Thin Film-Based Optically Variable Security Devices : From Passive to Active
Texte intégral
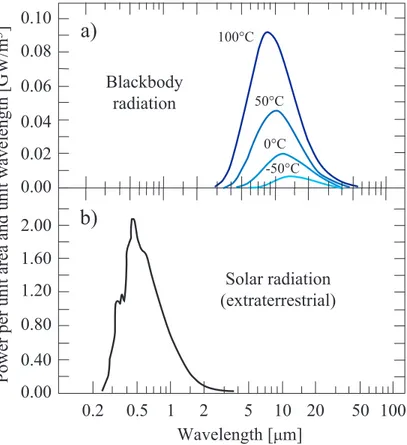
Figure
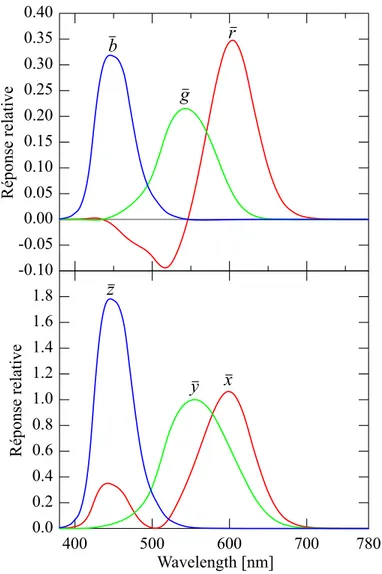

![Table 2.2 Illuminants defined by the CIE. Illuminant xy coordinates T c [K] Description](https://thumb-eu.123doks.com/thumbv2/123doknet/2323644.29721/53.918.109.811.311.908/table-illuminants-defined-cie-illuminant-xy-coordinates-description.webp)

Documents relatifs
The method is based on the computing of the amplitude of the transmitted zero-order antisymmetric Lamb mode in the far field as a function of the frequency after the wave
The first set of experiments is designed to understand the impact of the model type (and hence of the cost function used to train the neural network), of network topology and
In the context of the safety evaluation by EFSA of active or intelligent substances present in active and intelligent materials and articles intended to come into contact with
In comparison with the theoretical limit for a majority carrier trap according to Equation (5), black symbols in Figure 2 show a range of experimental values for the step height
In this section we first recall the concepts of power and interaction indexes in- troduced in cooperative game theory and how the Banzhaf index can be obtained from the solution of
Ahmed Zouinkhi, Eddy Bajic, Raja Zidi, Mohamed Ben Gayed, Eric Rondeau, Naceur Abdelkrim. To cite
Active products worked together and they exchange information on the environment and the security level in real time by a product that can manage asset safety and
In order to achieve this, the Authentication Manager utilizes two processing algorithms: the System Security (SS) Level Auto- matic Update Algorithm and the
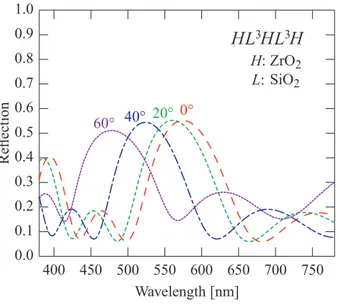


![Figure 4.8 Theoretical model developed by Ashrit et al. for Deb-type devices. [195]](https://thumb-eu.123doks.com/thumbv2/123doknet/2323644.29721/100.918.211.705.640.960/figure-theoretical-model-developed-ashrit-deb-type-devices.webp)