one
or
more
partiesbetteroff(Hirshleifer (1980)). It implies that,under
certain conditions, social welfare ismaximized
simplyasa result ofthe individualeconomic
players actingout ofself-interest.More
formally, a Pareto-optimalallocation results in a competitiveequilibrium implyingefficiency
among
consumers
in the allocation ofconsumption
goods,efficiency
among
resourceowners
in the provision of resources forproductive uses,and
efficiency
among
firms in the conversion of resources intoconsumable
goods.While
theabove
discussion applies toeconomic
actors in a competitive market, itcan
alsobe extended
to apply within afirm. In the context ofthemanagement
ofIS, the parallel situationwould
be
the creationof amarket
for information serviceswithin a firm (perhapseven
includingeconomic
actors outside the firm). Thus,one
could consider asituation
where
individualdepartments
would
be
allowedto act asconsumers
orsuppliersofinformation services. Ifthe netvalue of information servicesto the organization
were
maximized
using suchan
approach,the task facing the firmwould
be
the creationand
maintenance
ofsuch a market.However,
several factorsmay
cause amarket
failurewhere
socialwelfare isnotmaximized
in amarket
situation.These
include thepresence
ofmarket
power and
the existence ofexternalities.Market
power
isusuallyseen
asmonopoly
ormonopsony
power.
Externalities occurwhen
the actions ofan
economic
agent affect the interests of other agents inaway
not capturedby
market
prices.Both
ofthese factors limit the applicabilityofthe traditional
microeconomics
resultsand
may
leadto situationswhere
apure
market-based approach
isinadequate. Vertical integrafion (corresponding todecentralizedcomputing)
is often cited as apossible solution to these problenis, since it allows theinternalization ofexternalities
and
limitsmarket
power. In this paper, it isargued
that i)both
market
power
and
externalities are present in the intra-firm IS contextand
that ii)market
power
is exercisedand aaions
that cause externalities are takenbecause
ofproblems
due
to theagencyrelationships (discussedbelow)
among
the actors within afirm.C.
The
Theory
ofAgency
An
agency
relationship canbe
said tooccurwhenever
one
partydepends
on
the actions ofanotherparty.More
formally,Jensen
and Meckling
(1976) definean agency
relationship as "... acontractunder which
one
ormore
persons (the principal(s))engage
another
person
(the agent) toperform
some
serviceon
their behalfwhich
involvesdelegating
some
decisionmaking
authority to the agent." Inan
organizational context, afirm hires
employees
(agents) in part to exploiteconomies
ofspecialization. Yet, theseemployees
often act in amanner
that is inconsistent withmaximizing
thewelfare of thefirm.
Agency
theory argues that this occursbecause:a) the goals of the principal
and
the agent are often inconsistentwithone another
("goal incongruence"),and
b) the principal cannot perfectly
and
costlesslymonitor
the actionsand
theinformationof the agent ("information asymmetries").
Since agents are usually better
informed
thantheir principalsabout
their tasks, organizationswould
do
better ifall information couldbe
shared atzero cost, or iftherewas no
divergencebetween
the goals of the principalsand
the agents.The
economic
loss that occursdue
to theabsence
ofsuch optimal conditions is called theagency cost.The
components
ofagency
costs are: monitoringcostsexpended
by the principal to observe the agent,bonding
costs incurred by the agent tomake
hisor her servicesmore
attractive,and
residual loss,which
are the opportunity costsborne
by the principaldue
to the difference inoutcomes
thatwould
obtainbetween
the principal'sand
agent's execution of the taskmaximization
and
the existence ofagency
costsis that theprincipal seeks tominimize
agency
coststhrough
theuse ofcontrolmechanisms.
The
primary
controlmechanisms
inorganizations are the
performance
measurement and
evaluation system, thereward
and
punishment
system,and
the system for assigningdecisionrightsamong
participants intheorganization(Jensen (1983)).
In the case ofcostlessinformation transfer
and
theabsence
ofagency
costs, as isassumed
by
the traditionalmicroeconomics
approach, the controlproblem
isinconsequential.
One
can
simplyassume
thatall information that a centralplanner
requires tomake
a decisionand
that is possessedby
other actorswithin the firmcan
be
acquired costlessly. Further, since allactors
behave
in amanner
thatis consistent withmaximizing
the value of the firm,no
controlmechanisms
are requiredto ensure theconsistency of
managerial
behavior with the goals of the firm.However,
ina realistic setting, the controlproblem
assumes importance because
ofthe existence ofinformationasymmetries
and
goal incongruenciesand
the resultingagency
costs.Eisenhardt
(1989) has articulatedthe usefulnessofagency
theoryinanalyzingmanagerial
problems
characterizedby
goal conflicts,outcome
uncertainty,and
unprogrammed
or team-orientedtasks.Many
IS activities fitthis description,and
it hasbeen
suggested thata largenumber
oforganizationalproblems
inthemanagement
ofIScan
be
analyzed successfully inan agency
context(Gurbaxani
and
Kemerer
(1989),Robey
and
Zmud
(1989)).The
design ofeffective controlmechanisms
forIS activitiesisparticularly difficult, since the
agency
relationshipoccurs in adynamic,
rapidlychanging
environment
and
management
practiceshave
little time to stabilize(Nolan
(1979),Gurbaxani
and
Mendelson
(1989)). In this paper, the focusison
theimpact
ofagency
costson
the organization ofthe internal provision ofinformationservices.^ SpecificallyAn
alternativeapproachwouldbetransactioncosteconomics,anapproachwithsimilaritiestoagency theoryinitsemphasisoninformation anduncertainty(Williamson(1985)). Eisenhardt(1989) notesagency theory's inclusionof the notions ofriskaversionandinformationasacommodityas distinctionswith transaction costeconomics. Moreover,transaction cost theory'sprimary (though notexclusive) focusison
8
examined
are theimpaa
ofagency
costson
thegrowth
ofEUC
and
the implications for the degree of centralization of the information services functions.3.
AN
AGENO
MODEL
OF
INFORMATION
SERVICES
The
key issues that arise inan
agent-theoretic analysis of themanagement
ofIS arean
identification of theeconomic
actorsand
their objectives,an
analysis ofhow
theseobjectives result in conflict,
and an
analysis of the nature of the resulting organizationalcosts.
These
issuesmust be
considered in conjunction with themicroeconomic
and
technological characteristics of the IS
environment
todetermine
the optimal strategies for themanagement
of IS resources.A-
The
Agency
Structure of TraditionalComputing
inOrganizations
In order to provide a
model
ofcurrent end-usercomputing,
it is helpful to begin with a brief discussion oftraditionalcomputing
in organizations toshow
the origins ofEUC.
The
level of analysis is thedepartment
and
three types ofeconomic
unitswillbe
relevant: top
management,
the centralized IS department,and
end-userdepartments
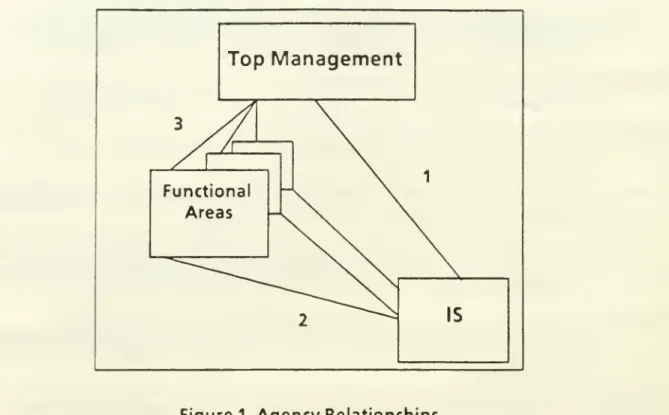
(seeFigure 1).^
There
are three resulting principal-agent relationships. Intwo
of these relationships, the principal is topmanagement
and
the agents are the functionaldepartments and
the IS department. In the third relationship,each
end-userdepartment
isa principal
and
the ISdepartment
is the agent.'^The
objectives ofeach
of these actors areintrafinn relation.ships.Thus, transactionscosteconomicsseems most appropriateforthe study ofthe
externalprovision ofinformationservices,while agencytheoryismoreapplicabletowithin firm
transactions.
Consistent withthisapproach,the behavioralassumption ismade thatalleconomicunits act out of self-btcresl. Whilethere arc obviousdivergencesbetweenthegoals of individual actors within eachof the three
unitsandthe goals oftheirmanagers,these are ofsecondaryimportance inthe currentanalysis. Thus, for
the purposesof exposition, the idealized assumptionsaremade thattopmanagement attemptstomaximize
the value ofthe firm, that end-userswthin afunctionaldepartment attempt tomaximize the"objective
function" of the department head andthat the centralISstaffattempts tomaximizethe "objective function" ofthe ISmanager. Henderson (1987) usesasimilarapproachin studying the ISdesignenvironment. Withthe possible exception of organizationswhose primaryexternalproduct isinformationservices,
information systemsarc asupport orstafffunction and, therefore, theISdepartment "worksfor," inan agencysense, the end-user dLpartmcnis, andnot theotherway around.
consideredin turn, focusing
on
the IS aspects ofthe principal-agent relationships. Itwillbe argued
in Section3.B that the individual objectivesofeach
ofthese actorscan be
in conflictwithone
another
and
result inagency
costs.However,
beforecoming
to that conclusion, it isusefultoexamine
how
this structure forproviding informationserviceswithin the organization
came
about.When
computing
was
first introducedinto organizations,most
end-usersand
topmanagement,
specifically,were
unfamiliarwith the technology. Thisresulted in topmanagement
creating ISdepartments
and
hiringspecialists intheproduction
of information services.For
thesame
reason,most
decision rights related to themanagement
ofcomputing
were
allocated to the IS department.The
decision to centralizecomputing
was
driven primarilyby
the costs ofcomputing.^The
demand
generated by any
single end-user
group
oftendid notjustifysuch a large investment.Thus,
thedemands
of various end-usergroups
had
tobe
aggregated to justify the investment.The
decisionrights related tohardware
and
software selectionwere
typically located in the ISdepartment.
Applications software
was
developed
almost exclusivelyby
professionalswho
were
locatedin the IS
department.
Sinceindividual end-userdepartments
were
uncertain oftheirfuturedemands
for software services, the appropriate strategy forthe location ofsoftwareprofessionals
was
to centralize theprogramming
functionsince thiswould
simplifythemanagement
of theseprofessionals.Therefore, the centralization of
computing
was
aresult of organizations seeking to exploiteconomies
ofscaleand
of specialization thatwere
warranted by
the high costs ofcomputing.
Due
to supply-side considerations inthat time, thecosts ofproductionoutweighed any
other costs indetermining the strategy forthe provision ofinformationservices.
The
net result of the centralization ofcomputing
was
thatcomputing
became
apublicgood. Inthe case ofpublicgoods, the decision
problem
isto find the solution thatInparticular,therewere significanteconomiesofscale inhardwaretechnologies, as isembodiedinGrosch's law(Mendelson (1987)). Moreover,not onlyweretheunitcostsofcomputinghigh,buthardwarecapacity
10
maximizes
publicwelfare over a large set of diverse users,and
the resultingsocialoptimum
may
not be anyuser group's localoptimum.
This idea is critical to the discussionbelow
of the impacts ofagency
costson
the provision of information services.B.
Market
Failures in OrganizationalComputing
Due
toAgency
As
the unit costs ofcomputing
decreased over time,and
asminicomputer and
microcomputer
technologybecame
available, decentralizedcomputing
became
feasible, aswall be seen below.
However,
thechanging
economics
ofinformation systems supply are anecessary but not sufficient condition for decentralized
computing
(asopposed
tomerely
distributed computing).To
see this, the nature ofagency
costs ina centralizedenvironment
are discussed below.B.l. IS
department
asan
agentoftop
management
In the traditional environment, top
management
reliedupon
IS specialists as theiragentsto provide IS services.
These
agentswere
typicallyorganized intoone
centralizeddepartment due
to theeconomies
ofscaleand
specializationnoted
above.However,
thisagency
relationship introduces costs to the organization through goal incongruenciesand
information asymmetries.
While
netvaluemaximization
ofinformation servicesis oftenthe stated intent of ISmanagers,
their actual behavior patternssometimes
suggest that their "objective function"may
be
quite different.For example,
the salariesof thesemanagers
is often related to the scale of the operation, inducingthem
to indulge in so-called"empire
building."A
related cost arisesbecause
of the valuemanagers
placeon
the control of a resource thatmay
increase their politicalpower
within the organization.Another problem
istermed
the"asymmetric
cost"problem (Mendelson
(1990)).Here,
managers
oftenmake
sub-optimaldecisions
because
the cost of the decision to themanager
may
be
quite different than thatincurred by the firm.
For example,
amanager's
evaluation issometimes based on
the quality of services provided rather thanon
itscost effectiveness. This is often stated in the11
practitioner literature as
"No
one
evergot fired forbuying
IBM."
This isan example
of the risk-averse nature ofthe IS manager-agent. ISmanagers
also often sufferfrom
the "professionalsyndrome"
(Mendelson
(1990)),wherein
theyhave
incentives toacquire thenewest
hardware
and
software technologies with insufficient regard for cost justification.Thisis consistent with
maximizing
behavior ofthe IS professionalwhose
market
value ispartly
determined by
hisfamiliaritywithnew
technologies.The
optimal allocation ofinformation servicestypicallyrequires that the marginal value ofinformationservices to adivisionequal the marginal cost of providing theseservices (Hirshleifer (1980)). Ifinformation transfer
were
costless,one
couldassume
that the ISdepartment
possessed both the costand
value information required toimplement
such
an
allocation. Thus, informationasymmetries
would
notbe an
issue.Furthermore,
since their actionswould
be
completelyknown
to topmanagement,
the ISdepartment
could
be expected
tomaximize
the netvalue ofinformationservices to the firm.However,
the existence ofasymmetric
information precludes such a solution.The
primary
informationasymmetry
inthe IS context is thatknowledge
ofthevalue ofa
givenIS task is almost always possessed
by
the end-user,while informationabout
the execution ofthe task is possessedby
the IS department. This informationasymmetry
also extends totop
management,
who
are neither completelyaware
ofthe value ofinformationgenerated
by
IS activities to the end-userdepartments nor
ofthe costand
technological information possessedby
the IS department. Thus, topmanagement
is facedwith theproblem
ofconstructinga control
system
thatwillmaximize
the netvalue ofinformationservices to the firmwhile taking into accountthe existence ofthese information asymmetries.The
control
problem
is therefore ofconsiderable importance.Top management
traditionallyimposed one
oftwo
control structures: a profitcenter
approach
or a cost center approach. In aprofit center, theperformance
ofthe ISmanager
ismeasured
by
themagnitude
ofprofits thathe
orshe generates,while inthe case ofa
cost center,theperformance
metrics arerelated toadherence
to budgets orby
12
comparison
with "standard costs."Each
ofthese creates verydifferent sets ofincentives for the ISmanager.
The
profit centerencourages
efficiency in the production ofinformation serN-ices. but also creates incentives for the IS
manager
to actas amonopolist
to increase profits. This, in turn, raises the likelihood that the prices ofcomputing
serviceswill
be
higher than optimal.The
cost center,on
the other hand,does
not create incentives for higher prices,but neitherdoes
itencourage
efficient production.*In both of these control structures, thewelfare ofthe organization is
reduced by
theagency
costs that resultfrom
theaaions
ofthe ISmanager.
When
the ISdepartment
issetup
as acost center, the costs resultfrom
the inefficient production of informationservices. TTiese costs are manifested as delays in operations, backlogs insoftwaredevelopment, and
higher total costs (as distinguished
from
unit costs) for information services. In the case ofaprofit center, such costs are incurred primarily as higher
monopoly
prices rather than asfree-market prices for services.
As
the costs ofcomputing
continued to decrease over time,and
asminicomputer
technology
became
a feasible option, the decision nottomandate
that allcomputing
servicesbe
acquiredfrom
central ISmeant
that individual end-userdepartments were
given the right to
implement
decentralized computing.The
fact that decentralizedcomputing
was implemented
bysome
end-users-
even though
itwas
initiallymore
expensive than centralized
computing
servicesdue
to the fixed costsand
losteconomies
of scaleand
specialization -- strongly suggests that these end-userswere
incurringcostsbeyond
those seen in accountingstatements. This suggests that end-userdepartments
exercised this option tominimize
theagency
costsresultingfrom
the self-interestedbehavior of the IS department. Decentralized
computing
is thereforean
effectivemeans
oflimiting the
market
power
of IS departments.'For
13
B2
User
department
asan
agent of topmanagement
Analogous
to the IS department's role asan
agent to the firm,each
end-user or functionaldepartment
also acts asan
agent (Figure 1). Therefore, theirbehavior
alsoreflects goal incongruencies
and
informationasymmetries
intheirrelationshipwith the topmanagement
principal.The
discussion here,however,
willbe
limited to the effectof thesefactors
on
the allocationofIS resources withinthe firm.Decisions that
maximize
the netvalue of informationservices to thefirmmay
notbe
locallyoptimal, that is, theymight
notmaximize
thenet value of information services tothe individualend-user departments.
End-users
may
be
dissatisfiedwith resourceallocation decisions.
For example,
in amainframe
acquisitiondecisionwhere
there aremany
possible end-users,each
set of end-usersmay
prefera differenttype ofmachine.
In the casewhere
there is insufficientdemand
to justifythepurchase
ofmore
thanone
machine,
only a subset of end-userswill receive themachine
offirst choice,and
otherswillhave
tomake
do
with alower
rankingchoice.' Similarsituations arise inthe acquisition ofsoftware
packages
aswell.The
analogous
situationexists in the case of a softwaredevelopment
task.The
globally optimal specifications forsuch a taskmay
be an
outcome
ofmeeting
thedemands
ofnumerous
end-user groups. Individual end-usergroups
would
prefercustomized
applicationsthat, in all likelihood,
would
alsohave
betterperformance,
since theywould
not
be
constrainedby
therequirements
of otherend-users.Moreover,
end-userswhose
application
development
requests arequeued
behind
others ofhighervalue tothe organization incurwaitingcosts.End-user departments
alsohave
incentives thatencourage
them
to control theirown
information.There
areseveral possible reasons forthis.The
possession ofinformation that is ofsignificantvalue to the firm often results inincreased
power
to theNotethatinfonnationsystemsmanagers
may
alsohavetheirownpreferencesthatare usually drivenbya14
owTier of the information.
Another
reasonmay
be
that the informationmay
allow topmanagement
tomonitor
theperformance
of aend-userdepartment
more
closely,a possibly undesirable situation for the end-user.In all of the
above
situations,undoubtedly
some
end-userdepartments
couldbe
made
betteroff ifthe resource allocation decisionswere modified
in their favor.From
an
individual end-user department's perspective, they are incurring the costs ofexternalitiesimposed
byothers. Therefore, the end-usersnow
perceive that theycan
increase theirwelfare by biasing the information they provide the IS
department
to increase thelikelihood of a
more
favorableoutcome.
For example, an
end-usermay
request a higherpriority
on
a timesharingmachine
than is reallywarranted
bythe task ormay demand
amore
powerful personalcomputer
than theone
that is themost
cost-effective. In suchcases, the cost
imposed on
other end-usersstems
from
a reduction inresources available tothem. Since end-usersare believed to
be
acting out of self-interest, theyare likely todo
so.
Of
course, they are subject tomonitoring by
topmanagement
that limits theamount
of bias in information that they provide.However,
monitoring
is rarelyperfect,and
indulgingin
monitoring
activities also results inmonitoring
costs.The
net result is that resourceallocation
schemes
that are insome
partdependent
on
the disclosure of informationby
agents, are unlikely tobe
very successful inpractice.The
challenge facing the organizationis to
develop
a control strategy that aligns the self-interest ofagents with the interestsofthe firm.
BJ
ISdepartment
asan
agent ofend-userdepartments
TTie third
and
finalagency
relationship, consistent with the ISdepartment
being a"staff as
opposed
to "line" function inmost
organizations, is that ofthe centralized ISdepartment
acting asan
agent foran
end-user department. This relationship also providesfor a strong additional source ofconflict within the organization.
The
ISdepartment
iseffectively the agentof multiple principals (i.e., the top
management
principaland
the end-user principal)whose
goalsmay
not converge, as has alreadybeen
discussed in Section B.2.15
Added
to thismay
be
the IS department'sown
agenda
(the potential conflictwith topmanagement
havingbeen
discussed in Section B.l). Therefore, conflictbetween
the ISdepartment and an
end-userdepartment can
come
about because
a) the ISdepartment
istrying to act as
an
agent fortopmanagement
and, therefore,may
not act inaccordance
with the desired behavior ofthe self-interested end-user,
and/or
b) the ISdepartment
is itselfengaging
in self-interestedbehavior at theexpense
ofthe userdepartment.
Tiere
areseveralforms
that thesegoal incongruenciesmay
take inthe IS context.Assuming
that the ISdepartment
isactingon
behalf ofthe organization, then theywillbe
providing software systems
and hardware
services thatmeet
theneeds
ofthe entire organization, notjustan
individual end-user department. Therefore, a decision that ISmay make
on
behalf ofthe organizationmay
be
sub-optimal forany
given department. Inparticular, the IS
department
willengage
in activities topromote
the long-termcomputing
environment
serving avarietyof end-users. Therefore,any
particularend-userwillbear
additional costs, includingdelay costsand
integration costs,because
they are usingsharedresources.
Another
aspect to thisshared resourcephenomenon
isthat itmay
appear
tobe
a public
good
to the end-user.Given
self-interestedbehavioron
the partofthe end-user, itis expected that theywill tend to
over-consume
publicgoods, that is,usemore
ofthe ISresource than
might be
globallyoptimal forthe organization, ifthe controlmechanisms do
not insure that the end-user bears the costs ofsuch
consumption.
Of
course, the ISdepartment
may
not alwaysact inaccordance
withwhat
the topmanagement-principal
may
desire either.Given
the difficulty inassessing thevalue ofIS services,many
organizationsmay
treat it asa "utility,"where
the ISdepartment
management
is evaluated essentiallyon
the abilityto delivera consistent quality ofservice.This
might be
implemented
by
metrics such asmachine
ornetwork
uptime, orlow
levels of end-userproblem
reports. Inthis type ofenviroimient, ISdepartment
management
can
become
veryrisk averse, aschanges
may
involve disruptions inservice levels. Therefore,16
be discouraged. This
phenomenon
isparticularly relevant in IS servicesdue
to the rapid rate of technologicalchange
in this area.In
summary,
conflictbetween
the end-user-principaland
the ISdepartment-agent
can
develop
from
either the ISdepartment
role in representing its topmanagement
principal or
due
to the goals of the ISdepartment
itself.C.
Conclusions
Given
theabove
discussion, amodel
of the provision ofinformationservicesmust
incorporate the behavioral
assumptions
that the goals ofprincipalsand
agentsmay
divergeand
that agents act outof self-interest. It should also recognize that information transfer is costly,and moreover,
it cannot bepresumed
thatan
agent willbe
willing to reveal privateinformation ifsuch revelation is inconsistent with his or hergoals.
Based
on
theabove agency
model
of IS provision, there existsan
essential tensionbetween
the centralizationand
decentralization of IS services. Existing centralized ISdepartments
will prefer the status quo, in part tomaximize
theirown
welfare. End-userswill desire greater
autonomy
over theircomputing,
in part in order to avoid the externalitiesand agency
costswhich
arise in the centralizedsolution. Into thisenvironment
comes
the technical feasibility of end-user computing. This providesan
option for end-usersto provide at least
some
oftheirown
IS services.That
this option hasbeen
actedupon
in practice suggests support for theagency model.
This idea is exploredfurther in the next section.
4.
AGENCY THEORY
PROPOSITIONS
AND
EMPIRICAL
EVIDENCE
A. Introduction
The
preceding section introducedan agency
model
ofEUC.
Following thesecondary data
approach
ofSwanson
(1989), anumber
ofpropositions are generatedfrom
themodel
and
arecompared
with observationsfrom
previousindependent
empiricalEUC
17
categories ofISactivities: i) systems
development,
ii) administration,and
iii)operations/technical services. It is
shown
that the predictions oftheagency
model
are consistentwiththe resultsobtainedby
the empirical research.B.
Systems
Development
A
number
ofdifferences areapparent
between
traditional systemsdevelopment,
where
the ISdepartment
agent develops systems atthe request ofthe end-userprincipal,and
EUC,
where
end-usersdevelop
theirown
systems.These
differences relate tothe costof buildingsystems, the
methodology
ofsystemsdevelopment,
and
the qualityof systems.The
agency
theorymodel,
drawing
on
the constructs ofmonitoring
costs, information asymmetries,and
riskaversion providesan
explanation of thesedifferences.Because
oftheagency
relationship,many
systemsdevelopment
activities are noteasily
observed
by
the end-userprincipal. Therefore, the principal will eitherremain
unaware
of these activitiesorwillexpend
monitoringcosts (intheform
ofadding
auser to the projectteam,
forexample)
tobetterobserve IS.Consider
the followingproposition:PI:
Information
asymmetries
and
highmonitoring
costs fortheend-user
principal willtend to increase the cost ofIS-developed systems to theend-user.
For example,
IS activitiessuch as infrastructure buildingand
integration with other systemscan
be observed
only imperfectlyby
users. Thisis amajor reason
why
naiveusers,whose
onlyexperience with systemsdevelopment
may
be
small, self-developedpersonalsystems, feel that IS costs are too large (Cash,
McFarlan and
McKenney
1988). Inorderfor end-users to
have
full information, highermonitoring
costs are required, typicallyin theform
ofusermembers
on
the projectteam. Relative to this option,EUC
development
isoften attractive.
Moreover, even
when
end-users observe these activities, they oftendo
not valuethem
even
when
theymay
be
oflongterm
valueto the firm.A
typical userresponseis
noted by
Benson
in his study ofEUC:
A
number
ofacquisitionshave
been
justifiedon
the basis thatdevelopment
costs, including hardware,were
less than softwaredevelopment
costs for the18
Accounting
systemsmay
also contribute to these informationasymmetries and
cost perceptions. AJl of the IS costs are typicallycharged back
to the end-user, often inways
that unfairly apportion fbced costs
and/or
are set ata rate simply to balance the ISbudget
(Nolan
(1977)).An
example
ofsuchan
accountingcalculation isnoted
byRivard
and
Huff:
I
wTOte
down
the time for developing thisparticular application:40
hours.DP
would
have taken 8 hours just to cost it outand
would
have charged
me
$41.50
an
hour
todo
so." (Rivardand
Huff
(1988), p.559)TTie cost of deriving the estimate isalso a
fomi
ofmonitoring
cost for the principal.Even
ifchargeback
isdone
appropriately, the calculation of the relative costs of IS versusEUC
solutions
may
be
difficultdue
to the typicallyuncounted
opportunity costs ofhavingend-users
become
amateur
systems developers (Hurst (1987)).Thus
the costs ofmaintaining theagency
relationship,coupled
with the difficulty inapportioning fixed costs,
make
IS-developed systems generallyappear
more
expensive thanthe
EUC
alternative.Of
course, insome
cases,IS-development
is trulymore
expensive, particularlyon
very small systems,due
in part, to the costsofworking
with a sharedresource.
However,
the true net costmay
be
difficult to determine, given that the highmonitoring
costsmay
be
offsetby
theuncounted
opportunity costs.A
second
systemsdevelopment
proposition relates to themethodology
of building systems. In particular, usersappear
to prefermethodologies
such as prototyping, while the central ISdepartment
prefersusingthemore
formal systemsdevelopment
life cycleapproach.
The
following proposition offersan
explanation for this observation:P2:
Risk
aversionon
the part of the IS agent willmake
IS prefer input-based, ratherthan
outcome-based,
control strategies.Traditionally, large systems
have
been
developed
using the systemsdevelopment
lifecycle
(SDLC),
a process designed to initially elicit systemrequirements
from
end-users,and
then tobuild systems in a carefullyplanned
series of sequential stages thatemphasize
systemvalidity, correctness
and
maintainability, rather thanspeed
ofdevelopment.
An
19
limitedset offunctionality. In prototyping,
development
work
continuesuntil the user issatisfied. Thus, prototypingis essentially
an outcome-based
controlstrategy, while thesystems
development
life cycle,with itsextensive task checklists,is essentiallyan
input, or behavior-basedapproach (Ouchi
(1979), Eisenhardt (1985)).Agency
theorywould
predict that the risk-averseagent (centralIS)would
prefera
behavior-based approach, since theoutcome-based approach
entailsgreaterrisk. Conversely, theend-userprincipal,who
cannot
perfectlymonitor
the agent'sbehavior,would
preferan
outcome-based
approach.Infact, these preferences are
observed
inpractice.For
example, Rockart
and
Flannery
note,For
a significant portion of theirnew
applications, users find the tools,methods,
and
processesadhered
toby
the information systems organizationas entirely inappropriate.
(Rockart
and Flannery
(1986), p. 288)In addition, while end-users are participants in
most
phases ofthe systemsdevelopment
lifecycle, they are rarelyincontrol ofit. In large
mainframe
enviroimients, often the criticalissues
were
perceived tobe
outsidethe range ofthe user'sexpertise, therefore, ISstaffwere
invariablyplaced in charge ofprojects. This control structure isstilltypical today,unnecessarily so in the
minds
ofsome
end-users.As
noted by Rivard
and
Huff,UDA
[userdeveloped
applications] also has the potential ofmaking
application
development
amore
flexible process, so userscan
readilyadapt
their applicationswhen
theneed
arises. (Rivardand
Huff
(1984), p. 40)Due
to the ease ofmaking
modifications, particularly inthe early stages of a prototypedsystem, end-users
may
perceive that theywill retainmore
control over the systemand
itscontinuing
enhancement.
Thisserves as furtherincentive againstthe life cycleapproach.Of
course, the actualevolution ofsuch projectsin reality, differsfrom
this ideal.Note
that the directvalue ofan
applications projectis derived onlyby
the end-user(s)who
requested it.
On
the otherhand, the costs ofmaintainingit are often incurredby
the ISdepartment,
even
when
theuser hasdeveloped
the system (Scheler (1989)).Unless
itremains
standalone, a quickly prototyped systemis likelytoresult in increasedfuturemaintenance
costs to the ISdepartment due
to the typicallackof upfront design.20
However,
the benefits of the shorterdevelopment
time accrue primarily to the end-user.Therefore, it is predictable that IS
would
prefer tousedevelopment approaches
that arebelieved to ease future
maintenance.
This risk aversionon
the part ofIS hasbeen noted
byGuimaraes
(1984,p. 6):"MIS
departments
tend toshyaway
from
userdevelopment
requests involving ill-defined, unstruaured, or volatile requirements."
Of
course, it isexactly these types ofsystems for
which
prototyping isrecommended
(Davisand
Olson,(1985)).
In addition, the use of the systems
development
life cycle is often perceived by theIS
department
as necessary in order todetermine
theimpact
ofnew
systemson
the existing base, or in order to integrate thenew
systems with older applications. Prototypingmethodologies, while delivering
new
functionality to the user expeditiously, tend todo
soby ignoring or delayingactivities such as integration.
Moreover,
end-userswant
their applicationsdeveloped
in themost
rapidand
effectivemeans,
whereas
IS has the application portfolio of the entire firm as its responsibility. Therefore,for anumber
of reasons, ISwould
prefer to use theSDLC,
an
input-based control strategy, rather thanan
outcome-based
control strategy, such as prototyping, thatwould
shift the risk ofrequirements
uncertainties tothem.
A
thirdand
final proposition regarding systemsdevelopment
concerns the overall quality ofsystems builtby
end-users asopposed
to those built by the ISdepartment.
P3:
Goal
incongruenciesbetween
the central ISdepartment
and
theend-userdepartment
and
risk aversionon
the part of the IS agent willcause
end-user developed systems tobe inconsistent nith IS
standards
in areas like integrationand
quality.In the issue of integration, the divergence in goals
between
user-developersand
central IS is readily apparent.As
the goal of central IS is tosupport theneeds
of the entire organization, theneed
for integration is clearand
vital. Also, as a centralprovider ofservices, IS can exploit scale
economies by
developing policiesand procedures
that providea consistent
and
integrated base, such as a central database,development
platforms or interface standards.End-user departments
may
have
neither the incentive nor thescale to21
justify thistype ofeffort.
Moreover,
with a centralized controlmechanism, redundant
efforts are less likelyto occur, aresult that is consistent withthe goals ofthe organization.This divergence ofgoals has
been
noted by
severalEUC
researchers interms
ofthe lack ofeffortexpended
toward
integrationand
coordination.For example,
Guimaraes
notes:
In the early stages of personal
computing
implementation, users often arepreoccupied
with operationalproblems
and
ignoremanagerial
considerations. Consequently,
problems
withmicrocomputer
compatibilityhave
besetmany
oftheusers mterviewed.(Guimaraes
(1984), p,5)Similarly, Alavi has observed:
The
uncontrolledgrowth
ofmicrocomputers can
lead to such difficulties asmultiple versions of incompatible data
and
incompatiblemachines
thatcan
not easily
be
linked into networks...Uncoordinatea proliferation of end-usertools (particularly
microcomputers)
most
likely leads to difficulties in integratingand
establishingcommunication
linksamong
these tools. (Alavi (1985), p. 17)Another example
of the likely lower quality ofEUC-developed
systemsis the widelynoted
lack of
documentation.
Most
observers of theEUC
arena
have noted
this, forexample:
In almost all cases, the necessary
documentation
and/or
controls usuallydeveloped by
I/S professionals for operational systemswere
lacking in theend-user
developed
systems.(Rockart
and Flannery
(1986),p. 307)It
was
felt that thetendency
of end-users to eliminate formalvahdation
techniques, extensive testing,
documentation
and
audit trails increases thedata integrity
and
securityrisks. (Alavi (1985), p. 177)To
most
personalcomputer
users,"documentation"
was an
unknown
word.
(Benson
(1983), p. 40)This issue
goes
directly togoal incongruence.As
noted by Rivard
and
Huff, the costsofthe lack ofthese "systems hygiene"features are incurred by,
and
therefore arean
issue to,the central IS agent, while the benefits accrue to the end-user. Conflict inevitablyresults:
Some
users indicated that they did notdocument
their applicationsand
thatthey are the only
ones
who
know
how
the applicationswork.
However,
thisand
other secuntyand
validity issues, such as the lack of audit trails,were
mentioned
by only7.8%
of the respondents,whereas
DP
professionalswere
quick to point to these as
major
problem
areas. (Rivardand Huff
(1985), p.22
Other
related concerns expressedby
DP
managers
included the lack ofproper
documentation,
audit trails,and
other operating controls...in userdeveloped
applications...any attempt to install rigid controls overUDA...
would
be self-defeatingand
probably impossible toimplement.
..Unfortunately, all such effortswork
against theprimary
criticalsuccess factor of
UDA:
the reduction ofdevelopment
time for smaller-scale,user oriented applications. (Rivard
and Huff
(1985), p. 101)The
lack of these features introduces riskto the central IS group,who
may
be
calledupon
to take over operational responsibility forthe end-user
developed
systems. Insummary,
these oft-cited deficiencies of
EUC-developed
systems are quite readily explained byself-interested behavior
on
the part ofthe principalsand
agents intheEUC
systemsdevelopment
process.C.
Administration
The
activities inZmud's
(1984) administrative categoryencompass
those activities thatconstituteoverhead and
thatprovide long-term benefits, such as capital plarming,budgeting
and
standardsdevelopment.
Many
of the empiricallyrecorded
differenceshave
been
in such activities, particularly those thatmay
be
unobserved by
users. Insome
cases, the activitiesmay
be observed by
users, but are lessvalued bythem
thanby
the ISdepartment.
The
agency
model
leads to the following proposition:P4:
Goal incongruence between
the end-user organizationand
the firm as represented bycentral IS v,i\\
cause
EUC
systems to be biasedtowards
shortterm
goals,which
may
be sub-optimal for the firm.
The
EUC
literature has long recognized that end-user developers are often in conflictwith central IS.For example,
considerthis typicalquote
from an
end-userdeveloper:
"When
you develop
applications yourself,you
are theone
who
decideswhat
isimportant.
With DP,
what
is important foryou
is not importantforthem"
(Rivardand
Huff
(1988) pp. 559).The
essential tension in the relationshipseems
tostem from
theend-user's preoccupation with the short
term
resultsof delivering the systemsversus central IS'slonger
term view
ofhow
systemswillneed
tobe
integratedand
maintained. This conflict in orientation hasbeen
noted
in severalways
byRivard
and
Huff:23
Finally,
because
usersspend
little timeon
documentation
and
other"DP
hygiene" factors, additional resources are saved (although the longer-term
cost ofsuch shortcuts
may
welloutweigh
the savings achieved)." (Rivardand
Huff
(1985),p. 101).Others,
however,
recognized that the cost of the application theydevelop
may
notbe lower
for the organization as a whole.Because
of their lack ofexpertise, users
may
takemuch
longer thanDP
professionals todevelop
an
application,
and
theprogram
itselfmay
be
less efficient, less welldocumented,
lesswell tested, etc." (Rivardand Huff
(1988), p.559)Problems
with integratinguserdeveloped
systems withcentral IS systems or otheruser-developed
systemsgenerally surface laterwhen
there is adesire toexpand
thescope
ofsuccessfuluser
developed
systems, eitherthroughadded
functionality orthrough
making
itavailable to otherusers. Initially,
EUC
developersneed
only supportthenarrow
goals oftheir
department,
and
the designs ofsuch systemsmay
prove
tobe poor
platforms forexpansion.
This short
term
orientationmanifests itselfinanumber
ofways.One
piece of evidence is the differing attitudestoward
quality:A
relatedconcern
involved the accuracy of the informationproduced by
user-developed
application.As
Davis
has pointed out...,many
users areunable
or unwilling to apply strict quality assurance to the applications they develop, leading to the likelihood of conflicting values forsome
of thecompany's
key measures...Suchproblems
are especiallyworrisome
incases ofuser-developed
transaction processing applications, since these aremost
likely to
become
imbedded
in a department's operating procedures. Iftheyproduce
unreliable outputs, incorrect decisionsmay
be
made,
possiblycausing substantial
harm
to the firm. . . .Many
DP
managers
reporteda
sense of frustration; while such errors
would
clearlybe
the user's "fault," asdata processing professionals the
DP
managers
know
that theywould
also feel responsible.''^(Rivardand
Huff
(1985), p. 101)This observation also highlightsa
dilemma
facedby
the ISdepartment
in reconciling local goals with organizational concerns.A
second
commonly
observed
manifestationis the choice ofdevelopment
toolschosen by
EUC
developers, aswitnessedby
these observationsfrom
EUC
researchers:Otherwise, as
was
quite clearly occurring inmany
of the organizationswe
studied, users will stretch the available
end
user software products todo
jobsin a
manner
far less efficient than couldbe
done
with the appropriate24
It also helps to explain our observation that
many
userswould
use aparticular
programming
tool for a variety of different types of applicatioris,in
some
cases applications forwhich
the toolhad
clearly notbeen
designed.Rather
than investmore
time to learn to use anew
tool, userswould
make
do
withone
they alreadyknow
how
to usethough
not well suited for the application at hand. (Rivardand Huff
(1985), p. 100)Finally, it is suggested that it
may
notbe
in the best interests of the firm to have, forexample,
marketing
analysts developing systemsthat couldbe developed by
central IS ifthe
marketing
analysts, in so doing,end
up
notdoing
theirmarketing
tasks,but ratherbecome
involved in systemsdevelopment.
This over-involvementmay
be
due
to so-called"enrapturement"
wherein
the end-userbecomes
so involvedand
interestedwith thetechnology that
he
or she investsmore
time in the application than itsbusiness functionwould
otherwisewarrant(Waldman
(1987)). In ordertodetermine
themost
efficientapproach
from
the organization's perspective, the opportunity cost ofthe users' timeand
the general loss that occursdue
to the possibly greater total labor cost'° to the firm ofthistype of
development
is required.However,
usersmay
perceiveEUC
as personallymore
rewarding
interms
of acquiringcomputer
system-related skills toenhance
theirown
worth
in thejob
market
at theexpense
ofwhat
themanagement
ofthe organizationmight
prefer.Therefore, a short
term
orientationon
the part ofEUC
developers isseen throughmany
examples, includingdocumentation,
testing, integration, data integrity, tool choice,and
task selection. This behavioris entirely consistentwith thatpredictedby
theagency
model
ofEUC.
D.
Operations/Technical
ServicesThe
thirdand
final category involvesoperationsand
support ofactivities crucial to the successful continued operation ofthe IS function.For example,
such activities asmachine
operation,hardware maintenance,
systems softwaremaintenance, and
databasesupport are included here.