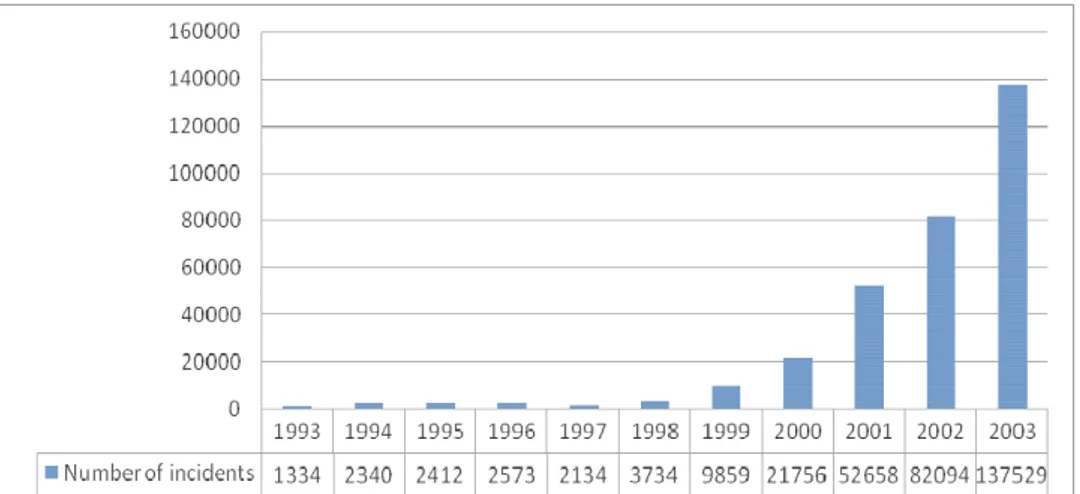
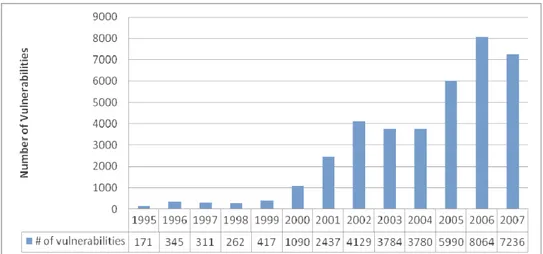
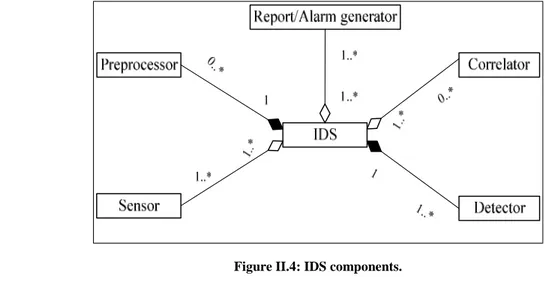
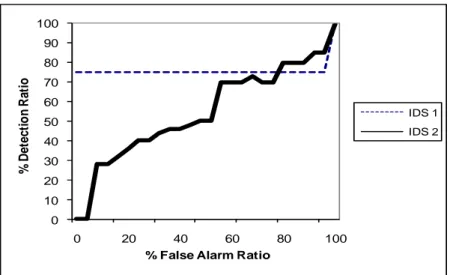
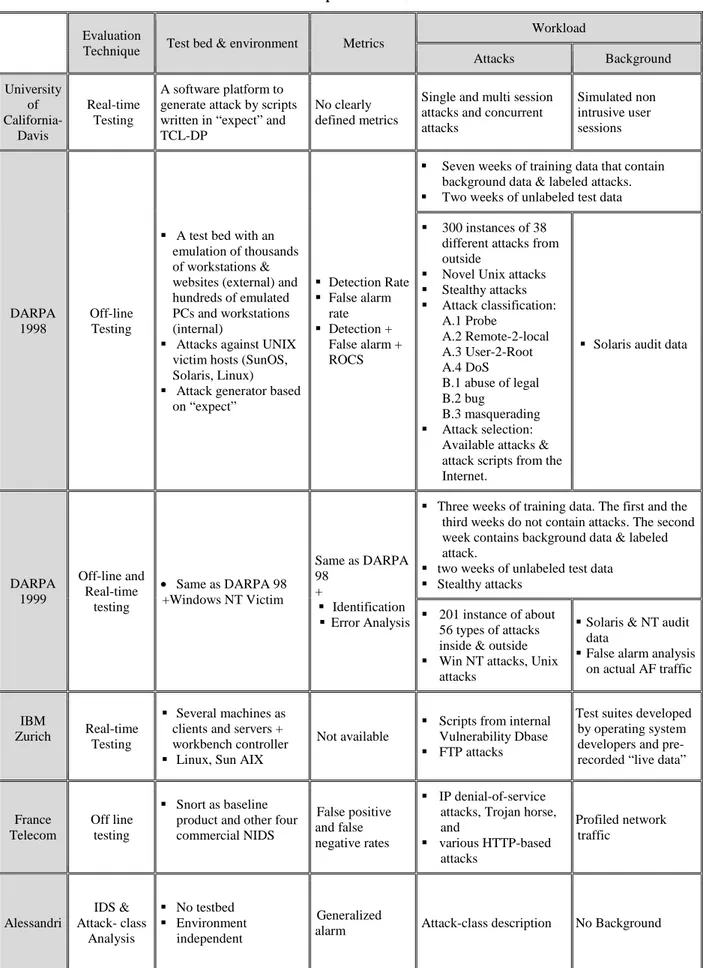
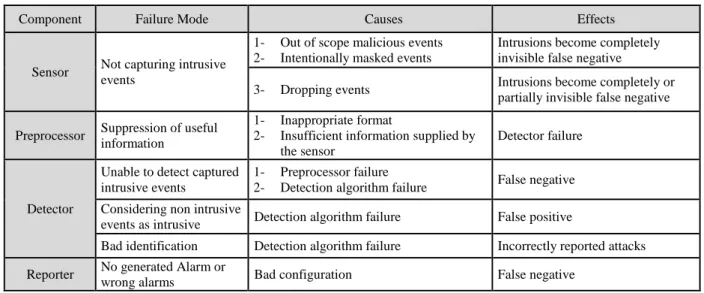
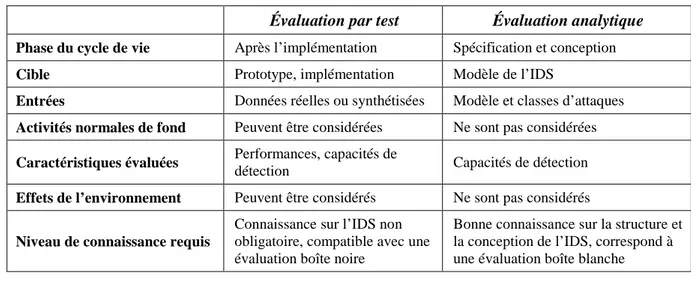
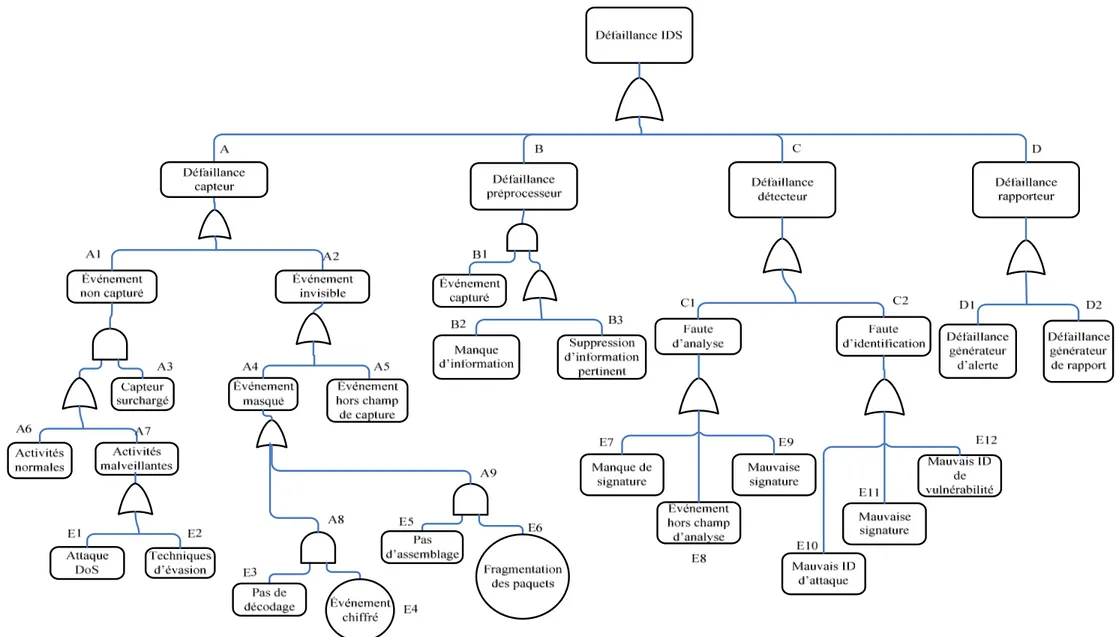
Évaluation des Systèmes de Détection d'Intrusion
Texte intégral
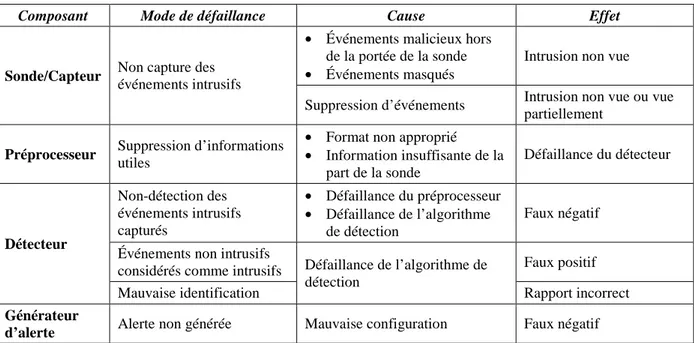
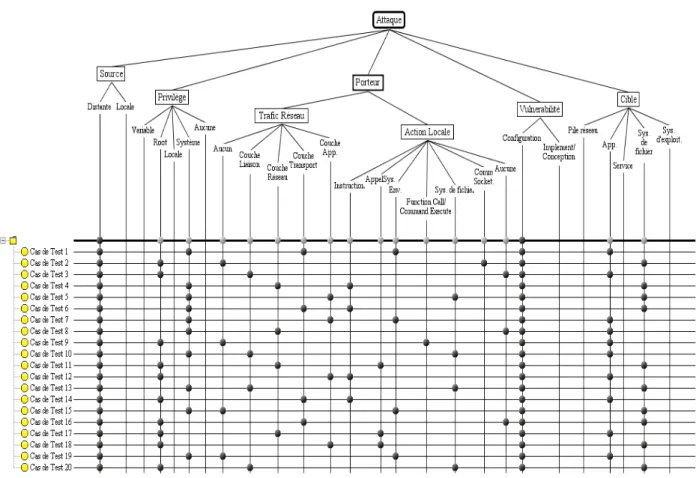
Figure
Documents relatifs
The semantic annota- tion tool contains: an ontology-based mark-up component which allows the user to browse and to mark-up relevant pieces of in- formation; a learning
This paper presents an intrusion detection system based on the model of the human immune system and which will use the artificial immune systems paradigm.. Furthermore
The approach proposed in this work aimed at addressing the aforementioned problem in a twofold manner: first, it wanted to define a method able to operate with any type of
She moves forward purposefully... SIMON, the
Specific questions include: "How does remembering self in moments of praxis construct educational perspeclivesthrough narrati ve?";"Whatdoesa critically-framed
In the first case driven by viability selection and in the diploid context, the Fisher theorem, stating that the mean fitness increases as time passes by, holds true but, as a result
Our main finding is that VAR-based and survey inflation expectations contribute signifi- cantly to inflation dynamics. Using final vintage data, their relative contributions
A way to assess both the accuracy (i.e., the ex- pected fraction of alternatives correctly classified) and the confidence of the classification model (i.e., the probability that