A Contract-extended Push-Pull-Clone Model
Texte intégral
Figure
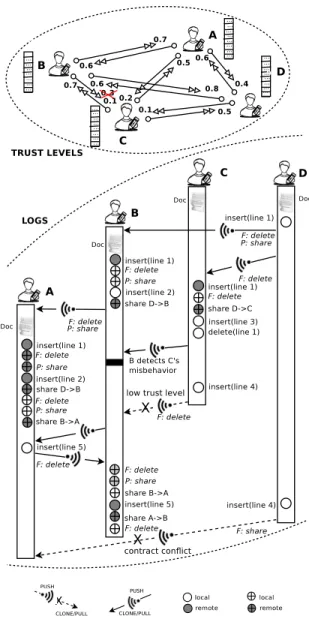

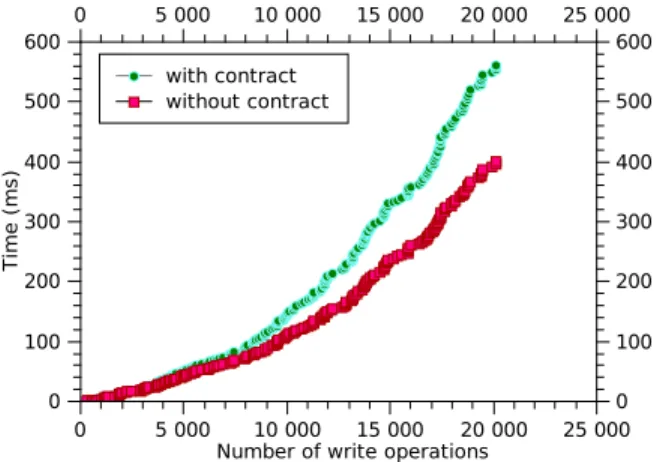
Documents relatifs
In this paper, we answer negatively to this question by exhibiting a threshold on the doubling dimension, above which an infinite family of Cayley graphs cannot be augmented to
Our negative result requires to prove that for an infinite family of graphs in G δ , any distribution of the long range links leaves the expected number of steps of greedy routing
It is essentially a local version of Tian’s invariant, which determines a sufficient condition for the existence of Kähler-Einstein metrics....
Jean-Pierre Demailly / Pha.m Hoàng Hiê.p A sharp lower bound for the log canonical threshold.. log canonical threshold of
[r]
In this work, a new method to produce a concise summary of sequences of events related to time is presented, which is based on the data size reduction obtained merging time
The ITU-T and the IETF jointly commissioned a Joint Working Team (JWT) to examine the feasibility of a collaborative solution to support OAM requirements for MPLS
The other transfer modes (Block, Compressed) do not close the connection to indicate the end of file. They have enough FTP encoding that the data connection can