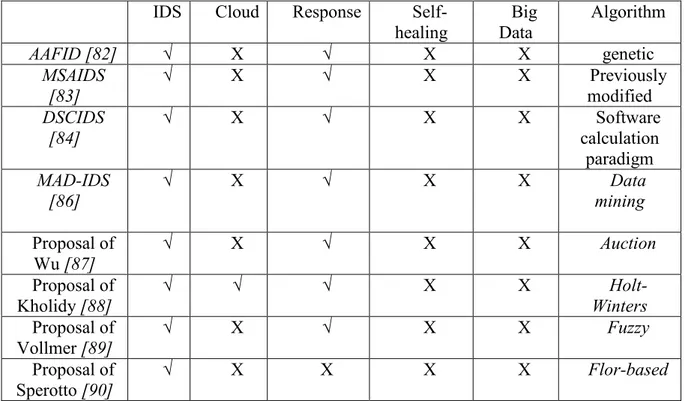
Une approche de sécurité Big Data dans le Cloud Computing
Texte intégral
Figure
![Figure II.1: Big Data-as-a-Service layers [7].](https://thumb-eu.123doks.com/thumbv2/123doknet/2183937.10693/20.892.245.653.109.383/figure-ii-big-data-as-a-service-layers.webp)
Documents relatifs
The detailing of these processes, carried out in [4], allowed us to identify about 50 curation practices, most of which also fall into such categories as data preservation,
Afterward, it has been illustrated that the architecture can manage different obtained data types (including real-time, last-recent, and historical data) in each cross-layer (from
The knowledge extraction in this research is to analyse the data sets by presenting a methodology from the application of big data to solve and offer
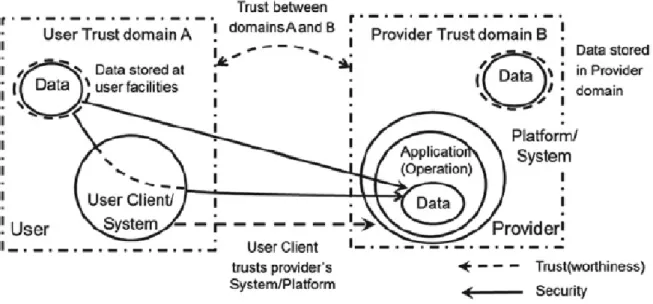
To inhibit these collusion attacks and to avoid blind trust on the integrity guarantees claimed by cloud providers, we advocate an innovative exploitation of the blockchain
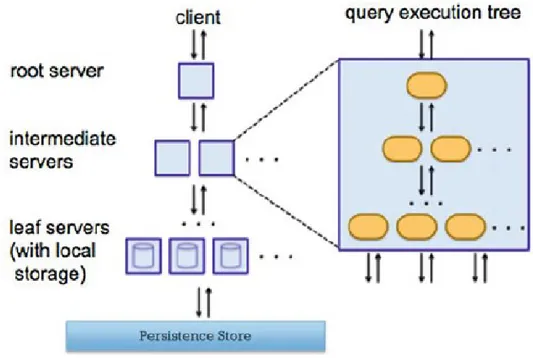
A layered architecture, DMEs and KVSs The idea is simple: A DME (the data consumer, DC) wants to use a data manipulation task at another DME (the data producer, DP).. For
However, if the devel- oped model is rather complex, covers multiple domains, the computation-independent model (describing real-world objects rather than particular sets of
Heatmaps of (guess vs. slip) LL of 4 sample real GLOP datasets and the corresponding two simulated datasets that were generated with the best fitting
CBDCom 2016 has been organized into 11 tracks: Big Data Algorithms, Applications and Services (co-chaired by Boualem Benatallah, University of New SouthWales, Australia