Transparent overlapping of blocking communication in MPI applications
Texte intégral
Figure
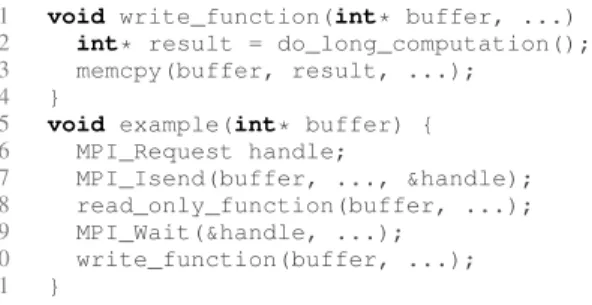
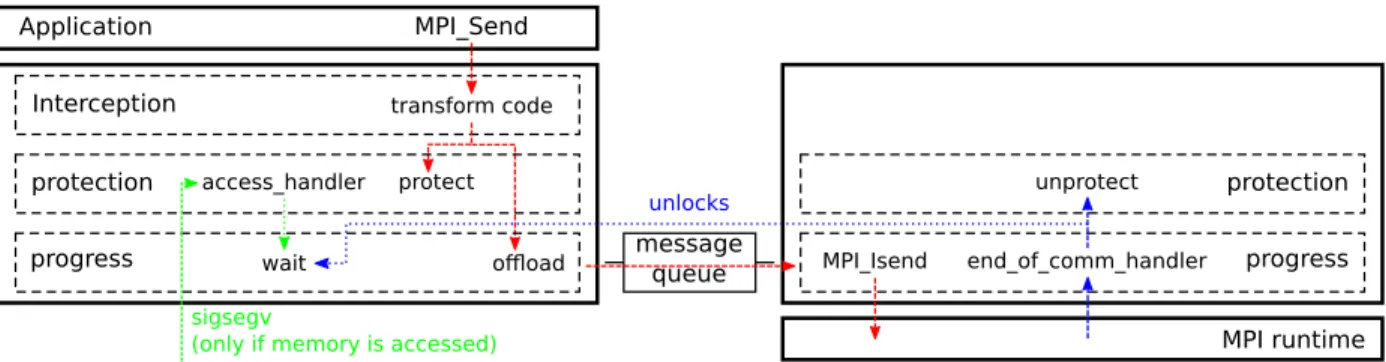
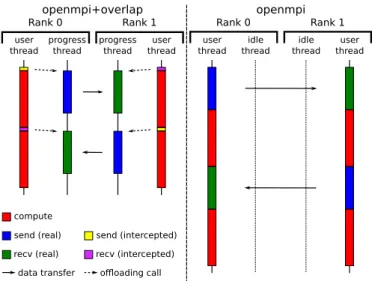
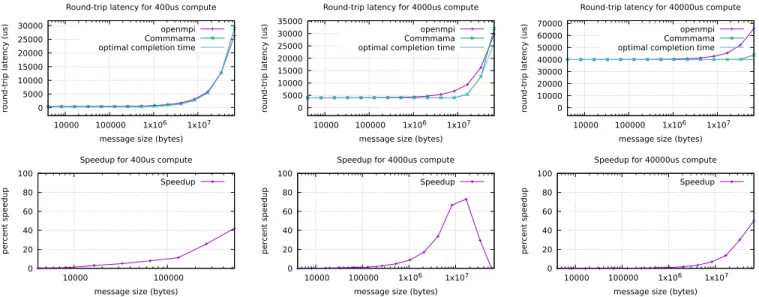
Documents relatifs
o We can estimate the number of theoretical plates in our column based on peak retention times and widths.. o Both factors are important in determining if a separation
(3) Computer and network service providers are responsible for maintaining the security of the systems they operate.. They are further responsible for notifying
Note that, although servers are required to return responses whenever such responses are defined in the protocol, there is no requirement for synchronous behaviour on the part
If an S/MIME client is required to support symmetric encryption and key wrapping based on IDEA, the capabilities attribute MUST contain the above specified OIDs in the
When used in conjunction with MS-CHAP-2 authentication, the initial MPPE session keys are derived from the peer’s Windows NT password.. The first step is to obfuscate the
subarea1 cannot get its zone keys properly signed as its parent zone, region1, is not secured.. The colloquial phrase describing the collection of contiguous secured zones at
2 Until a refrigerator-stable vaccine becomes available, however, varicella vac- cine will not be incorporated into the recommend- ed immunization schedule in Canada, as most
Finally, Bern- stein [2] has identified the obstruction for two smooth asymptotically conical expanding solutions to MCF coming out of the same cone to coincide: the obstruction can