HAL Id: hal-01198382
https://hal.inria.fr/hal-01198382
Submitted on 15 Jan 2016
HAL is a multi-disciplinary open access
archive for the deposit and dissemination of
sci-entific research documents, whether they are
pub-lished or not. The documents may come from
teaching and research institutions in France or
abroad, or from public or private research centers.
L’archive ouverte pluridisciplinaire HAL, est
destinée au dépôt et à la diffusion de documents
scientifiques de niveau recherche, publiés ou non,
émanant des établissements d’enseignement et de
recherche français ou étrangers, des laboratoires
publics ou privés.
A Smart Waste Management with Self-Describing
Complex Objects
Yann Glouche, Arnab Sinha, Paul Couderc
To cite this version:
Yann Glouche, Arnab Sinha, Paul Couderc. A Smart Waste Management with Self-Describing
Com-plex Objects. International Journal On Advances in Intelligent Systems, IARIA, 2015, International
Journal on Advances in Intelligent Systems, 8 (1 & 2), pp.1 to 16. �hal-01198382�
A Smart Waste Management with Self-Describing
Complex Objects
Yann Glouche, Arnab Sinha, Paul Couderc INRIA, Unit´e de Recherche Rennes-Bretagne-Atlantique
Campus de Beaulieu, Rennes, France
email: {yann.glouche,arnab.sinha,paul.couderc}@inria.fr
Abstract—Radio Frequency Identification (RFID) is a perva-sive computing technology that can be used to improve waste management by providing early automatic identification of waste at bin level. In this paper, we propose a smart bin application based on information self-contained in tags associated to each waste item. The wastes are tracked by smart bins using a RFID-based system without requiring the support of an external information system. Two crucial features of the selective sorting process can be improved using this approach. First, the user is helped in the application of selective sorting. Second, the smart bin knows its content upto the precision of composed materials by types and percentage. It can report back with its status or abnormalities to the rest of the recycling chain.
Keywords-green IT; waste management; recycling chain; RFID; NFC; QR code.
I. INTRODUCTION
Waste management is an important requirement for eco-logically sustainable development in many countries. Efficient sorting of waste is a major issue in today’s society. In [1], the concept of self-describing objects is introduced for using the technologies of information and communication to improve the recycling process. In Europe, the consumer society has led to an ever increasing production of waste [2]. This is a consequence of the consumer’s behavior, and worsened by packaging. In [3], it is shown, that the production of waste reaches almost 1.2 kg/day/inhabitant in western Europe. Paradoxically, the same consumers who are concerned with environmental protection are often reluctant when it comes to have more land-filing or more incinerators. Therefore, waste should be disposed and treated properly to reduce environmental impact.
Waste management services are becoming an important market, for which the waste collection process is a critical aspect for the service providers [4], [5]. The main goals are the following :
1) Reducing waste production
2) Ensuring that wastes are properly disposed 3) Recycling and re-using disposed products
To achieve these goals, regulations and taxes are being im-plemented to favor virtuous behaviors. In particular, to reduce the production of waste, there is an increasing trend towards individual billing, where people are charged depending on waste quantity disposed.
Selective sorting is another approach, which is often im-plemented to improve recycling and reduce the environment impact. The importance of resources and energy saving is another argument to manufacture recyclable materials.
The sorting of wastes must be implemented as early as pos-sible in the chain to increase the quantity of valuable recyclable materials. The use of pervasive computing technology such as Radio Frequency Identification (RFID), and sensor networks offer a new way to optimize the waste management systems. In recent years, we have seen increasing adoption of the radio-frequency identification (RFID) technology in many application domains, such as logistic, inventory, public trans-portation and security. Essentially, RFID makes it possi-ble to read digital information from one or several objects using a reader at proximity of the objects, enabling au-tomatic identification, tracking, checking of properties, etc. Apart from this, RFID has added advantages over barcodes. While barcodes compulsorily acts as an enabler that links to retailer’s/manufacturer’s centralized data (mostly exclusive), RFID can mimic the same with an additional advantage of having a memory for storing some information locally. This locally attached related information could be easily accessed by end-users; an evolution of QR code. Hence it could be predicted that RFID could replace existing barcodes, QR codes and attached to most products by the entities for better handling. In this perspective, it is the perfect time to use RFID for waste domain and leverage from their properties to improve current waste management processes.
This paper proposes a method to improve the quality of selective sorting. The approach is based on local interactions to track the waste flow of a city. Each waste is detected by information properties stored in a RFID tag associated to it. At each step where wastes are to be processed the RFID tags are read in order to provide the relevant information. This process improves the sorting quality of recyclable products. We assume organic wastes products are not recycled and hence RFID tags are not attached to it.
Without using an external information system, RFID can improve the selective sorting quality. The information stored in each tag associated to a waste can be used to help the user in the sorting process, and to analyze the content of a bin.
This article is organized as follows. The next section out-lines the architecture used to process the waste flow in our waste management system. Then, we present a tagged (or
“self-describing”) waste approach, before the section detailing on the wastes sorting system based on self-describing objects. The fifth section proposes a certification process of the content to implement reward the users making the selective sorting. The sixth and ninth section discusses other solutions to sort more complex wastes and related work, respectively. The seventh section presents the communication system between bins and the recycling service provider with the prototype demonstration illustrated in the eighth section. Finally, Section IX concludes the paper.
II. WASTE FLOW AND GLOBAL ARCHITECTURE OF THE WASTE MANAGEMENT SYSTEM
Proposing efficient waste management solutions is the pri-mary goal of this article. These solutions are specific to different phases a waste undergoes in the system, discussed later in this section. However, all these solutions exploit our principal approach of self-describing objects. Most of these everyday used objects also undergo through different other phases in their lifecycle; from manufacturing until disposal. As mentioned earlier, manufacturers and retailers already use RFID tagging of their products extensively for inventory. We have assumed their use would be extended with self-description to make them smarter. This would enable them to participate in smart interactions during their product phase as well after their disposal; once they become waste. Hence the tangible data for these items would be available pervasively for autonomous processing throughout the waste management chain. However, it might be necessary to have some exclusive information for products that would be useful for their proper disposal as waste.
The waste management architecture we have considered is built around several elements: waste items, domestic bin, trash bags, collective containers and collecting vehicles. The waste flow starts from the waste items and the domestic bin to end in the collecting vehicles. We now describe each of step in the waste flow and how elements interact.
A. Wastes description
The presented management system is based on a self-describing approach of each waste. We propose to associate digital information to each waste to ensure an appropriate treatment of each item. This is a key point of this approach.
In the selective sorting process, the type of a waste item is identified by its main component. For example, a plastic bottle is identified as a plastic waste, and a cardboard box is identified as a cardboard waste. In the presented approach, each self-describing waste carried digital information about its type. Other properties of the waste are interesting for the collection process of the wastes. For example, the weight of each wastes can be used to estimate if a bin is full, or empty. Without using measurement sensors, the weight data of a waste item can be stored in digital information attached to it, making itself describing.
B. Wastes identification
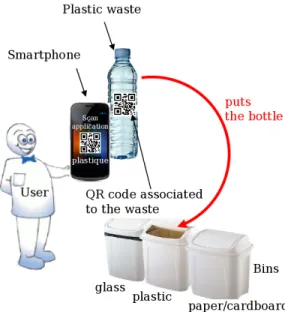
The user is the primary actor in the selective sorting process. Based on this observation, our waste management system proposes some pervasive assistance for the selective sorting process. Then, the waste flow presented in Figure 1, begins at the user level where the trash is generated. As it is shown on the top of Figure 1, we propose to favor a behavior of the users: by indicating the appropriate bin for a waste, or more directly, by opening the lid of the bin corresponding to the type of the waste.
C. Trash bag
To ensure an appropiate treatment, the knowledge of the type of wastes contained in a trash bag is crucial. As for the wastes, it is also possible to associate several properties of each trash bag: for example, the owner of the trash bag, and the number of items in the trash bag can also be considered. In the prototype presented in the next sections, some digital information about the total weight of the trash bag, its content and the number of items contained in the trash bag are physically associated to each trash bag. In this prototype, some digital information is also associated to identify the owner of a trash bag: the interest is to identify the waste production of each consumer. This information defines an analysis report associated to each trash bag.
The analysis report stores some important information for the selective sorting process. The information stored in the analysis report is to determine whether the trash bag could be accepted. In Figure 1, this analysis report is transmitted to the collective container, when a user brings a new trash bag. D. Collective container
In our waste management system, each collective container is associated to an embedded computing system which pro-cesses the data of the analysis report of each trash bag, making it a smart bin. When a new trash bag is added in a collective container, the analysis report is read.
Considering the type of wastes contained in a trash bag, a collective container determines whether it could accept a trash bag or not. For example, a collective container collecting only plastic wastes can stay closed when a user brings a trash bag containing the cardboard objects: it would only be opened for a bag of plastic wastes. If the trash bag is accepted, the smart bin stores some information about the content and owner of each trash bag. Then, the content of a collective container is iteratively updated as a new trash bag is added. The information stored by the collective container is transmitted to the truck during the collection by using a local connection, as it is presented on the bottom of Figure 1. At this step, the errors of the selective process can get transmitted. Among the collection of wastes, the highly polluting wastes which are not placed in the appropriate container, are detected: for example, it becomes possible to detect a battery placed in the container dedicated to plastic waste.
Considering this waste flow, we now present a system based on RFID technology to implement this waste sorting process.
Figure 1. Waste flow and global architecture of the system.
III. TECHNOLOGICAL SUPPORT FOR SMART WASTE INTERACTION
Our smart waste approach consists of associating a physical waste with digital information. In our approach, information associated to a waste can be stored in a QR code or in a RFID tag memory. Using QR codes does not introduce an additional cost. However, QR code requires the object to be in line of sight. Unlike this technology, the RFID tags can be read without requiring a precise position relative to the reader during the reading operation. The UHF tags, are used increasingly in the supply chain management and can be easily read at a distance of five meters from the reader antenna. In this context it is easy to envisage a widespread deployement of the RFID tags on each manufactured product. This is an important advantage for using RFID technology in the waste management domain.
The tagged waste concept uses the data banks memory of a tag to store information about each waste associated to the
tag. The tag memory is not used to store an identifer of the waste in an external database, but the information describing the associated waste is directly stored in the associated tag. A connection to an external database is not required to have some information about the smarte wastes. Only a RFID reader is required to read the information of a smart waste. Figure 2 presents a smart waste composed of a plastic bottle associated to a RFID tag which stores the data describing the bottle as a plastic object.
Figure 2. An example of a smart waste.
A RFID tag contains data banks for the users applications. The memory size of data banks is limited. For example, an UHF tag ALIEN ALN-9640 Squiggle shown in Figure 3 can store 512 bits of information.
Figure 3. The ALN-9640 Squiggle Alien tag.
In [6], the classification of type of wastes is proposed. In this classification, each type of waste is associated to an identification number. Taking examples from everyday life:
• the cardboard is associated to the reference 200101,
• the glass is associated to the reference 200102,
• the plastic is associated to the reference 200139. The smart waste concept proposes to use the classification [6], to store the reference number representing the type of the waste in memory blocks of each tag associated to a waste. As it is shown in Figure 4, our prototype also saves in the tag memory of each smart waste, the weight (represented by a measure in grams, encoded in hexadecimal) of the waste associated to the tag. The weight encryption presented in Figure 4 is a way to store directly the description of each waste directly in the associated tag.
Until this point of the section we have seen how the digital information is associated to the physical waste objects. During their disposal at different stages of the waste management sys-tem, these information are read and transferred for processing and aggregration. The rest of this section describes the various modes of the domestic waste collection; and the transfer of
Figure 4. Representation of the information in the tag memory.
its digital information to the smart trash bags. Finally the collective smart bin is demonstrated which is suitable for community waste collection area. The smart trash bags are disposed here.
A. Individual smart bins
At the first step of our waste sorting system, the information contained in the RFID tag associated to each smart waste is used to help the people discarding an object in the appropriate container. Here, the main goal is to reduce the sorting errors when someone does not know which is the right container, or mistakenly discards the object in the wrong one. It is also help people to learn the selective sorting rules applied locally. The smart bin system uses the self-describing approach of smart wastes to improve the selective sorting quality.
The description of smart wastes is stored in a RFID tag physically associated to each smart waste. Using a RFID reader, the smart bin reads the RFID tag attached to each smart waste to determine the appropiate treatment. Let’s consider the example of someone who wants to discard a plastic bottle in a bin. He puts the bottle near a smart bin as it is shown on Figure 5. When the plastic bottle is in the antenna area, the tag associated to the bottle is detected. The data stored in the tag is read to determine the appropriate procedure to discard the bottle. If the bin accepts plastic objects, then the system opens the lid of the bin. Otherwise, the system keeps closed the lid of the bin.
Note that it is also possible to control the opening of several containers using a single RFID reader. Figure 5 presents a prototype of a selective bin. In this approach, a management system connected to a RFID reader uses the data stored on waste tags to open the correct containers. In this example, when someone want to discard a pastic bottle, the container for the plastic wastes is opened by the management system. On Figure 5, only the lid of plastic container will be opened, all other lids will remain closed.
This approach assumes that the management system tracks the information of the wastes that are discarded in each container of a selective bin. When a waste is discarded in the container, the management system updates the memory inventory for this type of waste. In this way, undesirable wastes
Figure 5. A RFID based selective bin.
for a given container are either rejected or tracked, depending on the choosen policy for handling undesirable wastes.
The scanning of products is done itemwise to ensure a complete reliable reading process.
Figure 6 presents a prototype of a smart bin based on UHF RFID tags and a UHF RFID reader which implements this approach.
Figure 6. A collective bin using the RFID technology.
UHF RFID technology is already used in the supply chain management systems. In this context, a UHF tag is placed on the packaging of each product at the begining of its lifecycle.
Since the UHF tag is already attached on the packaging of each product for the supply chain management process, we are interested to reuse the tag and its technology in our smart bin approach.
B. Use of QR codes technology for a cheaper approach The passive UHF RFID tags are quite cheap, ranging from $0.25 to $0.40 per tag. However, the relative cost overhead and utility is important for businesses to adopt the technology. They would readily agree to tag an expensive item than very cheap ones. To take care of this practical aspect, we introduce a cheaper solution using QR codes technology. It would allow an early adoption of few concepts and applications presented previously. Using QR code is not necessarily an alternative but could also be considered as a complement to RFID for cheap items. This approach takes advantage of the embedded NFC capability in users smartphone.
This alternative approach assumes that every waste is asso-ciated to a QR code describing its type. The mobile application maintains in its memory the current inventory for each type of collected wastes (for example, 3 inventories if there are 3 types of collected waste). Waste disposal would require users to scan each item, allowing the mobile application to update the current inventory for this type of waste in phone’s memory. Some other waste properties, such as weight, could also be collected at this step.
A smartphone is a small, low-cost, mobile computer. More-over, most smartphones now embedd a camera enabling them to read bar codes or 2-dimensional QR codes (also known as “flash codes”). A first step in the solution would consist to scan a QR code (or bar code) associated to a product, and to use this information for giving a sorting instruction to the smartphone of the user. As in the approach of the individual RFID bin presented in section III-A, it is also important to report the actions of the user to the waste collecting chain.
On figure 7, a user wants to drop a plastic bottle. He scans the QR code associated to bottle. The properties associated to the bottle are added to the inventory of the plastic container that is stored in the smartphone’s memory.
Obviously, reading QR code is less convenient than RFID reading. In addition, in this approach the opening of the lid is also not controlled by an automatic system. However, this approach allows the deployment of the rest of the chain with-out requiring the smart bins presented in section III-A inside each home. Beside being cheaper, the mobile application also provides helpful support to the user regarding the selective sorting rules in application.
Like the individual bin presented in section III-A, the man-agement system of the collective bin tracks wastes properties as they are disposed. When a smart trash bag associated to a RFID tag is dropped in the collective container, the management system updates the collective inventory according to the new bag’s content. Prevention of sorting errors is also possible, provided that the user actually fills his trash bags according to what he scans.
We don’t rely a network connection on the bin instead it is
Figure 7. Reading of a QR code associated to a waste.
the waste bag itself which will store the waste inventory. As we will see in next section.
C. Smart trash bag
In the individual selective sorting point like a user’s smart kitchen bin, the wastes are not directly deposited in the container of the bin. Every user utilizes trash bags, which will be dropped to a collective container, or put at the entry of every households for being collected by the service provider. The smart trash bag concept is smart in the sense that the waste management infrastructure (bin, truck) will be able to check its contents. A smart trash bag is a trash bag associated to a RFID tag, as it is shown in Figure 8. The tag associated to a smart trash bag, offers a memory space to store some information about the contents of the trash bag: type of wastes, number of items. The RFID tag associated to the smart trash bag also stores some information about its owner: name, address, etc.
Figure 8. A smart trash bag.
Writing data in the tag associated to the smart trash bag about its content is very simple: for each new waste added,
it is identified by reading the waste tag; then, the trash bag content is updated by writing in the trash bag’s tag with the updated information about its content. This approach enables the tracking of trash bag content. Various information can be reported: the type and quantity of wastes contained in the bag, total weight of the content, and the interactions between the wastes. In this approach, it is assumed that the management system ensures that all the wastes of a container belong to the same type. Then, it is just necessary to store the expected type of wastes in the analysis report. The weight of the smart bag is estimated by considering the weight of each smart waste contained in it. When a smart waste is added, its weight is read in the tag memory of the smart waste. The weight of the smart trash bag is refreshed by adding the weight of this smart waste to its current weight. The weight is computed when a smart waste is added. This iterative process uses the information stored in the tag associated to each smart waste. This approach is totally autonomous and based on the information stored in the tags associated to each smart waste. A connection to an external information system is not required to obtain the information associated to each waste.
As it is illustred in Figure 9, the information stored in the tag associated to the smart trash bag, are encoded by a sequence of bytes. The storage of the identifier of the owner uses three bytes. Using the classification of wastes [6], the type of wastes is stored on six hexadecimal digit: three bytes. The number of waste items is stored on one byte. The weight (in gram) of the content is stored on two bytes. Without require to an external database, the description of trash bags content is direcly carried by the tag associated to the trash bag.
Figure 9. Data memory structuration of a smart trash bag.
The individual smart bin approach presented in Sec-tion III-A assumes that the management system tracks the information of the wastes that are discarded in each container of a selective bin. To this end, the management system updates the analysis report of a container when a smart waste is added in the container. The whole report is stored locally in the memory of a tag associated to the smart trash bags. In the prototype in Figure 6, the analysis report stores the information about the owner of the smart trash bag, the type of the content, the number of wastes, and the weight of the content, using the data representations shown in Figure 9.
We have also developed an application to store the analysis report of the content of a trash bag for the cheaper solution using QR codes technology presented in Section III-B. In our
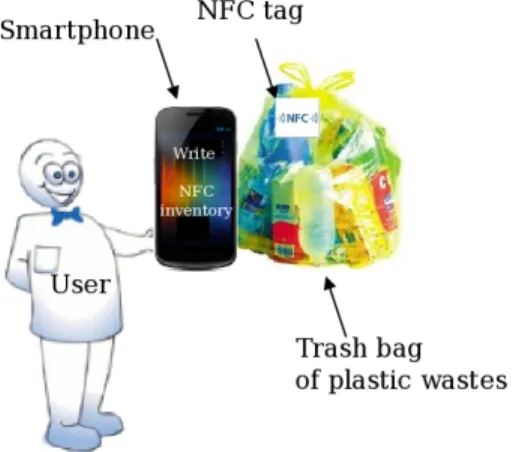
prototype, the NFC technology provides this second step of the solution: NFC-enabled smartphones can interact in close proximity: in particular, they can read some RFID tags and also emulate the response of some tags. It is in the former functionality that we are interested, as it allows a user to write the required information in a trash bag’s tag using only an NFC smartphone.
Figure 10. Writing analysis report operation with a smartphone.
When the bag for a given type is full, the mobile application is used to write the inventory in the RFID tag attached to the trash bag (figure 10). The smartphone uses its NFC reader/writer for this operation. Then the user closes his trash bag of plastic wastes. Now, he uses his smartphones application to write the inventory of the trash bag, in an NFC tag associated to the bag.
D. Collective smart bins
The collective smart bin collects the smart trash bags produces by the users. Here, we consider a scenario for the collective smart bins, which can be placed in a common space of several apartments or in a street. Using the self-describing approach of the smart trash bag, the collective smart bin monitors the flow of wastes, and it detects the alerts: fire, mistake of sorting, detection of undesirable objects. The information about its content is transmitted by an ambient network or local Bluetooth connection during the collection, according to the type of information. As for the individual bin approach for helping the sorting process, it is possible to open a container only when objects of the correct type is brought by a user. The RFID inventories cannot ensure that all the tags have been detected in antenna area of a reader, meaning that missing tags are unnoticed. Considering this limitation, we propose an “incremental” approach, where the global content of the collective container is updated each time a bag is disposed.
The analysis report of the content of a trash bag presented in Section III-A is used to update content of the collective bin. This approach is based on the self-describing concept of the content of a container. As the same way that the individual container stores knowledge about the wastes, the collective container stores knowledge about the smart trash bags. It is a
new way to measure the state of a container without require to the classical use of several sensors. For example, the weight of content, the size, or the type can be measured by using the information store in the tag of each waste of a container, without use one specific type of sensor for a specific property. For example, the total weight of the wastes of a collective container can be estimated by incrementally adding the weigth of each smart trash bag brought to the collective container. The information stored in the tag of the smart trash bag is only needed. This autonomous approach facilitates a large scale deployment of the smart bins.
Figure 11 shows a user in a garbage room. He presents his trash in reading area, where the trash bag’s tag is read. The
Figure 11. An individual bin using the RFID technology.
analysis report of the content of the trash bag is transmitted by the reader to the container’s controller. The controller can then determine the appropriate action, depending on the bag’s content and the local policy. For example, it could reject the bag if it contains an inappropriate item (container remains closed), explaining the cause of rejection to the user (such as “glass is not accepted in this container”). Implementing this policy is a way to avoid that a sorted container is contamined by undesirable material. For example, it becomes impossible to pollute a container for plastic waste with metal cap of a plastic bottle.
IV. AN INTEGRITY CERTIFICATION PROCESS OF THE CONTENT OF A TRASH BAG FOR REWARDING THE
SELECTIVE SORTING
Based on the smart waste and smart trash bag concepts, the applications presented in Section III proposes to help the user in the selective sorting process. Considering this selective sorting approach, it becomes easy to reward the behavior towards the environment. The smart bins approach uses all the hardware required to implement a payback mechanism based on a micropayment approach. Based on the same concept of ubiquitous computing, it can be implemented by a payback mechanism where some coins are locally stored in the smartphone of each user. This non centralized approach makes easier its deployment, and respect the privacy of the users: they don’t require a server with centralized data about the
detail of the wastes production of each household. Whatever the payback mechanism implementation, the reward process will be based some properties like the number of item, the weight, or a value associated to each waste. In this case, wastes and trash bags have a value, they become critical objects for which it is necessary to check the integrity. Then, it becomes essential to be able to check the integrity of a trash bag to implement a payback system based.
Our approach considers two steps of the selective sorting process. Firstly, the individual smart bin facilitates the selective sorting of the trash bag for the user. Secondly, the collective smart bin save ensures a good selective sorting of the smart trash bag, considering the informations stored in the tag of the smart trash bag. The collective smart bin uses the waste inventory stored in the tag of the trash bag, to ensure a real time waste management of its content. But, between the individual container and the collective container, some events which disturbes the selective sorting process, can arrive. In particular, many indesirable objects can be added. For example, a battery can be added in trash bag of plastic waste. A mistake or a malicious behavior can corrupt the chain of the selective sorting between the individual smart bin and the collective smart bin.
Here, we suggest a method to implement a certification pro-cess of the content of a smart trash bag. Using a certification inventory mechanism presented in [7], the inventory of the set of all the wastes contained in a trash bag can be used and certified. This approach purposes to add a integrity information in a group of tags. Then, an RFID inventory of this group is certified by checking the consistency of the informations distributed over the set of tags.
A. Certified content creation phase
In the selective sorting application presented in Section III, the certified content creation phase is made by a user with his personnal indiviual bin. In the smart bin application, the integrity information is a hash value computed with the set tag identifiers at the level of the individual smart bin.
Considering a set of tags with unique identifiers t1, t2, ..., tn.
Each tag is associated to a waste contained in a trash bag. The idenfiers are ordered in a determined sequence (using a choosen order relation). Then, a hash function is applied to this information to compute the digest: d = hash(t1, t2, ..., tn). As
it is shown on Figure 12 This hash value is used as a group identifier gid, stored in the tag of trash bag which content the set of wastes. This hash value is used as an integrity information which enables the integrity checking phase.
When a waste is added in the smart individual bin, the management system stored its identifier in its memory. The management system of the individual bin incremantaly stored the identifiers ti of each waste added by the user. When the
users closes his trash bag, the group identifier gid computes with the identifiers t1, t2, ..., tn of each wastes is stored in the
of tag of the smart trash bag.
Because the memory size in the tag is limited and the integrity check should be fast, the group will be represented by
Figure 12. Building of a certified object set.
a digest, computed by a hash code function. A good discussion of hash functions in the context of RFID is [8]. This approach enables full autonomous operation of both the association points and the checkpoints.
B. Checking integrity of content phase
The integrity checking phase is done at the level of the collective smart bin. The integrity checking phase considers the inventory of all the wastes contained in a trash bag. The integrity checking phase consists to verify if the hash value computed with all the tag identifiers read by the RFID reader, is equal to the integrity information stored in tag of the smart trash bag, at the individual bin level.
The principle is to read all the tags identifiers ti of the
wastes of a given trash bag (sharing the same group id gid), and verifying that the hash(t1, t2, ..., tn) = gid. If the
computed hash does not match the gid stored in the tags, the group of waste in a trash bag is considered as invalid. If many waste are remove from the trash bag, or, if many indesirables are put in a bag, the collective container will not open, because the integrity of the group of wastes inventory is wrong.
RFID inventory do not need line of sight with RFID tag for reading its contents: it is an important feature of the RFID inventory. That can be used to facilitate a checking process of the integrity of trash bag content, at the level of collective smart bin for. It becomes possible to read all the tags associated to many smart wastes contained in a smart trash bag.
This behavior of the collective container may seem be very restrictive. At the application level, some adjustments of behavior can be considered. For example, in the case where, the integrity information of the smart trash bag is not valid, considering the set of all waste types, detected during the
RFID inventory of the reader: if all the types of set are conformed to the type of wastes accepted by a container, the container can also be open. Using the RFID technology, this evolution of the system adds an automatic checking of the content of each trash bag.
C. Certification mechanism for the NFC and QR code ap-proach
The certification mechanism can also be applied to the approach presented in Section III-B based NFC and QR code technologies. To do this, it is necessary to duplicate the informations stored in the QR code of each waste to an RFID tag also associated to the same waste. The integrity informations is computes using the identifiers stored in each QR code associated to a waste, and it is written in the NFC tag associated to the smart trash bag using the smartphone application of the user. The informations contained in the tag will be used by the collective container presented in Section III-D. The collective container will check the integrity of the content of a the trash bag, without rescanning the QR code of each waste.
The checking operation consists to compare the group signature stored in the NFC tag of the trash bag, to the hash value compute with all the identifiers detected during the RFID inventory. If they are equal, the content of the trash bag is valid, else the content of the trash bag is corrupted.
Considering this certification mechanism, the NFC and QR code approach of the selective sorting stays also cheaper, because the RFID reader are not deployed the households, but only on the collective container.
V. SOME MORE COMPLEX SCENARIOS
Waste is a menace for the society. If these are not disposed and treated properly, it can be detrimental to the living beings and the environment [2]. Managing the waste is a huge task, given its ever-increasing volume generated. They could even be complicated at times depending on the nature of waste. They come in many different forms like biodegrad-able, biomedical, chemical, clinical, commercial, electronic (e-waste), hazardous, industrial, nuclear, sharp, toxic etc. Each of the categories has to be processed differently. Hence, sorting must be performed at the earliest for performing appropriate treatment. However, as discussed earlier, some waste contains potentially useful materials for reuse, which are recycled. These need early separation through sorting, to prevent their contamination by other waste types and maxi-mizing the amount of valuable recyclable materials contained in them. Hence, sorting is a very important process for waste management. In subsection V-A and V-B, we describe two other scenarios for efficient sorting.
A. Selective sorting
As described above, one of the aims for sorting is to maximize the amount of recyclable materials like paper, glass, plastic etc. We present another approach which would enable this aspect of maximization. Smart waste containing
the information about the amount of recyclables that could be recovered from them. Their tags are encrypted with the recyclable material classification type identifier and percentage information; instead of weight proposed, similarly, in section III.
Consider the examples smart waste in Figure 13. The cardboard box, glass bottle and plastic bottle are made of recyclable materials. Each of their tags contain the information that they are made of cardboard, glass and plastic with 48%, 97% and 83% respectively. This kind of information would benefit in taking preferential decisions when sorting. Suppose a sorting process wants to gather glass (type identifier 200102) waste with atleast 85% purity. Among the three items in figure, the glass bottle in the centre satisfies the conditions in respect of both, material and its quality. Hence, it would not be possible to contaminate a sorting process with inferior or other materials. As a matter of fact, contamination could also be the other way; like, adding the bottle from above example for a sorting process collecting low quality glass, between 40% and 75%. So, it is upto the sorting process to choose the purity range (in %) of recyclable materials while collecting waste.
Figure 13. Representation of recyclable material percentage in the tag memory.
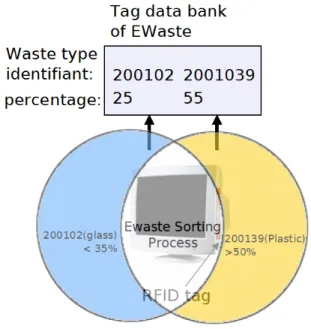
Practically there are various forms of waste that contain multiple materials. A typical example of such form would be ewaste or electronic waste. Computers, telephones, tele-visions, etc.; all such electronic items contain recyclables and hazardous materials. Plastic, glass, metal are some that can be extracted for reuse. Hence for such forms of waste, the above sorting process requires some modifications to its conditions. The sorting conditions must have flexibility to accept items containing multiple recyclable materials; unlike the process explained in the preceding paragraph. Consider for example a sorting process that accepts waste items containing glass (identifier 200102) < 35% and plastic (identifier 2001039) >50%. The two conditions are represented by the two coloured circles in figure 14 with their combined at the intersection. The monitor in the figure, is tagged containing composition information of type and quantity of materials used i.e. 25% and 55% of glass and plastic respectively. The composition satisfies the conditions set for the sorting conditions and hence would be accepted.
Figure 14. Representation of recyclable material percentage in the tag memory.
B. Detecting hazardous interactions
Until section V-A, we explained how RFIDs attached to items store information regarding its quantative measures (weight and percentage) of recyclable materials enabling ef-ficient sorting. The smart bin is a collective container that has an embedded computing system to read and process the tag data. However, there are other ways to perform sorting for better waste management. The sorting objective is to maximize on the concentration of recyclable materials for value. An accumulation could be contaminated due to the presence of other particular materials. This could render the entire collection unfit for recycling. Consider for example a glass bottle put into a paper or plastic bin. This would reduce the recycled value of the collected paper or plastic items [9]. Apart from mixing of materials, there could be physical hazards reducing the value of collected items. A flame caused due to an explosion from aerosol can in high temperatures can ruin the collected paper or plastic materials. Disposal of such unsafe items in the same waste bin could result in a snowball effect of physical hazards. The remaining part of this section proposes a sorting process that would enable avoiding such linked incompatibilities.
1) Principle: Pervasive computing is the growing trend of progressing beyond the idea of personal computing. Objects used everyday have embedded technologies attached, to per-form smarter activities collectively. Smart waste items have self description of their properties using RFID tags. Based on these properties, incompatibilities are computed among a collection of items present locally. In this section, we discuss its underlying principle. For the purpose we begin with organizing the waste domain in a specific manner for making such inferences.
a) Describing waste items: The waste domain can be categorized based on their various hazardous properties. There are standards that specify the properties of waste materials and categorizes them [10]. Although, discussion on such standards is outside the scope of this paper, however we utilize its idea for categorization and use few examples of hazards related to some of these categories.
Some examples of hazardous properties for this domain are spark, explosion, toxic fumes etc and can categorize based on them. As discussed in the previous section, we are interested to infer incompatibilities. So, it is essential to pick the properties only that are relevant for interactions with other items.
Figure 15 represents pictorially the data structure used for describing waste categories. Its individual fields are described as follows:
Figure 15. Conditions to describe a category
• under effect of: the condition(s) which holds the proper-ties that can influence the category
• can cause: this condition enlists the hazardous properties
that the category is capable of causing
• in presence of: this holds the external conditions under
which the can cause properties occur; they are the phys-ical environmental conditions that need to be captured using sensors.
In the subsequent sections, we will use the same pictorial representation to describe the waste categories or items in our examples.
Let us take some scenarios of interactions between cate-gories. First, let’s take an example of simple incompatibility between a pair of them. Suppose a category A can cause an incidence (for instance say hazardous property X) that affects a second category B. Hence, an incompatibility exists between the categories A and B. Our second example is a slightly more complex and realistic than the previous example. If the category A causes the incidence (i.e. X) only in presence of an external condition (let’s name as C), makes it an important augmentation to the scenario. Hence, the categories does not pose to be incompatible if the condition C is unfavorable. Both of these scenarios consider the incompatibility between different categories where the hazardous property affects each other. However, there are properties like explosion for exam-ple, which have hazardous effect by itself. The situation can be represented as a category that causes a hazardous property that affects itself and may depend on the external condition.
b) Inferring incompatibilities: As described above, we can self describe waste items accordingly. When a collection of these items is present locally we can infer incompatibilities
based on the discussed scenarios. Sometimes objects are located remotely and communicate within themselves and other knowledgebase using network infrastructure like the Internet to make decisions. Such an idea is called Internet of things (IoT) in the field of pervasive computing. Our approach in this paper proposes making the required information that describes waste domain available locally for inferences. Such collective inferences could be made without using network for communication. We prefer to use the name for such a situation as Intranet of Things (InoT) as it does not involve any devices located remotely and differentiate to avoid confusion.
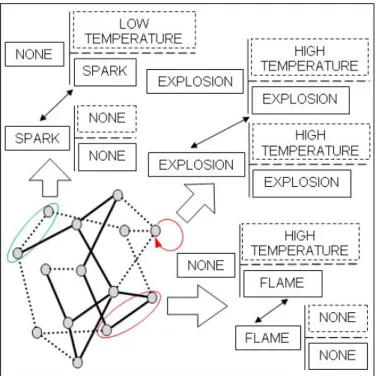
In V-B1a, we discussed the interaction scenarios between pairs of categories based on hazardous properties. Multiple such categories can constitute an InoT. The graph in Figure 16 represents an example of InoT formed. The shaded nodes represent some categories. They are connected by an edge if they interact. The dotted edges represent interactions which are unfavorable due to external conditions. One of the external conditions were high temperature at the instance this snapshot was drawn. Hence, the dotted edge encircled in the figure representing an interaction under low temperature becomes unfavorable. The firm edges represents favorable interactions, which could be either the first or second scenario described in V-B1a. The shaded node with a self-loop represents the last scenario of V-B1a, is favorable in this case as the external condition is satisfied.
Figure 16. InoT formed
Finally, if a waste item belongs to one or more categories, it would possess all their conditions. Hence, they could be used for collective inferences also.
2) System Design: In this section, we describe designing the system for making inferences locally. It essentially means
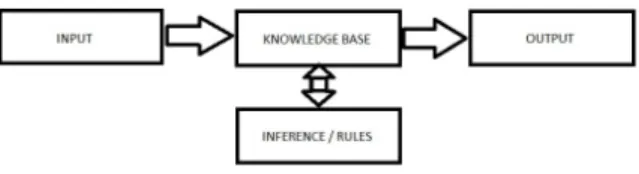
that all the information required are available without referring to remote database or knowledgebase. An alternative could be to distribute the information partially among the waste items and a local knowledgebase. The waste items are identified by the system before inferring on incompatibilities. We have chosen a commonly used architecture for our system, as shown in Figure 17 below.
Figure 17. Commonly used Architecture for Systems
We describe the components briefly.
• Input: It is that point in the system where the waste items are identified and added.
• Knowledge Base (KB): This contains all the required
in-formation to identify the items along with their properties. It also updates its knowledge regarding the presence of items that are being added to the system incrementally.
• Inference/Rules: This component of the model uses the KB to reason out about the possible incompatibilities and hazards. The inferences are added back to the KB.
• Output: It sends out notifications to communicate about alerts and warnings to the users of the system.
Next we elaborate on how the system works based on the architecture and uses the principle discussed earlier in Section V-B1.
a) Input: New waste items are added to the system. They are affixed with RFID tags only for the purpose of identification by the system, which contains a RFID reader for scanning. The tags do not contain any such data that has privacy concerns. Mostly they contain the category informa-tion.
b) Knowledge Base (KB): Machines can be made to perform reasoning effectively provided it has the necessary knowledge, which is machine readable. In cases of large do-main knowledge with lots of factors influencing the reasoning, using machines should have extra benefits. Using ontologies are a very good way to serve the purpose [11]. An ontology consists of common set of vocabulary as shared information of a domain. It includes machine-interpretable definitions of basic concepts in the domain and relations among them [12]. Lately, the development of ontologies has begun to find many uses outside the Artificial-Intelligence laboratories. They are being commonly used on the World-Wide Web and finds applications for sharing information widely in the field of medicine.
The Web Ontology Language (OWL) is a World Wide Web Consortium (W3C) Recommendation for representing ontologies on the Semantic Web [13]. Presently, there are a lot of ontology editors for OWL. Among them Prot´eg´e is a Java based Open Source ontology editor. We used Prot´eg´e since we found it to be an efficient and user-friendly tool to prototype
our ontology rapidly. During the ontology development phase we visualized the graphical representation of our OWL ontol-ogy on the editor. The comprehensive Java API provided by Prot´eg´e [14] was also an added advantage while developing our stand-alone application in the later phase.
We have used an ontology based approach for the KB for the reasons stated above. The properties causing incompati-bilities must be described in the ontology. Apart from these, other information like conditions in which the categories are incompatible, possible hazards of incompatibility etc are also stored in the ontology.
Due to the advantage for describing a domain easily, we have used ontology based approach for describing the waste domain. The ontology contains description of various cat-egories with the conditions for hazardous properties. This constitutes as the initial knowledgebase of the system, which is maintained locally. It updates itself as new items are added. Additionally, the external conditions are also updated from the environmental parameters from sensor data. The modelling and design of the ontology is detailed in the paper [15].
c) Reasoning/Rules: Reasoners are a key component of OWL ontologies. They are used for deducing implicit knowledge by querying the ontology. In the recent years, rule languages have been added on as a layer combined with ontol-ogy, in order to enhance the reasoning capabilities. Semantic web Rule Language (SWRL) is used to write rules expressed in terms of OWL concepts and for reasoning about OWL individuals. It provides a deductive reasoning specification that can be used for inferring new knowledge from the Knowledge base.
The ontology, which acts as a KB in our architecture, con-tain all the necessary information for reasoning. Our objective of inferring incompatibility or hazards are performed using OWL reasoners. The reasoner springs into action each time the RFID reader detects a tagged item. It infers if the incoming item has incompatibility with the already present contents using the ontology KB. The reasoner also provides the analysis if found unsuitable.
3) Applications: We have proposed the system using on-tology as it’s local knowledgebase to infer incompatibilities on the principle of InoT. We think that it can be used to infer incompatibilities among objects in various domains. “Bin That Thinks” is a project, that aims to propose an intelligent waste management solution based on item level identification. The goals are to improve recycling efficiency, reducing waste pro-cessing cost and avoiding hazardous situations [16]. Though we have not assessed for the financial benefits figuratively for using our system, our approach hints at the benefits qualitatively. Sorting wastes at the earliest retains the purity of the recyclables. This reduces the cost of sorting at a later stage in processing plants by waste management companies like Veolia, which is usually passed on to the consumers as penalties on the cities.
We have developed an application for the domain of waste management using the system described in this paper. It can be used to make inferences for incompatibilities and hazards
Figure 18. Final Smart bin Prototype
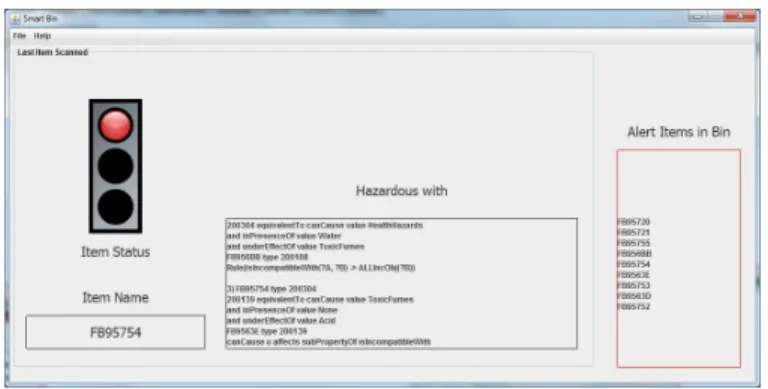
among the waste items present collectively at a place. They may be situated inside a bin or a waste collecting vehicle or at the processing plant. For very complex domains like waste management, they are sometimes verified at every step in the processing chain. Alternatively, when the processing is performed at a single point, we consider the acceptance of error up to some limit. Fig 18 shows a prototype of the final Smart bin that would identify the RFID tagged wastes and make inferences from its contents. It contains an RFID reader, an on-board processor, environment sensors for temperature, pressure etc., an OWL ontology based knowledgebase and a display. The reader senses and reads the category when an item is brought near the bin. Then the reasoner makes required inferences using the KB before the bin actuates. The appropriate lid opens for the user to dispose the item, if it is found suitable with a green signal on the display. Else, the display flashes red along with the reasoning for incompatibility. Fig 19 below shows a screenshot of our application. It shows the instance when an incompatibility is detected with two items present locally in the bin and the last item that was scanned. It also displays the inferred reasoning.
VI. COMMUNICATION ARCHITECTURE OVERVIEW
The self-describing information collected at the level of the collective containers are useful for the service provider of recycling. These information can used to enhance two aspects of the recycling process:
• to optimize the waste collection scheduling by the truck
(it is not necessary to collect an empty container) and monitor their waste inventory
• to adapt the treatment of the content of the bins (if a
container is polluted by an undesirable product which requires to have a specific treatment).
Figure 19. Hazard Detection Application for Waste
Obviously, it is necessary to communicate this information before the waste collection. The self-describing information of each collective container have to be transmitted to some terminals of the service provider of recycling, or to the truck driver which collects the bins.
The communication process between smart collective con-tainer is based on an ambient network, as it is shown on the top of Figure 20. In this communication architecture, each collective container is a starting point of the ambient network. The data of a given smart collective container are routed from the smart container to a terminal (to the service provider of recycling, or to the truck which collects the bins). So, the data can go through several communication nodes before being received by the terminal. The architecture is possible due to the urban topology where each bin is very close to the others. This non-centralized approach is less costly than using a GSM connection from each collective container to a terminal.
The motive behind incorporating this feature enables effi-cient waste management. The different types waste collected by the operators have associated monetary value. Hence they require sorting based on their types before being sold to third parties who recycle and reuse them. While the sorting is taken care at the bin level, the communication infrastructure of bins help in efficient collection and marketing. The operator can have a global view of the current stocks of the by-product materials (plastic, glass, etc.) in the bins for a given city, or even country-wide. Finally, it can receive alerts in case of incompatibilities or physical hazards in the waste containers; as described in the previous section.
Partners of the “BinThatThinks” project [16] have imple-mented this ambient network with nodes offering an effective radio-frequency communication. In a city, it is difficult to deploy a totally reliable ambient network of bins, due to envi-ronment constraints. In fact, the communication graph (where each vertex is a communication node, and each edge is a communication link between two nodes) can not be connected. Then, this architecture requires some communicating nodes to have a GPRS connection for sending data from parts of the ambient communication network which are not directly accessible go through the ambient network. These nodes are more costly, and use more energy. An energy efficient protocol for long life operation such as waste containers is presented in [17]. This protocol maximize the batteries life of the globale infrastructure. Using this protocol, the batteries have to be replace in same time. To achieve that, it use an energy balancing system. This aspect is important for the support of the network. To reduce the maintenance cost, it is particulary interesting to fix a replacement date of the set of batteries of all nodes of the ambient network.
VII. PROTOTYPE DEMONSTRATION
Figure 21 shows the prototype demonstration developed out of the collaborative project “Bin That Thinks” [16]. It consists of prototypes developed for the various solutions of the waste management chain discussed in this article and are marked numerically. The first shows two kitchen bins that collecting different types of waste. The QR codes are scanned using the smartphone placed in-between which is also used to write the inventory onto a NFC tag when a trash bag is sealed. The second is the collective container that can scan the inventory tag and verify with the bag contents for compliance. Its optional screen displays the status and statistics. The later two shows the required applications deployed for monitoring in the truck and operator’s station respectively. While the former visualizes information about bins to be collected, the later displays the waste management infrastructure over the city map. Appropriate operations could also be done through these applications. Finally, the entire demonstration can be viewed in [18].
VIII. RELATED WORKS
Some other approaches using the RFID technology for waste management systems have already been proposed. In [19], the author discusses about several applications of the RFID in the process of collecting wastes. The identification of each bin associated to a RFID tag is principally mentioned. The storage in a tag associated to each product some informa-tion about the end-of-life management process of the product, is also evoked in the paper.
These approaches propose to identify each bin using an identifier stored in a RFID tag associated to the container. In [20], [21], using this identifier, the author proposes to associate in an external database each container with the address of the household owning the container. The volume of wastes estimate the quantity of waste produced by each
Figure 21. Prototype demonstration: (1) Kitchen bin (2) Collective bin showing status (3) Truck’s Application Screen (4) Operator’s status application at city level
household. It is not an information based approach but a physical measurement approach using sensor. The estimation of the volume of waste is computed using an image analysis from a picture of the content of the bin (when the lid of the container is opened). The data are transferred using a GPRS connection to an external database.
The idea developped in [22] is also very close to this approach. In [22], a sensor measures the weight of the bin placed on the truck which collects the bins. It differs to our approach which proposes to use a self-describing approach of wastes to compute the weight of a container. At each collection operation, the truck saves the weight of each bin. The RFID tags are used to store an identifier in a external database of the owner of each container. This approach is not autonous, but using a Wifi connection, the external database of waste production is updated for each household. It becomes easy to track the waste production of each household. In [23], the author presents a real deployment of a system using an approach similar to the approach proposed in [22].
The concept developed in [24] rewards consumers for recycling empty packaging. The consumers are identified by a RFID tag associated to their bin. Also based on a weight measurement of their recycling packaging, the consumer can log into his personal account to view how much they have recycled, as well as statistics such as the number of trees saved by their effort. Every month, the consumers are also rewarded financially.
Actually, selective sorting is not the priority of these appli-cations. RFID is used by the container to identify its owner. To ensure the selective sorting, it is track waste at the item level. This is why item level RFID tagging can have an important role to play in the selective sorting, provided that the tag contain information about the components of the waste.
In [25], the presented approach also considers that each product is associated to an RFID tags from the begining of its cycle of life. The information stored in the RFID tags is not used to help the user in the selecting selective process.
The authors use the RFID technology at another level of the selective sorting process. The RFID tags associated to each product is used to help the service provider of recycling to decide of the appropriate treatment of a product. In this approach, the data stored in the RFID tags are used to access to the information of products in several databases from a single identifer of each product. This approach of the usability of the RFID technology in the recycling process is not autonomous. A major difficulty is then to shared some conformable infor-mation about a product accross several databases, and during all the life cycle of the product.
We had presented a complex scenario where interactions be-tween various waste categories are inferred. A similar ontology based model is presented in [26]. It’s application domain is in delimited environments where objects are located and is used to statically prevent/detect their dangerous spatial/temporal configurations. Although it could be an alternative for our case, the preciseness and complexity is on the higher side to be used when considering our real-time scenarios; like a user waiting with a smart trash bag for the bin to infer and open the lid for disposal.
The main goal developed in [27] is to bring out the environmental impact of RFID used in everyday life. The author discusses RFID for the waste management: a system of discounts and fees to stimulate responsible behavior of users in the selective sorting process, is also discussed. The idea of a bin which collects some information about the wastes is mentioned, although its implementation is not discussed. More generally, in [28], the author predicts an important development of RFID applications in the product recycling chains.
The approach that we propose is innovative in its infor-mation processing architecture: the properties are directly at-tached to physical objects (waste, bags) and data are ”moved” and processed along with the physical flow of wastes. Several systems for encoding the waste description are discussed. The most simple way is to encode the component of each waste in plain text.
IX. CONCLUSION
In this paper, we proposed a new solution to enhance waste collection efficiency using the RFID technology. Fully relying on digital information attached to waste items, this approach does not require any sensor, nor external information system support, enabling high scalability and availability. The pre-sented system helps the user in correctly sorting and disposing wastes.
Regarding the waste sorting support, the user is oriented to the correct container to dispose the waste, and is helped in case of errors. We present an approach for the simple wastes composed of one principal material, and we present another approach for more complex wastes composed of several materials. Another contribution of this system is to be able to report the content of a bin. This information is useful for waste processing operators, for example to optimize waste collection scheduling, or to set up a special handling
when an undesirable product is detected somewhere. This information is communicated to the operators using an ambient communication network of smart bins.
The reported information about the content of each bin is also a way to compute statistics of each type of waste in the recycling process. The smart bins can precisely determine the quantity of each type of waste produces by a household. It should help people to contribute to a more efficient sorting of waste, and reuse valuable materials. By considering the value of wastes produced by each household, it becomes possible to make a retributive incentive system to encourage each user to make the selective sorting of its wastes. This approach can also help to better plan waste collection and special intervention by operators in case of anormal conditions.
REFERENCES
[1] Y. Glouche and P. Couderc, “A smart waste management with self-describing objects,” in SMART 2013, The Second International Confer-ence on Smart Systems, Devices and Technologies, 2013, pp. 63–70. [2] “The EUs approach to waste management,” April 2012. [Online].
Available: http://ec.europa.eu/environment/waste/index.htm
[3] H. Boileau and H. Bj¨ork, “Comparing household waste treatment policies between two medium size cities: Bor˚as (sweden) and chamb´ery (france),” in Proceedings of the 7th World Congress on Recovery, Recycling and Re-integration, June 2006. [Online]. Available: http://csp.eworlding.com/3r/congress/manu pdf/420.pdf
[4] “Veolia: Research and Development.” [Online]. Available: http: //environmentalpassion.com/Research and development
[5] “Better Sorting for Better Recycling.” [Online]. Available: http: //environmentalpassion.com/resource.php?id=2239
[6] Assembl´ee des Chambres Franc¸aises de Commerce et d’Industrie, “Classification des d´echets,” November 2011. [Online]. Available: http://www.enviroveille.com/public/documents/nomenclaturedechets.pdf [7] Y. Glouche and P. Couderc, “A robust RFID inventory,” in Proceedings of the European Conference on Smart Objects, Systems and Technologies (Smart SysTech 2012), Munich, Germany, june 2012.
[8] M. Feldhofer and C. Rechberger, “A case against currently used hash functions in rfid protocols,” in Proceeding of RFID Security, RFID-Sec’06, 2006, pp. 372–381.
[9] “A way forward for glass recycling.” [Online]. Available: http://www.waste-management-world.com/articles/print/ volume-10/issue-1/features/a-way-forward-for-glass-recycling.html [10] “European waste catalogue and hazardous waste list.” [Online].
Available: www.environ.ie/en/Publications/Environment/Waste/WEEE/ [11] M. Cambillau, E. El-Shanta, S. Purushotham, and G. Simeu, “Owl
ontology for solar uv exposure and human health,” Advances in Semantic Computing, Eds. Joshi, Boley & Akerkar, vol. 2, pp. 32–51, 2010. [12] T. Gruber et al., “A translation approach to portable ontology
specifica-tions,” Knowledge acquisition, vol. 5, no. 2, pp. 199–220, 1993. [13] “World wide web consortium (w3c), “owl web ontology language
overview”.” [Online]. Available: http://www.w3.org/TR/owl-features/ [14] H. Knublauch, M. Horridge, M. Musen, A. Rector, R. Stevens, N.
Drum-mond, P. W. Lord, N. Noy, J. Seidenberg, and H. Wang, “The protege owl experience,” in OWLED, 2005.
[15] A. Sinha and P. Couderc, “Smart bin for incompatible waste items,” in ICAS 2013, The Ninth International Conference on Autonomic and Autonomous Systems, 2013, pp. 40–45.
[16] “Bin That Thinks.” [Online]. Available: http://binthatthink.inria.fr [17] D. Tony, N. Mitton, and M. Hauspie, “Energy-based Clustering for
Wireless Sensor Network Lifetime Optimization,” in WCNC 2013, The Wireless Communications and Networking Conference, 2013. [18] “Bin That Thinks prototype demonstration video.” [Online]. Available:
http://www.youtube.com/watch?v=daac0tFig34
[19] S. Abdoli, “Rfid application in municipal solid waste management system,” in IJER International Journal of Envionment Research, vol. 3, no. 3, July 2009, pp. 447–454.
[20] M. Arebey, M. Hannan, H. Basri, R. Begum, and H. Abdullah, “Inte-grated technologies for solid waste bin monitoring system,” in Environ-mental Monitoring and Assessment, vol. 177. Springer Netherlands, 2011, pp. 399–408.
[21] M. Hannan, M. Arebey, H. Basri, and R. Begum, “Rfid application in municipal solid waste management system,” Australian Journal of Basic and Applied Sciences, vol. 4, no. 10, pp. 5314–5319, October 2010. [22] B. Chowdhury and M. Chowdhury, “Rfid-based real-time smart waste
management system,” in Proceedings of the Australasian Telecommuni-cation Networks and AppliTelecommuni-cations (ATNAC 2007), December 2007, pp. 175–180.
[23] J. Wyatt, “Maximizing waste efficiency through the use of rfid,” April 2008, Texas Instruments Incorporated. [Online]. Available: http://www.ti.com/rfid/docs/manuals/whtPapers/wp lf hdx.pdf [24] C. Swedberg, “Rfid Helps Reward Consumers for Recycling,” in RFID
Journal, February 2008. [Online]. Available: http://www.rfidjournal. com/article/view/3936
[25] A. Parlikad and D. McFarlane, “Rfid-based product information in end-of-life decision making,” in Control Engineering Practice, vol. 15, no. 11, 2007, pp. 1348–1363. [Online]. Available: http: //www.sciencedirect.com/science/article/pii/S0967066106001535 [26] D. Cacciagrano, F. Corradini, and R. Culmone, “Resourcehome: An
rfid-based architecture and a flexible model for ambient intelligence,” in Systems (ICONS), 2010 Fifth International Conference on, April 2010, pp. 6–11.
[27] V. Thomas, “Environmental implications of rfid,” in Proceedings of the 2008 IEEE International Symposium on Electronics and the Environ-ment, ser. ISEE ’08. Washington, DC, USA: IEEE Computer Society, 2008, pp. 1–5.
[28] D. C. Wyld, “Taking out the trash (and the recyclables): Rfid and the handling of municipal solid waste,” in International Journal Of software Engineering & Applications (IJSEA), vol. 1, no. 1, January 2010, pp. 1–13.