Dependability engineering of complex computing systems
Texte intégral
Figure
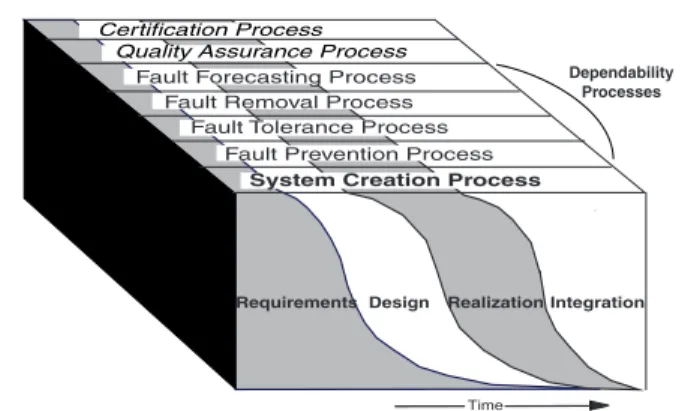


Documents relatifs
5.6 Performance of MO-BO on the aerospace test problem (values of the final hyper-volume obtained and its standard deviation on 20 repetitions) using MO-DGP, independent GPs, or LMC
Abstract: Awerbuch and Scheideler have shown that peer-to-peer overlays networks can survive Byzantine attacks only if malicious nodes are not able to predict what will be the
Awerbuch and Scheideler [8] have shown that peer-to-peer overlay networks can survive Byzantine attacks only if malicious nodes are not able to predict what will be the topology of
In this process, a great attention is done to traceability analysis, which allows verifying all the links among Acquirer and Other Stakeholder Requirements, Technical and Derived
The Systems Analysis Process is used to: (1) provide a rigorous basis for technical decision making, resolution of requirement conflicts, and assessment of alternative
[6] have studied the effect of defect shape and it is orientation on the burst pressure using an experimental and finite element analysis.. G.Fekete
A knowledge-based engineering (KBE) design methodology in which the interface knowledge base is implemented is then proposed to help the designers to improve the
In our experiments, temperature effects have been explored only for masculinization because mal-carrying animals are all genetic XX females, but we also observed a family effect