Theoretical and Applied Foundations for Intrusion Detection in Single and Federated Clouds
Texte intégral
Figure

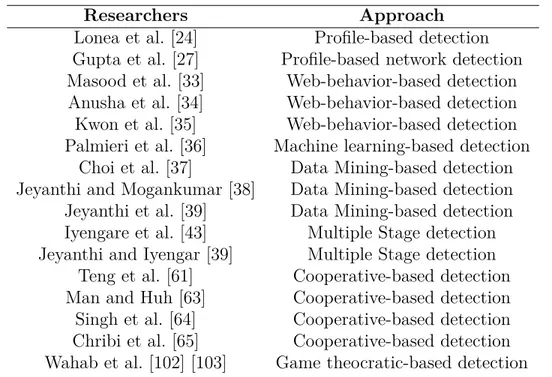
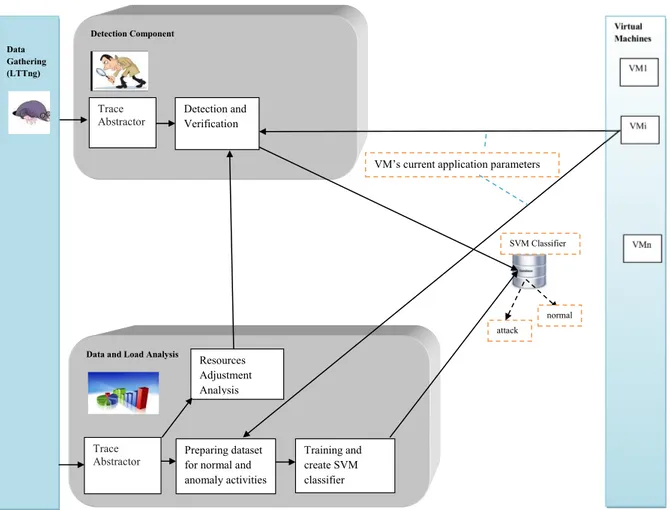
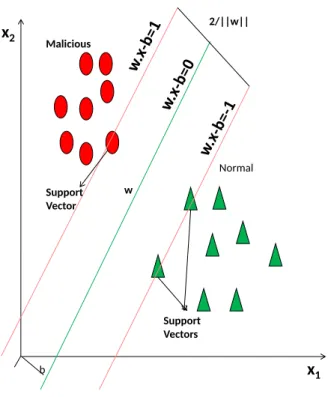
Documents relatifs
The most important system features of developed and partially implemented M-AHIDS are integration of the several anomaly detection tech- niques in a form of agent, machinery of
the output of the detection modules (e.g. it informs the user or a central system) and stores other information such as the alert database. Finally, the detection module detects
As a result, our analysis technique allows overcoming common restrictions in previous work such as unexpected runtime errors in the Java Virtual Machine (JVM) or applications
The proposed intrusion detection systems considers a general type of an attack scenario where malicious packets are injected into a SCADA network system composed of a
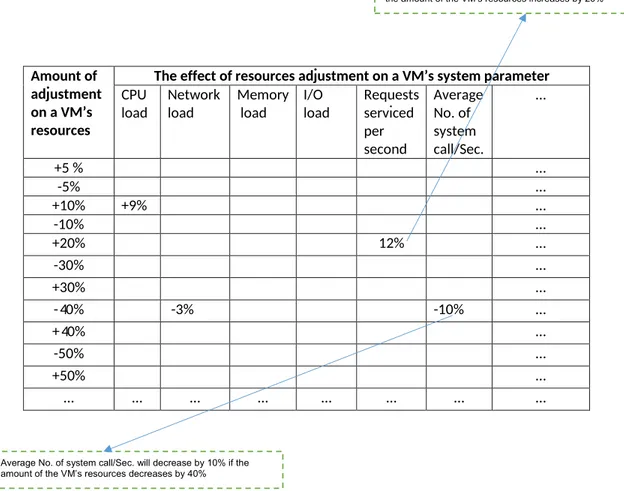
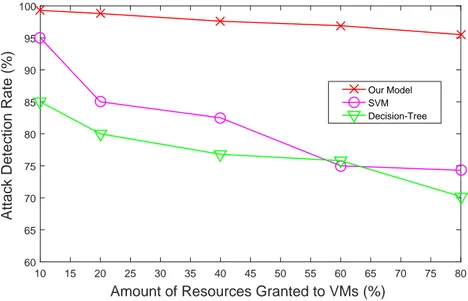
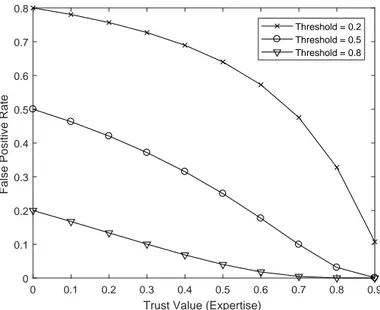
However IaaS clouds features, such as multi-tenancy and elasticity, generate new security vulnerabilities [1] for which the security monitoring must be partly run by the cloud
Probe index Spectrogram Processed spectrogram Loss function for autoencoder learning 4-norm distance Reconstruction error Error time series Detection threshold Cumulative
small
This paper presents an intrusion detection system based on the model of the human immune system and which will use the artificial immune systems paradigm.. Furthermore