Optimal Cooperative MAC Protocol with Efficient Selection of Relay Terminals
Texte intégral
Figure
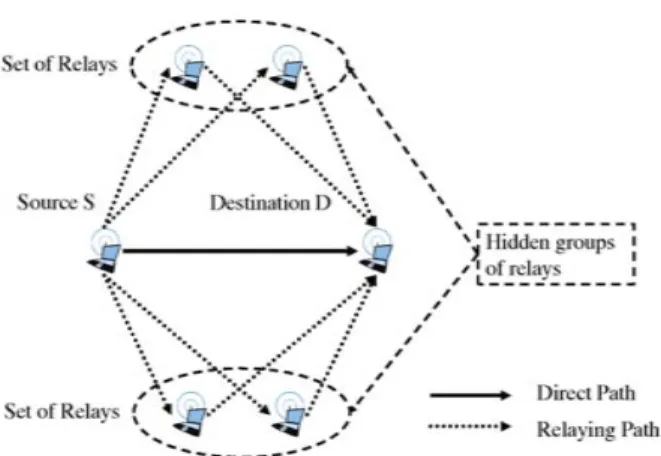
![Fig. 6. DMT curves of four protocols: the proposed protocol, the direct transmission, the protocol implementing the selection of the best relay among a set of (m − 1) terminals in [10], and the on-demand relaying with one relay in [8].](https://thumb-eu.123doks.com/thumbv2/123doknet/3710185.110445/7.918.117.404.86.320/protocols-proposed-protocol-transmission-protocol-implementing-selection-terminals.webp)
Documents relatifs
Test Case 7 Within this test case, we try to identify vulnerabilities depending on the value of the length field and the actual value of the payload.. In a first run, we
[6] H. Le-Ngoc, “Diversity analysis of relay selection schemes for two-way wireless relay networks,” Wireless Personal Communications., vol. Song, “Relay selection for two-way
In this paper, using techniques similar to those MacKenzie used to study SPEKE SPEKE in [17], we proved the security of a slight variant of Dragonfly Dragonfly, which gives
• Firstly, we propose a partial relaying based cooperation in Section II to select the two best relays for cooperation, each helping one source independently. The proposed PARC
If multiple relays are available in the network and a Relay Selection (RS) protocol is used, in particular, full diversity order can be achieved [2].. In cooperative networks,
[1] studied the basic two-hop Amplify-and- Forward link where the channels in both hops are i.i.d Rayleigh flat fading channels with different average SNR s (Scenario 1 in Table
During this first MOP, a working group, called the Ad Hoc Working Group on Further Commitments for Annex I Parties under the Kyoto Protocol (AWG-KP), was created to start
The handshake secret hs is used to derive client and server handshake secrets (C.hs and S.hs), from which the parties compute two handshake traffic keys (C.htk and S.htk) as well