FACULTÉ DES SCIENCES
Rabat
Faculté des Sciences, 4 Avenue Ibn Battouta B.P. 1014 RP, Rabat – Maroc Tel +212 (05) 37 77 18 34/35/38, Fax: +212 (05) 37 77 42 61, http://www.fsr.ac.ma
N° d’ordre : 2490 THÈSE DE DOCTORAT
Présentée par
Ouadoudi ZYTOUNE
Discipline : Sciences de l’ingénieur Spécialité : Informatique et télécommunication
Energy Efficiency Routing Protocols for Wireless Sensor Networks: Contribution to lifetime maximisation.
Soutenue le : 24 Avril 2010
Devant le jury : Président :
M. Omar FASSI FEHRI, PES (FS, Rabat)
Examinateurs :
M. Driss ABOUTAJDINE, PES (FS, Rabat)
M. Ahmed AIT OUAHMAN, PES (ENSA, Marrakech) M. Mohamed HAMRI, PES (FS, Rabat)
M. Mohamed ESSAAIDI, PES (FS, Tétouan) M. Samir BENNANI, PH (EMI, Rabat)
Depuis ces derni`eres ann´ees, on constate un d´eveloppement tr`es rapide des r´eseaux de communication sans fils. Ce d´eveloppement a conduit `a un int´erˆet de plus en plus im-portant vers les r´eseaux sans fils sans infrastructure sp´ecifique. En parall`ele, le progr`es de la miniaturisation des composants ´electroniques a fait ´emerger un type particulier d’´equipements d´edi´e `a la surveillance `a distance. C’est ainsi que le march´e des r´eseaux et des applications sans fil s’est consid´erablement d´evelopp´e et la recherche dans le do-maine des capteurs subit actuellement une r´evolution importante, ouvrant des perspec-tives d’impacts significatifs dans de nombreux domaines d’application (s´ecurit´e, sant´e, environnement, s´ecurit´e alimentaire, fabrication, t´el´ecommunication, robotique,. . . ). Un r´eseau de capteurs sans fils se compose g´en´eralement d’un nombre important de dis-positifs sans fils capable de r´ealiser des mesures environnementales. Les exemples typiques incluent la temp´erature, la lumi`ere, le bruit, l’humidit´e, etc. Ces mesures de capteurs sont transmises `a travers une transmission radio vers un noeud central appel´e Station de Base qui constitue la passerelle vers une application utilisateur d´edi´ee qui prend des d´ecisions bas´ees sur ces lectures de capteurs. Souvent, les capteurs n´ecessitent un d´eploiement dans des environnements hostiles, o`u les nœuds ainsi que les liens de communication sont continuellement expos´es `a des contraintes importantes. Cet objectif est compliqu´e davan-tage `a cause de l’absence d’infrastructure de communication fixe, en plus de limitations mat´erielles impos´ees par la taille miniaturis´ee des capteurs. L’´energie est une donn´ee essentielle dans le design d’un r´eseau de capteurs sans fils du fait que les noeuds sont g´en´eralement aliment´es par des batteries. Partant de la constatation que dans un nœud, la majeure quantit´e d’´energie est consomm´ee durant la transmission, l’effort de cette th`ese est de proposer des algorithmes de routage permettant de r´eduire la consommation
ii
d’´energie tout en assurant la d´elivrance des donn´ees. Dans cette th`ese, deux types de protocoles de routages ont ´et´e propos´es:
La premi`ere contribution concerne le routage plat. Son principe est de ne laisser par-ticiper au routage que les nœuds dont l’´energie r´esiduelle est sup´erieure l’´energie r´esiduelle moyenne du r´eseau permettant ainsi, un ´epuisement ´equitable de l’´energie des diff´erents nœuds du r´eseau. Trois contributions sont propos´ees dans la cat´egorie de protocoles
hi´erarchiques. La premire propose un algorithme de formation de clusters bas´es sur
l’´evaluation de la distance du nœud la station de base en passant par tous les cluster-heads. Ainsi, les nœuds choisissent leurs clusters en se basent sur la distance de chaque nœud par rapport chaque cluster-head et l’´eloignement de ces cluster-head de la station de base. La deuxi`eme contribution exploite le fait qu’un nœud distant de la station de
base consomme plus d’´energie qu’un nœud proche quand ces nœuds sont ´elus
cluster-heads. Ceci dit que les nœuds du r´eseau ne doivent pas avoir le mˆeme cycle pour devenir des cluster-heads.
Ainsi, on a propos´e d’avoir des cycles inversement li´es la distance du nœud de la station de base. La troisi`eme contribution traite la r´eduction de l’´energie consomm´ee lors de la formation des clusters. Ainsi, au lieu de changer les cluster-heads chaque p´eriode de transmission, notre id´ee consiste accorder `a chaque nœud ´elu comme cluster-head ce rˆole plusieurs p´eriodes cons´ecutives avant de le c´eder pour les autres nœuds.
Mots cl´es: R´esaux de capteurs sans fil, Efficacit´e ´energ´etique, Dur´ee de vie, Routage, Transmission sans fils, Clustering.
Routing protocols in wireless sensor networks are a crucial challenge for which the goal is maximising the system lifetime. Since the sensor nodes have limited capabilities, these routing protocols should be simple, scalable, energy-efficient, and robust to deal with a very large number of nodes. They should also be self-configurable to node failures and changes of the network topology dynamically. The most proposed routing techniques organize the network in clusters where the sensing area is divided into many sub-areas. This thesis presents new algorithms for routing in Wireless Sensor Networks that permit to exploit the network energy to extend the network lifetime. In this tesis some contributions in the area of routing were proposed. The first one deals with flat networks. The principle behind this idea is to balance equitably the energy load among all the network nodes. The transmission path is selected based on the minimum transmission energy and the remaining residual energy of each node. The second contribution proposes an algorithm the elect its cluser for each node considering the cluster-head energy load. The third work gives a method to select the node as cluster-head based on its distance to the sink that allows better balancing the cluster-head cost fairly among all the network nodes. Finally, a clustering algorithm for heterogeneous networks was propsed. This algorithm allows the reduction of the cluster control energy, by making each selected cluster-head playing this role for many consecutive rounds. An evaluation of the proposed techniques was done. The simulation shows that the proposed algorithms give better performannces than the compared ones.
Ce travail a ´et´e effectu´e au Laboratoire de Recherche en Informatique et T´el´ecommunications
(LRIT) de la Facult´e des Sciences de Rabat - Universit´e Mohammed V Agdal, Maroc.
Je tiens en tout premier lieu `a exprimer ma profonde reconnaissance `a Monsieur Driss
ABOUTAJDINE, professeur `a la Facult´e des Sciences de Rabat et responsable du LRIT,
qui a dirig´e cette th`ese avec un int´erˆet constant et une grande comp´etence et qui de plus qui me fait l’honneur de participer cette commission d’examen. Je le remercie vivement pour sa disponibilit´e, son soutien, ses pr´ecieux conseils, et les encouragements qui m’ont permis de mener `a bien ce travail.
Je suis tr´es honor´e par la pr´esence de Monsieur Omar FASSI FEHRI, secr´etaire perp´etuel `
a l’acad´emie Hassan II des Sciences et Techniques qui a accept´e de pr´esider le jury de ma th`ese, ´egalement tr`es honor´e par la pr´esence de Monsieur Mohamed HAMRI professeur `
a la Facult´e des Sciences de Rabat et Monsieur Abdellah AIT OUAHMAN Directeur
de l’Ecole Nationale des Sciences Appliqu´ees de Marrakech, qui ont accept´e d’ˆetre les rapporteurs de cette th`ese. Qu’ils trouvent ici mes plus vifs remerciements pour l’effort qu’ils ont fait pour lire mon manuscrit et l’int´erˆet qu’ils ont port´e `a mon travail. Ils ont ´egalement contribu´e par leurs nombreuses remarques et suggestions `a am´eliorer la qualit´e de ce m´emoire, et je leur en suis tr`es reconnaissant. Mes sinc`eres remerciements vont ´egalement `a Monsieur Mohamed ESSAAIDI, professeur `a la facult des Sciences de T´etouan, Monsieur Samir BENNANI, professeur `a l’Ecole Mohammedia d’Ing´enieurs `a Rabat et Monsieur Youssef FAKHRI, professeur assistant `a la Facult´e des Sciences de Kenitra, pour leur participation au jury de cette th`ese.
Mes remerciements vont aussi `a tous mes coll`egues dans les laboratoires LRIT. En
vi
AIT KAROUM, Rachid SAADANE et `a Monsieur Abdelilah JILBAB, pour leurs aides
et conseils.
Je remercie chaleureusement mes parents mes fr`eres, ma femme Saida et mes tr`es chers amis pour leur soutien et pour leurs f´elicitations lors de mes r´eussites...
Enfin merci `a ceux que je n’ai pu citer mais qui ont toutes mes amiti´es et mes remer-ciements.
1 Introduction . . . 1
1.1 Wireless Sensor Networks . . . 2
1.1.1 Sensor networks characteristics . . . 3
1.1.2 Wireless Sensor networks applications . . . 9
1.2 Problem Statement . . . 14
1.3 Performance Evaluation . . . 15
1.4 Thesis Outline . . . 15
2 Wireless Sensor Networks Routing Protocols . . . 17
2.1 Introduction . . . 18
2.2 Routing protocols for wireless sensor networks . . . 19
2.2.1 Flat routing protocols . . . 20
2.2.2 Location-based routing protocols . . . 33
2.2.3 Hierarchial routing protocols . . . 36
2.2.4 Routing protocols based on protocol operation . . . 48
2.3 Conclusion . . . 53
3 Flat Networks Routing Algorithms Contribution . . . 55
3.1 Introduction . . . 56
3.2 Lifetime Maximizing Algorithm for Wireless Sensor Networks . . . 58
3.3 A Decentralized Lifetime Maximizing Algorithm for Wireless Sensor Net-works . . . 60
viii
3.4.1 Simulation setting . . . 61
3.4.2 Simulation results . . . 61
3.5 Conclusion . . . 66
4 Hierarchical Routing Algorithms Contributions . . . 69
4.1 Introduction . . . 70
4.2 Energy Aware Cluster selecting algorithm for Routing in WSNs . . . 71
4.2.1 Motivation . . . 74
4.2.2 Set-up phase . . . 76
4.2.3 Steady-State Phase . . . 77
4.2.4 Simulations and Results . . . 77
4.3 Cluster-head selection based node to sink remoteness . . . 81
4.3.1 Motivation . . . 82
4.3.2 Clusters heads selection . . . 82
4.3.3 Simulation and Results . . . 87
4.4 Reducing Cluster Control Energy technique for heterogeneous networks . . 92
4.4.1 Set-up phase . . . 96
4.4.2 Steady-State Phase . . . 97
4.4.3 Simulation and Results . . . 97
4.5 Conclusion . . . 103
5 Conclusion and future work . . . 105
A Consumption Energy Model . . . 109
B List of Publications . . . 113
1.1 Typical node architecture . . . 7
1.2 Examples of sensor nodes . . . 8
1.3 Typical network architecture . . . 8
1.4 WSN applications taxonomy . . . 10
1.5 Some WSN applications . . . 10
2.1 Routing protocols taxonomy . . . 21
2.2 Flooding Implosion . . . 22
2.3 Flooding overlapping . . . 22
2.4 SPIN basic protocol operations . . . 24
2.5 Directed Diffusion protocol operations . . . 26
2.6 the leader node gets all the readings, calculates the average and if it is greater than a threshold sends it to the base station . . . 31
2.7 Virtual grid and active nodes in GAF . . . 34
2.8 Data flow in clustered network. . . 38
2.9 Level clustering in TEEN . . . 41
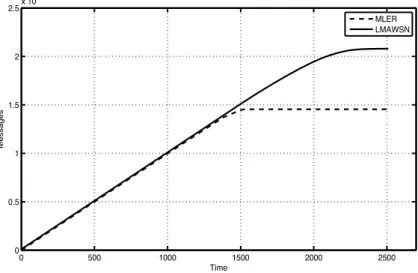
3.1 Relative Network lifetime Evolution vs Threshold . . . 59
3.2 Relative Network lifetime Evolution . . . 62
3.3 Number of nodes still alive over transmission time . . . 63
3.4 Total Data Packets transmitted . . . 63
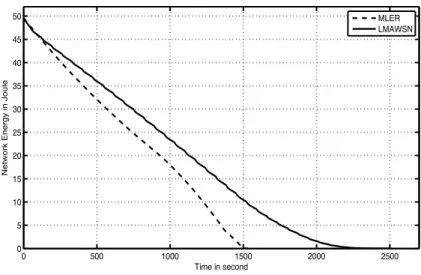
3.5 Total Network Remaining Energy . . . 64
x LIST OF FIGURES
3.7 Network remaining energy modelisation . . . 65
3.8 Network lifetime comparison . . . 66
3.9 Network transmission energy per round . . . 67
3.10 Data packets transmitted to the Base station . . . 67
4.1 Cluster-based mechanism in LEACH . . . 74
4.2 LEACH cluster formation flowchart . . . 74
4.3 The cycle of LEACH operations. . . 75
4.4 Selection of cluster-head for transmission to the base station. . . 75
4.5 Network Lifetime until the first node dies. . . 78
4.6 Number of nodes still alive by transmission rounds. . . 79
4.7 Network lifetime with no compression.. . . 79
4.8 Network Remaining Energy. . . 80
4.9 Energy per round. . . 81
4.10 Average number of nodes per cluster. . . 82
4.11 Cluster-heads comparison . . . 85
4.12 Number of clusters vs transmission rounds . . . 88
4.13 Lifetime of a network with 100 nodes. The base station at (50m,175m). . . 88
4.14 Lifetime of a network with 100 nodes. The base station at (50m,200m). . . 89
4.15 Lifetime of a network with different node density. . . 89
4.16 Lifetime of a network with different base station remoteness from the network. 91 4.17 Network transmission energy by round. . . 91
4.18 Protocol flowchart . . . 97
4.19 Total Network Energy for Clusters Forming in DEEC . . . 98
4.20 Relative Network lifetime . . . 100
4.21 Total Network Energy for Clusters Forming in CTRWSN . . . 100
4.22 Network lifetime . . . 101
4.23 Network Remaining Energy . . . 101
4.24 Network lifetime until the first node dies f = 0.2 and a varying from 0.5 to 5102 4.25 Network lifetime until the first node dies a = 3 and f varying from 0.1 to 0.9102 A.1 Radio energy dissipation model.. . . 109
ADC Analog to Digital Converter
ADV Advertisement message
APTEEN Adaptive periodic threshold-sensitive energy efficient
ASIC Application Specific Integrated Circuit
BFA Brute Force Algorithm
BS Base station
CADR Constrained Anisotropic Diffusion Routing
CDMA Code Division Multiple Access
CH Cluster head
CPU Central Processing Unit
CSMA Carrier Sense Multiple Access
CSMA/CA Carrier Sense Multiple Access With Collision Avoidance
DAC Digital to Analog Converter
DC-DC Direct Current to Direct Current Energy Converter
DEEAC Distributive Energy Efficient Adaptive Clustering Protocol
DEEC Distributed Energy Efficient Clustering algorithm for heterogeneous wireless sensor networks
DD Directed Diffusion
DirQ Directed Query Dissemination
DSR Dynamic Source Routing
EAD Energy-Aware Data-Centric Routing Algorithm
EAR Energy Aware Routing
xii LIST OF FIGURES
EEPROM Electrically Erasable Programmable Read-Only Memory
FDMA Frequency Division Multiple Access
FPGA Field Programmable Gate Array
GAF Geographic Adaptive Fidelity
GEAR Geographic and Energy Aware Routing
GPS Global Positioning Sustem
HEED Hybrid energy-efficient distributed clustering algorithm
IDSQ Information-driven sensor querying
IP Internet Protocol
LEACH Low energy adaptive clustering hierarchy
LELE Leader Election with Load balancing Energy in Wireless Sensor Network
MAC Meduim Access Control
MCU Microcontroller Unit
MMSPEED Multi-path and multi-speed routing protocol
PEGASIS Power-Efficient Gathering in Sensor Information Systems
QoS Quality of Service
RAM Random Access Memory
REQ Resquest message
SAR Sequential Assignment Routing
SEP Stable Election Protocol for clustered heterogeneous wireless sensor networks
SPEAR Sensor Protocol for Energy Aware Routing in Wireless Sensor Network
SPEED Stateless Protocol for End-to-End Delay
SPIN Sensor Protocols for Information via Negotiation
TDMA Time Division Multiple Access
TEEN Threshold-sensitive energy efficient
TTL time-to-live
1
I
NTRODUCTIONThis chapter gives the reader a background related to the field of wireless sensor networks. We start by defining what is a wireless sensor networks, after, we present the functions of the various building blocks of a sensor node and provide some node features. Finally, a wide scope of applications are described to illustrate how this technology is making its presence felt in everyday life. Based on the requirements posed by sensor network applications, we then highlight the main characteristics that should be present in any protocol designed for sensor networks.
In recent years, with the advent of further miniaturization of electronics, many wire-less networks have emerged. The development in these networks focuses in data rates enhancement and power consumption reduction. Because of wireless Internet access be-comes increasingly popular, higher data rates are solicited. So, either more bandwidth must be allocated, or advanced signal processing has to be used to increase the spectral efficiency. Power consumption has always been a relevant issue in wireless networks. In certain applications, this concern is important than the needs for high data rates. In fact, some emerging wireless networks are designed for low data rate applications. Conse-quently, they can use simple radios and aggressive power management to accomplish very low power consumption. Among emerging wireless networks, the wireless sensor network is yet another type where low power consumption is crucial than high data rates.
2 CHAPTER 1. INTRODUCTION
1.1
Wireless Sensor Networks
What is a Wireless Sensor Network? A wireless sensor network is a collection of sensor nodes organized into a cooperative network. A sensor is a small device which observes the environment of physical parameters such as temperature, pressure, relative humidity, sound, vibration, motion or polluants, at different locations [Romer, 2004, Haenselmann, 2006]. And, Wireless Sensor Networks (WSN) are highly distributed networks of wireless sensor nodes, deployed in large numbers to monitor the environment or system. Compared to other categories of wireless networks, WSN possess two principal characteristics: multi-hop transmission and constrained energy sources. First, since sensor nodes have limited transmission ranges and organize themselves in an ad hoc manner, which means that two wireless sensor nodes that can not reach each other directly transmit on other sensor nodes to relay data between them. In general, data packets from the source node have to traverse multiple hops before they reach the destination. Second, since sensors are usually small and inexpensive, they are usually, battery powered and are often deployed in a rough or hostile physical environment. Therefore, changing the batteries is a so difficult task, as some networks may consists of hundreds to thousands of physically distributed nodes, and in many case is even, impossible to node access to do this replacement. Consequently, these nodes have constrained energy sources, and any protocols to be deployed in sensor networks need to be aware of energy usage.
These two features have important implications to the fundamental performance limits of WSN. With respect to the performance of WSN, the data transmission capacity and the lifetime of the sensor networks are critical and influential toward the design of optimal deployment planning and data gathering techniques used such networks.
As cited above, the WSN can used multi-hop to gather data toward the base station. That involves similitude between WSNs and mobile ad hoc networks (MANETs). In fact, these networks are similar in some ways. However, the applications and technical require-ments for the two systems are significantly different in several respects [I.F. Akyildiz, 2002, C. S. Raghavendra, 2004, McDonald and Znati, 2000, G. H. Lynn, 2003, B. Krish-namachari, 2002, K. Romer, 2002, R. Shorey, 2006]:
• In WSN, data generated by each node, are to travel from multiple sources to a data recipient or sink rather than communication between a pair of nodes. This implies that in WSN, the communication is multi-point to point and in MANET this communication is point to point.
• In most applications, the sensor nodes themselves are static (even though the sensed phenomena may be); which implies that the dynamics in the two types of networks
are not similar. However, in recent development, sensor nodes are increasingly
allowed to move and change their location to monitor mobile events, which results in unpredictable and frequent topological changes.
• The data collected by multiple nodes are based on common phenomena. So, there existes a potentially degree of redundancy in the data being transmitted by the various sources in WSNs. Also, there is potentially some dependency on traffic event generation in WSNs, such that some typical random-access protocol models may be inadequate at the queueing-analysis level. In MANETs is not generally the case.
• A critical resource constraint in WSNs is energy; this is not generally the case in MANETs, because the MANETs devices that handled by users can be replaced or recharged relatively frequently. The scale of WSNs and the necessity for unattended operation for periods of weeks or months implies that energy resources have to be controlled very judiciously.
• A WSN consists of hundreds or thousands of devices using sensors to monitor condi-tions at different locacondi-tions. These devices collaborate among themselves to achieve a sensing network. So, the number of nodes in WSN can be very important than the nodes in a MANET.
1.1.1
Sensor networks characteristics
Figure 1.1 shows the basic diagram of wireless sensor node. These subsystems are con-trolled by the operating system, using drivers, protocols and algorithms. In a sensor node
4 CHAPTER 1. INTRODUCTION
there are four essential parts [V. Raghunathan, 2002]: processing subsystem; sensing subsystem; transceiver subsystem and, power subsystem.
• The processing system usually constitutes of a controller and a memory unit. The controller unit can either be a micro-controller unit (MCU), a field programmable gate array (FPGA) or an application specific integrated circuit (ASIC). The MCU together with its on-board RAM, Flash and/or EEPROM provide the sensor node the intelligence. It is responsible for control of the sensors, and execution of com-munication protocols and signal processing algorithms on the gathered sensor data. The use of software which is easily altered or replaced depending on the circum-stances makes the MCU a very flexible controller. The MCU also has the ability to assign to itself a number of operating states in which parts of the MCU. In gen-eral, four main processor states can be identified in a MCU: off, sleep, idle, and active. In sleep mode, the MCU and most internal peripherals are turned off, and can only be activated by an external event (interrupt). In idle mode, the MCU is still inactive, but other peripherals are active, for example, the internal clock or timer. In the active state, multiple substates may be defined based on clock speeds and voltages. Within the active states, the CPU and all peripherals are active. Moreover, MCU can use dynamic voltage scaling to alter the operating frequency to fit the application needs. However the flexibility that the MCU provides comes at a cost [C. Talarico, 2005, Nikolaidis and Laopoulos, 2002], with typical trade-offs towards energy-efficiency and performance loses. The use of an ASIC in which everything is constructed in haedware can provide a higher energy-efficiency and improved performance with a loss towards the ßexibility that the MCU provide. • The sensor subsystem constitutes of a number of sensors that collects data for further
processing by the micro-controller. It is the component that translates physical phenomena to electrical signals. There exists a variety of sensors that measure environmental parameters such as temperature, light intensity, sound, magnetic fields, image, etc. The sensors can be classified as either analog or digital devices and it depends on how its output is produced. An analog sensor must be connected
to ADC before the data can be processed, which is not the case for a digital sensor. • The communication subsystems responsibility is to provide the sensor node with communication capabilities, in such a way that the sensor nodes are able to com-municate with other sensor nodes in its proximity. The communication medium for the sensor node varies and depends on the actual application. In some cases wired communication can be applied, but its applications are limited. A much more interesting technique to use in this subsystem is a wireless communication component. The wireless communication medium used for sensor networks includes radio frequency, optical and acoustic (e.g. ultrasound) techniques [M. A. M. Vieira, 2003]. The most common choice, when constructing a sensor node today, is to use a radio frequency (RF) transceiver. This is due to the fact that it fits the require-ments of most wireless sensor network applications. It consists of a short range radio which usually has a single channel, a low data rate and operates at unlicensed bands of 868 − 870M Hz (in Europe), 902 − 928M Hz (in Americas) or near 2.4GHz (global). There are several factors that affect the power consumption characteris-tics of a radio, including the type of modulation scheme used, data rate, transmit power (determined by the transmission distance) and the operational duty cycle. For the energy consumption, four different states need to be distinguished: Trans-mit, Receive, Idle and Standby modes. An important observation in the case of most radios is that, operating in Idle mode results in significantly high power con-sumption, almost equal to the power consumed in the Receive mode [van Hoesel, 2007]. Thus, it is important to completely shut down the radio rather than set it in the Id le mode when it is not transmitting or receiving due to the high power con-sumed. Another influencing factor is that, as the radio’s operating mode changes, the transient activity in the radio electronics causes a significant amount of power dissipation. For example, when the radio switches from standby mode to Transmit mode to send a packet, a significant amount of power is consumed for starting up the transmitter itself [A. Wang, 2001]. Since the radio transceiver must be in sleep mode to achieve energy effeciency, when its not used, a wake-up mechanism will be integrated to switch ON the radio when the node has to receive. The idea, with a
6 CHAPTER 1. INTRODUCTION
wake-up radio[Gu and Stankovic., 2005, Jr. da Silva, 2001, Miller and Vaidya., 2004, J. M. Rabaey, 2000, L. Zhong, 2001], is to have a specialised circuit that detects when a packet is inbound and notifies the appropriate component which in turn schedules the activation of the main transceiver so it is able to receive the incoming data. The goal with such a wake-up receiver is to have very low power consumption, preferably less than 1µW , and to be able to distinguish the destination address, so that the main receiver is only activated for packets that are addressed to this sensor node. Even without the use of address recognition this approach lowers the power consumed by the transceiver enormously. So far, constructing a wake-up radio that are able to distinguish the destination address has not been achieved.
• The power-supply subsystem provides power to the other components of the sensor node and there exist a number of different methods in which this can be accom-plished. These methods can be classified into the following categorises[A. Kansal, 2003]: power distribution; energy reservoirs; and power scavenging. Energy reser-voirs: In this case, the energy is stored in some type of container and as energy is consumed the available energy is decreased. The most commonly used of these techniques are the battery, which is the usual way of powering a sensor node today. The authors of [Holger Karl, 2005] gave the energy density for some batteries, these values are illustrated in Table 1.1.
Battery type Energy density
Lithium Battery 2880J/cm3
Rechargeable Lithium Battery 1080J/cm3
Table 1.1: Battery energy density.
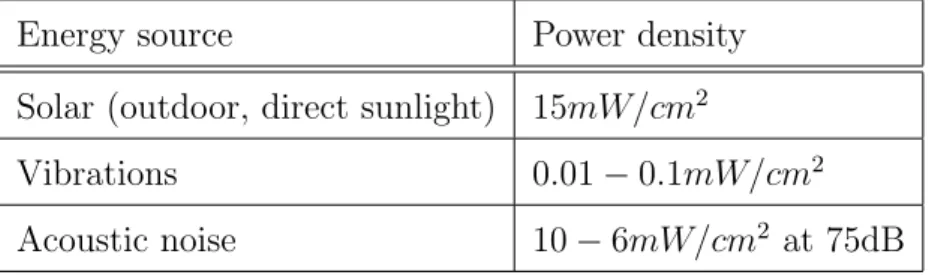
Power scavenging devices can be used to restore energy into rechargeable batteries (See table 1.2 taken from [Holger Karl, 2005]) . However, currently these techniques are an issue of research in order to fit in sensor nodes.
Thus, the most commonly used technique is the battery, which is the usual way of powering a sensor node today. DC-DC converter and voltage regulator are circuits
Energy source Power density
Solar (outdoor, direct sunlight) 15mW/cm2
Vibrations 0.01 − 0.1mW/cm2
Acoustic noise 10 − 6mW/cm2 at 75dB
Table 1.2: Sample Scavenging Power Density. that can provide a constant voltage to the sensor node.
Since, battery technologies advance much more slowly than semiconductor technolo-gies For example, the Li-ion battery energy density increases only 50% from 1995 to 2005 (280 watthours per liter in 1995 to 580 Whr/l in 2005) Conner [2005] . While in the same period of time, the number of transistors of Intel processors doubles every 24 months [Hiremane]. These facts make the need to develop highly efficient communication and data management protocols for WSNs.
Also, additional components may be included depending on the specific application. As supplementary components we can cite a location finding system to determine their po-sition, a mobilizer to change their location or configuration (e.g., antenna’s orientation), and so on. However, as the latter components are optional, and only occasionally used, rarely they are considered in the literature studies.
Figure 1.1: Typical node architecture
In wireless sensor node, the much lot of energy is consumed in the radio communication. A comparison of computation and communication costs has shown that transmitting one bit over a distance of 100 m consumes approximately the same energy as executing
8 CHAPTER 1. INTRODUCTION
3000 instructions [G. Pottie, 2000]. Then, to reduce energy consumption the number of communications should be minimized, even at the cost of increasing data processing. The figure 1.2 gives examples of WSN nodes pictures. As depicted, the size of the nodes is very small.
Figure 1.2: Examples of sensor nodes
Figure 1.3: Typical network architecture
To give reader an overview of sensor node hardware, Table 1.3 gives some marcket nodes features:
A wireless sensor network is a collection of nodes organized into a cooperative network. These sensor nodes are able to communicate with other neighbor nodes using wireless com-munication technique and to collect data from a phenomenon or a set of phenomenons. Because of phenomenon is the entity of interest to the end-user, the collected data are
Sensor node platform Microcontroller Transceiver
CPU Clock freq (MHz) RAM (kB) Program memory (kB) Type Freq (MHz) Max data rate (kbps)
weC[con, a] Atmel AT90S8535 4 0.5 8 RFM TR1000 916.5 10
Rene mote [con, a] Atmel AT90S8535 4 0.5 8 RFM TR1000 916.5 10
Rene2 mote[con, a] Atmel ATmega163 4 1 16 RFM TR1000 916.5 10
MIT µAMPS [R. Min, 2000] Intel StrongARM SA1100 206 16384 512 National Semiconductor LMX3162 2400 1024
Crossbow MICA [con, b] Atmel ATmega128L 4 4 128 RFM TR1000 433, 915 40
Crossbow MICA2DOT [con, b] Atmel ATmega128L 4 4 128 Chipcon CC1000 315, 433, 915 38.4
Crossbow MICA2 [con, b] Atmel ATmega128L 7.37 4 128 Chipcon CC1000 315, 433, 915 38.4
Crossbow MICAz [con, b] Atmel ATmega128L 4 4 128 Chipcon CC1000 2400 250
EYES (Nedap) [L. F. W. van Hoesel, 2003] TI MP430F149 2 8 60 RFM TR1001 868.35 57.6
EYES (Infinion) [V. Handziski, 2004] TI MP430F149 2 8 60 Infinion TDA 5250 868-870 64
BTnode rev3 [con, c] Atmel ATmega128L 7.37 244 128 Chipcon CC1000 433, 915 38.4
Moteiv Tmote Sky [con, d] TI MP430F149 8 10 48 Chipcon CC2420 2400 250
Ambient µ Node [con, e] TI MP430 4.6 10 48 Nordic nRF9E5 868, 915 50
Ambient SmartTag [con, e] 8051 16 - 4 Nordic nRF9E5 868, 915 50
Table 1.3: Nodes characteristics.
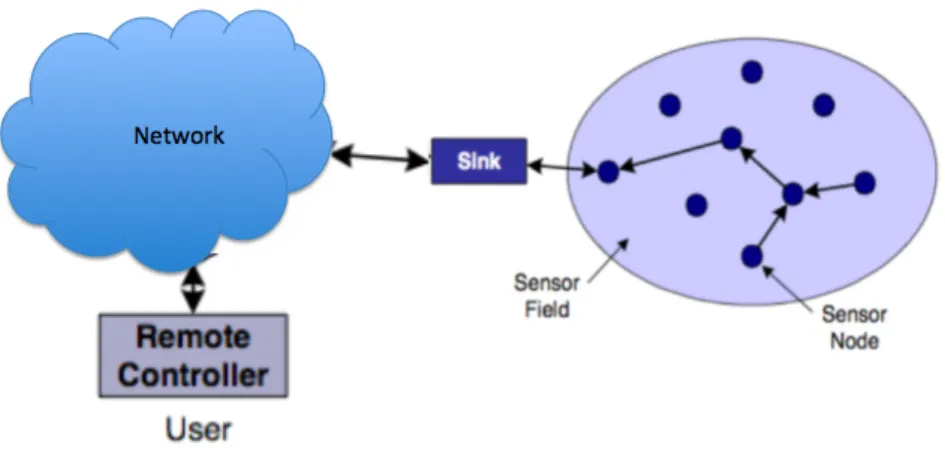
routed using other sensor nodes as routers to a sink node. The sink (or base station) is a collector that sends end-user interests to the sensor network and collects data related to these end-user interests from the network. It is normally a resourceful node having unconstrained computational capabilities and energy supply. There can be single or mul-tiple base stations in a network. Practically, the use of mulmul-tiple base stations decreases network delay and performs better using robust data gathering. Base station in a network can also be stationary or dynamic. The dynamic base stations can influence the routing protocols greatly because of its changing position which will be not clear to all the nodes in a network. The data of interest for a particular end-user is either available directly to the end-user or it must be forwarded through a network before it is available to the end-user. This is illustrated in Figure 1.3.
Depending on the sensor network application, the data delivery model to the sink can be continuous, event-driven, query-driven and hybrid [R. Min, 2001]. In the continuous delivery model, each sensor sends data periodically. In event-driven and query- driven models, the transmission of data is triggered when an event occurs or a query is generated by the sink. Some networks apply a hybrid model using a combination of continuous, event- driven and query-driven data delivery. The routing protocol is highly influenced by the data delivery model, especially with regard to the minimization of energy consumption and route stability.
10 CHAPTER 1. INTRODUCTION
Figure 1.4: WSN applications taxonomy
1.1.2
Wireless Sensor networks applications
Actually, the WSNs are low-cost, easy deployment and, self-configuring. This make them desirable for various application classes as compare to other networks [E. Biagioni, 2002, 2003, A. Cerpa, 2001, A. Mainwaring, 2002, D. C. Steere, 2000, H. Wang, 2003, H. Wang, I. F.Akyidiz, 2002, Salem and Mohamed, 2006]. As main application classes of WSN, we can cite data gathering, event detection, object tracking and sink-initiated querying (see Figure 1.5 redrawn from [K. Sohraby, 2007] and Figure 1.4 redrawn from [J. Yick, 2008]). In the following, we give a brief list of applications areas where WSNs are or can be deployed:
• Environmental monitoring: Remote sensing has usually used to perform large-scale environmental monitoring. Remote sensing techniques have been traditionally con-signed to the implementation of airborne or space-borne configurations, e.g. using satellites. Although, satellites do not allow continuous monitoring of a particular location. Since the quality of images taken by satellites are weather conditions dependent, WSNs can be used to complement remote sensing data from satellites as they can be used to observe environments at high spatio-temporal resolutions [Thomas C. Henderson, 2004].
• Precision agriculture: WSNs may be employed to facilitate the tasks of the farmer by continuously monitoring parameters such as soil temperature, moisture and salin-ity(e.g. Irrigation Management: Soil Moisture to monitor water delivery to spe-cific Irrigation blocks, soil moisture monitoring for Stress irrigation to improve crop quality, remote Irrigation Control (valve actuation, pump control), monitoring Irri-gation line flow/pressure water delivery to correct destination). This would allow the farmer to act immediately to conditions that are unfavorable to the growth of crops and thus ensure a higher gain. WSN applications in agriculture are not just limited to growing crops. Also, they are used to monitor animals. Currently sows are tagged to help farmers that need to detect when a sow enters its heat period. Because of it is known that a correlation exists between the movement of sows and its heat period, using a sensor nodes with built-in accelerometers allow farmers to
12 CHAPTER 1. INTRODUCTION
track the sows remotely and would also help identify when a sow is in heat.
• Industrial Automation: In addition to being expensive, using wires can be constrain-ing, especially when system moving parts are involved. Then the use of wireless sensors allows a rapid installation to sense equipment and allows observe locations that would not be accessible if cables were attached. Erlier, the use of wired sen-sors was too difficult to be implemented in a production line environment. The use of wireless sensors in these applications is enabling, allowing a measurement to be made that was not previously practical. Other applications include energy control systems, security, wind turbine health monitoring.
• Logistics and transport: With a rapid increase in the number of vehicles on the road worldwide, intelligent road management systems are seen as the key to managing transport infrastructure efficiently. Some researchers describe a WSN that uses magnetometers to detect the presence of vehicles, speed and also detect the vehicle type. The information provided by the traffic monitoring system can be used to optimise traffic light settings at urban intersections. Road users can also use this information to better arrange their activities and adapt their routes.
• Medicine and health care: The WSN could provide interfaces for disabled, integrated patient monitoring. It can observe and detect aged people’s behavior, e.g., when a patient has fallen. These small sensor nodes allow patients a greater freedom of movement and allow doctors to identify predefined symptoms earlier on[Young Han Nam, 1998]. The small installed sensor can also enable tracking and monitoring of doctors and patients inside a hospital. Each patient has small and lightweight sensor nodes attached to them, which may be detecting the heart rate and blood pressure. Doctors may also carry a sensor node, which allows other doctors to locate them within the hospital. The work presented in [Geoffrey G. Messier, 2007] points the use of wireless nodes for patient surveillances and gives a traffic models for the data packets genetated by WSN node monitoring body temperature and electrocardiogram (ECG) data.
tolerance characteristics of sensor networks make them a very promising sensing technique for military applications. Military sensor networks could be used to detect and gain as much information as possible about enemy movements, explosions, and other phenomena of interest, such as battlefield surveillance, nuclear, biological and chemical attack detection and reconnaissance. As an example, sensors help to locate the source of incoming small arms fire so that counterattacks can be launched against snipers quickly and precisely.
• Maintenance: Sensors embedded into machines and structures enable condition-based maintenance of these assets [A. Tiwari, 2004]. Typically, structures or ma-chines are inspected at constant time intervals, and components may be repaired or replaced based on their time duration in service, rather than on their working conditions. This method is expensive if the components are in good working or-der, and in some cases, scheduled maintenance will not protect the asset if it was damaged in between the inspection intervals. Wireless sensing will allow assets to be inspected when the sensors indicate that there may be a problem, reducing the cost of maintenance and preventing catastrophic failure in the event that damage is detected. Additionally, the use of wireless reduces the initial deployment costs, as the cost of installing long cable runs is often prohibitive.
• Disaster prediction and management : The ability to predict upcoming disasters could have a major impact on saving lives. Such predictions could help with the continuous monitoring capability of WSNs. For example, sensor nodes equipped with seismoacoustic sensors can be deployed to monitor the behaviour of active volcanoes. The data collected from such networks could be used to predict the eruption moments. WSNs are also being used to complement deep-water tsunami detection mark to help improve the detection of tsunamis. In addition to predicting disasters, WSNs can also be used in the management of disasters after they occur. Some researchers intend to embed sensor nodes into the structures of buildings. These nodes stay dormant until a breakdown is detected. They then collaborate to help create a view of the collapsed interior identifying the structurally strong
14 CHAPTER 1. INTRODUCTION
support walls and cavities. The WSN is also able to locate survivors using heart pulsation sensors. The collected information is then propagated to the rescue team using energy-efficient routing algorithms.
• Home applications: The tiny sensor nodes can be embedded into furniture and appliances, such as vacuum cleaners, microwave ovens and refrigerators. They are able to communicate with each other and the room server to learn about the services they offer. These room servers and sensor nodes can be integrated with existing embedded devices to become self-organizing, self-regulated and adaptive systems to form a smart environment.
1.2
Problem Statement
Since many of the proposed WSN application systems involve large networks, it is essential to provide routing infrastructures that concurrently offer small routing state, small rout-ing stretch, and robustness [R. Fonseca, 2005, Y.-J. Kim, 2005, Y. Mao, 2007]. Small state is critical for scalability and efficiency. With only a few kilobytes of memory in typical sensor node, reducing the routing state will enable supporting large networks. In addi-tion, with smaller routing state, a lower maintenance traffic is implied, as these two are usually correlated. Since WSNs knowledge topology and connectivity changes due to node failures and environmental impact, robustness entails handling such changes efficiently. More specifically, to minimize resource consumption and interruption of higher-level sys-tem components, the routing infrastructure must handle the changes in the network with minimal traffic and latency. The critical importance of any wireless sensing node is to min-imize its consumed power. Therfore, all network stack protocols must be energy efficient especially the communications ones, because it is the data transmission that consumes the most lot of energy [Townsend and Arms]. Because of the node radio subsystem requires the considerable amount of power, it is suitable to send data over the radio channel only when required. The best way, in terme of energy consumption, must be selected for data travel. Additionally, it is important to minimize the power consumed by the sensor itself. Therefore, the hardware should be designed to allow the processing subsystem to
effi-ciently control power to the radio, sensor, and sensor signal conditioner. With Wireless sensor networks constraint, the purpose of this research effort is to design, implement, and test a new wireless sensor network (WSN) routing protocol which coordinates sensor node transmissions to extend network service durations and conserve energy in memory-and power- constrained devices. In this work, two kinds of problems are addressed, the path selection in flat networks to balance the energy load between the network nodes and the clustering algorithms in hierchical networks to extend the network lifetime.
Through this thesis, we propose some contributions for routing algorithms in wireless sensor networks. As given above, the metric used in this work, is the network lifetime. Therefore, the performed algorithm is that giving the extended lifetime.
1.3
Performance Evaluation
The primary metric for evaluating the performance of a sensor network is lifetime, which means the network service duration from deployment until the network energy nodes ex-haustion, even in some applications, the network lifetime is defined until the first node run out its residual energy. The principal limiting factor for the WSN lifetime the energy supply. Therefore, each node should be designed to manage its local energy as a means to enhance total network lifetime. In many applications it is not the average node lifetime that is critical, but rather the minimum node lifetime. For wireless security application, every node must last for multiple years. And a single node failure would make a vulner-able area in the security systems. One tell that nodes would be energy scavenged. But, this energy is low, and yet, the nodes would be enegy constrained. Indeed, the enegy consumed for transmitting a data packet should be reduced. Obviously, the technique that requires the minimal transmission energy will extend the network lifetime. So, the transmission energy may be used to assess the routing protocols. Moreover, any proposed communication technique should be decentralized to deal with network auto-configuration and to allow scalability. So, performance evaluation takes in account the technique be-havior; the best technique is that completely decentralized. Finally, the communication protocols must be adaptable to the network topology, in order to facilitate the nodes
16 CHAPTER 1. INTRODUCTION
deployement, which means that a communication protocol that implies a specific nodes deployement is expensive.
1.4
Thesis Outline
The thesis is organized as follows:
Chapter 2: LITERATURE REVIEW
This chapter reviews the state of the art of WSN routing algorithms in the literature and shows performance evaluation technics.
Chapter 3: Flat network routing proposition
In this chapter we propose an algorithm for routing in WSN that permits to extend network lifetime. This algorithm considers the network as flat, where all network nodes have the same role.
Chapter 4: Hierarchical network routing propositions
Chapter 4 presents some contributions for routing in WSN based on network clustering.
Chapter 5: Conclusions and future works
2
W
IRELESSS
ENSORN
ETWORKSR
OUTINGP
ROTOCOLSSommaire
2.1 Introduction . . . 18 2.2 Routing protocols for wireless sensor networks . . . 19 2.2.1 Flat routing protocols . . . 20 2.2.2 Location-based routing protocols . . . 33 2.2.3 Hierarchial routing protocols . . . 36 2.2.4 Routing protocols based on protocol operation . . . 48 2.3 Conclusion . . . 53
18 CHAPTER 2. WIRELESS SENSOR NETWORKS ROUTING PROTOCOLS
2.1
Introduction
A wireless sensor network is a sensor network that uses wireless radio as its physical layer. This network enables users to remotely access information and services electron-ically. They are extremely versatile and can be deployed to support a wide variety of applications in many different situations, whether they are composed of stationary or mobile sensor nodes. These sensors deployment depends on the nature of the application. For example, in environmental monitoring and surveillance applications, sensor nodes are typically deployed in an ad hoc fashion so as to cover the specific area to be monitored. In health care-related applications, smart wearable wireless devices and biologically com-patible sensors can be attached to or implanted strategically within the human body to monitor vital signs of the patient under surveillance. Once deployed, sensor nodes self-organize into an autonomous wireless ad hoc network, which requires very little or no maintenance. Sensor nodes then collaborate to carry out the tasks of the application for which they are deployed. Each sensor has wireless communication capability and suffi-cient intelligence for signal processing and networking of data. However, sensor nodes are constrained in energy supply and bandwidth. Such constraints, combined with a typical deployment of a large number of sensor nodes have posed many challenges to the design and management of sensor networks. These challenges necessitate energy-awareness at all layers of the networking protocol stack. And especially at the network layer, the main aim is to find methods for energy efficient route setup and reliable relaying of data from the sensor nodes to the sink so that the lifetime of the network is maximized. The character-istics of the environment within which sensor nodes typically operate, coupled with severe resource and energy limitation, make the routing problem very challenging. The objec-tive of this chapter is to survey the state-of-the-art routing protocols for WSNs. Thus, a taxonomy of the basic routing strategies used to strike a balance between responsiveness and energy efficiency, is provided. The principle of each routing class is given, and some related works are exposed.
2.2
Routing protocols for wireless sensor networks
Although, wireless sensor networks and ad hoc networks have some similitudes, WSNs have theirs own unique characteristics which create new challenges for the design of rout-ing protocols for these networks. Since, sensors have very limited transmission power, computational capacities and most of all, stored energy. The operating and networking protocol must be much simpler as compared to other ad hoc networks. This simplicity may also break with conventional layering rules for networking protocols, since abstractions typically cost time and space. Also, due to the large diversity of application scenarios for WSNs, it is impossible that there will be a one-thing-fits-all solution for these very different possibilities. So, the application requirements involve the specific design of a sensor network routing protocol. In fact, the data traffic in WSNs has significant redun-dancy since data is probably collected by many sensors based on a common phenomenon. This redundancy needs to be exploited by the routing protocols to improve energy and bandwidth utilization.
Among possible classifications, routing protocols can be grouped into three categories, namely, proactive, reactive, and hybrid protocols depending on how the source finds a route to the destination. Proactive routing protocols offer update routes to any destination in the network at any given time by frequently updating the routing tables. The main advantage of this approach is the minimal delay an application experiences when it wants to send information across the network. Keeping track of all the routes through the network, on the other hand, introduces a large protocol overhead. The routing table updates are usually periodic but can be extended by event-driven updates to quickly react to network changes.
Reactive routing means that routing information is not gathered in advance, but first when requested by an application. This saves control overhead but introduces the need for a discovery phase each time an application needs to send data over the network and increases the communication delay. In the route discovery phase, the network is partially or entirely flooded with route request messages to find the shortest path to the destination. In reactive routing, the scalability is better because routing information is only exchanged
20 CHAPTER 2. WIRELESS SENSOR NETWORKS ROUTING PROTOCOLS
when needed and a node can be certain to use the most recent routing information, which leads to a higher transmission success than with proactive routing where routes might be outdated. Flooding an entire WNS means considerable communication efforts and the flooding should be restricted to a particular area of interest to minimize the energy loss.
The size of a WSN, its network dynamics and energy constraints are factors in favor of reactive routing protocols using local information. This allows the network to react quickly to local changes or bursty traffic and does not require the global transmission of routing information. On the other hand, when information has to be transmitted quickly from nodes to the sink (e.g. when an alarm was triggered), a predetermined path from source to sink reduces the delay considerably.
When sensor nodes are static, it is preferable to have table driven routing protocols rather than using reactive protocols. A significant amount of energy is used in route discovery and setup of reactive protocols.
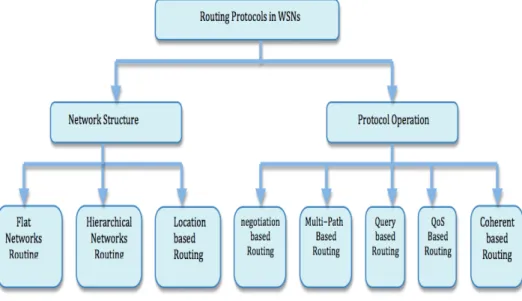
Al-karaki and Kamal [Al-karaki and Kamal, 2004] proposed some classifications of WSN routing protocols. Depending on the network structure, routing protocols in WSNs can be also, divided into three kinds: flat-based routing, hierarchical-based routing, and location-based routing. In flat-location-based routing, all nodes are typically assigned equal roles or func-tionality. However, in hierarchical-based routing, nodes will play different roles in the network. And in location-based routing, sensor positions are used to route data in the network. In some cases, certain system parameters can be controlled in order to adapt to the current network conditions and available energy levels. In these situations, the rout-ing protocol is considered adaptive. Furthermore, these protocols can be classified into multipath-based, query-based, negotiation-based, QoS-based, or coherent-based routing techniques depending on the protocol operation. In order to streamline this survey, we use a classification according to the network structure and protocol operation (routing criteria). The classification is shown in Figure 2.1 redrawn from [Al-karaki and Kamal, 2004].
Figure 2.1: Routing protocols taxonomy
2.2.1
Flat routing protocols
In flat-based routing protocols all sensor nodes collaborate with the same role in the rout-ing procedures. Since the number of sensor nodes is huge therefore it is not possible to assign a individual identifier to each and every node. This leads to data-centric rout-ing approach in which the base station sends query to a group of particular nodes in a region and waits for response. So, in data-centric routing paradigm, data is important than the individual nodes identities. Information is referred by using attributes of the phenomenon. For example, the query ”Give me the temperature in the region R” needs to be disseminated to sensor nodes of a region R. At the same time, data coming from the region R have to be delivered to the user that sent the query. A flat network architecture presents several advantages; it has minimal overhead to maintain the infrastructure and the abilities for the discovery of multiple routes between communicating nodes to achieve fault tolerance. In the following, we summarize the most known flat routing protocols and highlight their advantages and performance issues.
22 CHAPTER 2. WIRELESS SENSOR NETWORKS ROUTING PROTOCOLS
Figure 2.2: Flooding Implosion
Sensor Protocols for Information via Negotiation (SPIN)
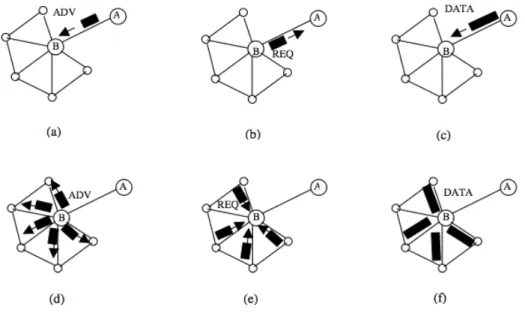
Simple protocols such as flooding and gossiping are frequently proposed to achieve in-formation dissemination in WSNs. Flooding and Gossiping [Hedetniemi and Liestman, 1988] are among the conventional routing protcols. Flooding requires that each node transmits a copy of its data packet to all its neighbors until the information reaches all nodes in the network. On the other hand, gossiping uses random transmission to reduce the number of duplicate data packets. It requires only that a node receiving a data packet retransmits it to a randomly chosen neighbor. The simplicity of fooding and gossiping is benefic since both protocols use simple forwarding basis and do not need topology maintenance. However, the performance of these algorithms in terms of packet delivery delay and resource utilization, decreases quickly with the size of the network and the traffic load. The performance fall is caused by traffic implosion as depicted in Figure 2.2 and geographical overlapping (Figure 2.3 redrawn from [K. Sohraby, 2007]). Implosion is due to multiple duplication of the same data being transmitted to the same sensor node by several neighboring nodes. On the other hand, geographical overlapping makes nodes that cover the same geographical area to spread, needlessly, identical data infor-mation items to the network sensor nodes. Moreover, simple protocols such as fooding and gossiping do not change their behavior to adjust communication and computation to the current state of their energy resource. This deprivation of resource awareness and adaptation may decrease significantly the network lifetime, since highly active nodes may rapidly drain their energy resources. In order to improve the classic flooding and gos-siping, Sensor Protocols for Information via Negotiation (SPIN) is proposed. SPIN is a data-centric negotiation-based family of information dissemination protocols for WSNs [W. Heinzelman, 1999, J. Kulik, 2002]. It is a family of adaptive protocols, which effi-ciently disseminate information in a WSN. The principles of this family of protocols are the use of data negotiation and resource-adaptive algorithms. Nodes running SPIN assign a high-level name to describe their collected data, called data, and perform meta-data negotiations before any meta-data is transmitted between network nodes . A receiver that indicates interest in the data content can send a request to get the advertised data. This scheme of negotiation guarantees that data are sent only to nodes that are interested in
24 CHAPTER 2. WIRELESS SENSOR NETWORKS ROUTING PROTOCOLS
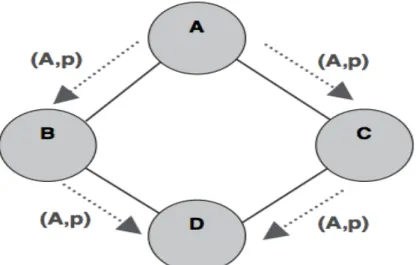
Figure 2.4: SPIN basic protocol operations
it, consequently, avoiding traffic implosion and reducing considerably the transmission of redundant data over the network. Besides, the use of meta data descriptors excludes the possibility of overlap, since nodes can limit their requests to express only the data that they are interested in getting. These negotiations assure that redundant data is not transmitted throughout the network. SPIN uses three messages to exchange data between nodes: The ADV message that allows a sensor to advertise a particular meta-data, the REQ message to request the needed data and the DATA message that transfert the actual data. Figure 2.4., redrawn from [W. Heinzelman, 1999], summarizes the function of the SPIN protocol. In this figure, node A will transmit a data packet, it starts by advertising its data to node B. Node B responds by sending a request to node A. After receiving the requested data, node B then sends out advertisements to its neighbors, who in turn send requests back to B. SPIN presents some advantages. First, any topological changes are localized since each node needs to know only its single-hop neighbors. Second, it highly reduces energy consumption compared to flooding. Three, it also achieves high data dis-semination rates. However, SPIN data advertisement mechanism cannot guarantee the delivery of data. For instance, if the nodes that are interested in the data are far away from the source node and the nodes between source and destination are not interested in
that data, such data will not be delivered to the destination at all. Consecontly, SPIN is not a good alternative for applications such as intrusion detection, which require reliable periodic delivery of data packets.
Directed Diffusion
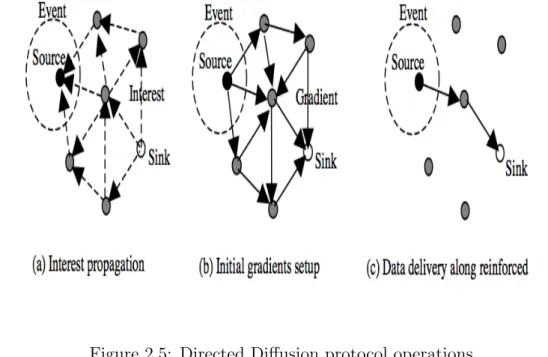
Directed Diffusion[C. Intanagonwiwat, 2000, et al., 1999] is an important improvement in the data-centric routing protocols for sensor networks. The goal behind Directed Diffusion is to diffuse data over sensor nodes by naming it. The main reason behind using such a scheme is to reduce unnecessary operations of network layer routing in order to save energy. To understand the naming mecanism, in the following, we give an example of task naming (interest):
type = wheeled vehicle // detect vehicle location interval = 20 ms // send events every 20 ms duration = 10 seconds // for the next 10 seconds
rect = [-100, 100, 200, 400] // from sensors within rectangle
In this example, the sink is interested in receiving the vehicle location in the region rec every interval for the next duration. Directed Diffusion combines data coming from different source and en-route them by eliminating redundancy, minimizing the number of data transmission; thus maximizing network lifetime. The base station requests data by broadcasting an interest message which contains a description of a sensing task. This interest message propagates through the network hop-by-hop and each node also broadcast interest message to its neighbor. As interest message propagates throughout the network, gradients are setup by every node within the network. The gradient is a reply link to a neighbor from which the interest was received. This process continues until gradients are setup from source node to base station. Consequently, by using interest and gradients, paths are created between sink and sources. Several paths can be established, and loops can exist. Loops are not checked at this stage but removed at later stage. After this path of information flow are formed and then best path are reinforced to prevent further flooding according to a local rule. Data aggregation took place on the way of different paths from different sources to base station or sink. To provide reliability, the base station periodically
26 CHAPTER 2. WIRELESS SENSOR NETWORKS ROUTING PROTOCOLS
Figure 2.5: Directed Diffusion protocol operations
refresh and resend the interest message as soon as it start to receives data from sources. Figure 2.5, redrawn from[C. Intanagonwiwat, 2000], summarizes the Directed Diffusion protocol. To enhance reliability, path repairs are also possible in Directed Diffusion. Thus, when a path between a source and the sink falls, an alternative path should be selected. To do that, Directed Diffusion fundamentally regenerates reinforcement by exploring among other paths, which are sending data in lower rates. The authors of [Ganesan et al., 2002] proposed the use of multiple paths in advance so that in case of a failure of a path, one of the alternative paths is chosen without any cost for searching for another one. There is extra overhead for keeping these substitute paths alive by using low data rate, which will clearly use extra energy but more energy can be conserved when a path fails and a new path should be chosen. Directed Diffusion and SPIN differ in terms of the on demand data querying mechanism it has. In Directed Diffusion, the base station queries the sensor nodes if a specific data is available, by flooding some tasks. In SPIN protocols, sensors announce the availability of data allowing interested nodes to query that data. Directed Diffusion has numerous advantages. Because of it is data centric, all transmission is neighbor-to-neighbor with no requirement for a node addressing mechanism. Each node can do data aggregation and caching, in addition to do environment sensing. Data caching
is an important advantage in terms of energy efficiency and delay. Besides, Direct Diffusion is highly energy efficient because it is on demand and there is no need for maintaining global network topology knowledge. On the other hand, Directed Diffusion cannot be appropriate to all sensor network applications as it is based on a query-driven data delivery model. The applications that require continuous or periodic data delivery to the sink will not work efficiently with a query-driven on demand data model. Consequently, Directed Diffusion is not a good alternative as a routing protocol for the applications such as environmental monitoring. Moreover, the naming schemes used in Directed Diffusion are application based and each time should be defined a priori. In addition, the matching process for data and queries might request some extra overhead at the sensors.
Rumor routing
Rumor routing[Braginsky and Estrin, 2002] is another version of Directed Diffusion and is mainly designed for applications where geographic routing is not feasible. In general, Directed Diffusion uses flooding to introduce the query to the whole network when there is no geographic rule to diffuse tasks. However, in some situations, there is only a little amount of data that requested from the nodes and so, the use of flooding is unneeded. An alternative method is to flood the events only if the number of events is small and the number of queries is important. The aim is to route the queries to the nodes that have detected a particular event rather than flooding the whole network to get information about the occurring events. The Rumor Routing algorithm uses long-lived data packets, called agents to flood events through the network. So, when a node observes an event, it adds this event to its local table that called events table, and creates an agent. Agents traverse the network in order to spread information about local events to distant nodes. When a node creates a query for an event, the nodes knowing the route to access to that event, may respond to the query by examining its event table. Therefore, there is no require to flood the entire network, which diminishes the energy communication cost. On the other hand, Rumor Routing conserves only one path between source and destination as against to Directed Diffusion where data can be transmitted through multiple paths at low rates. However, Rumor Routing operates well only when the number of events is small.
28 CHAPTER 2. WIRELESS SENSOR NETWORKS ROUTING PROTOCOLS
For a large number of events, the cost of maintaining agents and event-tables in each node becomes impracticable if there is not enough interest in these events from the base station. In addition, the overhead involved by Rumor Routing is controlled by different algorithm parameters such as time-to-live (TTL) appropriate to queries and agents. Because the nodes become aware of events through the event agents, the proceeding for selecting the route of an event agent highly affects the performance of next hop selection in rumor routing.
Minimum Cost Forwarding Algorithm (MCFA)
The MCFA algorithm [F. Ye, 2001] exploits the idea that the direction of routing is always known, which is towards the fixed base station. Consequently, a sensor node require not have a unique ID nor keep a routing table. As an alternative, each node maintains the least cost estimated to transmit from itself to the base station. Then, each packet to be forwarded by the sensor node is broadcasted to its neighbors. Receiving the packet, the node checks if it is on the least cost path between the source sensor node and the base station. If this node find that is on the least cost path, it rebroadcasts the packet to its neighbors. This method repeats until the base station is attained. In a network using MCFA, each node must know the least cost path estimate from itself to the base station. To do that, the base station broadcasts an advertisement message with the cost initialized to zero while every node initially set its least cost to the base station to infinity. Upon receiving the broadcast packet created at the base station, each node checks to see if the estimate in the packet plus the link on which it is received is less than the current estimate. If it is the case, the current estimate and the estimate in the advertisement message are updated. If the received broadcast message is updated, then it is forwarded; else, it is purged and nothing further is done. As result of forwarding advertisement message immediately after updating, some nodes will have multiple updates and do multiple forwards as lesser cost estimates flow in. Furthermore, the nodes far away from the base station will get more updates from those closer to the base station. To avoid this instability during the setup phase, the MCFA was modified to run a backoff algorithm at this phase. The backoff algorithm dictates that a node will not send the
updated message until A × Cnode time units have elapsed from the time at which the
message is updated, where A is a constant determined through simulation and Cnode is
the link cost from which the message was received.
Gradient-Based Routing
Schurgers et al. [C. Schurgers, 2001] proposed another variant of directed diffusion, called Gradient-Based Routing (GBR). The key idea behind GBR is to keep the number of hops when the interest is diffused through the whole network. Which means that each node can calculate a parameter called the height of the node. This parameter is the minimum number of hops to attain the base station. The gradient on the link between a node and its neighbor is defined as the difference between a node height and that of its neighbor. So that, a packet is forwarded on a link with the largest gradient. GBR protocol uses some additional techniques such as data fusion and traffic spreading in order to uniformly balance the traffic over the network. When multiple paths pass through a node, which acts as a relay node, that relay node may aggregate data according to a certain function. In GBR, three different data dissemination techniques have been proposed (1) Stochastic Scheme, where a node chooses one gradient at random when there are two or more next hops that have the same gradient, (2) Energy-based scheme, where a node increases its height when its energy falls below a certain threshold, so that other sensors are prevented from sending data to that node, and (3) Stream-based scheme, where new streams are not relayed through nodes that are currently part of the path of other streams. The main objective of these schemes is to achieve a balanced distribution of the traffic in the network, which allows extending the network lifetime.
Information-driven sensor querying (IDSQ) and Constrained anisotropic dif-fusion routing (CADR)
The authors of [M. Chu, 2002] proposed two routing techniques, namely, information-driven sensor querying (IDSQ) and constrained anisotropic diffusion routing (CADR). CADR has a goal to be a general form of directed diffusion. The key idea behind CADR is to query sensors and route data in the network in order to maximize the information
30 CHAPTER 2. WIRELESS SENSOR NETWORKS ROUTING PROTOCOLS
gain, while minimizing latency and bandwidth. CADR diffuses queries by using a set of information criteria to choose sensors that can get the data. This is performed by activating only the sensors that are close to a particular event and dynamically adapting data routes. CADR takes in consideration both information gain and communication cost, which is the main difference from directed diffusion. Thus, each node evaluates an information/cost objective and forwards data based on the local information/cost gradient and end-user stipulations. To evaluate information/cost, an estimation theory was employed to model information utility measure. In IDSQ, the querying node can determine which node can provide the most pertinent information with the additional opportunity of distributing the energy cost. Even so, IDSQ does not precisely define how the query and the information are routed between sensors and the base station. Consequently, IDSQ can be seen as a complementary optimization procedure for the protocol. As compared to Directed Diffusion, these approaches are more energy-efficient where queries are diffused in an isotropic fashion and reaching nearest neighbors first.
COUGAR
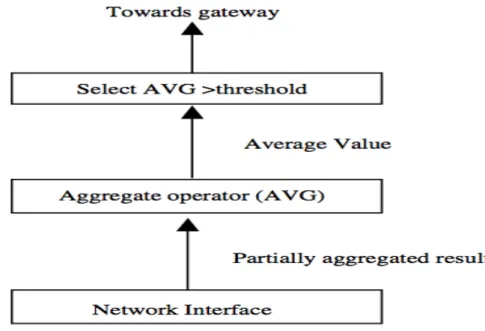
COUGAR [Y. Yao, 2002] views the network as a big distributed database system. The principle of this protocol, is to use declarative queries to abstract query processing from the network layer functions such as selection of appropriate sensors, etc. COUGAR uses in-network data aggregation to save energy. The abstraction is provided through an new query layer lying between the network and application layers. COUGAR proposes an architecture for the sensor database system where sensor nodes choose a leader node to achieve aggregation and transmit the data to the sink( see Figure 2.6 redrawn from [Y. Yao, 2002]). The sink takes charge of generating a query plan, which defines the necessary information about the data flow and in-network computation for the incoming query and transmit it to the relevant nodes. The query plan also indicates how to select a leader for the query. The architecture provides in-network computation capacity that can provide energy efficiency in situations when the generated data is enermous. To assure abstraction, COUGAR provided a network-layer independent methods for data query. But, COUGAR has some drawbacks. First, the use of query layer on each sensor
Figure 2.6: the leader node gets all the readings, calculates the average and if it is greater than a threshold sends it to the base station
node may cause an extra overhead in terms of energy consumption and memory storage. Second, to achieve successful in-network data computation, before sending the data to the leader node, nodes must be synchronized because not all data are received at the same time from incoming sources. Third, to prevent nodes failure, the leader nodes should be dynamically maintained, because leader role is high energy draining.
ACQUIRE
Sadagopan et al. [N. Sadagopan, 2003], proposed a technique for gathering data from sensor networks called ACtive QUery forwarding In sensoR nEtworks (ACQUIRE). As COUGAR, ACQUIRE consideres the network as a distributed database. To drop with complex queries, ACQUIRE proposes dividing each complex query into several sub-queries. In the following, the operation of ACQUIRE is described. The BS transmits a query to the network, This query is forwarded by each node receiving it. Each node that receives the query, tries to respond to it partially by using its pre-stored information and then forward it to another sensor node. If the pre-stored information is not up-to-date, the nodes collecte information from their neighbors within a look-ahead of d hops.