A secure protocol based on a sedentary agent for mobile agent environments
Texte intégral
Figure


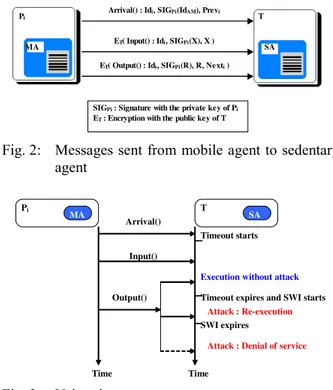
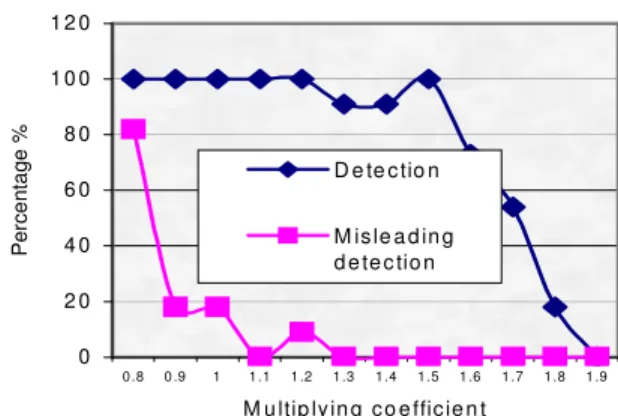
Documents relatifs
troller Agent tracks the status of resources in the datacenter. When the Scheduling Agent gets the response from the Controller Agent, it verifies if the proposed QoS and
Dominique Duhaut, "Distributed Algorithm For High Control Robotics Structures", International Conference On Artificial Intelligence – 1999 – Volume 1 p 45 à 50
This model has a major advantage that the domain remains unaffected by non trusted users (with only decreased amount of trust degree). But this model suffers from
Security in agent systems is obtained by regulating the information exchanged between and used by agents - by controlling the services used by each agent as well as the
For instance, a user cannot have a system class replaced by subtyping it since these classes are declared with (the access modifier) final. Finally, bytecode verifica-
Designed with complex service environments in mind and the service as a central concept, the JIAC IV agent framework constitutes a toolkit for developing and de- ploying
L'agent mobile utilisé dans cette solution est à base de composants, il s'agit de l'agent GAMA pour Agent Mobile Générique et adaptable, agent proposé dans le cadre de travail
Thus, network environment is populated by a set of mobile management agents that co-operate with each other in order to perform global security management activities (described in
