Sec2graph: Network Attack Detection Based on Novelty Detection on Graph Structured Data
Texte intégral
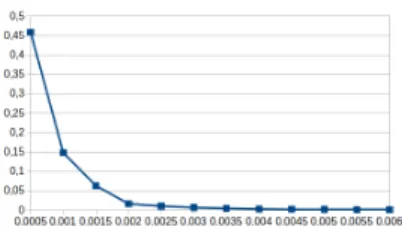
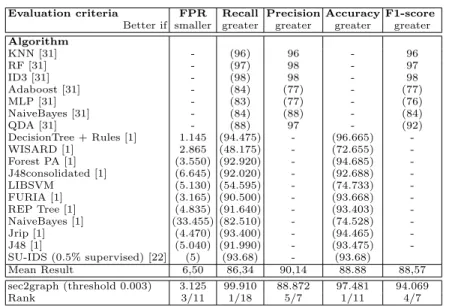
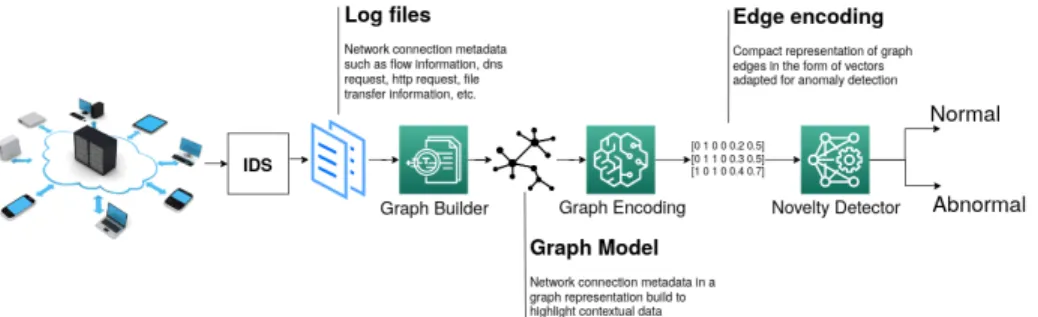
Figure
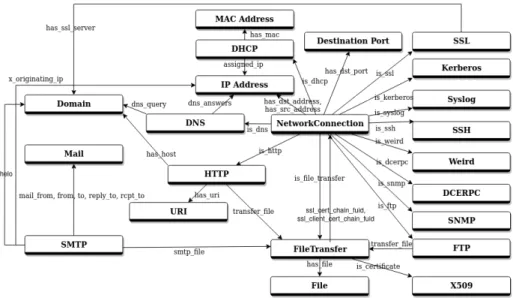
![Figure 2 shows the different types of links between SOs. The semantic of these links is derived from the CybOX model [8].](https://thumb-eu.123doks.com/thumbv2/123doknet/12411881.332953/6.918.203.723.703.929/figure-shows-different-types-links-semantic-derived-cybox.webp)
Documents relatifs
In the first part of this paper, a theoretical security analysis of QIM data hiding measures the in- formation leakage about the secret dither as the mutual informa- tion between
Flair: An easy-to-use framework for state-of-the-art NLP. Contextual string embeddings for se- quence labeling. To- wards Scalable Hybrid Stores: Constraint-Based Rewriting to
The dendritic morphology corresponds to an ordered crystal growth (of few main trunks with secondary branches tilted with a well-defined angle); it is obtained when the growth
In a special case where each source refers to a single information item, set-valued belief functions decompose with respect to intersection and are thus multiple source
While similarity was defined by the human in their work, we will use our Visual Similarity module to provide the most similar known object (compared to a new one) which allows the
Because of that metagraph processing framework can read data stored in the form of textual predicate representation and import it into flat graph data structure handled by
We first introduce the notion of λ-K¨ onig relational graph model (Definition 6.5), and show that a relational graph model D is extensional and λ-K¨ onig exactly when the
kernel function, number of neighbors L in the adjacency matrix, number of wavelet scales S, wavelet coefficients used in feature extraction for a given scale s (we are using only