Engineering secure software architectures: patterns, models and analysis
Texte intégral
Figure



Documents relatifs
This expansion happened simultaneously to a steep rise in TFP in the tradable sector relative to the non-tradable sector, increasing markups and profit shares in both sectors of
Elga briefly considers the possibility that agents with imprecise credences may still be rationally obliged to accept or refuse any particular bet. But this
BrainFist proposes a solution to this specific problem of document management by using metadata to maximize the potential use of content.. Furthermore, BrainFist is
L’accès à ce site Web et l’utilisation de son contenu sont assujettis aux conditions présentées dans le site LISEZ CES CONDITIONS ATTENTIVEMENT AVANT D’UTILISER CE SITE WEB.
/ La version de cette publication peut être l’une des suivantes : la version prépublication de l’auteur, la version acceptée du manuscrit ou la version de l’éditeur. Access
This article presented a brief review on the main nondestructive methods currently available to evaluate corrosion activity in rebars, and introduced the new surface
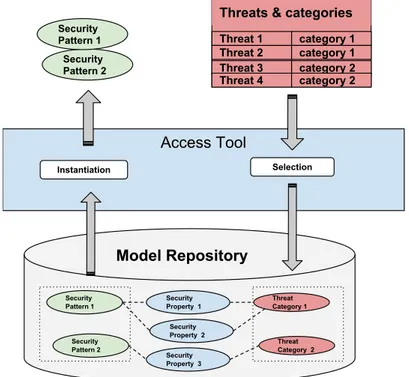
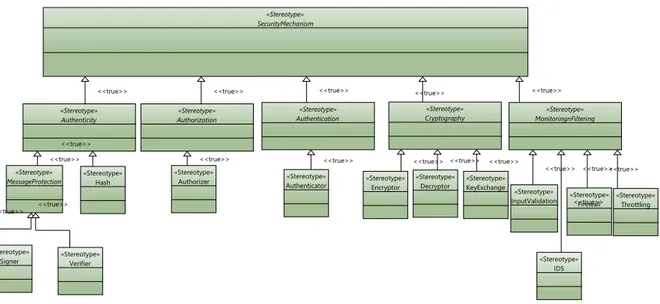
The approach consists of the following steps (a) model-based risk assessment per- formed on the architecture to identify threats, (b) selection and instantiation of security