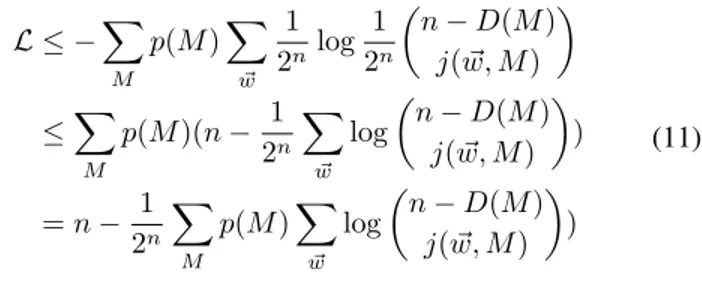Hide & Share: Landmark-based Similarity for Private KNN Computation
Texte intégral
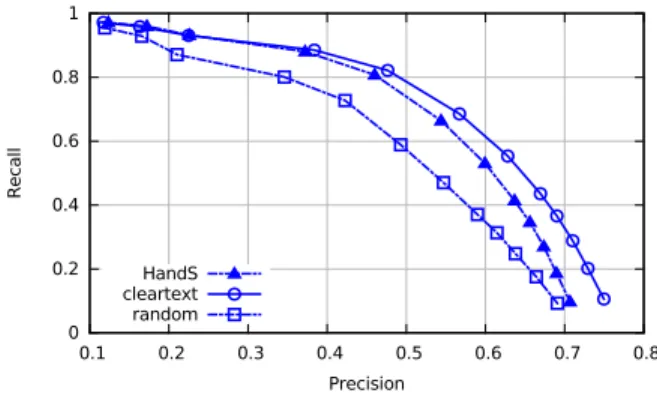
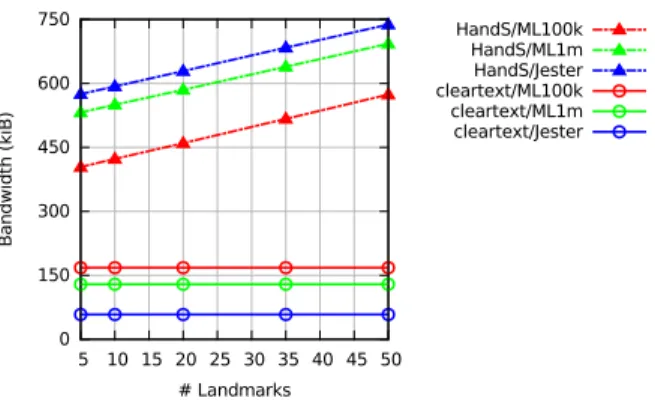
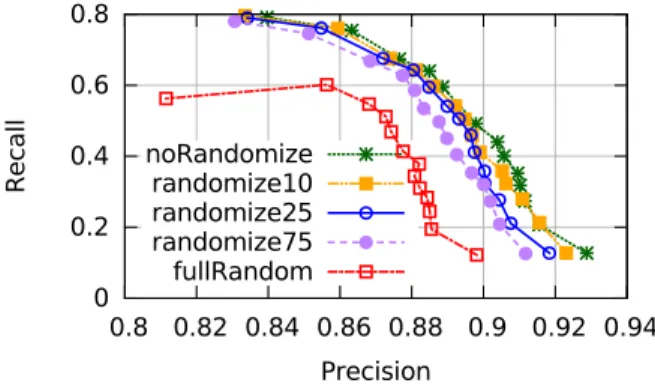
Figure
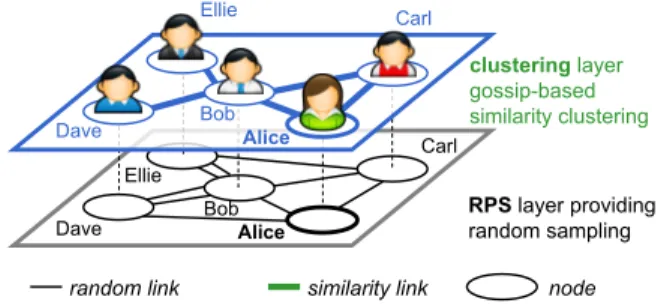


Documents relatifs
Performance on the Similar Seg- ments in Social Speech Task at MediaEval 2013 was well above baseline, showing the value of prosody for
Biham , \Two practical and provably secure block ciphers: BEAR and LION." Proceedings of the 3rd Fast Software Encryption Workshop, Lecture Notes in Computer Science Vol...
Let X be an algebraic curve defined over a finite field F q and let G be a smooth affine group scheme over X with connected fibers whose generic fiber is semisimple and
The first step of our method attempts to select representatives in the matrix for the concepts of the new taxonomy based on string similarity, which we will call attractors (as
For direct and 1-hop relationship, the differences appeared to be significant, i.e., users connected by a direct or 1-hop distanced reciprocal relation shared significantly
The similarity index presented here is not only an extension of the Pearson correlation coefficient in rating systems, but also easy to be extended to quantify the structural
Fortis N.V., Archimedeslaan 6, 3584 BA Utrecht, Netherlands; Fortis S.A./N.V., Rue Royale 20, 1000 Brussels, Belgium The Royal Bank of Scotland Group plc, Head Office,
Our research models, for example, a situation in which data about individuals is collected in a database (e.g., consumer data or clinical data). Control over the utilization of the