ScienceDirect
Available online at www.sciencedirect.com
Procedia Computer Science 176 (2020) 261–270
1877-0509 © 2020 The Authors. Published by Elsevier B.V.
This is an open access article under the CC BY-NC-ND license (https://creativecommons.org/licenses/by-nc-nd/4.0) Peer-review under responsibility of the scientific committee of the KES International.
10.1016/j.procs.2020.08.028
10.1016/j.procs.2020.08.028 1877-0509
© 2020 The Authors. Published by Elsevier B.V.
This is an open access article under the CC BY-NC-ND license (https://creativecommons.org/licenses/by-nc-nd/4.0) Peer-review under responsibility of the scientific committee of the KES International.
ScienceDirect
Procedia Computer Science 00 (2020) 000–000
www.elsevier.com/locate/procedia
1877-0509 © 2020 The Author(s). Published by Elsevier B.V.
This is an open access article under the CC BY-NC-ND license (https://creativecommons.org/licenses/by-nc-nd/4.0/) Peer-review under responsibility of KES International.
24th International Conference on Knowledge-Based and Intelligent Information & Engineering
Systems
Enhancing Energy Efficiency of Wireless Sensor Network for
Mining Industry Applications
Abdellah Chehri
a*, Rachid Saadane
b, Nadir Hakem
c, Hasna Chaibi
ba University of Quebec in Chicoutimi, Québec, G7H 2B, Canada.
b SIRC/LaGeS-EHTP, EHTP Km 7 Route El Jadida, Oasis, Morocco c Université du Québec en Abitibi-Témiscamingue, Val d’Or, QC, J9P 1Y3, Canada
Abstract
Recent advances in sensing modules and radio technology will enable small but smart sensors to be deployed for a wide range of environmental monitoring applications. They collect data from different environment or infrastructures in order to send them to the cloud using different communications platforms. These data can be used to provide smarter services. However, they are various issues and challenges related to the ubiquitous sensors that should be solved. In this paper we interest on analysis of wireless sensor network from an energy management perspective. The idea behind the energy-efficiency wireless sensor networks is that each node can only transmit to a limited number of other nodes directly. The limited resources of nodes imply that the transmission range is limited. In order to transfer the data to the final destination, the traffic must be relayed using intermediate nodes, creating a multi-hop route. The total energy consumption associated with an end-to-end transmission over such a route can be significantly reduced if the nodes are correctly configured. In this paper, underground mine monitoring system is presented with an overview of the related issues and challenges such as reliability, cost, and scalability.
© 2020 The Author(s). Published by Elsevier B.V.
This is an open access article under the CC BY-NC-ND license (https://creativecommons.org/licenses/by-nc-nd/4.0/) Peer-review under responsibility of KES International.
Keywords: IoT, Wireless Sensor Networks, Mining Industry, Cross-layer Design , Adaptive Modulation, Adaptive Routing.
* Corresponding author. Tel.: +1 (418)-545-5011;
E-mail address: achehri@uqac.ca
1. Introduction
Wireless sensor networks (WSN) are one of today’s most compelling emerging technologies. WSN is made up of a large number of inexpensive devices that are networked via low power wireless communications. It is the networking
Available online at www.sciencedirect.com
ScienceDirect
Procedia Computer Science 00 (2020) 000–000
www.elsevier.com/locate/procedia
1877-0509 © 2020 The Author(s). Published by Elsevier B.V.
This is an open access article under the CC BY-NC-ND license (https://creativecommons.org/licenses/by-nc-nd/4.0/) Peer-review under responsibility of KES International.
24th International Conference on Knowledge-Based and Intelligent Information & Engineering
Systems
Enhancing Energy Efficiency of Wireless Sensor Network for
Mining Industry Applications
Abdellah Chehri
a*, Rachid Saadane
b, Nadir Hakem
c, Hasna Chaibi
ba University of Quebec in Chicoutimi, Québec, G7H 2B, Canada.
b SIRC/LaGeS-EHTP, EHTP Km 7 Route El Jadida, Oasis, Morocco c Université du Québec en Abitibi-Témiscamingue, Val d’Or, QC, J9P 1Y3, Canada
Abstract
Recent advances in sensing modules and radio technology will enable small but smart sensors to be deployed for a wide range of environmental monitoring applications. They collect data from different environment or infrastructures in order to send them to the cloud using different communications platforms. These data can be used to provide smarter services. However, they are various issues and challenges related to the ubiquitous sensors that should be solved. In this paper we interest on analysis of wireless sensor network from an energy management perspective. The idea behind the energy-efficiency wireless sensor networks is that each node can only transmit to a limited number of other nodes directly. The limited resources of nodes imply that the transmission range is limited. In order to transfer the data to the final destination, the traffic must be relayed using intermediate nodes, creating a multi-hop route. The total energy consumption associated with an end-to-end transmission over such a route can be significantly reduced if the nodes are correctly configured. In this paper, underground mine monitoring system is presented with an overview of the related issues and challenges such as reliability, cost, and scalability.
© 2020 The Author(s). Published by Elsevier B.V.
This is an open access article under the CC BY-NC-ND license (https://creativecommons.org/licenses/by-nc-nd/4.0/) Peer-review under responsibility of KES International.
Keywords: IoT, Wireless Sensor Networks, Mining Industry, Cross-layer Design , Adaptive Modulation, Adaptive Routing.
* Corresponding author. Tel.: +1 (418)-545-5011;
E-mail address: achehri@uqac.ca
1. Introduction
Wireless sensor networks (WSN) are one of today’s most compelling emerging technologies. WSN is made up of a large number of inexpensive devices that are networked via low power wireless communications. It is the networking
capability that fundamentally differentiates a sensor network from a mere collection of sensors, by enabling cooperation, coordination, and collaboration among sensor assets.
Harvesting advances in the past decade in microelectronics, signal processing, wireless communications and networking, wireless sensor network technology is expected to have a significant impact on our lives in the twenty-first century [1].
Unlike centralized networks, wireless sensor networks are working in ad hoc fashion. The configuring, self-healing characteristics make WSN; and therefore allows them a significant advantage in a large number of situations.
The development of this attractive network has many open doors for several numbers of “new and exciting” applications, in which flexibility, easy deployment, and configuration are essential properties.
How can IoT help the mining industry?
The general objectives can be summarized a as follows [2]-[3]: • Real time monitoring of gases and other parameters;
• Monitoring equipment locations and operation statuses to improve productivity and reduce fatal collision accident;
• Locating and tracking miners in case of disaster for emergency rescue operations; • Tracking and monitoring assets equipment;
• Monitoring miner’s unsafe practices and warning.
• Automate maintenance and operations of machines – Leads to creation of newer collaboration models with OEMs for monitoring via cloud connectivity and networks.
• Standardize processes – Helps build newer business models and highly agile processes at the operations level. • Improve traceability and visibility – Lets users automatically transfer and receive data over a network without requiring human intervention. Moreover, remote monitoring of operations ensures maximum efficiency, improved safety, decreased variability, and better identification of performance issues.
• Ensure safety of people and equipment – Integrates mine automation system with automated physical elements to create a real-time, multi-dimensional model from a variety of data sources including the sensors on equipment as well as geological and other data. The system can then be used to optimize and coordinate the mine’s layout, operation, and vehicle paths to ensure high efficiency and safety.
The measurement of physical parameters makes the sensors the most suitable technology for monitoring and reporting critical quantifiable measures. Sensors though are not just limited to environmental sensing. Any application involving sensing of physical parameters like sound, pressure, temperature, etc., might use sensor networks [3].
The choice of WSN deployment in underground mine should make a compromise between conflicting requirements. The priority is to ensure a robust global network with battery-operated nodes. Therefore, these types of systems are usually developed with the following goals in mind.
In short, there is an abundance of applications that could utilize wireless ad hoc networks. However, the other side of the coin is the numerous challenges associated with this kind of system. First, the nodes are, in most cases, tiny devices and often battery-powered. Some applications have stringent QoS requirements in terms of timely delivery of packets (bounded delay), high packet delivery ratio, and low jitter. Packet delay is directly related to the number of hops traversed by the packet and the congestion level of the network, while other networks might have a required system lifetime [4]-[5].
The distributed and the mobile nature of wireless sensor network combined with the QoS requirements makes traditional protocols unsuitable. Therefore, an alternative analysis should be adopted for the design of WSN [6].
Another technique, called modulation scaling, which exhibits benefits similar to those of voltage scaling has been presented in [7]. In [8], an adaptive modulation scheme for a point-to-point path loss Additive White Gaussian Noise (AWGN) channel has been investigated. In this work, the authors included circuit energy in the total energy budget. This creates a trade-off: Transmitting at a high rate requires more transmission power, but a shorter period is required to transmit the packet, thereby saving circuit energy, and vice versa.
Routing problems are usually considered to be the core of wireless sensor network design. However, in most application scenarios, WSN nodes are powered by small batteries, which are often in practice non-rechargeable. Therefore, software solution, which combines cross-layer and energy-aware system design to increase energy efficiency, is a promising way worth exploring [5].
Bhardwaj and Chandrakasan [10] have provided upper bounds on the lifetime of sensor networks where sensor node locations are given. In [11], the authors propose a transmission range optimization scheme to maximize the
network lifetime given fixed node locations. However, many of these routing protocols separate the different layers (physical layer, medium access, and routing). This may lead to largely suboptimal network designs.
Recently, many works are focused on “energy-efficiency routing.” Joint power control and scheduling have been proposed in [12]. A hierarchical cross-layer design approach through mutual adaptation of nodes transmitting powers and route selection is proposed in [13] to increase network lifetime [14]- [18].
For instance, in the Radio Network model, the interference from non-neighboring nodes is neglected, and Signal to Interference- plus-Noise Ratio (SINR) is a simplified model. In addition, we consider an isolated network settings, by neglecting the interference from nodes that are not participating in the cooperation scheme.
The paper focus on the link budget between two nodes to find minimized communication parameters by numerical analysis.
The paper is organized as follows: After discussing the energy-efficient surveillance system using wireless embedded devices in underground mines, we introduce underground channel characteristics. Our model and a formulation of the considered power consumption minimization problem in Section 4. Section 5 discusses enhancement of the power consumption of the sensor node in average-case networks. Section 5 concludes the paper.
2. Enhancing Energy Efficiency of Wireless Sensor Network for Underground Mines Monitoring System
Lifetime sensor nodes are battery-driven and hence operate with a limited energy resource. In large-dense sensor networks, it is infeasible to replace batteries when a sensor is down. In practice, it will be necessary for many applications to provide guarantees that a system with unattended wireless sensors can remain operational without any replacements for several months and even years.
2.1. Deployment
The network must be deployed, keeping in mind two main objectives: coverage and connectivity [19]. Both describe the robustness of always having a path between every pair of nodes. For example, in a single-hop star topology, the sink has a higher traffic load than the sensing ones. Therefore, the sink node must have better performance characteristics in order to cope with the requirements. Self-configuration nodes in a wireless sensor network have to be able to configure their own network topology; localize, synchronize, and calibrate themselves; coordinate inter-node communication; and determine other important operating parameters [19].
Thus, many protocols provide auto-management techniques for avoiding collisions adapt the radio-coverage of sensors, replace dropped nodes, and many other aspects.
2.2. Topology
For larger areas and networks, multi-hop routing is necessary. It provides robustness and scalability properties. Also, mesh networks are used: they are regularly distributed systems that generally allow transmission only to a node's nearest neighbor. Therefore several topologies are usually utilized in WSN projects. Some of them are described in the following:
A- Single-hop Star Topology: It is the simplest WSN topology (fig.1. a). It follows the common pattern "many to
one» that is given in many WSN configurations.
B- Tree-based Topology: It can be considered as a hierarchy of several single-hop star topologies. Therefore, a
node in this configuration has the duty of receiving and forwarding packets from its lower level interconnected star topology (Fig. 1. b).
C- Multi-hop Mesh-based Topology (arbitrary/grid): This topology brings multiple routing paths between nodes,
which means that these nets are robust to the failure of individual nodes or links. If they are placed randomly, nodes form an arbitrary mesh graph, provide better flexibility of arrangement, and promote self-organization and fault tolerance. If not, they can build a more structured communication graph such as the 2D grid structure shown in Fig. 1. c.
Figure 1. Different WSN topologies
D- Clustered-based Topology: One of the most convincing architectures for WSN is a deployment architecture
where multiple nodes within each local region report to different cluster-heads (Fig. 1. d).
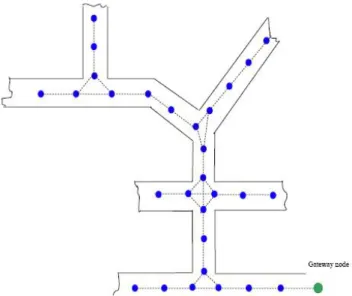
E. Daisy chain topology: In our case, for the underground mine environment, a daisy chain of nodes installed along
a tunnel must withstand the failure of a node. One effective way add to redundancy is to ensure each node in the chain is in range of at least two other nodes on each side. Figure 2 illustrates an example of WSN deployment in underground mines. Networks' topology designs should also take into consideration potential attenuation caused by rubble if ever part of mine tunnel collapses.
Fig. 2. Sample setup for WSN deployment in underground mine.
2.3. Energy
It is important to know what the sources of power consumption in WSN are. The simplest radio model considers that the energy consumed by the radio of a node has two components (this model will be used for our analysis):
• Electronic power (𝑃𝑃"): the energy consumed by digital and analog components that carry out the RF,
baseband and protocol processing.
2.4. Medium Access Control
One of the main challenges in designing wireless sensor networks is to create a system that performs efficiently across layers of communication. There are trade-offs between optimizations in the different layers, and thus ad hoc networks are designed based on their application.
Cross-layer interaction [18] refers to the fact that it is virtually impossible to design a ‘universal’ protocol (Physical, routing, MAC, transport, etc.) and expect that it will function efficiently in all conditions and applications. Since there often is an extreme range of variability in the system parameters of sensor networks, it is essential to tune the network protocols to the radios, and the applications to the network protocols. Even more important is the concept that in many cases, the MAC protocols, routing, and applications must be jointly designed (i.e., cross-layer design), and due to the dynamical change of parameters, the protocols must be adaptively tuned as well.
Other challenges in the design of ad hoc networks are the mobility of the communication nodes and the scalability of the system. As already discussed, mobility is one of the main characteristics of ad hoc wireless networks, and this property means that the network must, in many applications, cope with the communicating nodes being in motion. Note that mobility, which is often viewed as the #1 enemy of wireless ad hoc networks, if adequately characterized, modeled, predicted and taken into account, can indeed be of great help in the design of scalable protocols.
Medium Access Control (MAC) is an algorithm performed locally by communicating nodes. No scheduling or global control unit is required, allowing efficient access to and a fair share of a communication resource, such as a radio frequency, a bandwidth, or time slots. Due to the scarce channel bandwidth and other resources available in ad hoc networks, there is a need to regulate the nodes’ access to their shared channel. This gives rise to the challenge of designing efficient MAC protocols [20].
2.5. Network Layer
Sensor nodes are deployed in the field for a common task. Since they are densely deployed, the nodes are often close to each other. Thus, using a multihop communication allows to WSN to consume less power than the traditional single-hop communication. Furthermore, the transmission power levels may be kept low, which is highly desired for covert operations. In addition, multihop communication may effectively overcome some of the signal propagation effects experienced in long-distance wireless communication.
The routing protocol of the sensor networks is usually designed according to the following principles: • Power efficiency is always an important consideration.
• Sensor networks are mostly data-centric.
• An ideal sensor network has attribute-based addressing and location awareness.
• Data aggregation is useful only when it does not hinder the collaborative effort of the sensor nodes. • The routing protocol is easily integrated with other networks, e.g., the Internet.
The energy efficiency is the main criteria for routing protocol design for the wireless sensor networks since the life-time of the systems depends on the longevity of each sensor node. In addition, a routing protocol may be data-centric. A data-centric routing protocol requires attribute-based naming [21]. For attribute-based naming, the users are more interested in querying an attribute of the phenomenon, rather than querying an individual node. For instance, “the areas where the temperature is over 20 C” is a more typical query than “the temperature read by a certain node”. The attribute-based naming is used to carry out queries by using the attributes of the phenomenon. It also makes broadcasting, attribute-based multi-casting, geo-casting, and any-casting important for sensor networks.
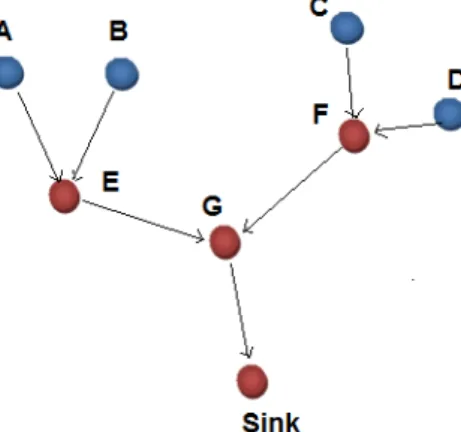
As data-centric routing is essential, it should also leverage the usefulness of data aggregation. Data-aggregation is a technique used to solve the implosion and overlap problems in data-centric path [22]. Data coming from multiple sensor nodes are aggregated as if they are about the same attribute of the phenomenon when they reach the same routing node on the way back to the sink. For example, sensor node E aggregates the data from sensor nodes A and B while sensor node F aggregates the data from sensor nodes C and D, as shown in Figure 3.
Data aggregation can be perceived as a set of automated methods of combining the data that comes from many sensor nodes into a collection of meaningful information [36]. With this respect, data aggregation is known as data fusion [23]. Also, care must be taken when aggregating data, because the specifics of the data, e.g., the locations of reporting sensor nodes, should not be left out. Such specifics may be needed by certain applications.
used to select an energy-efficient route. Figure 3 is used to describe each of these approaches, and node “Tran” is the source node that senses the phenomena [24].
Figure 3. An example of data aggregation.
3. Underground Channel Characteristics
The propagation in the underground channel is complicated due to scattering and rough surface diffraction. The underground propagation has been studied by Murphy et al. [25]. It was also found that underground electromagnetic propagation behavior depends on several factors. Radio transmission has been identified as the most desirable form of communication to reach miners. There are necessarily three ways to achieve this:
• Select frequencies high enough to utilize the mine galleries as a waveguide • Install a leaky feeder cable to act as a distributed antenna to guide the propagation.
• Select frequencies low enough to penetrate the strata enabling “through-the-earth” propagation. It enables mine-wide paging systems but supports low bandwidth.
Other modeling channel researches in underground mine have been done [26], as well as experimental measurements [27], [28]. The underground mine radio environments are far from ideal, the high density of scatters caused by the rigorous wall with many metal surfaces to block and reflect radio signals. In [27], the author states that multipath characteristics can vary considerably with gallery dimensions and transmit-receive antenna separation [28].
The authors explain that this localized phenomenon is caused by destructive multipath combinations and by the variations in phase of the paths induced by the connecting galleries, possibly implying constructive combinations. These results indicate the RF link budget should include a safety margin of several dBs to ensure reliable communications in underground mine environments. Moreover, according to measurements done in an even wide mine [29] – [30], delay spread, which is essential to determine the maximum data rates that can be transmitted into radio channels without distortion. The results give a delay spread of about 500 ns, and the power difference between the two most robust paths is nearly 90% of the time under 10 dB. Clearly, for mines with wide tunnels, delay spread can significantly deteriorate the performance of wideband communications.
3.1. RF Budget Link
The RF budget link is the difference between the transmitted power and receiver sensitivity. The field mentioned above measurements reveal attenuations of 40 dB/decade occurring in harsh environments, even with line-of-sight.
The standard RF budget link of Zigbee/802.15.4 and Bluetooth are 85 dB and 75 dB, respectively, which is sufficient for short-range applications. However, for long-range applications and robust links with safety margins, an RF budget link at least 110 dB is recommended. Power amplifiers should be avoided in low power consumption. Lowering the data rate to increase the receiver sensitivity is a will be the right choice.
4. Problem formulation
the theoretical energy consumption models in the transmitter and receiver nodes along the route, for both communication and processing block, are taken into account.
The goal is to find the optimal configuration for a route minimizing the total energy consumption per packet transmission while ensuring that the QoS requirements are satisfied. The entire end-to-end delay must not exceed the delay constraint, and the received signal to noise and interference ratio (SNIR) in all hops must be above the minimal fixed threshold. The problem is mathematically described as:
• Modulation levels can be adjusted for the wireless module of the node. • The buffer of each node can hold up to 𝑄𝑄 packets.
• Each link is assumed to be reliable.
• The inference among nodes is assumed to be solved by spatial, frequency, or code diversity using other ALOHA MAC layers.
Therefore, given a path of 𝑛𝑛 nodes (and thus 𝐿𝐿 hops), two main constraints are suggested:
𝐸𝐸*+* = ∑ 𝐸𝐸/.01 . ∀ 𝑖𝑖 (1)
Subject to:
∑ 𝜏𝜏/.01 .≤ 𝑇𝑇789 ∀ 𝑖𝑖 (1.a)
𝛾𝛾.≥ 𝛾𝛾7.< ∀ 𝑖𝑖 (1.b)
𝑃𝑃*9,.≤ 𝑃𝑃789 ∀ 𝑖𝑖 (1.c)
The first expression gives the total energy consumption for each transmitting packet over all accessible routes. The inequality (1.a) ensures that the packet should transmit through the route with minimum time 𝑇𝑇789, while 𝜏𝜏. is the
individual transmission time of a node. The second one is the SNR constraint which is proportional to the SER constraint (Eq. 1b). The 3rd line of (Eq. 1c) means that each node transmits with an adaptive power which is less than
a certain fixed power 𝑃𝑃789. Where 𝑃𝑃789 is the peak power constraint that limits the total power consumption in each
node.
The immediate solution for finding the optimal modulation for each node is to study all possibilities and then to determine the optimal modulation order. However, it is very expensive in processing time to find the optimal modulation by the examination of all possibilities. As solution which is more efficient consists of finding the optimal modulation of each node that respect all constraints without processing all possibilities. Therefore, the estimated modulation is suboptimal solution. We use a greedy algorithm for resolve the system of Eq. (1).
5. Simulation
In this section, we present some numerical results to evaluate the energy efficiency of the pass-band modulation schemes. The system described has been simulated taking as a reference IEEE 802.15.4 standard in order to make a realistic choice of the simulation parameter values. For this purpose, we assume that all modulation schemes operate in B = 65.5 KHz and the 𝑓𝑓? = 2.4 GHz Industrial Scientist and Medical (ISM) band has been utilized for WSNs.
According to the Federal Communications Commission (FCC 15.247 RSS-210 standard) for United States / Canada, the maximum allowed antenna gain is 6 dBi [31]. In this work, we assume that Gt = Gr = 5 dBi. According to [27] The value of the path-loss exponent in underground mines for the 2.4 GHz band has been determined to be equal to 2.16 [32] – [35]. Table (I) summarizes the system parameters for the simulation.
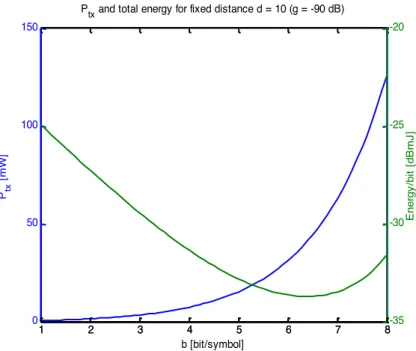
From figure 4, we can see that when the transmission range increases, the required energy to transmit a bit increase; this seems evident. However, If we expand the modulation order, this would waste valuable energy for transmission over shorter distances, where a higher modulation order is far more energy-efficient.
Generally speaking, the optimal configuration for each hop is found as the best trade-off between saving circuit energy at the cost of transmission energy, and vice versa [36]. This is illustrated in figure 5, where the total energy consumption per bit and required transmission power are plotted against modulation order. A single packet transmission over a hop of length 10 m and a target BER of 10BC is considered. The total energy includes energy
consumption in both the transmitting and the receiving node. As we can see from this figure, the required transmitted power increases exponentially with the modulation order. Due to the peak constraint the maximum allowed modulation is bEFG= 8.
Tab. 1 System evaluation parameters. Parameter Value 𝐏𝐏𝐦𝐦𝐦𝐦𝐦𝐦 250 mw 𝐆𝐆𝟏𝟏 30 dB 𝛈𝛈 2.16 𝐌𝐌𝐥𝐥 40 dB 𝛂𝛂𝟐𝟐 -174 dBm/Hz 𝐍𝐍𝐟𝐟 10 dB B 62.5 Khz 𝐐𝐐 1024 bit 𝚭𝚭 0.35 𝛀𝛀 1
In addition, the configuration that yields the lowest total energy consumption is approximately 𝑏𝑏+Z* = 6.4
bits/symbol as shown in the same figure (green curve). Obviously, in practice we cannot use a modulation orders with non-integer values (the modulations order will be restricted to integer values,). So the closest value is 𝑏𝑏+Z* = 6.
Fig. 4. Energy 𝐸𝐸. vs distance and b (bit/symbol).
0 10 20 30 40 50 0 2 4 6 8 10 0 1 2 3 4 x 10-3 b [bit/symbol] distance [m] Ener gy /bi t [ dB m J]
Fig. 5. Consumed energy 𝐸𝐸.per bit vs b (green curve), required transmitted power vs. modulation order (blue line)
6. Conclusion
In this work, we investigate a route optimization problem for wireless sensor networks for localization and monitoring in underground mines. Our goal is to adapt all routes in the networks to transmit the data from any node to the central node with the best energy performance. This is calculated according to a certain quality of service (QoS) in under to provide an energy-efficiency routing strategy.
The algorithm should be taking into account the mobility of the node as well as the propagation characteristics of the underground mines channel. The optimization formulation assumes that at least an existing route has been found between node and sink. It allows QoS requirements in terms of end-to-end bit error rate.
The analysis given here takes into account the mutual interactions between the physical and routing layer. In fact, the cross-layer study is still a complex problem. Hence, some assumptions must be considered to give a useful analysis.
References
[1] L. K. Bandyopadhyay, S. K. Chaulya, P. K. Mishra. (2009), “Wireless Communication in Underground Mines: RFID-based Sensor Networking”, Springer Editions.
[2] A. Chehri, P. Fortier, P.-M. Tardif, (2006) “Deployment of Ad-Hoc Sensor Networks in Underground Mines”, Sixth International Conference on Wireless Sensor Networks, WSN 2006, Banff, Alberta, Canada.
[3] A. Chehri, P. Fortier, P.-.M. Tardif, (2007) "Security monitoring using wireless sensor networks", Proceedings of the IEEE Communication Networks and Services Research, CNSR’07, pp. 13-17.
[4] A. Chehri, P. Fortier, P.-M. Tardif, (2009) "Cross-layer link adaptation design for UWB-based sensor networks", Comput. Commun., 32(13), 1568-1575.
[5] Weilian Su and Tat L. Lim. (2006) “Cross-layer design and optimization for wireless sensor networks”, In SNPD-SAWN ’06: Proceedings of the Seventh ACIS International Conference on Software Engineering, Artificial Intelligence, Networking, and Parallel/Distributed Computing (SNPD’06), pages 278–284, Washington, DC, USA.
[6] A. Chehri, G. Jeon, and B. Choi, “Link-quality measurement and reporting in wireless sensor networks,” Sensors, vol. 13, no. 3, pp. 3066-3076, March 2013.
[7] C. Schurgers, O. Aberborne, M. Srivastava, (2001) “Modulation scaling for energy-aware communication systems”, in ISLPED, 96-99. [8] S. Cui, A. J. Goldsmith, A. Bahai, (2005) “Energy-constrained modulation optimization”, IEEE Trans. on Wireless Com., 4(4), 2349 – 2360.
1 2 3 4 5 6 7 8 0 50 100 150 Ptx [m W] b [bit/symbol]
Ptx and total energy for fixed distance d = 10 (g = -90 dB)
1 2 3 4 5 6 7 8-35 -30 -25 -20 E ner gy /bi t [ dB m J]
[9] J. H. Chang, L. Tassiulas, (2004) “Maximum lifetime routing in wireless sensor networks”, IEEE/ACM Transactions on Networking, 12, pp. 609 – 619.
[10] M. Bhardwaj, A. P. Chandrakasan, (2002) “Bounding the lifetime of sensor networks via optimal role assignments”, IEEE INFOCOM, 3. [11] M. Perillo, Z. Cheng, W. Heinzelman, (2004) “On the problem of unbalanced load distribution in wireless sensor networks”, IEEE Globecom
Dallas, United-States.
[12] T. ElBatt, A. Ephremides, (2002) “Joint scheduling and power control for wireless ad-hoc networks”, in Proceedings of the 21st IEEE Annual Joint Conference of the IEEE Computer and Comm. Societies, 2, 976 - 984, NY, USA.
[13] C. Comaniciu, H. V. Poor, (2007) “On Energy-Efficient Hierarchical Cross-Layer Design”, EURASIP Journal on Wireless Communications and Networking, special issue on Wireless Mobile Ad Hoc Networks, Article ID 60707, 9 pages, doi :10.1155/2007/60707..
[14] F. F. Digham, M. S. Alouini, (2002) “Adaptive M-FSK modulation for power limited systems”, in Proc. IEEE Veh. Technol. Conf., Vancouver, Canada, 1202 - 1206.
[15] H. Yang, L. Yang, K. Wu, (2006) “Minimum-Energy Route Configuration for Wireless Ad Hoc Networks”, 25th IEEE International Performance, Computing, and Communications Conference (IPCCC), Phoenix, USA.
[16] G. Bravos, A. G. Kanatas, (2004) “Wireless sensor networks: an energy-aware adaptive modulation scheme”, in processing of International society for Optical Engineering, 5611, 133-143.
[17] X. Liang, W. Li, T. A. Gulliver, (2007) “Energy efficient modulation design for wireless sensor networks”, Proc. IEEE Pacific Rim Conference on Communication, Computers and Signal Processing (PACRIM’07), 98- 101.
[18] A. Chehri and G. Jeon, “Routing protocol in the industrial internet of things for smart factory monitoring,” in Proc. Springer KES IIMSS 2019, St. Julians, Malta, June 17-19, 2019, pp. 505-515.
[19] A. Chehri and G. Jeon, “The industrial internet of things: examining how the IIoT will improve the predictive maintenance,” in Proc. Springer KES IIMSS 2019, St. Julians, Malta, June 17-19, 2019, pp. 517-527.
[20] W. Ye, J. Heidemann, D. Estrin, (2002) ”An energy-efficient MAC protocol for wireless sensor networks” IEEE Proceedings INFOCOM 2002, vol. 3, pp. 1567 - 1576.
[21] K. N. Qureshi, S. Din, G. Jeon, and F. Piccialli, “Link quality and energy utilization based preferable next hop selection routing for wireless body area networks” Computer Communications, vol. 149, pp. 382-392, Jan 2020.
[22] I. Ahmed, A. Ahmad, F. Piccialli, A. K. Sangaiah, and G. Jeon, “A robust features based person tracker for overhead views in industrial environment,” IEEE Internet of Things Journal, vol. 5, no. 3, pp. 1598-1605, June 2018.
[23] Heinzelman, W. R., Chandrakasan, A., and Balakrishnan, H., "Energy-Efficient Communication Protocol for Wireless Microsensor Networks," IEEE Proceedings of the Hawaii International Conference on System Sciences, pp. 1-10, Maui, Hawaii, USA, January 2000.
[24] M. Khan, S. Din, M. Gohar, A. Ahmad, S. Cuomo, F. Piccialli, and G. Jeon, “Enabling multimedia aware vertical handover management in internet of things based heterogeneous wireless networks,” Multimedia Tools and Applications, vol. 76, no. 24, pp. 25919-25941, Dec 2017. [25] J. N. Murphy, H.E. Parkinson, (1978) ”Underground mine communications”, Proceedings of the IEEE, vol 66, Page(s):26 - 50.
[26] S. Chow, (1992) “Propagation of radio waves in potash mine tunnels and its implication on radio systems performance”, Singapore ICCS/ISITA ’92, pp: 890-894.
[27] C. Nerguizian, C. Despins, S. Affes, M. Djadel, (2005) ”Radiochannel characterization of an underground mine at 2.4 GHz”, IEEE Transactions on, Wireless Communications, 4(5), 2441 - 2453.
[28] A. Benzakour, S. Affes, C. Despins, P.-M. Tardif, (2004) ”Wideband measurements of channel characteristics at 2.4 and 5.8 GHz in underground mining environments”, Vehicular Technology Conference, VTC2004- Fall.
[29] H. Chehri, A. Chehri, N. Hakem (2019), “In underground vehicular radio channel characterization”, Proceedings of the Elsevier's Procedia Computer Science, Twenty-third International Conference on Knowledge-Based and Intelligent Information and Engineering Systems, Budapest, Hungary.
[30] H. Chehri, A. Chehri, N. Hakem (2019), “Empirical radio channel characterization at 5.9GHz for vehicle-to-infrastructure communication Proceedings of the IEEE 90th Vehicular Technology Conference, Hawaii, USA.
[31] J. Abouei, K. Plataniotis and S. Pasupathy (2010), “Green modulation in dense wireless sensor networks”, IEEE International Conference on Acooustics, Speech and Signal Processing (ICASSP’10), Dallas, Texas, USA.
[32] A. Chehri and H.T. Mouftah, "Energy Efficiency Adaptation for Multihop Routing in Wireless Sensor Networks ”, Journal of Computer Networks and Communications Volume 2012, Article ID 767920, 8 pages.
[33] Abdellah Chehri and Rachid Saadane. 2019. Zigbee-based remote environmental monitoring for smart industrial mining. In Proceedings of the 4th International Conference on Smart City Applications (SCA ’19). Association for Computing Machinery, New York, NY, USA, Article 111, 1–6. DOI:https://doi.org/10.1145/3368756.3369099.
[34] A. Chehri, H. T. Mouftah, "QoS aware green routing protocol for wireless sensor networks", Electrical & Computer Engineering (CCECE) 2012 25th IEEE Canadian Conference on, pp. 1-4, 2012.
[35] A. Chehri, H. T. Mouftah, "Link adaptation-based optimization for wireless sensor networks routing protocol", Communications (QBSC) 2012 26th Biennial Symposium on, pp. 142-145, 2012.
[36] A. Chehri, H. Mouftah, "Energy-Aware Multi-Hop Transmission for Sensor Networks based on Adaptive Modulation", IEEE 6th International Conference on Wireless and Mobile Computing. Networking and Communications. 2010.