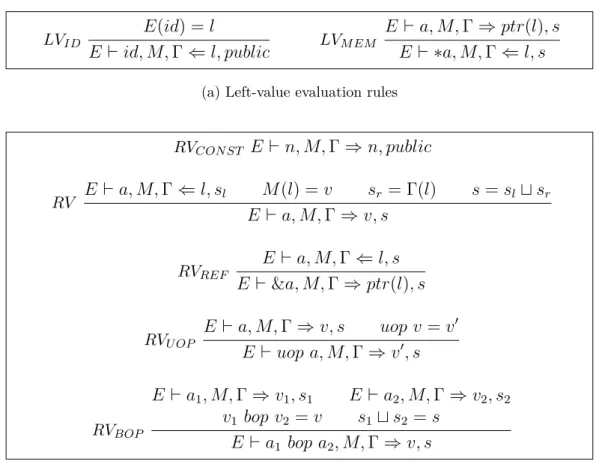
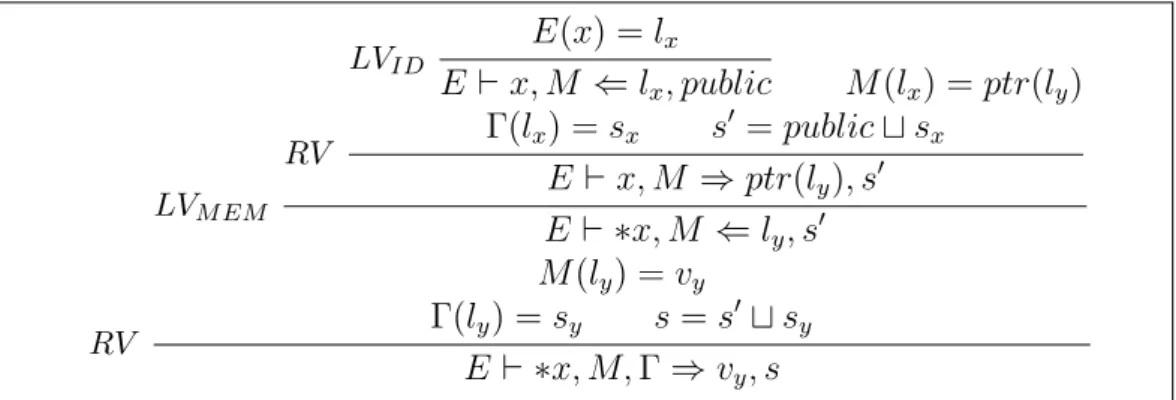From qualitative to quantitative program analysis : permissive enforcement of secure information flow
Texte intégral
Figure



Documents relatifs
In this paper we investigate the effect of attacks to the trust level of honest users on the security of existing anonymity networks, such as the Reiter and Rubin’s C
The results we present in this article are twofold: first, we exhibit a fine hierarchy within the class of languages p-recognised by monoids from J, depending on the length of
The new next-to-next-to-leading order pQCD calculations (NNLO) for jet production cross sections in neutral-current DIS are exploited for a determination of the strong coupling
On the other hand, we have one parasite dimension, which does not originate from the theoretical model of uses of symbolic resources (Zittoun, 2006), and which describes
Rojas (Eds), 1 The Global Handbook of Quality of Life..
We have shown how a data-flow interface between a regular program expressed in Alpha and its host program can be designed automatically by analysis of the code of the Alpha
Leakage reported by ApproxMC2 and sharpCDCL as a number of bits, relative error (as a percentage) in number of bits of channel capacity, running times for each tool, and speedup
Several properties of circadian rhythms could then be verified and compared to experiments: period, amplitudes and the ordered sequence of the phosphoforms involved, phase